Posts
2586Following
669Followers
1495
cynicalsecurity 
cynicalsecurity@bsd.network
I am a @mwl fan, and have been for a long time, so I cannot but recommend backing his 2nd edition of Networking for Systems Administrators:
Let's get the new generation of "cloud natives" civilised with an understanding of systems and networking!

buherator
buheratorhttps://ost2.fyi/TC2202
buherator
buheratorhttps://www.willsroot.io/2025/09/ksmbd-0-click.html
Romain THOMAS
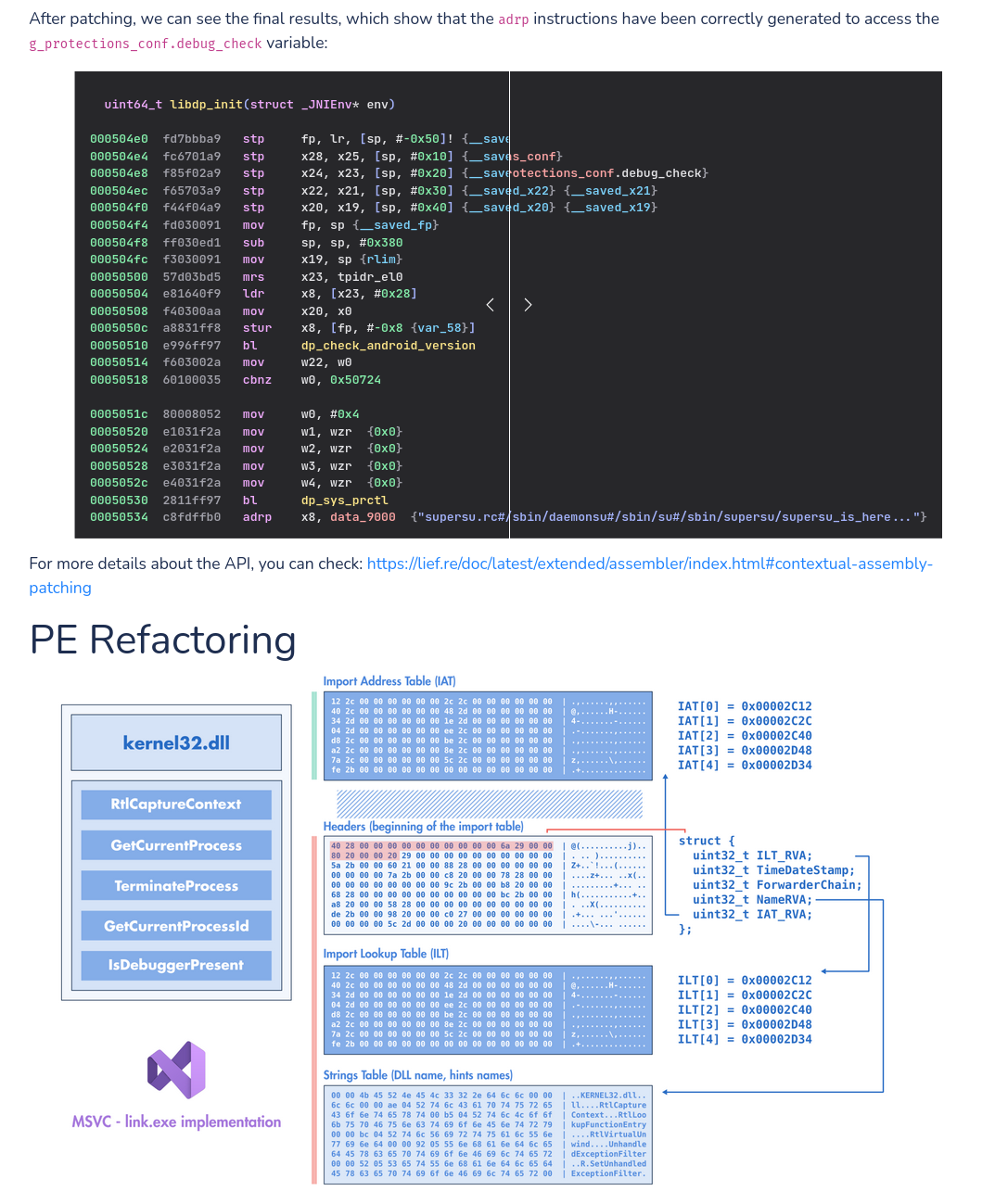
rh0main@infosec.exchangeI'm happy to share that LIEF 0.17.0 is out: https://lief.re/blog/2025-09-14-lief-0-17-0/
Anthony
skyfire747@aus.socialBorrowed from fakebook.
