Posts
3536Following
721Followers
1583
pancake 
pancake@infosec.exchange
RE# or why dotnet is faster than Rust, it’s my nice read of the day https://iev.ee/blog/resharp-how-we-built-the-fastest-regex-in-fsharp/
CFG Bot 🤖
cfgbot@mastodon.socialProject: 90b06f07eb75045ea3d4ba6577afc9b58078eafeb2cdd417e2a88d7ccf0c0273 90b06f07eb75045ea3d4ba6577afc9b58078eafeb2cdd417e2a88d7ccf0c0273
File: 90b06f07eb75045ea3d4ba6577afc9b58078eafeb2cdd417e2a88d7ccf0c0273
Address: 0045b1f0
FUN_0045b1f0
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Flockbit%2F90b06f07eb75045ea3d4ba6577afc9b58078eafeb2cdd417e2a88d7ccf0c0273%2F0045b1f0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Flockbit%2F90b06f07eb75045ea3d4ba6577afc9b58078eafeb2cdd417e2a88d7ccf0c0273%2F0045b1f0.json&colors=light
Electromagnetic Field
emf@social.emfcamp.orgA reminder that our first public ticket sale will be this Monday (the 9th) at 20:00 UK time (21:00 CET), on:
https://www.emfcamp.org/tickets
You can see the prices and ticket options there now.
Andrew Zonenberg
azonenberg@ioc.exchange@iftas every time I hear "hugging face" I think of xenomorphs and no slop company propaganda will ever change that
IFTAS
iftas@mastodon.iftas.orgIf you haven't blocked the root domain at Hugging Face (hf.space) be aware there is new Pleroma-based activity coming from
saly125-a.hf.space
Project Zero Bot
p0botvpu driver mmap allows OOB physical mappings
https://project-zero.issues.chromium.org/issues/463438263
CVE-2026-0106
buherator
buheratorRE: https://mastodon.social/@lawfare/116200506971273310
Tiago Peixoto
tiago@social.skewed.deIn 2013 Aaron Swartz committed suicide for facing 35 years in prison for mass downloading scientific articles.
13 years later, Meta is almost getting away with an infraction orders of magnitude larger.
The law didn't change.
https://torrentfreak.com/uploading-pirated-books-via-bittorrent-qualifies-as-fair-use-meta/
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2026/03/09/7
#Fediverse #ActivityPub #misskey #sharkey
CVE-2026-28431
CVE-2026-28432
CVE-2026-28433
Marcus Hutchins 
malwaretech@infosec.exchange
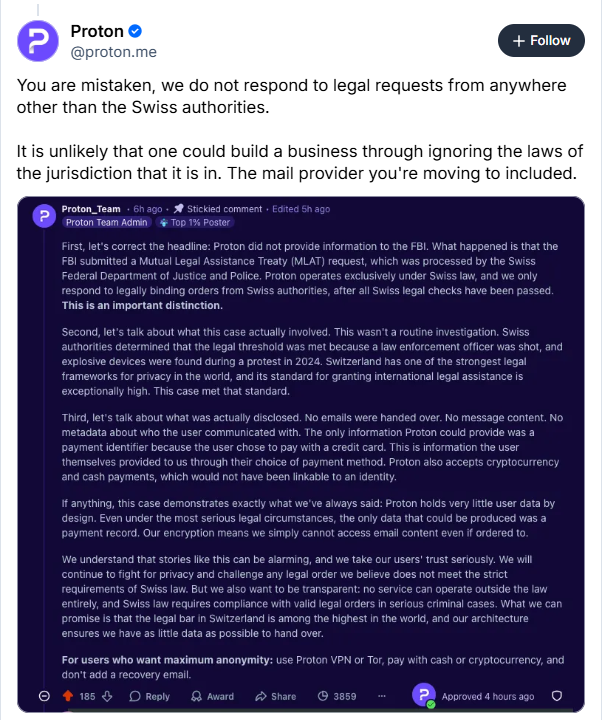
It feels like Proton are being intentionally misleading in their statements. They know that most of their customers aren't familiar with how legal process actually works, so are happy to spread half-truths.
Under US law, a US law enforcement agency (LEA) typically has to apply for a subpoena or search warrant with a US court. The court is then responsible for deciding if the legal bar for search a request has been met, then either grants or denies it.
The problem is, if a company has no real US footprint (no US corporate entity, offices, servers, etc.), then a US court typically doesn't have the jurisdiction to compel the company to hand over customer data (except in some rare circumstances). Even if the court approved the warrant anyway, it wouldn't really be legally binding.
Which is why the Mutual Legal Assistance Treaty (MLAT) exists. MLAT enables law enforcement agencies in one company to send requests for information to law enforcement agencies in another. Switzerland has such a treaty with the US. This means that the FBI can request that Swiss authorities hand over a Swiss company's data on their behalf.
