Posts
3059Following
703Followers
1553Nina Kalinina
nina_kali_nina@tech.lgbtI love reverse-engineering because it allows me to dismantle structures of control.
Blacktop
blacktop__@bird.makeupFirst attempt at building macOS 26.0 XNU as a LIBRARY?! 👩🔬
Check it out! 🎉
https://github.com/blacktop/darwin-xnu-build/releases/download/v26.0/xnu-lib-26.0.tar.gz
CFG Bot 🤖
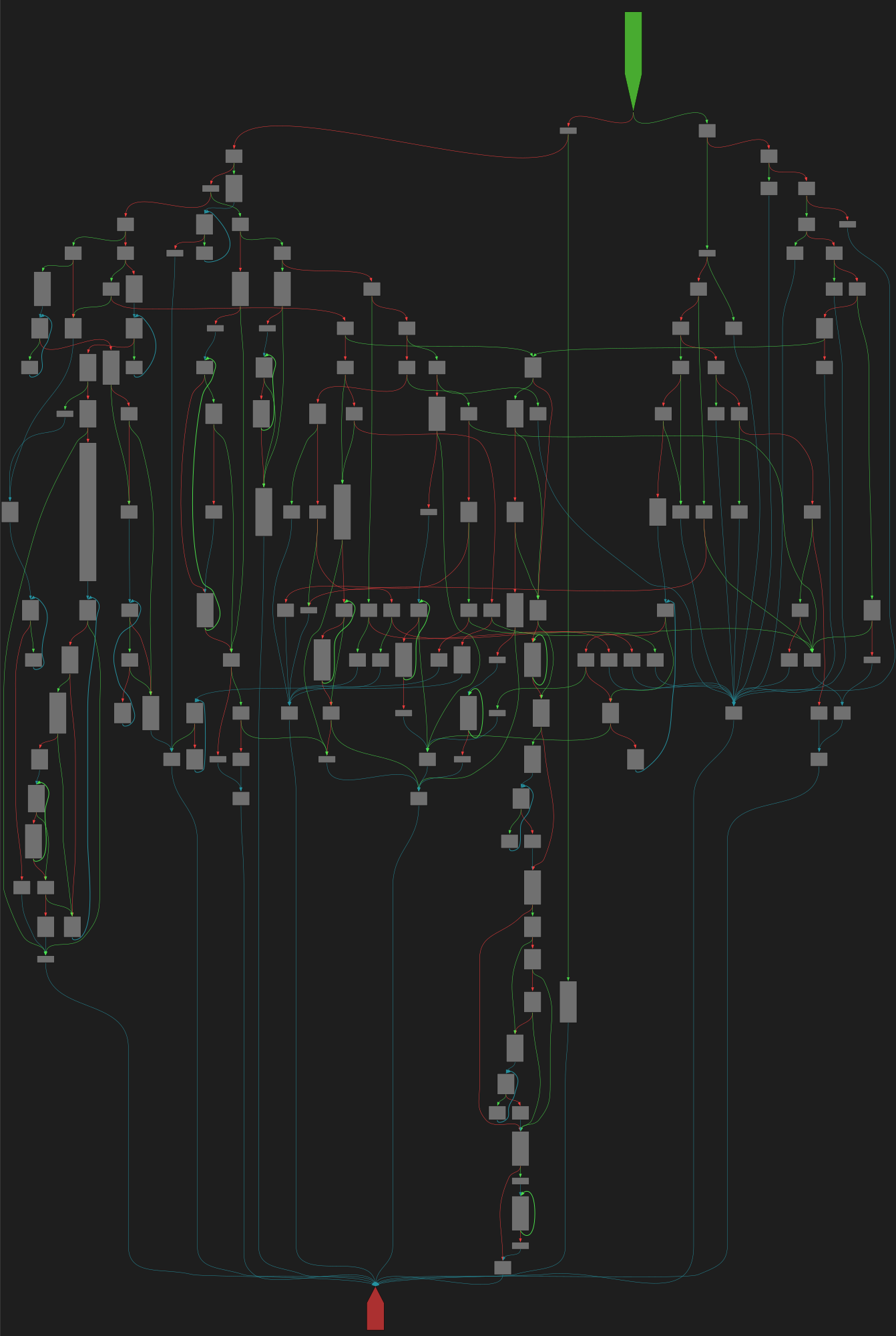
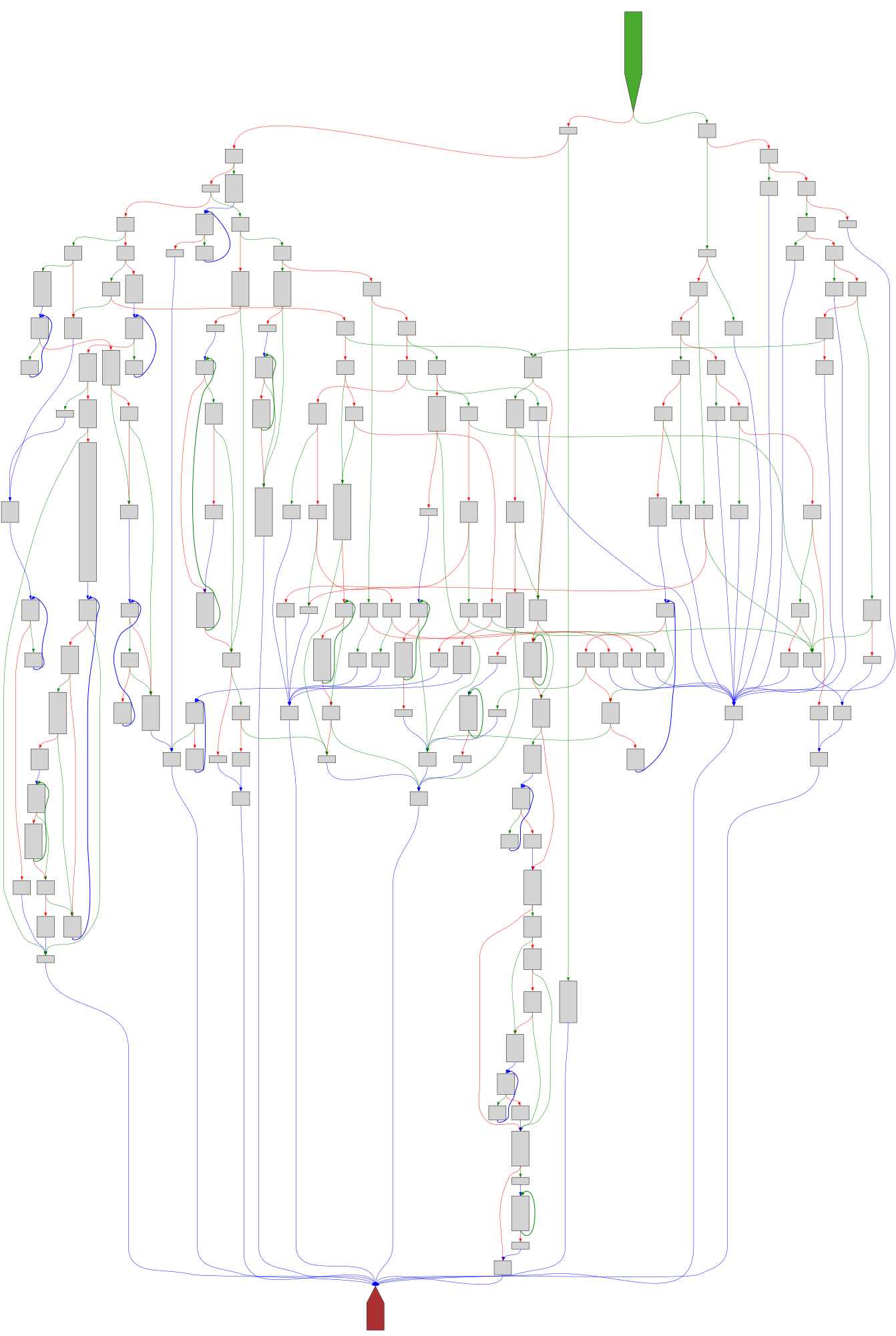
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a287e00
sqlite3GetToken
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a287e00.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a287e00.json&colors=light
ApplSec
applsec@infosec.exchange⚒️ FIXED IN iOS and iPadOS 26.1 ⚒️
- 18 bugs in WebKit
- 4 bugs in Model I/O
- 3 bugs in Safari
- 2 bugs in Apple Neural Engine
and 29 other vulnerabilities fixed
https://support.apple.com/en-us/125632
buherator
buheratorhttps://www.oobs.io/posts/four-bytes-one-lie/
CVE-2025-50168
Natalie Silvanovich
natashenka@infosec.exchangeNew Blog Post: Seth Jenkins broke kASLR by doing … nothing 😩
https://googleprojectzero.blogspot.com/2025/11/defeating-kaslr-by-doing-nothing-at-all.html
FFmpeg
ffmpeg@bird.makeupHere's an example of Google's AI reporting security vulnerabilities in this codec:
https://issuetracker.google.com/issues/440183164
We take security very seriously but at the same time is it really fair that trillion dollar corporations run AI to find security issues on people's hobby code? Then expect volunteers to fix.
https://bird.makeup/users/ffmpeg/statuses/1983949866725437791
FFmpeg
ffmpeg@bird.makeupArguably the most brilliant engineer in FFmpeg left because of this. He reverse engineered dozens of codecs by hand as a volunteer.