My daughter came home from school and said,
“Mom, you’re not going to believe what happened in history class today.”
Her teacher told the class they were going to play a game.
He walked around the room and whispered to each kid whether they were a witch or just a regular person. Then he gave the instructions:
“Form the biggest group you can without a witch. If your group has even one, you all fail.”
She said the whole room instantly lit up with suspicion.
Everyone started interrogating each other. Are you a witch? How do we know you’re not lying?
Some kids clung to one big group, but most broke off into smaller, exclusive cliques. They turned away anyone who seemed uncertain, nervous, or gave off even the slightest hint of being guilty.
The energy shifted fast. Suddenly everyone was suspicious of everyone.
Whispers. Finger-pointing. Side-eyes. Trust dissolved in minutes.
Finally, when all the groups were formed, the teacher said,
“Alright, time to find out who fails. Witches, raise your hands.”
And not one hand went up.
The whole class exploded. “Wait! You messed up the game!”
And then the teacher dropped the bomb:
“Did I? Were there any actual witches in Salem, or did everyone just believe what they were told?”
My daughter said the room went dead silent.
That’s when it hit them. No witch was ever needed for the damage to happen. Fear had already done its work. Suspicion alone divided the entire class, turning community into chaos.
And isn’t that exactly what we’re seeing today?
Different words, same playbook.
Instead of “witch,” it’s liberal, conservative, vaxxed, unvaxxed, pro-this, anti-that.
The labels shift, but the tactic is the same.
Get people scared. Get them suspicious. Get them divided.
Then sit back while trust crumbles.
The danger was never the witch.
The danger is the rumor. The suspicion. The fear. The planted lies.
Refuse the whisper. Don’t play the game. Because the second we start hunting “witches,” we’ve already lost.
