Posts
3062Following
703Followers
1553Today is 31 October 2025.
Twenty years ago today, on 31 October 2005, https://en.wikipedia.org/wiki/Mark_Russinovich published a detailed description and technical analysis of First 4 Internet’s (F4I) XCP software, which he discovered had been secretly installed on his computer by a Sony BMG music CD.
The software was part of the CD’s digital component and automatically installed itself on Windows computers when the disc was inserted into a CD-ROM drive. A similar component for MacOS was blocked from automatic installation with Operating System confirmation prompts. The driver interfered with any attempt to rip audio CDs on that system and actively concealed itself to prevent detection or removal.
Russinovich compared XCP to a rootkit because of its covert installation and use of stealth techniques to hide its presence. He pointed out that the EULA made no mention of the software and argued that its behavior was illegitimate.
The security firm F-Secure agreed, stating: "Although the software isn't directly malicious, the rootkit hiding techniques it uses are exactly the same as those used by malicious software." Following public backlash, Symantec and other antivirus vendors added detection and removal for the rootkit, and Microsoft announced that it would include protection against it in its security updates.
XCP operated with high system privileges and contained numerous exploitable vulnerabilities, creating a serious security risk. That risk quickly became real: within weeks, several trojans and worms appeared that exploited flaws in the XCP software.
As the result of government investigations and class-action lawsuits, Sony BMG partially addressed the scandal with consumer settlements and a recall that affected about 10% of the affected CDs. It ceased the copy-protection efforts in 2007.
The Sony rootkit scandal only affected users that bought legitimate copies of music. Everybody who used Napster or Donkey to grab the MP3 was of course unaffected.
Sony has never apologized to its customers.
Timeline, in German:
https://netzpolitik.org/2005/rookit-sonys-digitaler-hausfriedensbruch/
Sony also produced, only one year later, the
https://www.engadget.com/2006-01-05-sony-vaio-xl2-digital-living-system.html
Like the XL1, the XL2 sports an HDMI video out, operation via wireless keyboard and remote, and an optional 200 CD/DVD changer for library management. Running Windows MCE 2005, the XL2 is harboring Intel Viiv inside
Sony also turned off the DRM-Servers for the Conect-Online Musicshop in March 2008, again fucking over all customers that paid for their content.
https://www.golem.de/0804/59229.html
In an interview 2012, Sony Music boss Edgar Berger said
Das Internet ist für die Musikindustrie ein großer Glücksfall, oder besser gesagt: Das Internet ist für uns ein Segen.
"The Internet for us is a boon."
Whatever companies think, even today the only way to actually purchase content on the internet is to buy content without DRM, or buy content with removable DRM, downloiad and deDRM it immediately.
Have a media library. Make sure your stuff can use this media library. Back up your media library.
Ada Swordlace
swordlace@www.librepunk.clubAnybody remember how twitter used to work over text message?
I think I broke that feature.
You could send and receive tweets, and do some basic interactions like following keywords - for example FOLLOW Guybrush Threepwood would text you any tweets about the classic Lucasarts Adventure Game series Monkey Island™.
So one day at work I had an idea. I took my Nokia and texted FOLLOW lol.
My phone immediately blew up. I got the next tweet someone posted that said lol. And the one after that.
I tried to text STOP lol but my phone couldn't multitask, so every new instance of lol interrupted my attempt to stop them. When my phone's text memory filled up (300!), I found out it deletes old texts and keeps going
So I turned my phone off to stop the flow (I didn't have unlimited texting, this was getting expensive!)
When I got home from the office, Twitter was down. For a while.
When it came back up, the text messaging feature did not come back up. Ever.
ℒӱḏɩę 💾☮∞🎶♲☀🔋
Lydie@tech.lgbtSo #youtube is deleting videos of people showing how to install #Windows 11 on computers without TPMs and using local accounts. Can't imagine why.
So, please share mine! I make absolutely no money on my videos, I purely educate.
https://peertube.wtf/w/pqMrXFbzpJAS4r5NRj5o8j
Also 🖕 Microsoft
/r/netsec
_r_netsec@infosec.exchangeAutomating COM/DCOM vulnerability research https://www.incendium.rocks/posts/Automating-COM-Vulnerability-Research/
abadidea
0xabad1dea@infosec.exchange🎃🎃 if you've got spooky business this weekend, don't forget to put on the Gameboy Halloween chiptune playlist! 🎃🎃
404 Media
404media@flipboard.comSomeone Snuck Into a Cellebrite Microsoft Teams Call and Leaked Phone Unlocking Details
https://www.404media.co/someone-snuck-into-a-cellebrite-microsoft-teams-call-and-leaked-phone-unlocking-details/?utm_source=flipboard&utm_medium=activitypub
Posted into 404 Media @404-media-404media
Mr. Bitterness
wdormann@infosec.exchangeMicrosoft:
As much as 30% of the company's code is written by AI.