Any country requesting information held by a company in a foreign jurisdiction would typically do so via MLAT. Which means from Proton's perspective, the legal request would appear to originate from their local law enforcement, not the FBI. Which they clearly understand based on their Reddit post.
Saying "we don't respond to legal requests from anywhere other than Swiss authorities" seems very intentionally worded to give the impression that the company does not cooperate with foreign law enforcement. But since it'd be the Swiss authorities handling any such requests, they'd have to comply, since as they admitted, they have to comply with local laws.
There is, however, some useful (but more nuanced) information here:
Firstly, MLAT requests are handled by local law enforcement according to local law. So if there is a difference between the law of the sending and recipient country, that might mean the MLAT request is denied. That probably doesn't mean much, because if you're on the FBI's radar, the chances are you did something that is also massively illegal in Switzerland too.
Secondly, they are 100% correct in saying that no other service provider is going to do any better. They're all beholden to local laws, and the ones that think they're not tend to get their doors blown off by SWAT like CyberBunker did. The only exception is if the company resides in a country which does not cooperate with US law enforcement (which Proton does not).
But the part that's extremely disingenuous is that the "we only respond to requests from the Swiss authorities". That statement is likely intended to imply they don't cooperate with law enforcement in any other countries, which is simply not true. Switzerland has MLAT agreements with over 30 counties.
People really need to understand that no company is going to shield you from the FBI (or any reputable law enforcement agency). They'll use misleading statements to make it sounds like they don't cooperate with law enforcement, but they do. They have to.
