Posts
3060Following
703Followers
1553Viss
Viss@mastodon.socialinfosec has a lot to learn about understanding failure conditions and accurate, understandable error messages from roadies
Joshua Small
jsmall@infosec.exchangeWell done to this Redditor for explaining Remote Desktop.
Addison
addison@nothing-ever.worksA little interactive post on a little error in fuzzer evaluations: https://addisoncrump.info/research/metric-shenanigans/
Harry Sintonen
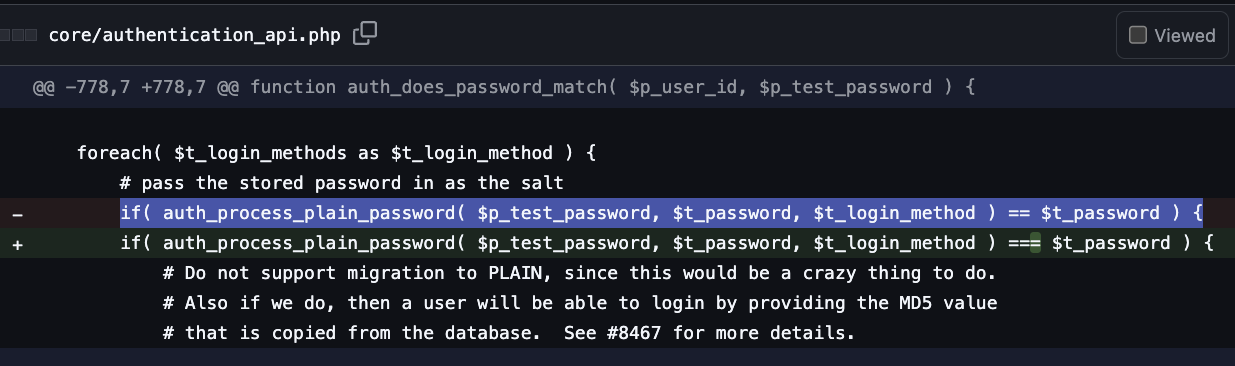
harrysintonen@infosec.exchangeSeveral months ago, I found a #vulnerability from #MantisBT - Authentication bypass for some passwords due to PHP type juggling (CVE-2025-47776).
Any account that has a password that results in a hash that matches ^0+[Ee][0-9]+$ can be logged in with a password that matches that regex as well. For example, password comito5 can be used to log in to the affected accounts and thus gain unauthorised access.
The root cause of this bug is the incorrect use of == to match the password hash:
if( auth_process_plain_password( $p_test_password, $t_password, $t_login_method ) == $t_password )
The fix is to use === for the comparison.
This vulnerability has existed in MantisBT ever since hashed password support was added (read: decades). MantisBT 2.27.2 and later include a fix to this vulnerability. https://mantisbt.org/download.php
Joxean Koret (@matalaz)
joxean@mastodon.socialAnybody having problems with #Firefox version 144.0.2 with random domains failing due to cookies? An example error with eBay:
Cookie “ds2” has been rejected for invalid domain.
Cookie “ebay” has been rejected for invalid domain.
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20251027-00/?p=111731
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-91-patch-gapping-browsers-ubuntu-lpes-bluetooth-int-underflows-and-more/
My clearest (and slightly frightening) measure of the passage of time is the weekly exploits.club newsletter.
Rémi GASCOU (Podalirius)
podalirius_@bird.makeupI have released an OpenGraph collector for network shares and my first blogpost at @specterops on the subject!
You can now visualize attack paths to network shares in BloodHound 👀
https://specterops.io/blog/2025/10/30/sharehound-an-opengraph-collector-for-network-shares/
Simple Sabotage Field Manual
simple_sabotage@mastodon.socialApply all regulations to the last letter.
RE//verse Conference
REverseConf@infosec.exchange2 weeks left to drop your talk in the ring. CFP closes Nov 14! https://sessionize.com/reverse-2026
codecolorist
codecolorist@infosec.exchangeNew post: Abusing macOS tclsh as shellcode loader
https://codecolor.ist/2025/10/31/macos-abuse-tcl-lol/
Happy Halloween 🎃
blasty
bl4sty@bird.makeupkind of funny that bugs that are communicated to vendors in a way they don't appreciate can result in no CVE being allocated for the vuln(s). while i guess it is bureaucratically legit (or is it?) it makes the CVE system an unreliable source of truth (more news at 11)
https://bird.makeup/users/0xmadvise/statuses/1983893375498776932
Oooh! Crowd Supply has finally posted a link to my talk at Teardown 2025 about trusting silicon: https://www.youtube.com/watch?v=pxQCApAAT0s
buherator
buheratorShow content
Really cool stuff!
