Posts
2502Following
656Followers
1476hackaday
hackaday@hackaday.socialA Gentle Introduction to Fortran
https://hackaday.com/2025/08/04/a-gentle-introduction-to-fortran/
Metacurity
metacurity@infosec.exchange27 Behind the Scenes Polaroid Snapshots From the Making of the 1995 Cult Classic “Hackers”
https://www.vintag.es/2025/07/hackers-polaroids.html
buherator
buheratorhttps://www.youtube.com/watch?v=TMoz3gSXBcY
"you are specifically and intentionally refusing to learn anything, which just seems like a problem." <- This!
Nina Kalinina
nina_kali_nina@tech.lgbtVibecoding can never reach the level of coolness Borland Delphi had
Marco Ivaldi
raptor@infosec.exchangebuherator
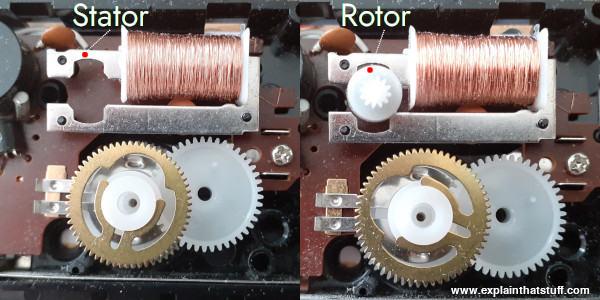
buherator(img source: https://www.explainthatstuff.com/quartzclockwatch.html )
#electronics
buherator
buheratorhttps://docs.google.com/document/d/1fynP2jWwrFP9wOQLFQIyFjmq0PDUaJW3e-x5I7yN7ZI/edit
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🌪️ TyphoonCon 2026 is set for May 25-29 in Seoul!
Our Call for Papers and Call for Training are now open. Interested in joining our 2026 lineup? Get all the details here:
Call for training: https://typhooncon.com/call-for-training-2026/
Call for papers: https://typhooncon.com/call-for-papers-2026
buherator
buheratorWe should definitely have that role!
Programming Quotes
programming_quotes@mastodon.socialA fool with a tool is a more dangerous fool.
— u
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeThe Google Project Zero post from a while ago that showed memory safety bugs were more common in new code continues to annoy me because it’s such a clear example of computer scientists doing social science without understanding how to do it.
The root problem is that they are no counting the number of bugs. There is no ground truth that they are able to use. They are counting the number of bugs found. And how are bugs found? When you have some existing technique (static analysis, fuzzing, code review, whatever) that finds that kind of bug.
So their conclusion is ‘bugs that existing techniques are able to find are less likely to appear in code that has already been subject to those techniques’. To which the correct response is ‘well, duh’.
The original Coverity paper, which introduced a large range of brand new static analysis techniques, found a load of bugs in old code. When we started running existing C and C++ code on CHERI, we saw very little correlation between the bugs that we found and the age of the codebase (we found quite a few bugs that were 20+ years old).
If you remove the sample bias, the results are far less clear cut and there are a load of confounding factors. If a memory-safety bug causes random crashing in one in a million runs of a userspace program based on some non-deterministic factor, it’s unlikely that anyone will debug it. If a sequence of actions reliably crashes a kernel, it will probably be fixed. If an attacker finds it and is actively exploiting it, it will almost certainly be fixed. The symptoms and reproducibility of the bug have a huge impact on whether it will be fixed.
buherator
buheratorhttps://www.youtube.com/watch?v=IAuapNwJ2vQ
Praise be the Omnissiah!
#wh40k
Ivan Ožić Bebek
obivan@infosec.exchangeHashcat v7.0.0 released https://hashcat.net/forum/thread-13330-post-63567.html#pid63567
buherator
buheratorShow content
https://carbomb.bandcamp.com/album/tiles-whisper-dreams-ep
#extrememetal
David Gerard
davidgerard@circumstances.runProton’s Lumo AI chatbot: not end-to-end encrypted, not open source
https://pivot-to-ai.com/2025/08/02/protons-lumo-ai-chatbot-not-end-to-end-encrypted-not-open-source/ - text
https://pivottoai.libsyn.com/20250802-protons-lumo-ai-chatbot-not-end-to-end-not-open-source - podcast
https://www.youtube.com/watch?v=HDPZbUPUFyk&list=UU9rJrMVgcXTfa8xuMnbhAEA - video
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/08/03/1
deater
deater78@mastodon.sociala 2661 byte program I wrote just won the "Sur Prize" at the International Obfuscated C Code Competition. You can probably guess what it is once I mention that @foone might enjoy it
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250723-00/?p=111403
Some fun anti-reverse possibilities here :)