Posts
2586Following
669Followers
1495allison
aparrish@friend.camp@KinkyKobolds this is the best explanation i've read for why anyone who is monetarily backed by the tech industry is feeling pressured to include generative models in everything https://gauthierroussilhe.com/en/articles/how-to-use-computing-power-faster
pancake 
pancake@infosec.exchange
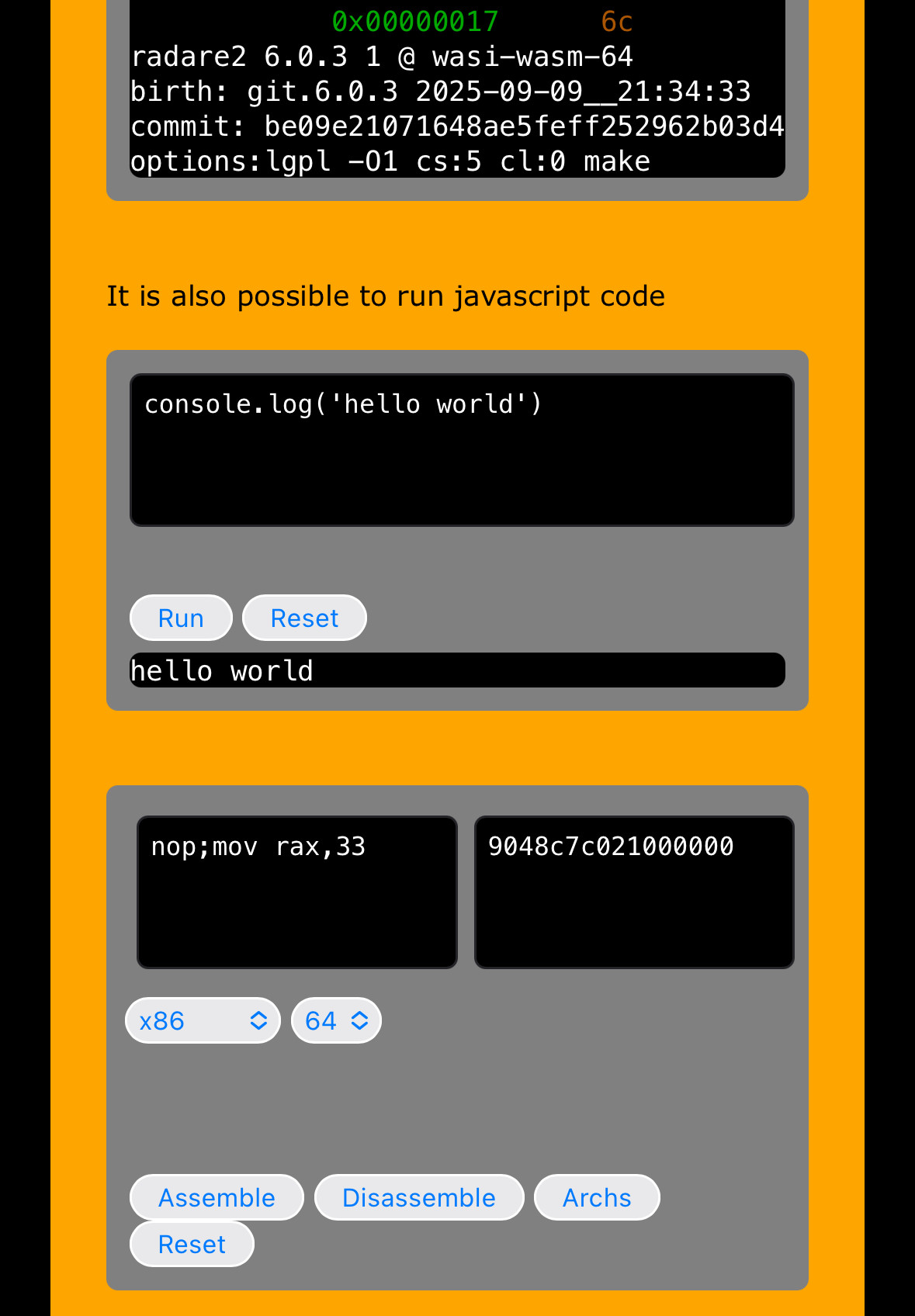
Just pushed the last #webassembly build from git in the r2wasm test website. Testing, feedback and patches are welcome! Let’s make the web a solid foundation for r2 users too https://radareorg.github.io/r2wasm/index.html
buherator
buheratorhttps://curl.se/docs/CVE-2025-9086.html
Found via Google Big Sleep:
https://googleprojectzero.blogspot.com/2024/10/from-naptime-to-big-sleep.html
daniel:// stenberg://
bagder@mastodon.socialThere's going to be more speak about AIs finding genuine security problems soon.
