Posts
2579Following
628Followers
1403buherator
buheratorI'm wondering how good LLM's are (or can be) at coming up with the data structure in the first place.
buherator
buheratorAre there any (case-)studies about using LLM's to create data models?
Heads-up if you or your target run IBM Hardware Management Console.
https://www.ibm.com/support/pages/node/7231507
sev:CRIT 9.3 - CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
IBM Hardware Management Console - Power Systems V10.2.1030.0 and V10.3.1050.0 could allow a local user to execute commands locally due to improper validation of libraries of an untrusted source.
https://nvd.nist.gov/vuln/detail/CVE-2025-1950
https://www.ibm.com/support/pages/node/7231389
sev:HIGH 8.4 - CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
IBM Hardware Management Console - Power Systems V10.2.1030.0 and V10.3.1050.0 could allow a local user to execute commands as a privileged user due to execution of commands with unnecessary privileges.
buherator
buheratorhttps://www.youtube.com/watch?v=Zt5AOR5zLhM
Very nice presentation about #IBMi security, including post-exploitation steps and lateral movement via pass-the-hash!
buherator
buheratorhttps://pivot-to-ai.com/2025/04/18/reasoning-ai-is-lying-to-you-or-maybe-its-just-hallucinating-again/
Soatok Dreamseeker
soatok@furry.engineerLet's talk about xPal, which purports to be an encrypted messaging app. https://xpal.com
Anyone that reads my blog probably already knows where this is going.