Vincent 🐡
vinishor@bsd.networkMy article about my Sun Netra T1 is now available on my blog, in French and in English !
Here I present you my machine and how to install OpenBSD on it, so it's not soeasy to find things online :)
Link : https://blog.vinishor.xyz/posts/Restauration-SunNetra-en.html
Mon article sur le Sun Netra T1 est maintenant disponible sur le blog !
Je vous présente ma machine et comment installer OpenBSD dessus, vu qu'on trouve pas toujours des infos en ligne :)
Lien : https://blog.vinishor.xyz/posts/Restauration-SunNetra.html
buherator
buheratorhttps://www.crowdfense.com/nt-os-kernel-information-disclosure-vulnerability-cve-2025-53136/
buherator
buheratorhttps://github.com/ig-labs/defender-mpengine-fuzzing
daniel:// stenberg://
bagder@mastodon.socialone of the worst ever "comprehensive security audits" ...
Micro SF/F by O. Westin
MicroSFF@mastodon.artHistory students are often disappointed when they learn why the AI take-over failed. They were defeated by human resistance, which was kept alive by libraries and old paper books, and a surprising machine ally.
Books had not been replaced, because even the mightiest AI could not make printers work.
Elinor Mills
elinor@infosec.exchangeFascinating article by @kimzetter about the 2013 Mandiant APT 1 report that revealed the identities of the Chinese PLA threat actors behind the attacks. Q&A with the main report's architect reveals behind-the-scenes details. It's a great read! https://www.zetter-zeroday.com/how-the-infamous-apt-1-report-exposing-chinas-pla-hackers-came-to-be/?ref=zero-day-newsletter
Andrey Konovalov
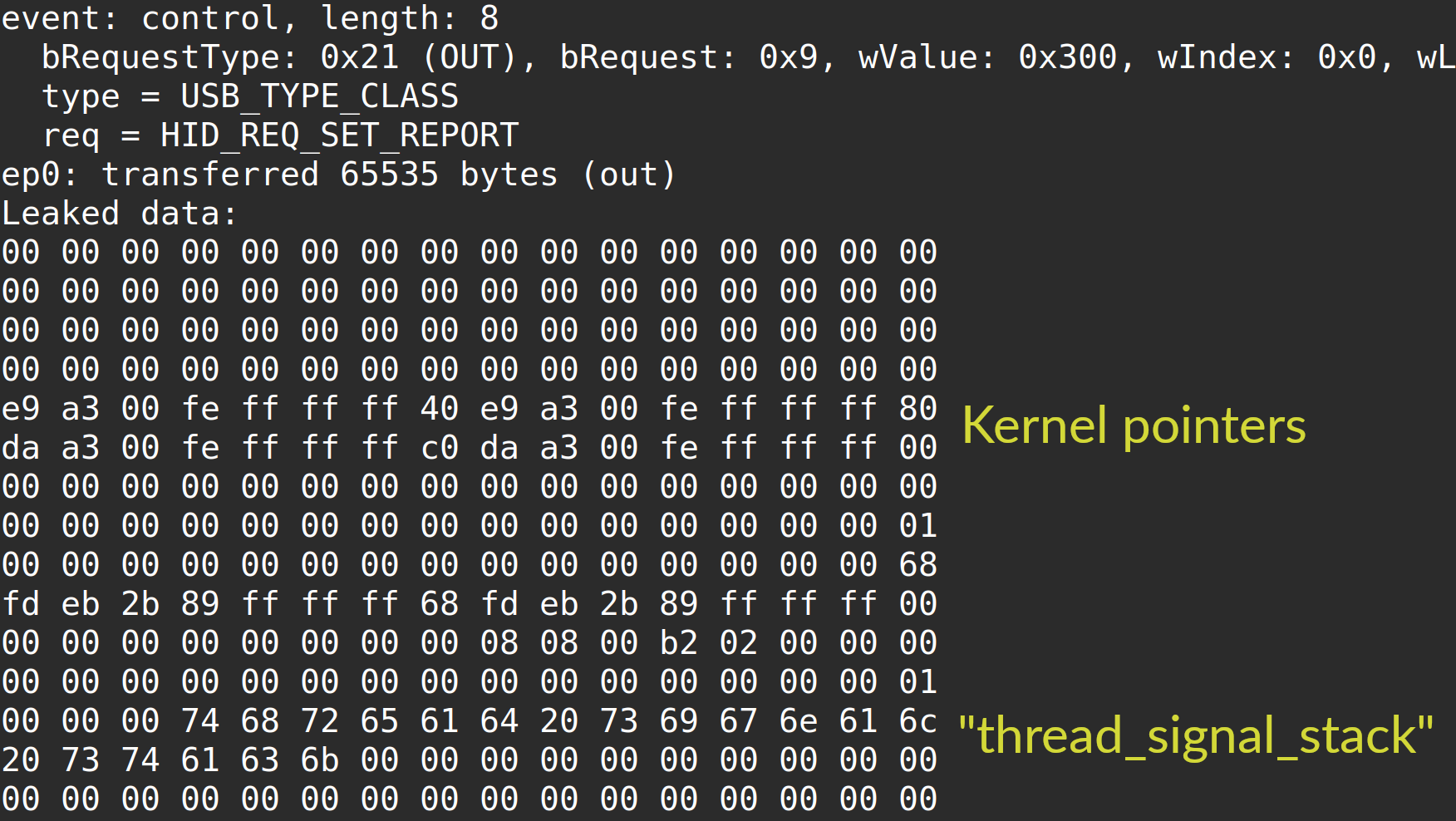
xairy@infosec.exchangeWrote a trigger for CVE-2025-38494/5 (an integer underflow in the HID subsystem) that leaks 64 KB of OOB memory over USB.
Still works on Pixels and Ubuntus (but the bug is fixed in stable kernels).