Google Big Sleep found one in #curl that we reveal tomorrow.... in about eight hours. (but no, we don't know how much was AI and how much was human or how many false positives they had to wade through to get there etc maybe they will let us know later?)
Allison Husain
ezhes_@mastodon.onlineMemory Integrity Enforcement is the culmination of a truly incredible amount of work :)
While there's so much to love, one of my favorite pieces was getting to bring kalloc_type-style isolation to out-of-bounds accesses on both the architectural and speculative path. This lets us both mitigate a variety of Spectre v1 style attacks and break the reliable exploitation of some of the most powerful first-order memory corruption primitives (arb offset OOB R/W).
https://security.apple.com/blog/memory-integrity-enforcement/
Dino A. Dai Zovi
dinodaizovi@bird.makeupEvery minute that your security team is spending on things that aren't a risk is a minute that they *aren't* spending on things that *are* a risk.
rev.ng
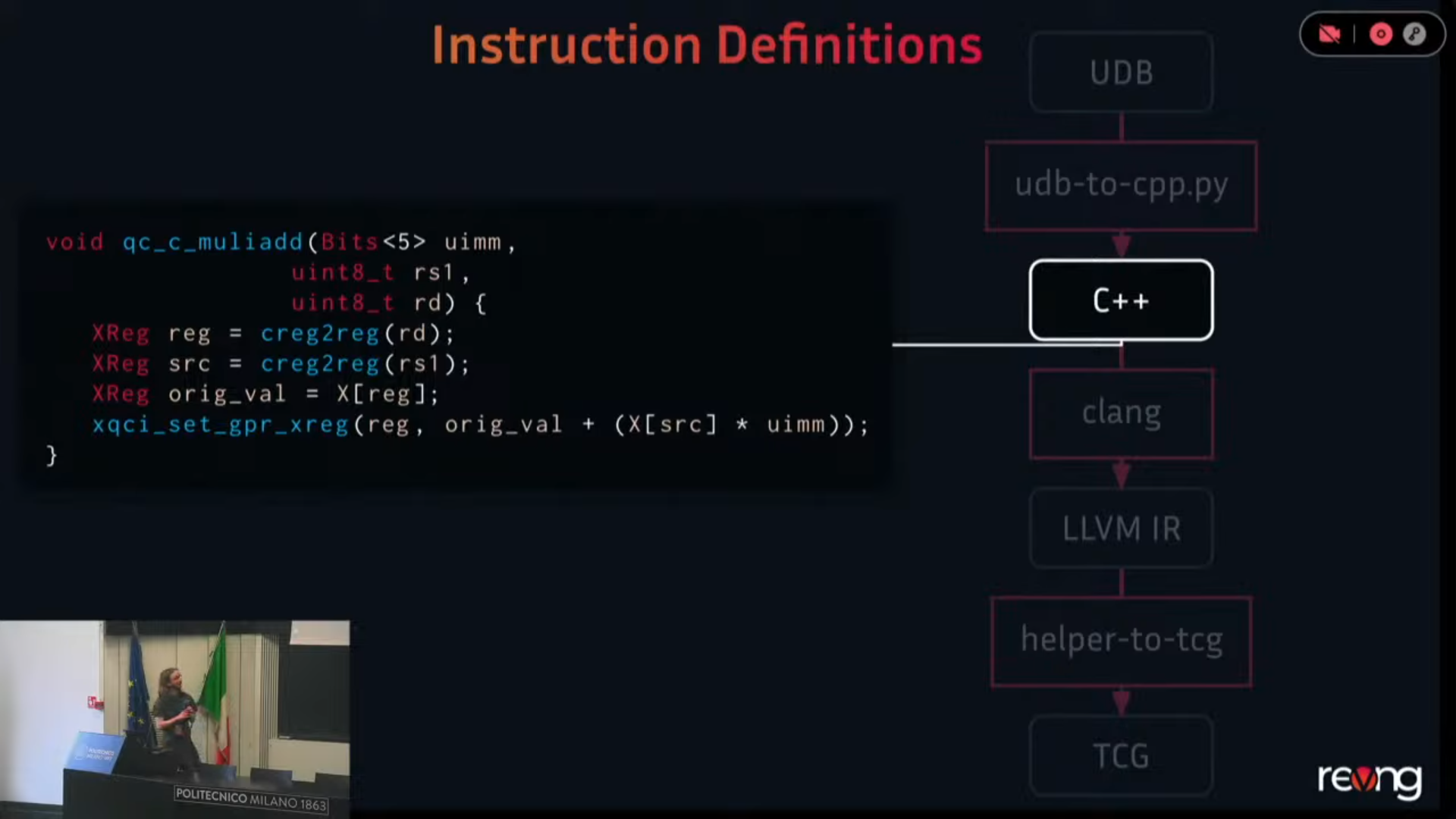
revng@infosec.exchange📢 Aaand here is Anton's talk about QEMU+RISC-V at KVM Forum 2025!
Automatic Frontend Generation for RISC-V Extensions
Video: https://www.youtube.com/watch?v=GPSKsZmu_S8&t=1297s (21:37)
Code: https://github.com/revng/udb-to-qemu/ 🦾
DebugPrivilege
