Posts
2536Following
640Followers
1436Trend Zero Day Initiative
thezdi@infosec.exchangeSuccess! Hyeonjin Choi of Out Of Bounds targeting Microsoft Windows 11 wasted absolutely no time at all to successfully demonstrate his Local Escalation on #Windows11 - he is off in the disclosure room now! #Pwn2Own #P2OBerlin
Trend Zero Day Initiative
thezdi@infosec.exchangeAfter a dramatic pause in getting things setup Billy and Ramdhan of STAR Labs preformed a Docker Desktop escape to pop calc - and they are also now off to the disclosure room - good luck! #Pwn2Own #P2OBerlin
Trend Zero Day Initiative
thezdi@infosec.exchangeWe have another collision - Viettel Cyber Security targeting NVIDIA Triton Inference Server successfully demonstrated their exploit - however it was known to the vendor, but not yet patched. They still earn $15,000 and 1.5 Master of Pwn Points #Pwn2Own #P2OBerlin
Trend Zero Day Initiative
thezdi@infosec.exchangeAs expected, in his first #Pwn2Own attempt, Marcin Wiązowski showed of his Windows 11 privilege escalation. He went from a standard user SYSTEM in the blink of an eye. He's off to the disclosure room with his white paper of knowledge. #P2OBerlin
Trend Zero Day Initiative
thezdi@infosec.exchangeSweet! Hyunwoo Kim (@V4bel) and Wongi Lee (@_qwerty_po) of Theori were able to escalate to root on Red Hat Enterprise Linux. They head off to the disclosure room to cover the details of their exploit.
Kevin Beaumont
GossiTheDog@cyberplace.socialCoinbase filed an 8K with the SEC for a breach. They believe multiple insiders have sold customer information to a threat actor who is now extorting them.
It looks like a very significant breach as it includes customers passport scans.
https://www.sec.gov/ix?doc=/Archives/edgar/data/1679788/000167978825000094/coin-20250514.htm
Trend Zero Day Initiative
thezdi@infosec.exchangeWith our first confirmation, our results blog is now live. We'll be updating this blog throughout the day with the latest results. https://www.zerodayinitiative.com/blog/2025/5/15/pwn2own-berlin-2025-day-one-results
Trend Zero Day Initiative
thezdi@infosec.exchangeWe have a bug collision. Although Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) successfully demonstrated his exploit of #NVIDIA Triton, the bug he used was known by the vendor (but not patched). He still earns $15K and 1.5 Master of Pwn points.
Trend Zero Day Initiative
thezdi@infosec.exchangeConfirmed! Chen Le Qi of STARLabs SG combined a UAF and an integer overflow to escalate to SYSTEM on #Windows 11. He earns $30,000 and 3 Master of Pwn points. #Pwn2Own #P2OBerlin
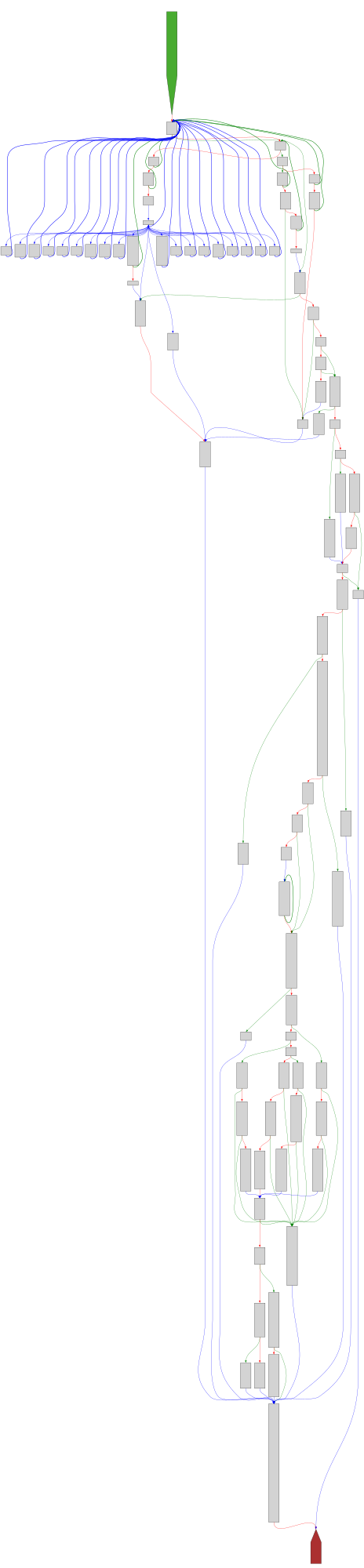
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 0043acc0
rsautl_main
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0043acc0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0043acc0.json&colors=light
buherator
buheratorhttps://karmainsecurity.com/KIS-2025-02
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.socialSleep deprivation is a form of torture.
Unless you are a parent, in which case it is a form of "children are a blessing, you wanted this, you're on your own, suck it up, good luck."
dragosr
dragosr@chaos.socialTime to update microcode on your Intel processors (gen >9)...
New speculative prediction bug lets you capture /etc/shadow with 99% reliability. They didn't make anything like it work on AMD or ARM... yet...
https://comsec.ethz.ch/research/microarch/branch-privilege-injection/
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-01247.html
https://github.com/intel/Intel-Linux-Processor-Microcode-Data-Files/releases/tag/microcode-20250512
chompie
chompie1337@haunted.computerMe and the homies are dropping browser exploits on the red team engagement 😎. Find out how to bypass WDAC + execute native shellcode using this one weird trick -- exploiting the V8 engine of a vulnerable trusted application.
https://www.ibm.com/think/x-force/operationalizing-browser-exploits-to-bypass-wdac
Taggart 
mttaggart@infosec.exchange
Holy wow, XSS to RCE in Restricted Mode in VSCode. What a find!
https://starlabs.sg/blog/2025/05-breaking-out-of-restricted-mode-xss-to-rce-in-visual-studio-code/
Trend Zero Day Initiative
thezdi@infosec.exchangeThe schedule for #Pwn2Own Berlin is now live! We have three days of exploitation set - including our first AI entries. https://www.zerodayinitiative.com/blog/2025/5/14/pwn2own-berlin-the-full-schedule #P2OBerlin
Peter Cohen
flargh@mastodon.socialdays like today I remember to do my breathing exercises and gently remind myself this is nothing an extinction level event cant fix
mahaloz
mahaloz@infosec.exchangeWhat does it mean to be a hacker? This semester, I taught a hacker history and culture class, which was a blast. In one assignment, my students paid tribute to the classic @phrack Pro-Phile -- a small bio on a famous hacker. Check out their pieces: https://cse194.mahaloz.re/prophiles.html
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@eupolicy.socialYes, hello! If you were following @bert_hubert@fosstodon.org you should have been redirected automatically to following this new account. And if not, if you are still interested in my ramblings, please follow this account manually. Can I ask for retoots so the people that might be interested see this news? Thanks!