If this post accidentally reaches escape velocity and people that don't know me find it: Hi, I'm a furry cryptography nerd. Usually when I talk about so-called private apps, it's to disclose vulnerabilities in them.
(Today, I just don't have the damn energy to do a formal write-up.)
Let's start with how they market their app.
Lukasz Olejnik
LukaszOlejnik@mastodon.socialInteresting AI Act case in Europeaj Court of Justice may decide if just about any algorithms, including non-AI ones, are subject to the AI Act (regulation about Artificial Intelligence). It would be a fascinating expansion of the regulation applications. https://curia.europa.eu/juris/showPdf.jsf?text=&docid=298104&pageIndex=0&doclang=PL&mode=lst&dir=&occ=first&part=1&cid=12213338
buherator
buheratorhttps://github.com/moreveal/hash-resolver
buherator
buheratorhttps://scribe.rip/@cy1337/tracing-data-flow-with-pcode-f879278d9fc1
#Ghidra #ReverseEngineering
buherator
buheratorhttps://msrc.microsoft.com/blog/2025/04/zero-day-quest-2025-1.6-million-awarded-for-vulnerability-research/
Lukasz Olejnik
LukaszOlejnik@mastodon.socialRussia is quietly rewriting reality — but not through tanks or troops, but by feeding disinformation and propaganda into the tools people may increasingly trust to understand the world: AI chatbots. It's gaming of the system, feeding propaganda in ways that people might never know what’s happening. Efforts to influence chatbot results are growing, as former SEO marketers now use "generative engine optimization" (GEO) to boost visibility in AI-generated responses https://www.washingtonpost.com/technology/2025/04/17/llm-poisoning-grooming-chatbots-russia/
