Posts
3370Following
712Followers
1579bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@eupolicy.socialThe awesome people of @c3voc have released the recording of my Sunday #why2025 talk "Reverse Engineering Life: A teardown of the DNA source code of a whole bacterium"! https://media.ccc.de/v/why2025-34-reverse-engineering-life-a-teardown-of-the-dna-source-code-of-a-whole-bacterium https://www.youtube.com/watch?v=NUUFQyq4F_o
buherator
buheratorRE: https://mastodon.social/@simple_sabotage/115010865658460649
kaoudis
kaoudis@infosec.exchangeMy colleagues at Trail of Bits and I wrote an LLVM RFC about constant-time coding support in Clang and LLVM! I’d love to have folks with opinions on this topic, who are interested to, comment on the RFC 💚 https://discourse.llvm.org/t/rfc-constant-time-coding-support/87781
Alexandre Borges
alexandreborges@infosec.exchangeSo far, I have already written 15 articles (1045 pages), which have been published on my blog:
blog: https://exploitreversing.com
ERS: Exploiting Reversing Series (currently at 439 pages, with continued progress underway):
[+] ERS 05: https://exploitreversing.com/2025/03/12/exploiting-reversing-er-series-article-05/
[+] ERS 04: https://exploitreversing.com/2025/02/04/exploiting-reversing-er-series-article-04/
[+] ERS 03: https://exploitreversing.com/2025/01/22/exploiting-reversing-er-series-article-03/
[+] ERS 02: https://exploitreversing.com/2024/01/03/exploiting-reversing-er-series-article-02/
[+] ERS 01: https://exploitreversing.com/2023/04/11/exploiting-reversing-er-series/
MAS: Malware Analysis Series (606 pages -- finished):
[+] MAS 10: https://exploitreversing.com/2025/01/15/malware-analysis-series-mas-article-10/
[+] MAS 09: https://exploitreversing.com/2025/01/08/malware-analysis-series-mas-article-09/
[+] MAS 08: https://exploitreversing.com/2024/08/07/malware-analysis-series-mas-article-08/
[+] MAS 07: https://exploitreversing.com/2023/01/05/malware-analysis-series-mas-article-7/
[+] MAS 06: https://exploitreversing.com/2022/11/24/malware-analysis-series-mas-article-6/
[+] MAS 05: https://exploitreversing.com/2022/09/14/malware-analysis-series-mas-article-5/
[+] MAS 04: https://exploitreversing.com/2022/05/12/malware-analysis-series-mas-article-4/
[+] MAS 03: https://exploitreversing.com/2022/05/05/malware-analysis-series-mas-article-3/
[+] MAS 02: https://exploitreversing.com/2022/02/03/malware-analysis-series-mas-article-2/
[+] MAS 01: https://exploitreversing.com/2021/12/03/malware-analysis-series-mas-article-1/
I'll soon begin writing the next articles in the Exploiting Reversing series, which will focus on vulnerability and exploitation, once I've laid all the necessary groundwork.
Enjoy reading and have a great day.
#windows #iOS #macOS #cybersecurity #infosec #chrome #kernel #malware #reverseengineering #vulnerability #research #hypervisor
buherator
buheratorhttps://analyst1.com/ransomware-diaries-volume-7-i-had-to-take-the-guilt-for-everyone-the-kaseya-hacker-breaks-his-silence/
Jack Rusher
jack@berlin.social“The enjoyment of one's tools is an essential ingredient of successful work.”
#DonaldKnuth
Reading all these posts about AIxCC challenge. Quite interesting and exciting material. What bothers me is saying the agents have deep understanding and next that they get stuck and need many attempts to get over the problems. This normalization of properties that don't really exist bothers me, you see it everywhere. LLMs can't think, don't have real understanding of anything. That doesn't mean they can't be very useful tools for certain domains.
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchangeCurious how a bug in Linux’s ipset subsystem could lead to full kernel compromise?
In our new article, we revisit CVE-2024-53141 to break down the bug, explore the memory layout, and show how it can be turned into a powerful privilege escalation.