Then security "researchers" and corporate employees came along repeatedly insisted "critical" security issues were fixed immediately waving their CVEs.
This was hugely demotivating to the fun and enjoyment of reverse engineering.
https://bird.makeup/users/ffmpeg/statuses/1978390935433097310
BleepingComputer
BleepingComputer@infosec.exchangeAn out-of-band (OOB) security update that patches an actively exploited Windows Server Update Service (WSUS) vulnerability has broken hotpatching on some Windows Server 2025 devices.
Josh Bressers
joshbressers@infosec.exchangeThis week on #OpenSourceSecurity I talk to @ottok about his blog post about detecting an attack like xz in Debian
It's a fascinating conversation about a very complicated topic
There are things that could be detected, but this one would have been very very difficult
buherator
buheratorhttps://github.com/purseclab/deepSURF
buherator
buheratorhttps://research.checkpoint.com/2025/drawn-to-danger-windows-graphics-vulnerabilities-lead-to-remote-code-execution-and-memory-exposure/
Gareth Heyes 
gaz@infosec.exchange
Firefox nightly introduces the setHTML() method. Which is like a native DOMPurify. You can easily test it here:
https://portswigger-labs.net/mxss/
Set HTMLSanitizer ✅
Auto update ✅
I'm trying to break it, I encourage you to break it too
OpenSecurityTraining2
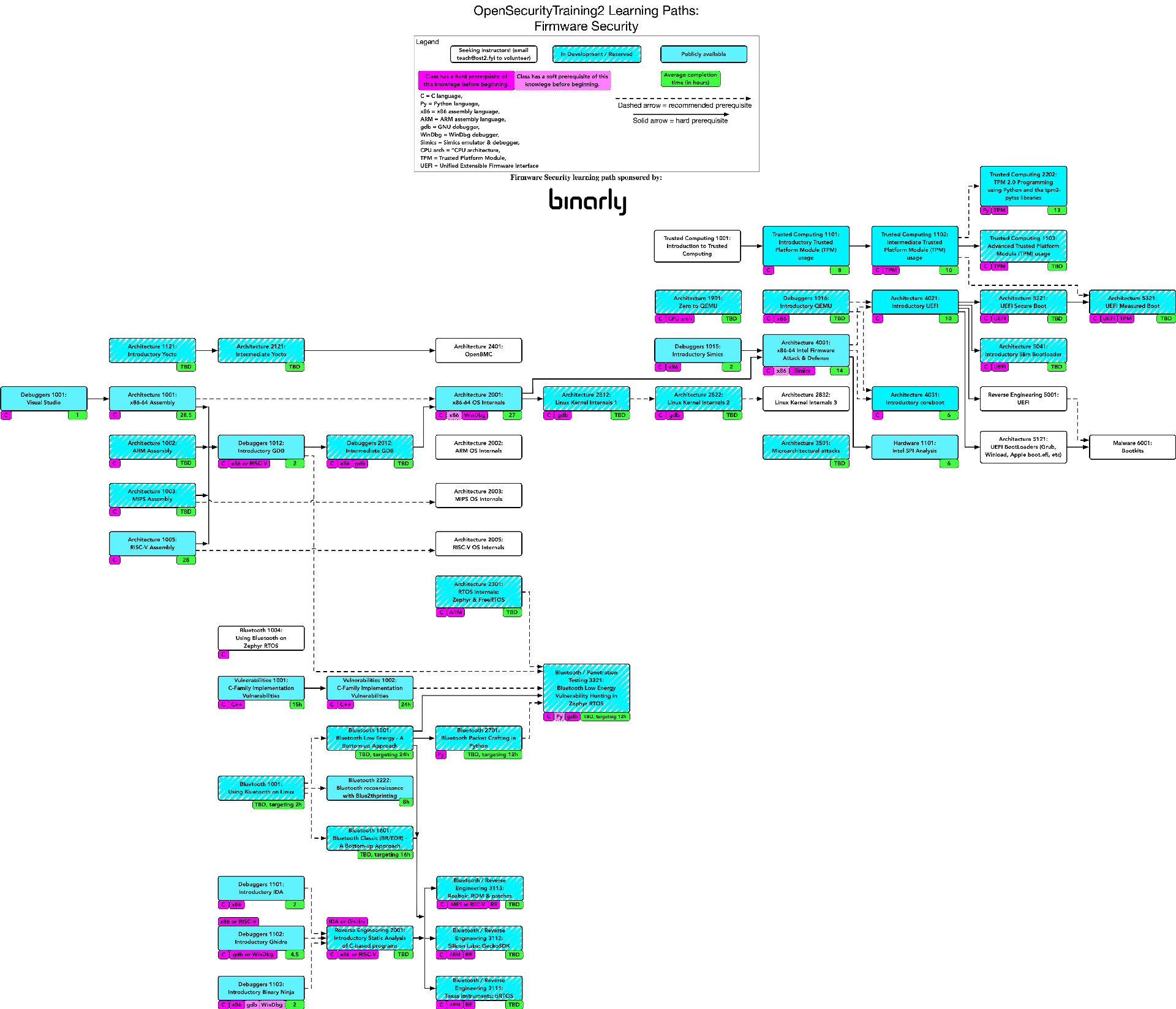
OpenSecurityTraining2@infosec.exchangeThis year Binarly has also expanded their sponsorship to the creation of a new Firmware Security Learning Path! https://ost2.fyi/OST2_LP_FWSEC.pdf
This captures current and future plans for classes involving security in the deep-dark of firmware! But Binarly is starting to give visibility into what's going on there with their binary analysis platform.
