Posts
3368Following
712Followers
1580/r/netsec
_r_netsec@infosec.exchangeHow to craft a raw TCP socket without Winsock? https://leftarcode.com/posts/afd-reverse-engineering-part1/
[realhackhistory@home]#
realhackhistory@chaos.socialFrom a CBS news segment from July of 1985 discussing the busting of various #hackers and BBS operators in New Jersey.
Ouch, but also 💀
Will be uploading the entire segment to Internet Archive later today.
evacide
evacide@hachyderm.ioAnother day, another conversation with the press team where I explain that I did not give the quote in that story and the whole thing is AI slop. This happens once every few weeks now.
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20050322-00/?p=36113
TIL about COMDAT folding #compiler optimization!
buherator
buheratorhttps://incendium.rocks/posts/Exploit-Development-For-MSRPC/
Talos Vulnerability Reports
talosvulnsEclipse ThreadX FileX RAM disk driver buffer overflow vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2088
buherator
buheratorhttps://www.shielder.com/blog/2025/07/materialx-and-openexr-security-audit/
buherator
buheratorhttps://www.ioactive.com/characterizing-the-raspberry-pico-2-fi-countermeasures-part-1/
Ken Shirriff
kenshirriff@oldbytes.spaceIn 1983, Philips produced the first FM radio receiver on a chip, leading to products such as the FM radio wristwatch. Let's look at the tiny silicon die inside this chip and see how it works. 1/N
Unnamed RE Podcast 
unnamedre@infosec.exchange
New episode is up!
We talked with Nathan Emerick about the Spotify CarThing and it's journey to becoming the DeskThing :D
https://unnamedre.com/episode/75
buherator
buheratorhttps://github.com/NationalSecurityAgency/ghidra/releases/tag/Ghidra_11.4.1_build
What's New:
https://github.com/NationalSecurityAgency/ghidra/blob/Ghidra_11.4.1_build/Ghidra/Configurations/Public_Release/src/global/docs/WhatsNew.md
Change History:
https://github.com/NationalSecurityAgency/ghidra/blob/Ghidra_11.4.1_build/Ghidra/Configurations/Public_Release/src/global/docs/ChangeHistory.md
Graham Sutherland / Polynomial
gsuberland@chaos.socialblue cheese (the blue is Cherenkov radiation)
Caitlin Condon
catc0n@infosec.exchangeThis is super interesting and isn’t a type of research I’ve seen a lot of before. Great write-up from @albinolobster and team on attacker infrastructure longevity: https://www.vulncheck.com/blog/stillup-stillevil
Joel Chippindale
joel@social.monkeysthumb.co.uk"If you only praise last-minute saves, you’ll keep getting last-minute problems. Make sure to recognize the engineer who reduced incidents, the PM who saw the risk a month out, the designer who caught the complexity before it shipped. Make that kind of foresight just as visible and valuable as triage and repair."
— @timcheadle from https://www.timcheadle.com/dont-let-crisis-become-a-compass/
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Related: If you want to tell me you've jailbroken the AI, you better be prepared to tell me how you reverse engineered the ETL, data model and guard rails, not how you clicked on the shiny, shiny and got a shell prompt.
Samuel Groß
saelo@chaos.socialWe released our Fuzzilli-based V8 Sandbox fuzzer: https://github.com/googleprojectzero/fuzzilli/commit/675eccd6b6d0c35ea6c7df24a0a1e513cce45bb3
It explores the heap to find interesting objects and corrupts them in a deterministic way using V8's memory corruption API. Happy fuzzing!
