Posts
3104Following
706Followers
1551buherator
buheratorhttps://en.wikipedia.org/wiki/Rule_of_law
It's so weird to see people (esp. in the US) acting as if humanity didn't have hundreds or even thousands of years of experience about how governance should (not) work.
Ange
Ange@mastodon.socialIn ~1h, we’ll explore the awesome and clever DOOM.PDF!
https://www.youtube.com/live/t17joAiWBkE?si=clV3nvyFZ5DjKQ5e
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250117-00/?p=110777
Rust made me see cases like this in a much different light!
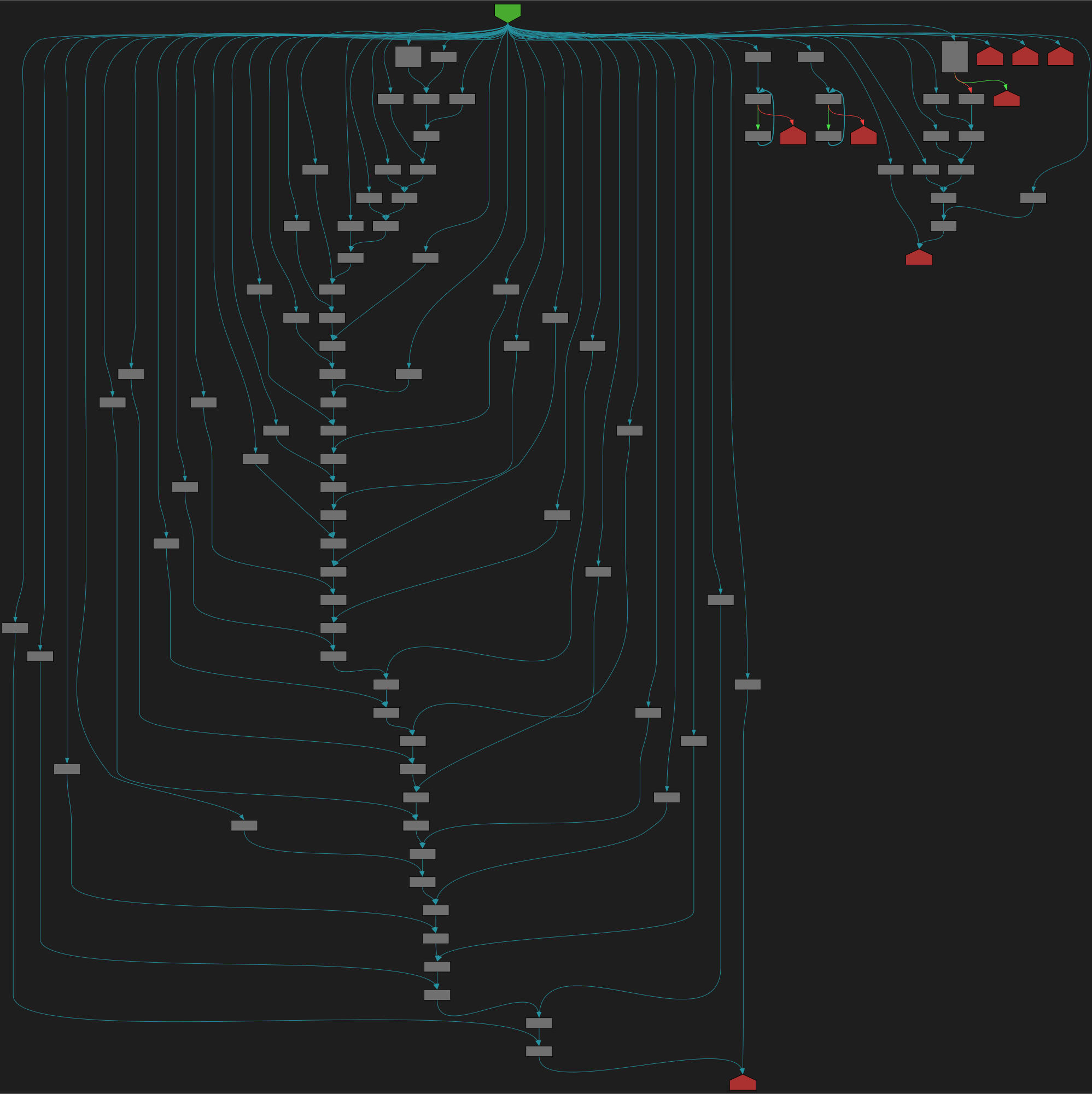
CFG Bot 🤖
cfgbot@mastodon.socialProject: microsoft/TypeScript https://github.com/microsoft/TypeScript
File: src/compiler/utilities.ts:3549 https://github.com/microsoft/TypeScript/blob/cbac1ddfc73ca3b9d8741c1b51b74663a0f24695/src/compiler/utilities.ts#L3549
function isExpressionNode(node: Node): boolean
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fcompiler%2Futilities.ts%23L3549&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fcompiler%2Futilities.ts%23L3549&colors=light
Colin Finck
ColinFinck@hachyderm.ioFor those of you who are also deep into Windows #reverseengineering, #bootloaders, and #WinDbg: My first blog post on researching the Windows driver load order and all its quirks is out, beginning with some WinDbg fundamentals: https://colinfinck.de/posts/nt-load-order-part-1/
Molly White
molly0xfff@hachyderm.ioThe TikTok ban, the Musk Twitter takeover, the Facebook moderation policy changes, the Republicans’ rapidly intensifying crackdowns on speech... let these be the proof you needed to move anything you care about online to a space you control.
