Posts
2580Following
628Followers
1402buherator
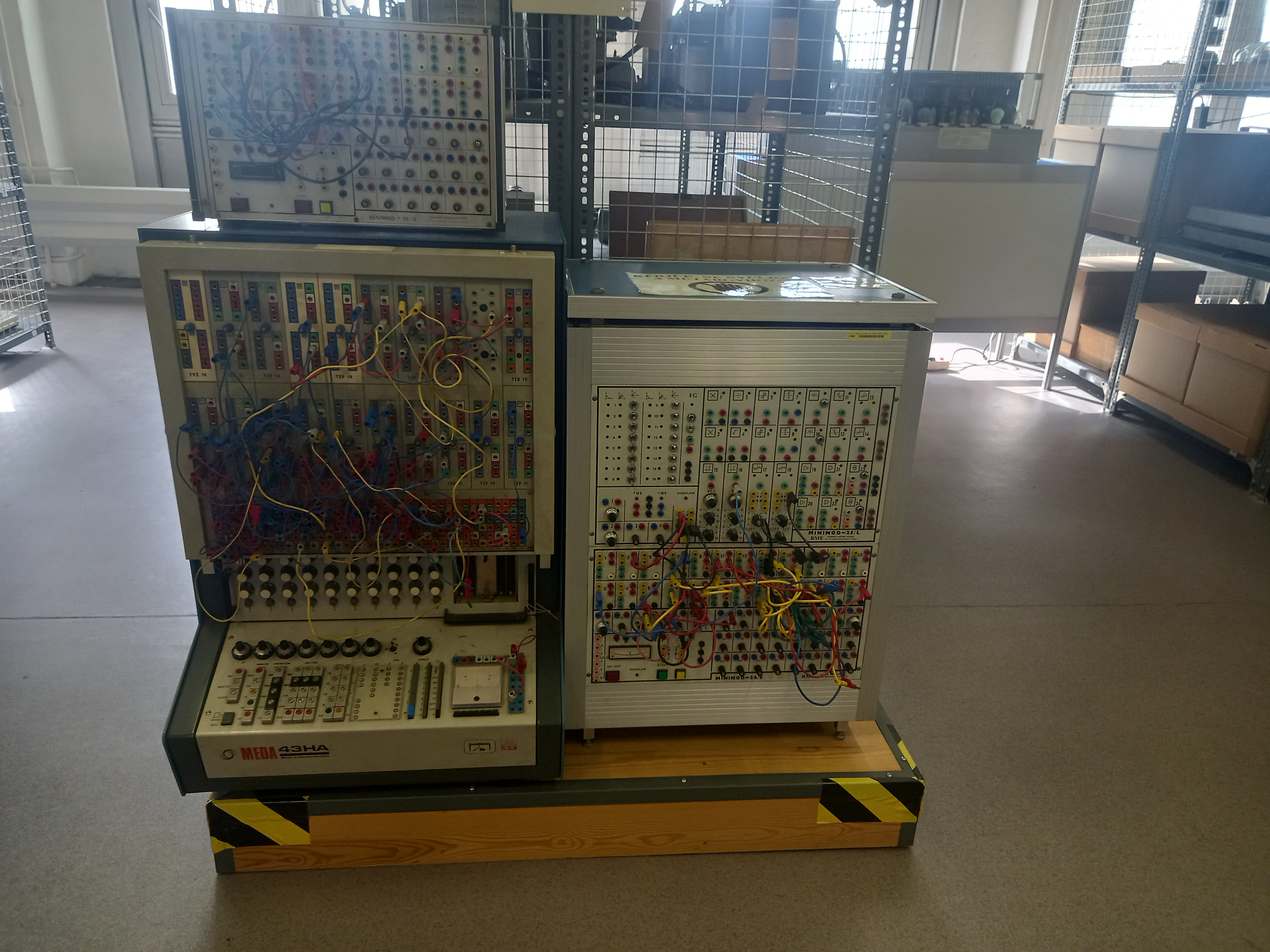
buheratorhttps://muzeuldecalculatoare.ro/2020/06/11/the-meda-43-analog-hybrid-computer/
Synacktiv
synacktiv@bird.makeupThe FastCGI library, mostly used in embedded equipment, was vulnerable for decades to an integer overflow over the IPC socket in 32-bits architecture. Check out how @shiropycatchown found it and exploited it for RCE!
https://www.synacktiv.com/en/publications/cve-2025-23016-exploiting-the-fastcgi-library
Mike Stone
mike@fosstodon.orgI know Chrome is the browser everybody loves to hate, but I think most would agree this would be very bad.