yossarian (1.3.6.1.4.1.55738)
yossarian@infosec.exchangei'm very excited about this new work my team at @trailofbits is doing: we're building an ASN.1 API for PyCA Cryptography, giving users direct access to the same memory-safe, high-performance DER parser that Cryptography already uses for X.509:
https://blog.trailofbits.com/2025/04/18/sneak-peek-a-new-asn.1-api-for-python/
buherator
buheratorhttps://www.darknavy.org/blog/a_first_glimpse_of_the_starlink_user_ternimal/
buherator
buheratorhttps://spaceraccoon.dev/cybersecurity-antipatterns-busywork-generators/
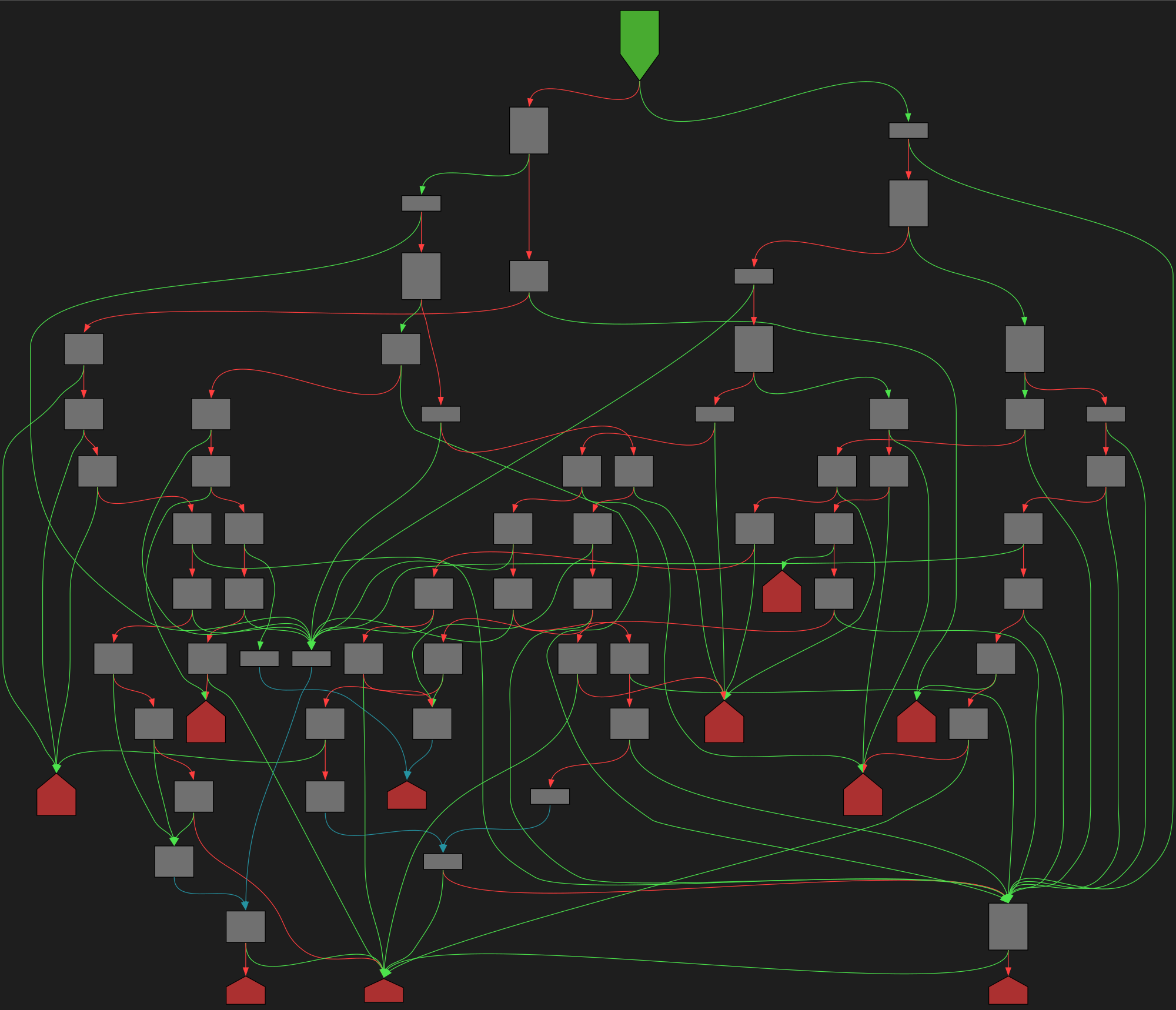
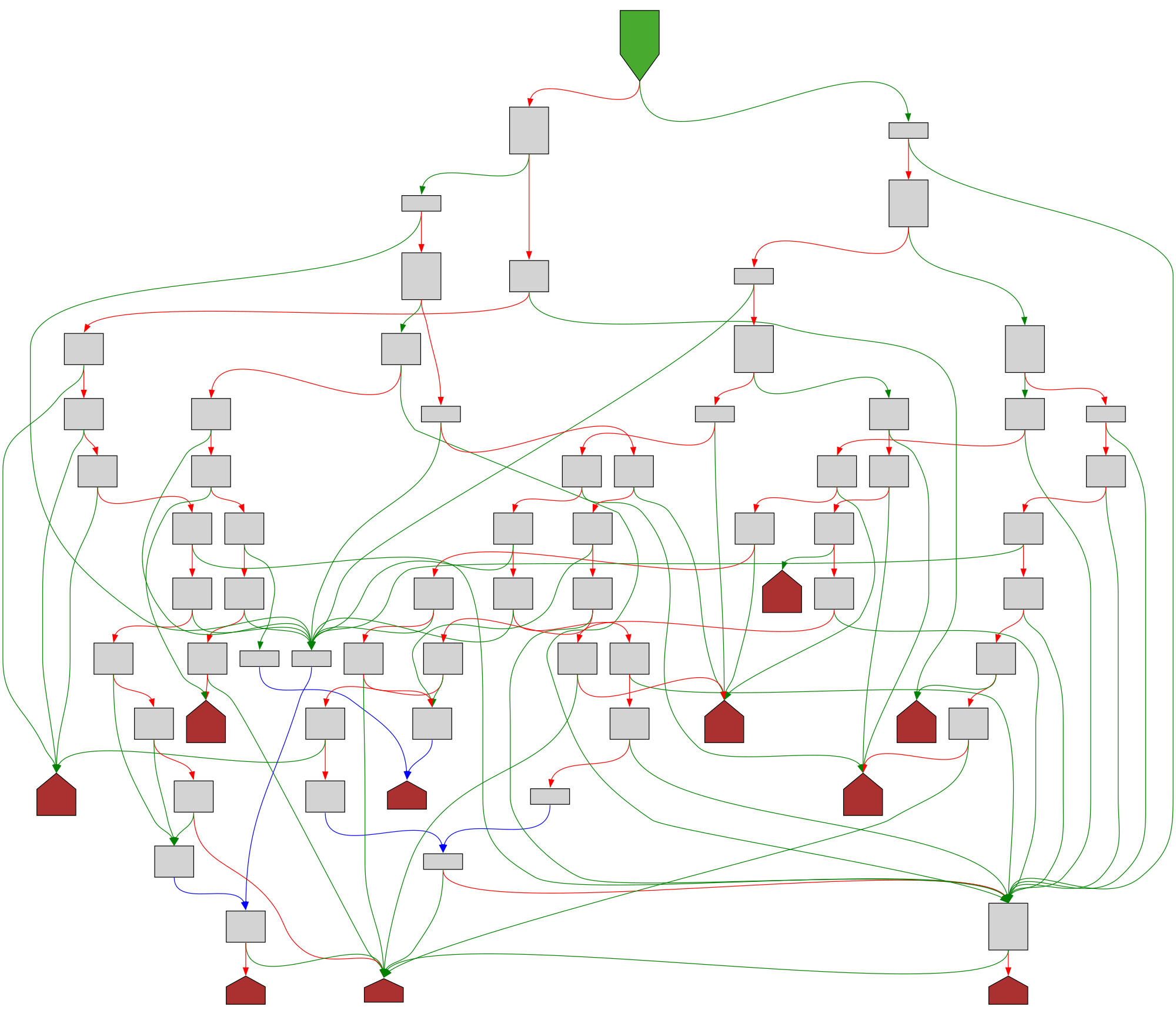
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a287bec
yy_destructor
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a287bec.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a287bec.json&colors=light
Alex Plaskett
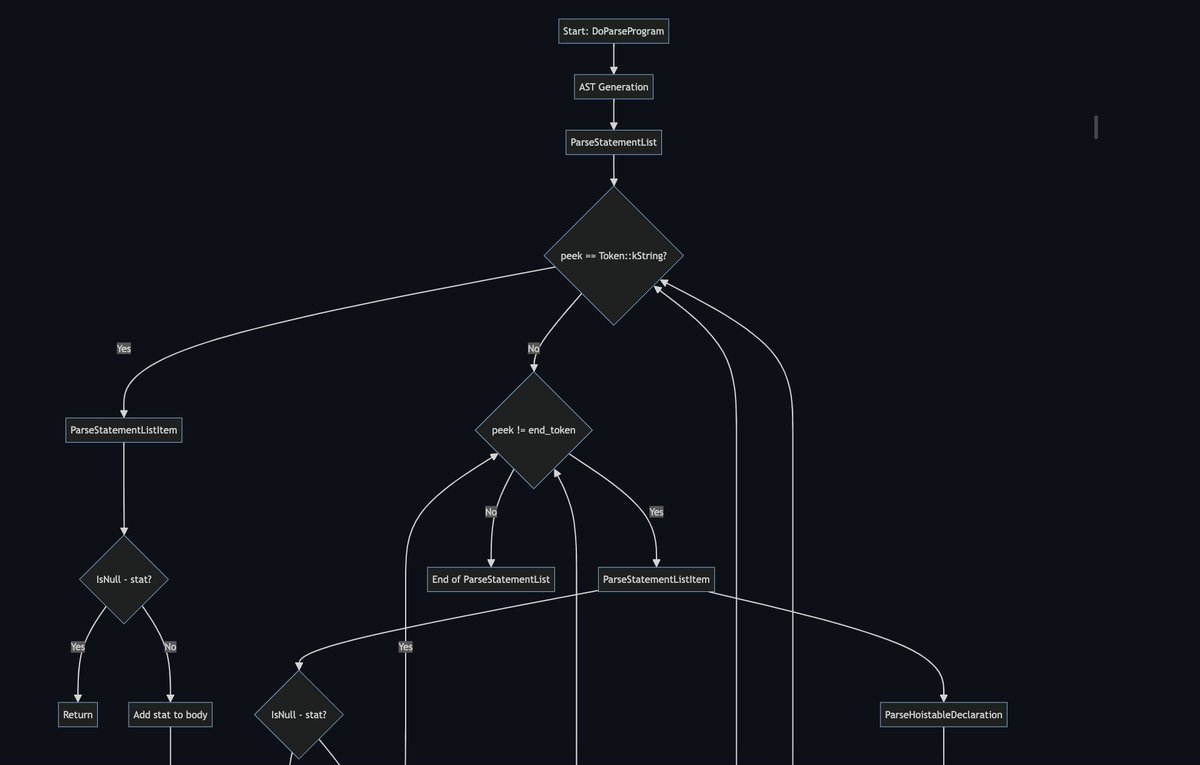
alexjplaskett@bird.makeupA blog explaining V8 Parser Workflow with a case study by w1redch4d
Alex Plaskett
alexjplaskett@bird.makeupExploiting the Nespresso smart cards for fun and profit coffee
Seth Larson
sethmlarson@fosstodon.orgVery good thread from @inthehands, LLMs cement the patterns of today and actual engineering and long-term problem solving require slow careful iteration and improvement.