Posts
2916Following
693Followers
1518Open Source Security mailing list
oss_security@bird.makeupCVE-2024-28956: Xen Security Advisory 469 v2: x86: Indirect Target Selection https://www.openwall.com/lists/oss-security/2025/05/12/5
A bug in the hardware support for prediction-domain isolation. An attacker might be able to infer the contents of arbitrary host memory, including memory assigned to other guests.
buherator
buheratorhttps://bsky.app/profile/tannerofthenorth.bsky.social/post/3lp572utm5c2c
h/t @neurovagrant
#fromBsky
LaurieWired
lauriewired@bird.makeupWhat happens if a cosmic ray hits a voting machine?
In Belgium’s 2003 elections, a relatively unknown Communist Party candidate received 4096 extra votes…from a spontaneous bit inversion.
It was more votes than was mathematically possible at that polling station.
buherator
buheratorhttps://threadreaderapp.com/thread/1922015999118680495.html
buherator
buheratorhttps://www.politico.eu/article/viktor-orban-fidesz-party-hungary-russia-democracy-transparency-public-life-civil-society/
The darkest times of my life in #Hungary.
buherator
buheratorhttps://blog.trailofbits.com/2025/05/14/the-cryptography-behind-passkeys/
buherator
buheratorhttps://codeanlabs.com/blog/research/cve-2025-32464-overflowing-haproxy-regsub-converter/
tante
tante@tldr.nettime.orgI think the most tragic aspect of deploying "AI" in teaching and learning situations is how much it pushes people into a situation of learned helplessness. This constant feeling of not knowing how to do a thing of being incapable of actually doing work on one's tasks is mentally so harmful. How do people under those conditions gain confidence in their abilities? Like ever?
Alex Plaskett
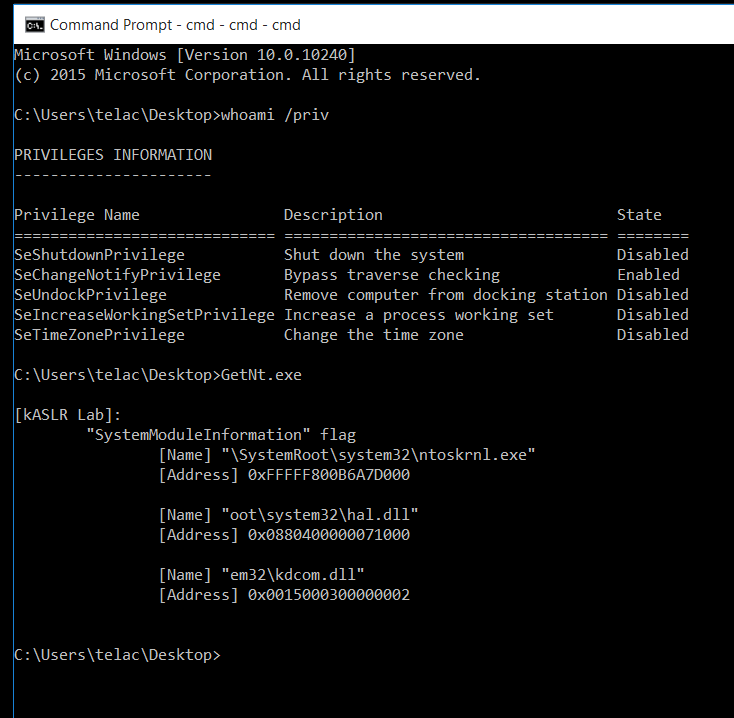
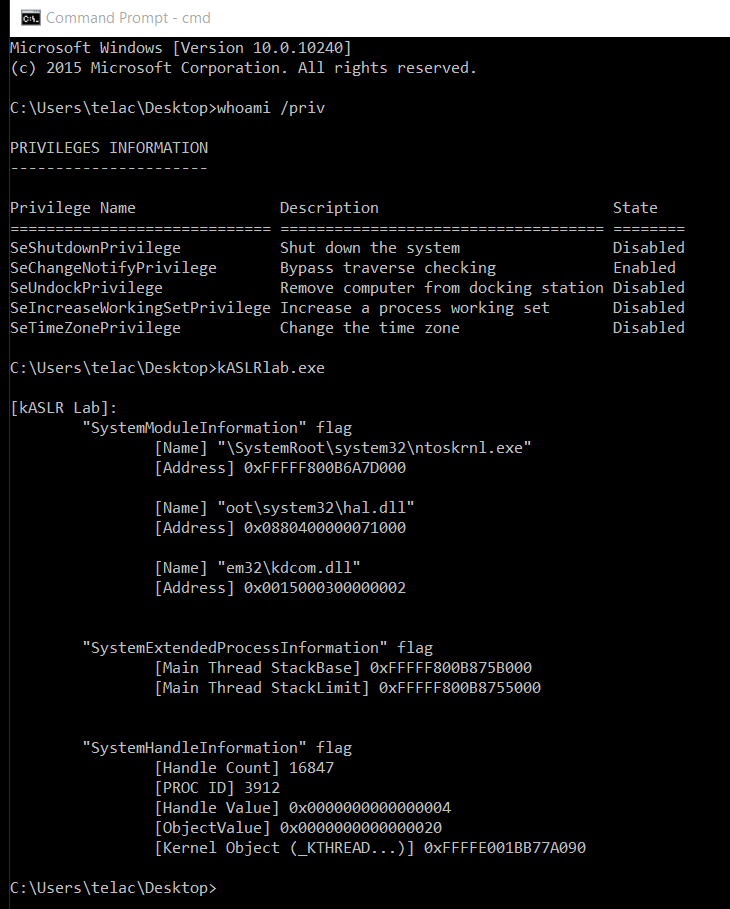
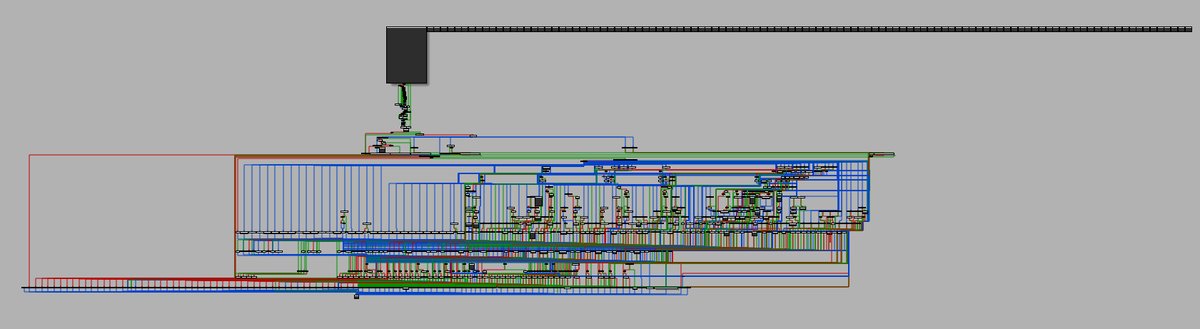
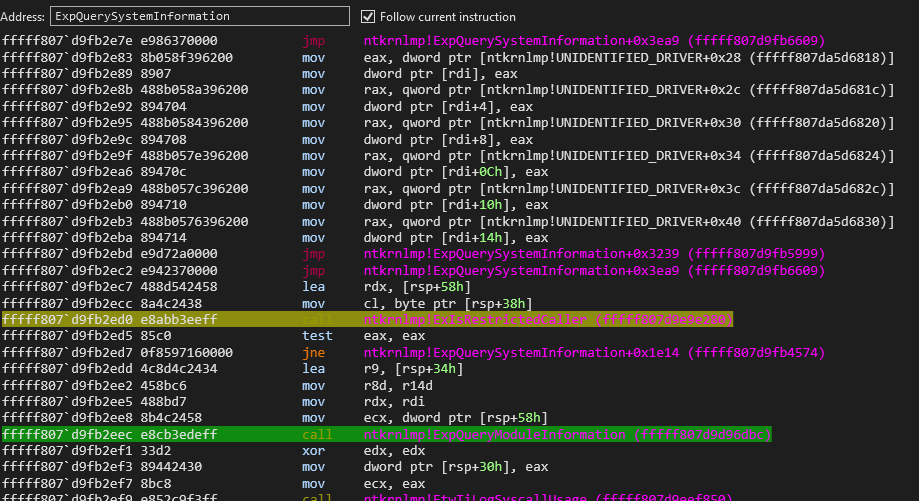
alexjplaskett@bird.makeupkASLR Internals and Evolution by @r0keb
https://r0keb.github.io/posts/kASLR-Internals-and-Evolution/
Pwnie Awards
pwnieawards@bird.makeupGreat news! The Pwnie awards nominations are now open!