RE//verse Conference
REverseConf@infosec.exchangeIf you haven't seen it yet, make sure to check out another great RE//verse talk, Code reuse and attribution: best friends and worst enemies from Max 'Libra' Kersten (https://youtu.be/GPT1IksBkaI)
Alex Plaskett
alexjplaskett@bird.makeupRE//verse 2025 videos
https://www.youtube.com/playlist?list=PLBKkldXXZQhAW5QKjUQOUWaMAHAxDtgio
Ryan Castellucci 
ryanc@infosec.exchange
Coworker: ...and the IP address are compared with a string match.
Me: grinning manically
Coworker: Why are you looking at me like that?
Me: Open up a terminal and type ping 4.2.514 and hit enter.
Coworker: ...what's the fourth number?
Me: grin widens Just hit enter.
Coworker: WTF!?
testssl.sh 
testssl@infosec.exchange
testssl.sh 3.2.0 is finally out, see https://github.com/testssl/testssl.sh/releases/tag/v3.2.0 or just https://testssl.sh .
Changelog see https://github.com/testssl/testssl.sh/blob/3.2/CHANGELOG.md .
JA Westenberg
Daojoan@mastodon.socialGoogle is what happens when a system forgets why it was built but remembers how.
HN Security
hnsec@infosec.exchangeWe have identified some security vulnerabilities (CVE-2025-1731) in Zyxel USG FLEX H Series firewall appliances, that allow local users with access to a Linux OS shell to escalate privileges to root.
https://security.humanativaspa.it/local-privilege-escalation-on-zyxel-usg-flex-h-series-cve-2025-1731
#Zyxel #VulnerabilityResearch #CoordinatedDisclosure
Phrack
phrack@haunted.computer🐣 HAPPY EASTER FROM PHRACK 🐣
SPECIAL CrackMe Easter-2025 Challenge ONLINE NOW.
👉ZGlnICtzaG9ydCBlZ2c/Pz8/LnBocmFjay5vcmcgVFhU👈
Go find the EGG by solving the riddle :>
buherator
buheratorhttp://blog.quarkslab.com/auditing-moodles-core-hunting-for-logical-bugs.html
Kevin Beaumont
GossiTheDog@cyberplace.socialIf you heard about that hacking of the voices of traffic light crosswalks in the US recently, the root cause is the devices all had the password '1234' and an app to reprogram the devices was on the Apple app store.
https://www.theregister.com/2025/04/19/us_crosswalk_button_hacking/
buherator
buheratorhttps://jericho.blog/2025/04/22/reporting-on-the-ibm-2025-report/
MITRE ATT&CK
mitreattack@infosec.exchangeATT&CK v17 is now live! This release includes the first version of the ESXi platform, a pile of defensive upgrades, and fresh content across Enterprise, Mobile, and ICS.
Check out our blog post describing the changes by Amy Robertson & @whatshisface at https://medium.com/mitre-attack/attack-v17-dfb59eae2204
Siguza
siguza@infosec.spaceThe year is 2031.
Chrome development has accelerated even more under OpenAI, to the point where every tab now needs 16GB of RAM.
Mozilla has been restructured and is now a joint venture between IBM and Oracle, aiming to put the "Java" back in "JavaScript" and some vague statements about quantum computing.
Opera's parent company has been absorbed by Tencent and now requires sign-in with a China mainland phone number.
Microsoft has rebranded Edge to "Copilot for Web" and is gradually removing the last hacks that allow manual text input. Amazon and Meta are currently lobbying the government to force Microsoft to sell Copilot to them. It's not clear what "Copilot" they're talking about, but that may be intentional.
Apple's Safari has escaped regulatory scrutiny for the most part, but its market share is slow to recover after half a decade of an "Apple Intelligence first" user interface that Apple has now finally reversed course on.
n00py
n00py1@bird.makeupToday I found an unauthenticated Docker API endpoint, and couldn't find a working exploit script, so I made one. It exfils out-of-band if you can't get output (I couldn't) and auto-cleans up after itself.
Nessus: Docker Remote API Detection