Digital sovereignty is more important than ever.
buherator
buheratorlegally exhausted mouse
algernon@come-from.mad-scientist.clubROFLMAO.
Claude decided to crawl one of the sites on my new server, where known bots are redirected to an iocaine maze. Claude has been in the maze for 13k requests so far, over the course of 30 minutes.
I will need to fine tune the rate limiting, because it didn't hit any rate limits - it scanned using 902 different client IPs. So simply rate limiting by IP doesn't fly. I'll rate limit by (possibly normalized) agent (they all used the same UA).
Over the course of this 30 minutes, it downloaded about ~300 times less data than if I would've let it scrape the real thing, and each request took about the tenth of the time to serve than the real thing would have. So I saved bandwidth, saved processing time, likely saved RAM too, and served garbage to Claude.
Job well done.
Angus McIntyre
angusm@mastodon.socialI knew #AI would come for all our jobs eventually, but I really thought that Holocaust denial would be safe for a little while longer.
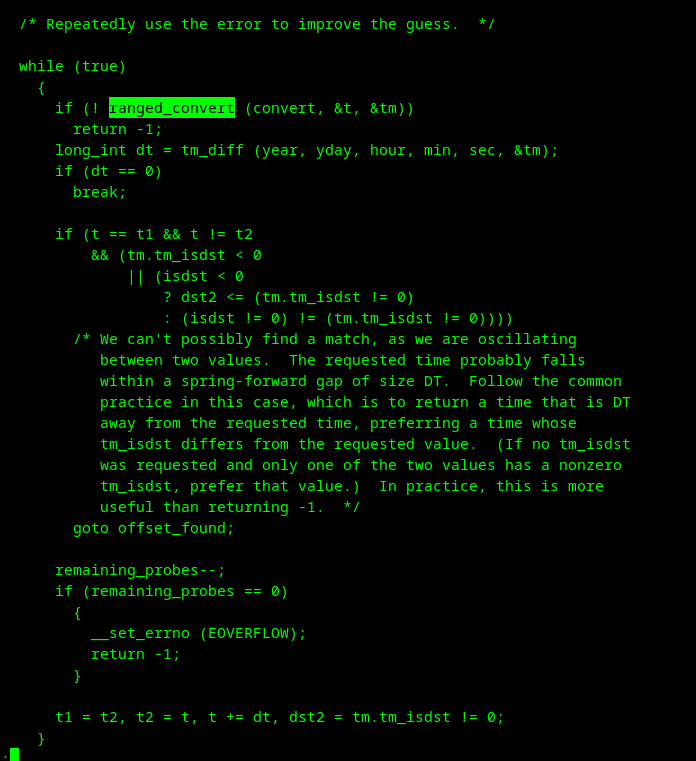
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgAlso for your mental health, I recommend never reading the source code for the various implementations of mktime() and strptime(). The authors really try their best, but on reading that, you worry how anything ever works. https://github.com/bminor/glibc/blob/master/time/mktime.c
mort
mort@fosstodon.orgOkay this is wild: I just noticed that changing 'PasswordAuthentication' to 'no' in /etc/ssh/sshd_config is no longer enough to disable password authentication in #ubuntu. That's because Ubuntu Server now by default creates a sshd_config.d/50-cloud-init.conf file which contains 'PasswordAuthentication yes' which takes priority over sshd_config.
I would've unknowingly left password auth on if I hadn't double checked.
Why?
More: https://askubuntu.com/questions/1516262/why-is-50-cloud-init-conf-created
buherator
buherator"so the decryption of the private key and mail files happens on your own computer (or in your browser). " - this a periodic reminder that browser-based clients download the code required to "securely" handle the user keys from the same entity (in this case Proton) that we want to hide the keys from...
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgSo how hard could it be to convert `Fri, 17 Jan 2025 06:07:07` in UTC into a UNIX epoch time_t timestamp, in C or C++? Quite hard. Many things that you'd think would work actually don't. Here I present solutions (with running code), and a little tour through 'struct tm', 'time_t', 'mktime' and 'strptime':
https://berthub.eu/articles/posts/how-to-get-a-unix-epoch-from-a-utc-date-time-string/
buherator
buheratorhttps://neodyme.io/en/blog/bitlocker_why_no_fix/