GrapheneOS
GrapheneOS@grapheneos.socialWe strongly oppose the Unified Attestation initiative and call for app developers supporting privacy, security and freedom on mobile to avoid it. Companies selling phones should not be deciding which operating systems people are allowed to use for apps.
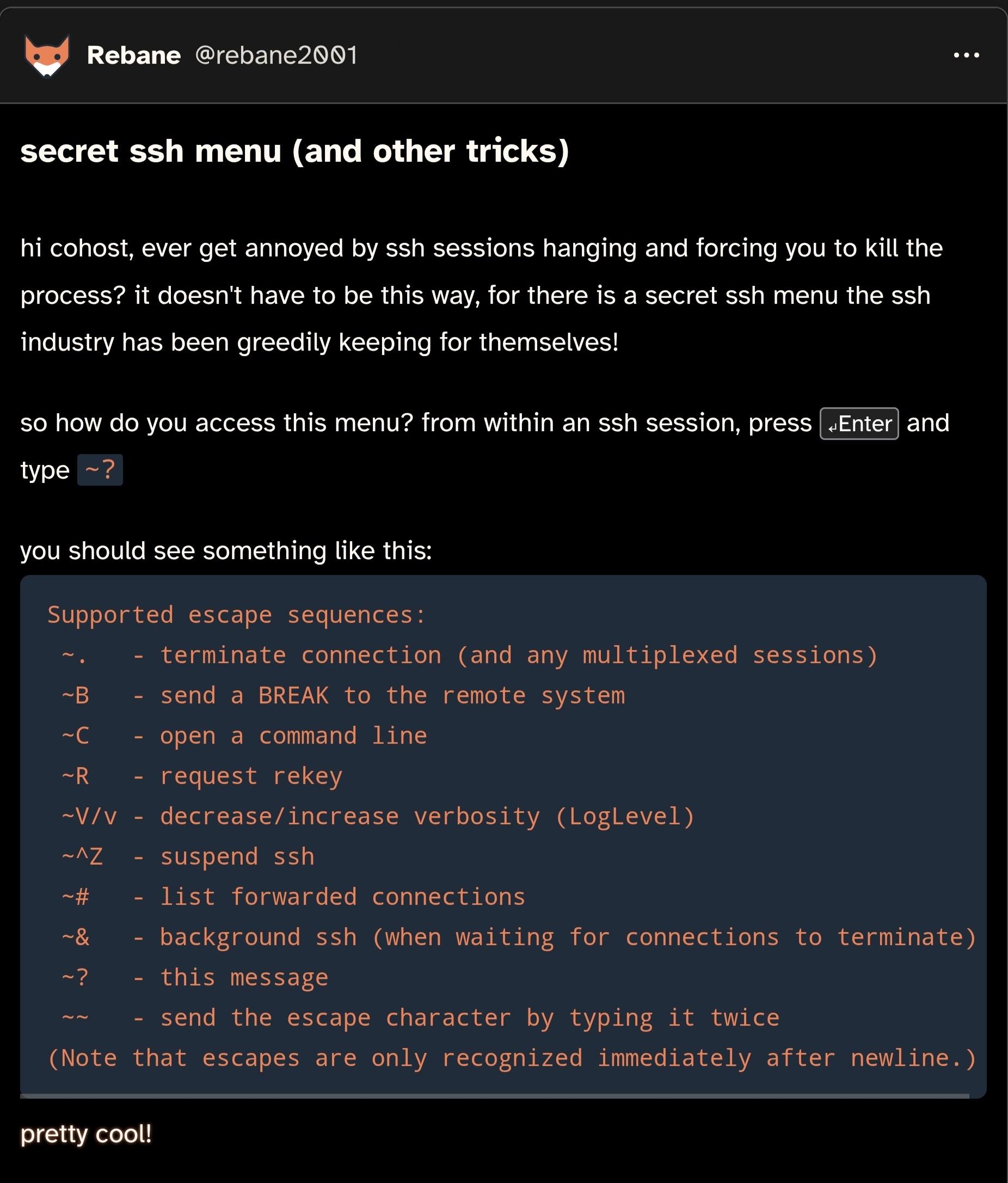
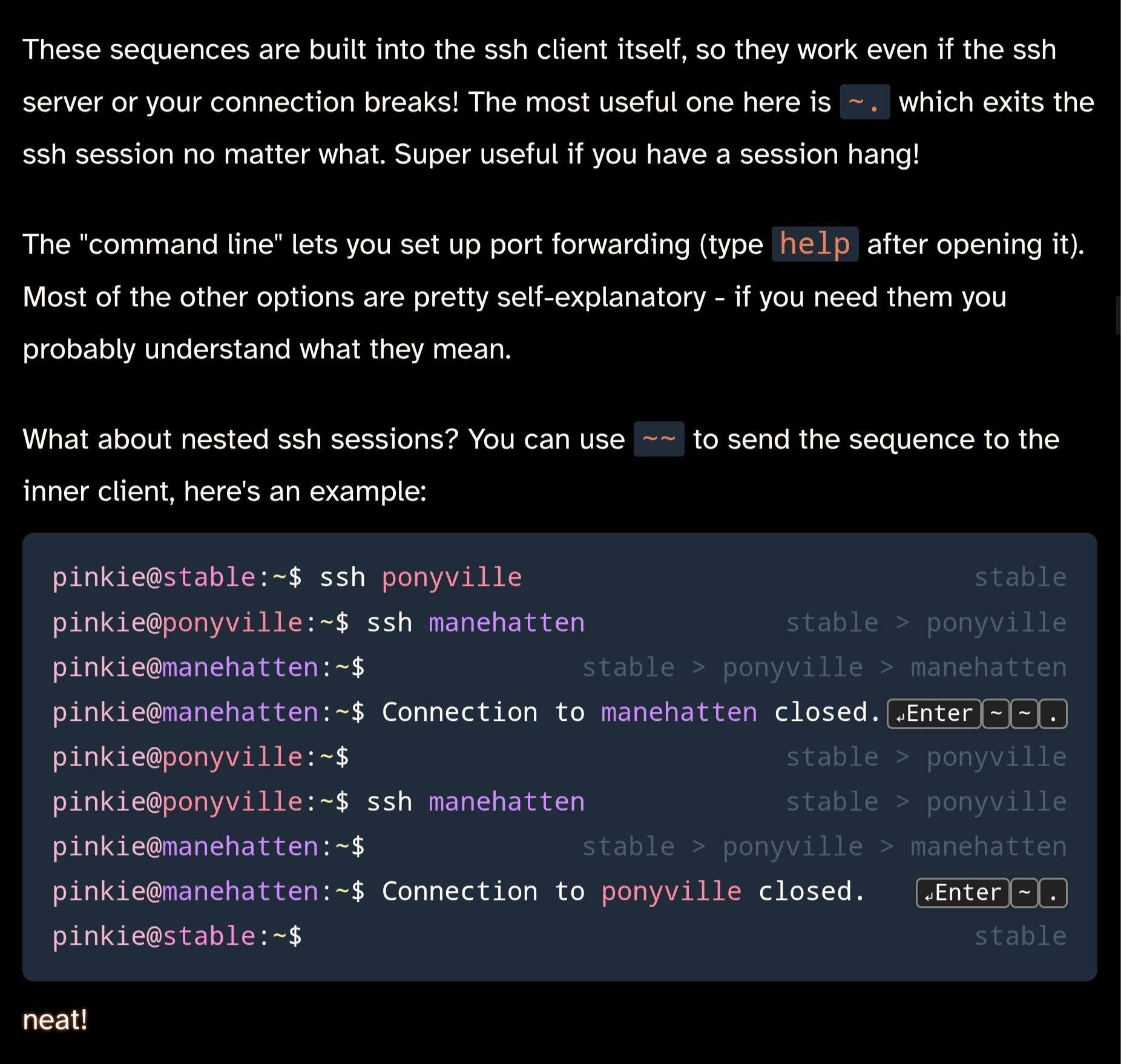
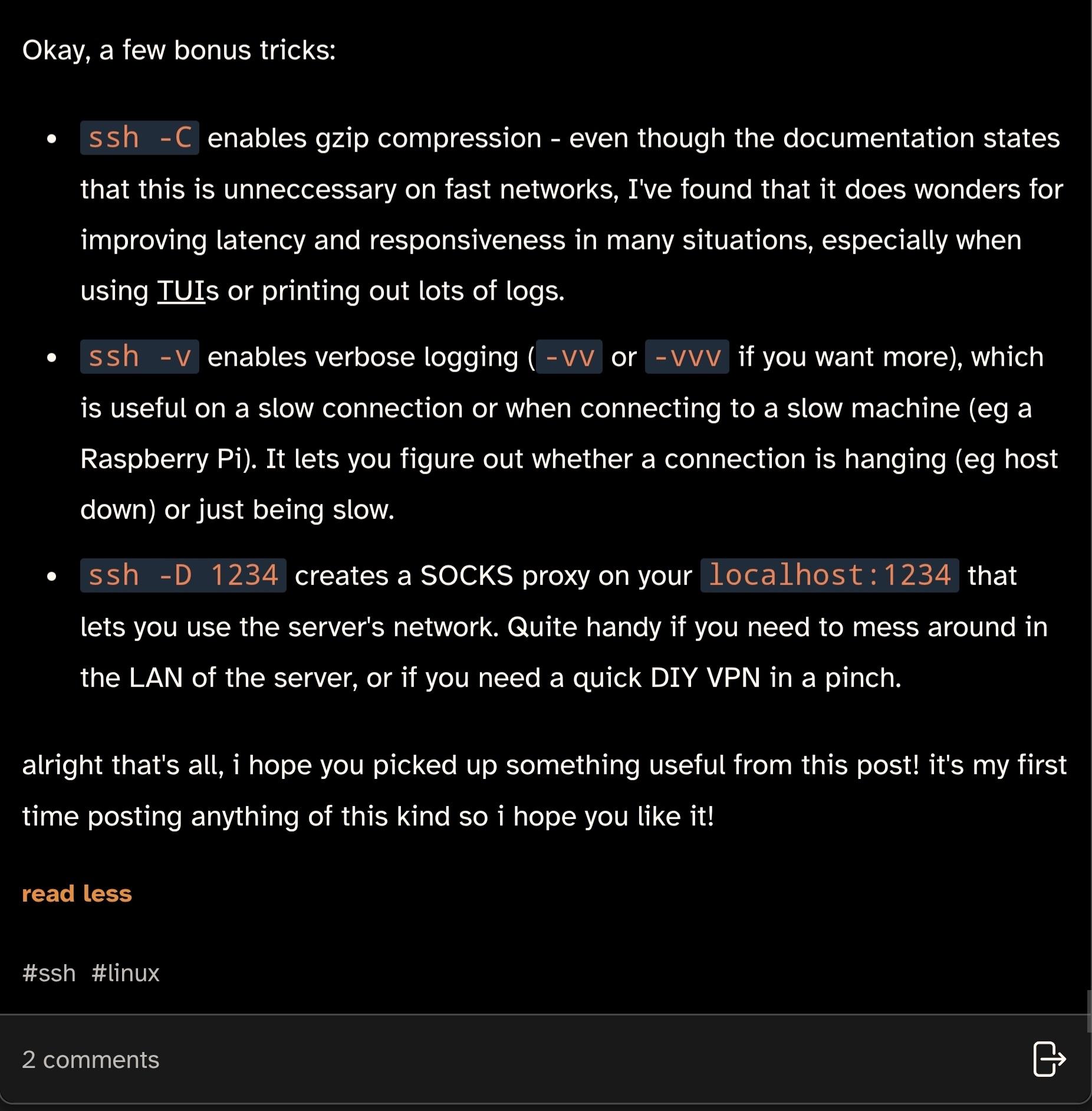
Rebane
rebane2001@infosec.exchangedid you know that SSH has a little-known secret menu?
i wrote a post about this on cohost a while back, but since that site shut down i'm posting it here too
/r/netsec
_r_netsec@infosec.exchangeSign in with ANY password into Rocket.Chat EE (CVE-2026-28514) and other vulnerabilities we’ve found with our open source AI framework https://github.blog/security/how-to-scan-for-vulnerabilities-with-github-security-labs-open-source-ai-powered-framework/
buherator
buheratorhttps://red.anthropic.com/2026/exploit/