SensePost
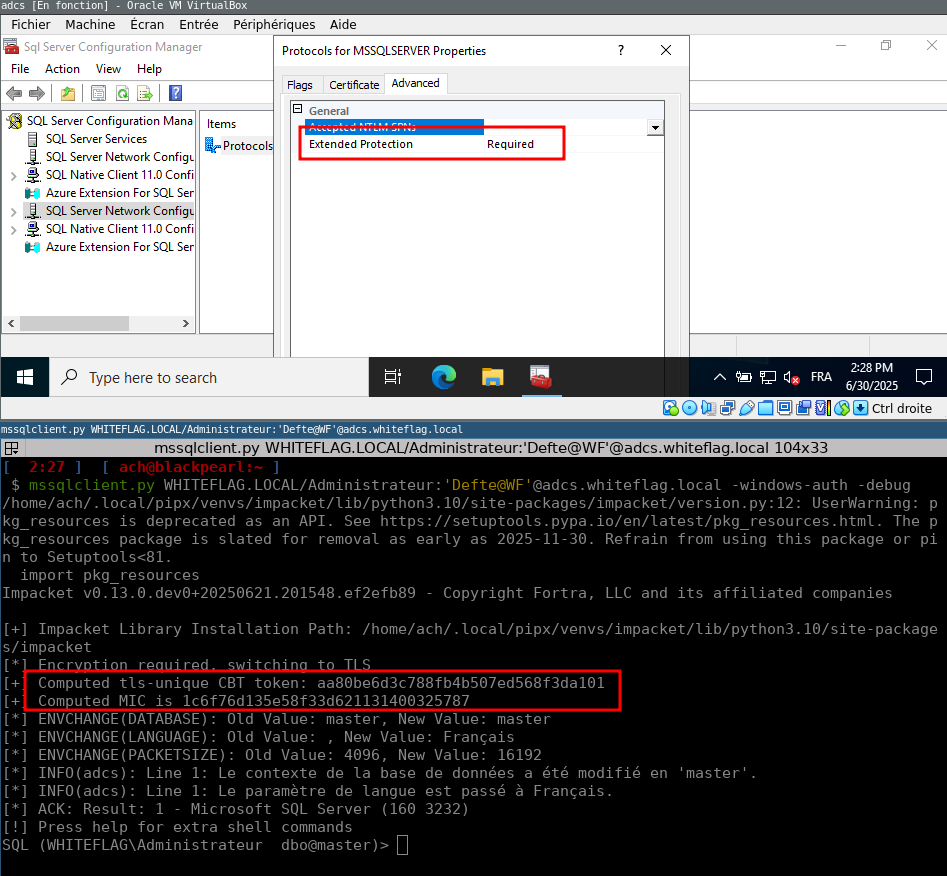
sensepost@infosec.exchangeReverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (@defte_), including instructions for reproducing the test environment yourself.
https://sensepost.com/blog/2025/a-journey-implementing-channel-binding-on-mssqlclient.py/
BobDaHacker 🏳️⚧️
bobdahacker@infosec.exchangeFound critical vulns in Lovense (the biggest sex toy company) affecting 11M+ users. They ignored researchers for 2+ years, then fixed in 2 days after public exposure. 🤦
What I found:
- Email disclosure via XMPP (username→email)
- Auth bypass (email→account takeover, no password)
History of ignoring researchers:
- 2017: First recorded case of someone reporting XMPP email leak.
- 2022: Someone else reports XMPP email leak, ignored
- Sept 2023: Krissy reports account takeover + different email leak via HTTP API, paid only $350
- 2024: Another person reports XMPP email leak AND Account Takeover vuln, offered 2 free sex toys (accepted for the meme)
- March 2025: I report account takeover + XMPP email leak, paid $3000 (after pushing for critical)
- Told me fix for email vuln needs 14 months because "legacy support" > user security (had 1-month fix ready)
- July 28: I go public
- July 30: Both fixed in 48 hours
Same bugs, different treatment. They lied to journalists saying it was fixed in June, tried to get me banned from HackerOne after giving permission to disclose.