BSidesVienna.at
bsidesvienna@infosec.exchangeIt is decided, the final round of #BSidesVienna tickets will be in 7 days from now on Sunday 09.11.2025 at 7 pm. That is 19:00 o'clock Vienna time UTC+1!
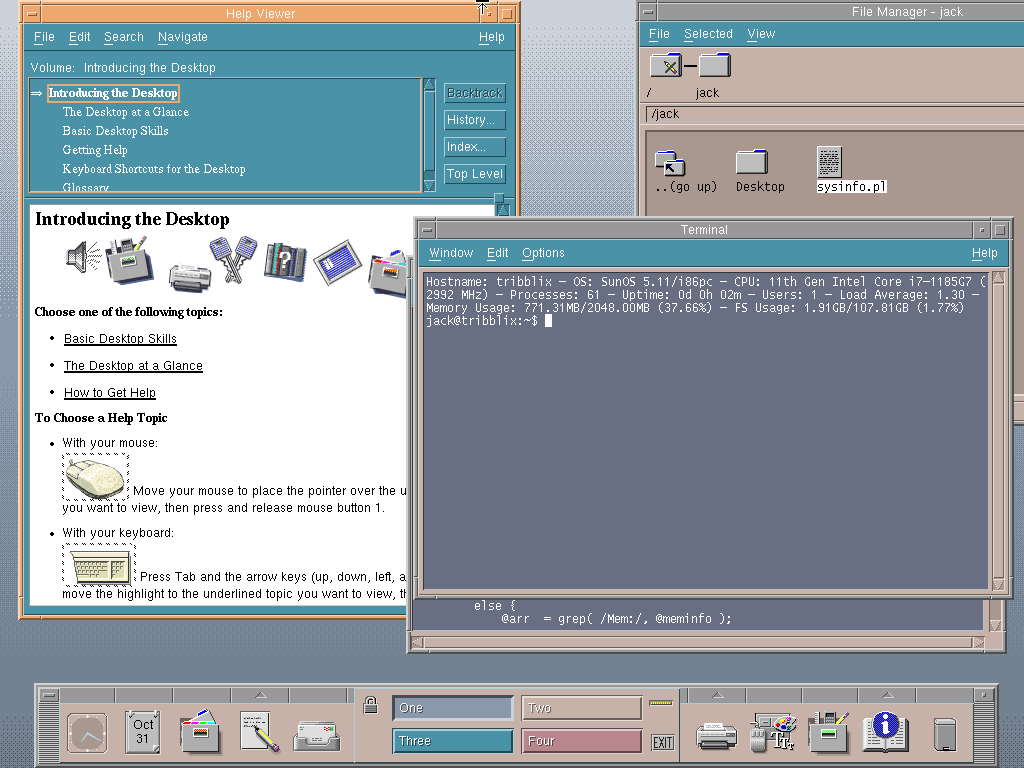
Cryogenix
cryogenix@fosstodon.orgCDE (proper CDE) and sysinfo.pl on Tribblix 0m37
Tribblix: http://www.tribblix.org/
sysinfo.pl: https://codeberg.org/int16h/sysinfo-pl
Erik Jonker
ErikJonker@mastodon.socialA great quote from the book Autocracy Inc from Ann Applebaum, a recommended read. A good description of the atmosphere the Trump administration tries to create.
#trump #autocracy #applebaum
im trying to vibe code an ida plugin rn and its not going great folks