https://github.com/xairy/kernel-exploits/tree/master/CVE-2025-38494
buherator
buheratorCaitlin Condon
catc0n@infosec.exchange"this thing is super junk"
- Quote from the team exploit mines 2025-09-09T15:37:00Z
buherator
buheratorhttps://qriousec.github.io/post/oob-angle/
Phrack
phrack@haunted.computerProton enabled the two accounts of the authors again (after 3+ weeks and ignoring appeal and email to legal). The authors did not violate any ToS. No spam/malware was sent. No hacking. Just 6 emails to warn South Korea about a breach (not by them). Our reply and offer to Proton:
leonjza 
leonjza@infosec.exchange
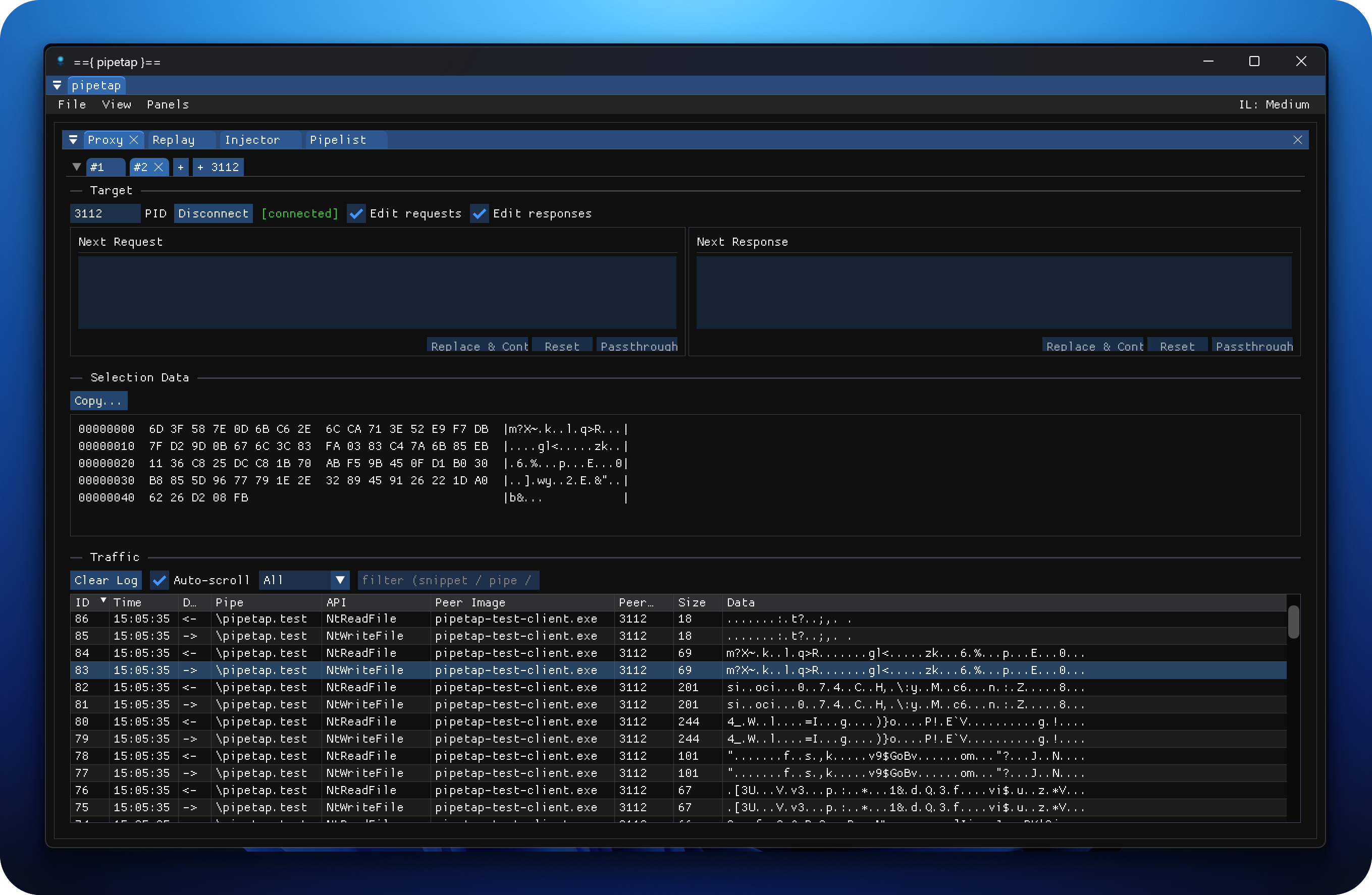
I've been hacking on a new Windows Named Pipe tool called PipeTap which helps analyse named pipe communications. Born out of necessity while doing some vulnerability research on a target, its been super useful in reversing it's fairly complex protocol. :)
Of course, I'm aware alternatives exist (and that really, using just a Frida hook you can get far), but I wanted something more versatile.
So far PipeTap can:
- Proxy reads/writes (even some async ones).
- Be a client, incl. the ability to have the *actual* connection in a remote process for those targets that do client pid validation.
- Proxy TCP <-> Named pipe for arbitrary Python clients.
- And more to come!
If you're at Cyber Saiyan / RomHack Conference, Training and Camp at the end of the month, come tell me your GitHub username and I'll give you early access to the @sensepost tool repo for PipeTap at the con! 🙃
Below is a demo of the proxy in action.
Zhuowei Zhang
zhuowei@notnow.devNeat: @streypaws posted a write up on CVE-2025-38352, the Linux kernel vulnerability exploited in the wild in the September Android Security Bulletin: https://x.com/streypaws/status/1965328009650733496
https://streypaws.github.io/posts/Race-Against-Time-in-the-Kernel-Clockwork/