News covered it but my blog has the full technical details:
https://bobdahacker.com/blog/lovense-still-leaking-user-emails/
#InfoSec #BugBounty #ResponsibleDisclosure #Security #Vulnerability #IoT #cybersecurity
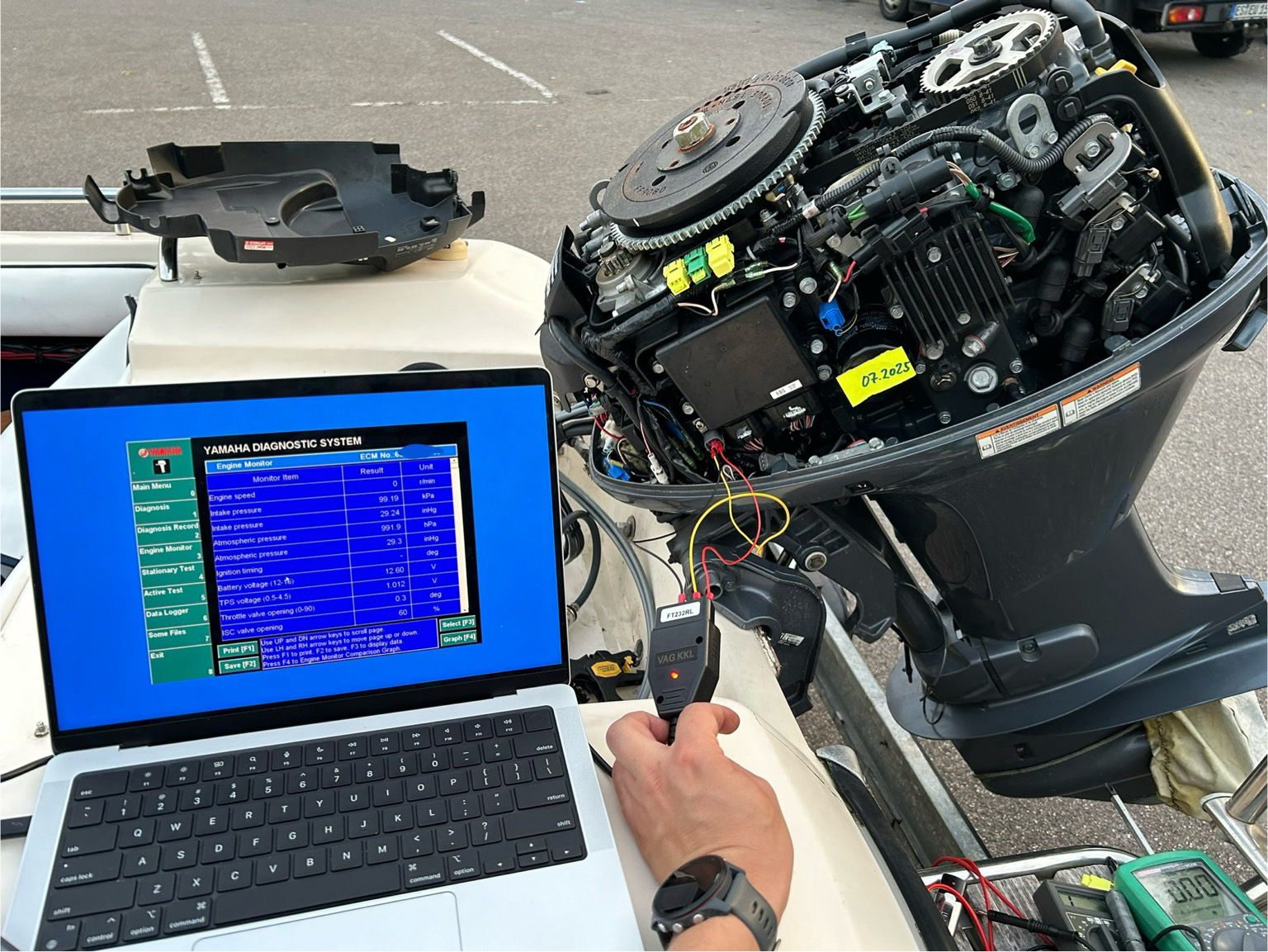
stacksmashing
stacksmashing@infosec.exchangeWhy do so many aspects of my life involve connecting FT232s to random pins 😂