Also Microsoft:
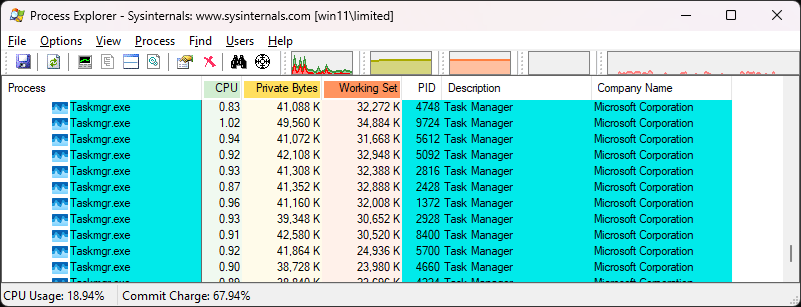
Somehow we managed to make it so that clicking the x in Task Manager doesn't close the app. Whoopsie daisy!
buherator
buheratorhttps://code-white.com/blog/wsus-cve-2025-59287-analysis/
buherator
buheratorhttps://blog.0patch.com/2025/10/micropatches-released-for-windows_30.html
Trail of Bits
trailofbits@infosec.exchangeWe're spilling the TEE: We're disclosing vulnerabilities (CVE-2025-59054, CVE-2025-58356) in LUKS2 disk encryption affecting 8 confidential computing systems.
Dan Goodin
dangoodin@infosec.exchangeAMD, Intel and Nvidia have poured untold resources into building on-chip trusted execution environments. These enclaves use encryption to protect data and execution from being viewed or modified. The companies proudly declare that these TEEs will protect data and code even when the OS kernel has been thoroughly compromised. The chipmakers are considerably less vocal about an exclusion that physical attacks, which are becoming increasingly cheap and easy, aren't covered by the threat model These physical attacks use off the shelf equipment and only intermediate admin skills to completely break all TEEs made from these three chipmakers.
This shifting Security landscape leaves me asking a bunch of questions. What's the true value of a TEE going forward?. Can governments ever get subpoena rulings ordering a host provider to run this attack on their own infrastructure? Why do the companies market their TEEs so heavily for edge servers when one of the top edge-server threats is
physical attacks?
People say, "well yes. just run the server in Amazon or another top tier cloud provider and you'll be reasonably safe." The thing is, TEEs can only guarantee to a relying party that the server on the other end isn't infected and couldn't give up data even even if it was. There's no way for the relying party to know if the service is in Amazon or in an attackers's basement. So once again aren't we back to just trusting the cloud, which is precisely the problem TEEs were supposed to solve?
blasty
bl4sty@bird.makeupthe most important question I have about this HackingTeam revival that was exposed by @oct0xor and co is if #YourBoySerge is still saving the day when the live demos fail during a sales pitch. or did they find a new Serge?
(anyone remember #YourBoySerge? or am I just really old?)
Zack Whittaker
zackwhittaker@mastodon.social🚨🚨🚨 Absolutely insane stuff here. @lorenzofb spent months working on this story.
Peter Williams, former L3Harris Trenchant boss — the division that makes cyber exploits, zero-days and spyware for Western governments — has pleaded guilty to selling Trenchant's exploits to Russia.
mhoye
mhoye@mastodon.socialThere's an Azure outage, so in the Netherlands, rail services aren't working.
(Originally read "trains", but it's not the actual trains, it's ticket sales and planning)
https://nltimes.nl/2025/10/29/ns-hit-microsoft-cloud-outage-travel-planner-ticket-machines-affected
Cat 🐈🥗 (D.Burch) 
catsalad@infosec.exchange
If Azure isn't back up in 15 minutes, everyone can go home.
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-hhv7-p4pg-wm6p
Edit: This is CVE-2025-8291 (thx for all who noted!)
Erkhyan
erkhyan@yiff.lifeI’ve just seen someone describe Windows 11 as a “sloperating system”.
James Forshaw 
tiraniddo@infosec.exchange
Administrator Protection has finally been released in KB5067036. This is an optional update, but it does fix 7 of the 9 issues that I reported to MSRC (hopefully the other 2 get fixed next month as security bulletins). I honestly don't know if they've actually fixed the SSPI issues like my Kerberos bypass or not, I'm not inclined to check. People should kick the tyres on it, maybe there's still some bounties to be had :D
Zack Whittaker
zackwhittaker@mastodon.socialSCOOP: On Mon, Kaspersky said it found new spyware called Dante targeting Windows users in Russia & Belarus, saying the spyware was developed by Milan-based Memento Labs.
Memento's CEO confirmed to TechCrunch's @lorenzofb that Dante is its spyware, and blamed one of its government customers for getting caught.
Wolfie
wolfie@blahaj.socialWorking in cybersecurity is weird.
“Wolfie where do you get your threat intel?”
“Gay furries on Mastodon.”
“What?”
“Well it’s a decentralised social network…”
“No stop are you saying we’re prioritising our cybersecurity activity based on what furries are shitposting?”
“Yes.”
“…”
“You want the good cybersecurity, yes?”
“Yes.”
“Right, so this week between the jokes about Copilot now looking like a blob of jizz with a face, the big topics are…”