debugprivilege@bird.makeupNew blog post of me analyzing a crash dump with the bugcheck 0x9F. Root cause was a power IRP timeout in RAS SSTP during a device removal. The post walks PnP locks, the stuck IRP, and more, including my thought process. Check it out here: https://medium.com/@Debugger/power-irp-timeout-in-ras-sstp-causes-blue-screen-0x9f-during-sleep-e59cb76f291c
eShard
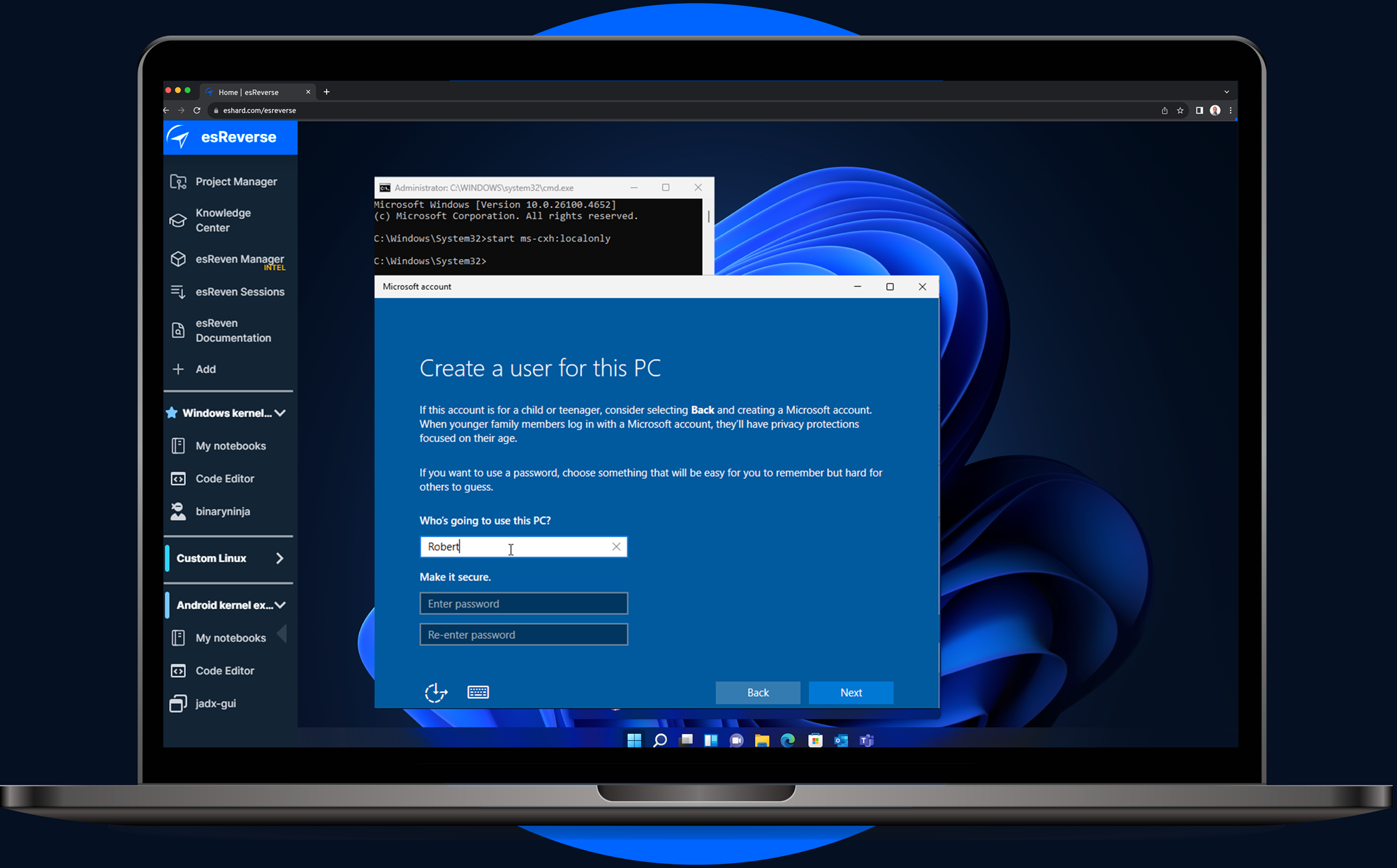
eshard@infosec.exchangeWindows 11 in esReverse. 💻 Full system emulation to boot, record, and rewind your analysis from kernel to userland.
Read the guide: https://eshard.com/posts/windows11-esreverse-emulation #windows #emulation #reverseengineering
p0pcycle
pamoutaf@infosec.exchange@Blackhoodie_RE X @hexacon_fr happening again! This time it’s my turn to give back 🥹
Use the registration link below to sign up to 4 days of free training given by Sonia, @naehrdine and myself !
Kevin Beaumont
GossiTheDog@cyberplace.socialThat NodeJS supply chain hack incident is amazing because the threat actor(tm) got RCE access to like a billion devices and ran the world’s shittest Etherum dumper.
Imagine if they had done reverse shells instead, or automated lateral movement to ransomware deployment NotPetya style.
The thing that saved companies here was the threat actor was incompetent crypto boy, nothing more.
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-39q3-f8jq-v6mg
CVE-2025-9951