https://unhumanofficial.bandcamp.com/album/unhuman
(TBDM classival cover is here: https://www.youtube.com/watch?v=c7gp8syqCBo (
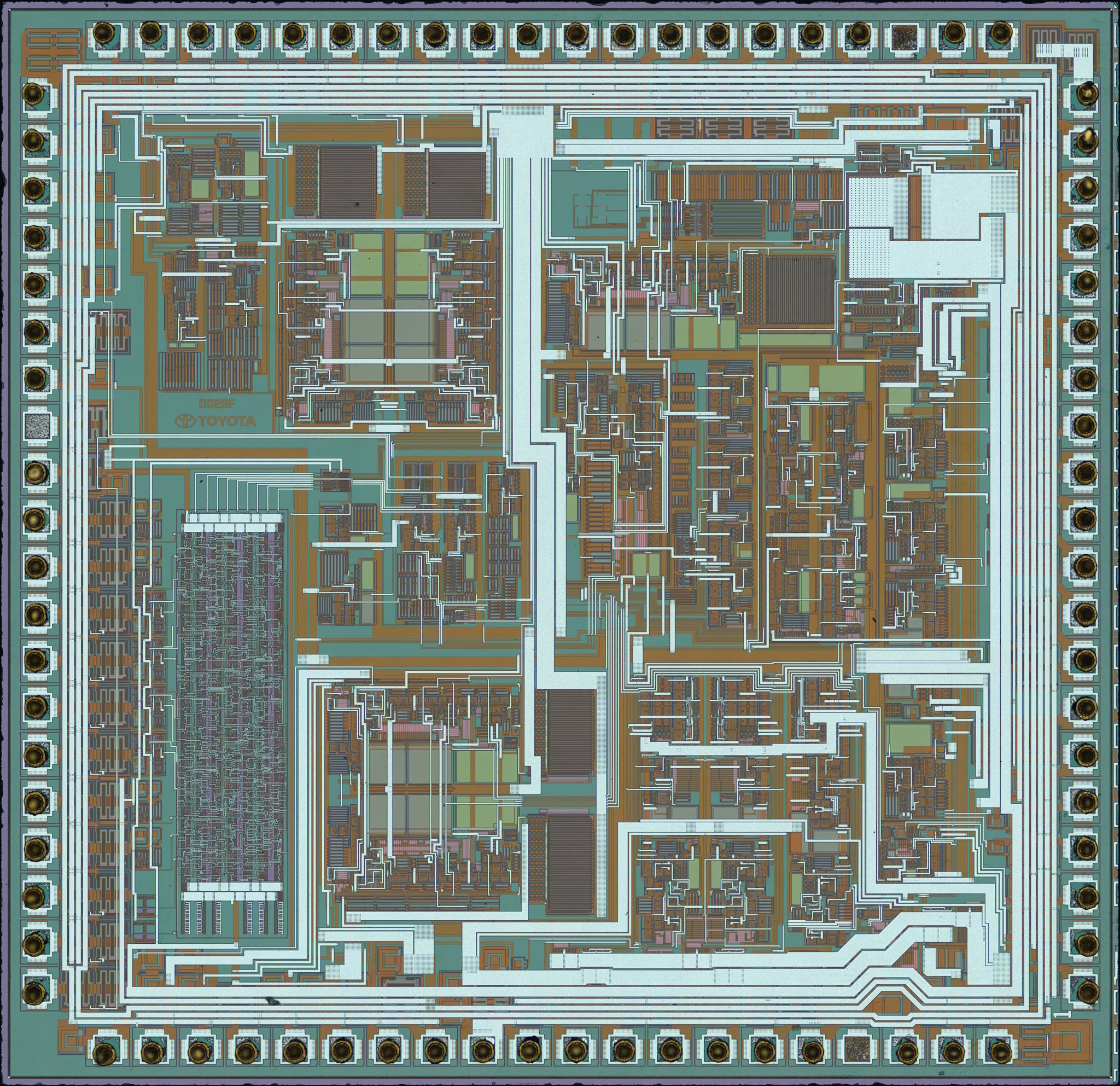
Hello! Hello. It's #nakeddiefriday today, and I wanted to show you one of the older works. This is an automotive ASIC fabbed for Toyota, part number DF028. I do not know the function of this particular device.
SiPron page: https://siliconprawn.org/archive/doku.php?id=infosecdj:toyota:d028f
Olivier Duclos
odc@mstdn.io✋ Stop writing #CSS yourself for your blog. Since 1998, the W3C provides a bunch of ready to use style-sheets: the W3C Core Styles. https://www.w3.org/StyleSheets/Core/Overview
Guaranteed to work on Netscape 4!