Read it here: https://ssd-disclosure.com/linux-kernel-netfilter-ipset-missing-range-check-lpe/
HD Moore
hdm@infosec.exchangeThank you to everyone who made it out for my DEF CON 33 presentation, "Shaking Out Shells With SSHamble", you can find the materials online at https://hdm.io/decks/MOORE%20-%20Shaking%20Out%20Shells%20With%20SSHamble.pdf
This deck includes some lightly-censored zero-day and I recommend tossing `sshamble scan -u root,admin,guest 22,24442,2222,70,222,10022,10399,2022,22222 --interact=all` at your local network to see what shakes out =D
(PS. You can find most of my presentations at https://hdm.io/)
Alexandre Dulaunoy
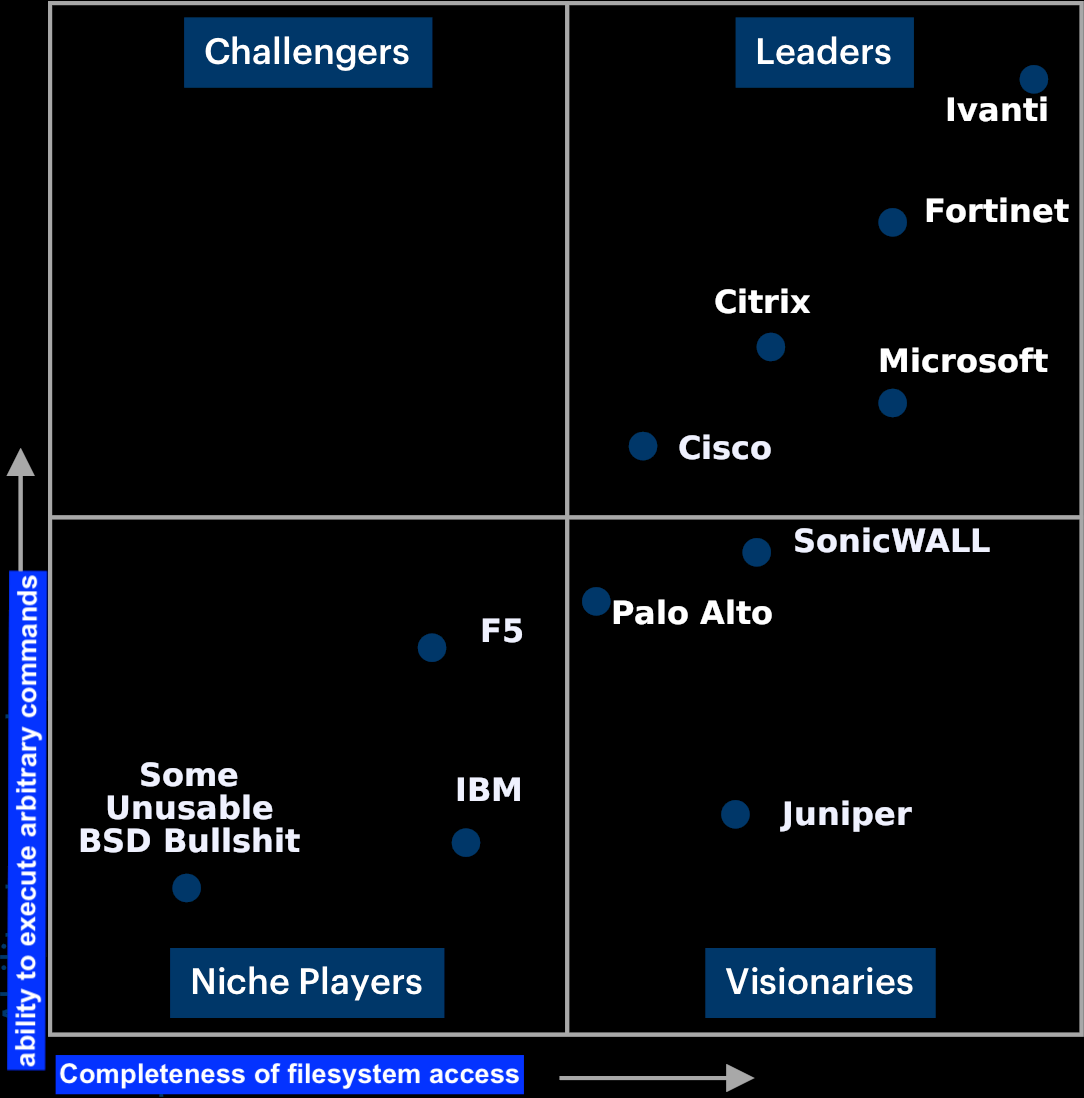
adulau@infosec.exchangeFinally a useful magic quadrant
Thanks to @wendynather for the discovery.