Ars Technica
arstechnica@mastodon.socialAll 54 lost clickwheel iPod games have now been preserved for posterity
Finding working copies of the last few titles was an "especially cursed" journey.
https://arstechnica.com/gaming/2025/09/all-54-lost-clickwheel-ipod-games-have-now-been-preserved-for-posterity/?utm_brand=arstechnica&utm_social-type=owned&utm_source=mastodon&utm_medium=social
Extreme Electronics
Extelec@mstdn.social2nd of to nights fixes. A 139 year old electrotherapy machine.
Three problems, a brush wasn't contacting the rotor (bent back into shape). The handles were suffering from corrosion (cleaned), and the horseshoe magnet had lost most of its power(see 2nd image).
Works well now... no wonder they were nervous :)
buherator
buheratorhttps://banyaszvonat.github.io/breaking-videogames/2025/09/07/hidden-functionality-in-spyro-the-dragon.html
#Disgaea #GameHacking
Anderson Nascimento
andersonc0d3@infosec.exchangeA VM tuning case study: Balancing power and performance on AMD processors
Hex-Rays SA
HexRaysSA@infosec.exchange📣 IDA 9.2 is here!
➥ Smarter Go decompilation
➥ New Dynamic Xref Graph & Xref Tree
➥ Debugger & UI upgrades
➥ Expanded processor support (ARM, RISC-V)
➥ And more...
Explore the full release here: https://hex-rays.com/blog/ida-9.2-release
buherator
buheratorhttps://lucasteske.dev/2025/09/running-code-in-pax-machines