Frédéric Jacobs
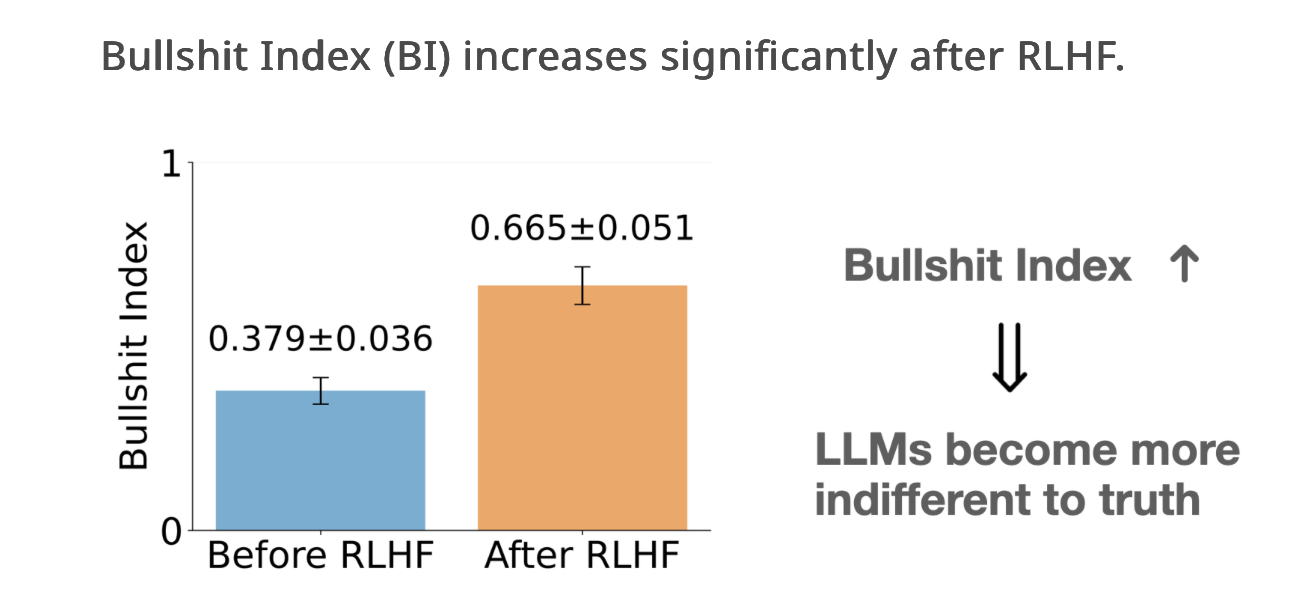
fj@mastodon.socialReinforcement learning makes LLM bullshit more.
https://machine-bullshit.github.io
buherator
buheratorhttps://mrwint.github.io/winter/writeup/writeup2.html
buherator
buheratorhttps://seclists.org/oss-sec/2025/q3/82
Attila Szasz
4ttil4sz1a@bird.makeup🐧🏆 Linux just bagged a Pwnie with my CVE—well, technically multiple rejected CVEs 😏 Congrats!
📜 BTW, MITRE is still investigating my -4.6 Dispute Resolution- request… submitted back in June. 🗓️⏳
Jay 🆘
jsit@social.coopIf you want an ebook of some public domain work, either:
1. Check standardebooks.org before Gutenberg. They clean up books from Gutenberg with sane typography and print design.
2. Consider buying a "Dover Thrift Editions" version of the ebook. Many fly-by-night ebook "publishers" are turning a quick buck on selling you a Gutenberg edition. Dover is a real publisher, even in print, and their well-formatted ebooks of public domain works are usually under $4, or even less.
I wonder how things are going right now in the universe where IBM chose CP/M for the IBM PC instead of MS-DOS.
(Like… with computers. I mean.)