https://pwnies.com/nominations/
tante
tante@tldr.nettime.org"If all these big companies are shouting from the rooftops that AI is up to production code the money relies on, then zero open source contributions of substance is a glaring absence."
(Original title: If AI is so good at coding … where are the open source contributions?)
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeThis week’s exciting instalment of Security Vulnerabilities that would be deterministically mitigated by #CHERI is a multi-part series sponsored by #Apple.
Media decoders are trivial to sandbox on a CHERI system (around four lines of code). They take an input buffer and produce an output. They can run with write access to that output buffer and nothing else. An attacker who gains arbitrary-code execution in an image decoder, for example, gains the ability to write an image to the output buffer: exactly the same rights that someone who can substitute a different image file has already.
Trend Zero Day Initiative
thezdi@infosec.exchangeAdobe's patches are (finally) out. 13 bulletins addressing 40 CVEs in Cold Fusion, Lightroom, Dreamweaver, Connect, InDesign, Substance 3D Painter, Photoshop, Animate, Illustrator, Bridge, Dimension, Stager, & Modeler. The patch blog has been updated. https://www.zerodayinitiative.com/blog/2025/5/13/the-may-2025-security-update-review
buherator
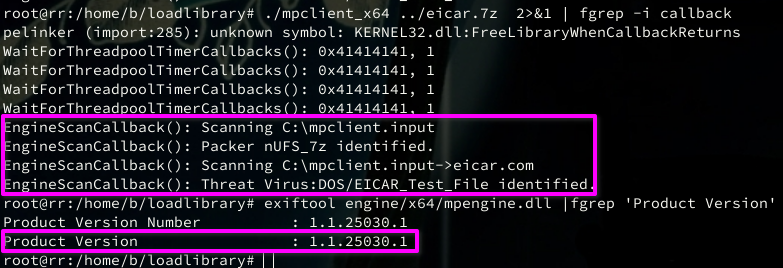
buheratorhttps://scrapco.de/blog/fuzzing-windows-defender-with-loadlibrary-in-2025.html
#PatchTuesday
../kajer/.
kajer@infosec.exchangeIn case you thought CTRL-F in chromium was useless... Microsoft has your back. https://www.neowin.net/news/microsoft-removes-a-lot-of-features-from-the-edge-browser/
Find on Page in Microsoft Edge for Business will soon be integrated with Microsoft 365 Copilot Chat. Microsoft Edge for Business is introducing Microsoft 365 Copilot Chat to Find on Page (CTRL+F). This feature seeks to help users more easily find relevant content and save time. Note: This is a controlled feature rollout. If you don't see this feature, check back as we continue our rollout.
Trend Zero Day Initiative
thezdi@infosec.exchangeWhile the #Adobe patches are still missing, the #Microsoft patch Tuesday rolls on with 5 0-days being exploited in the wild. Join @TheDustinChilds as he breaks down the release and calls out some familiar components. https://www.zerodayinitiative.com/blog/2025/5/13/the-may-2025-security-update-review
Jan Schaumann
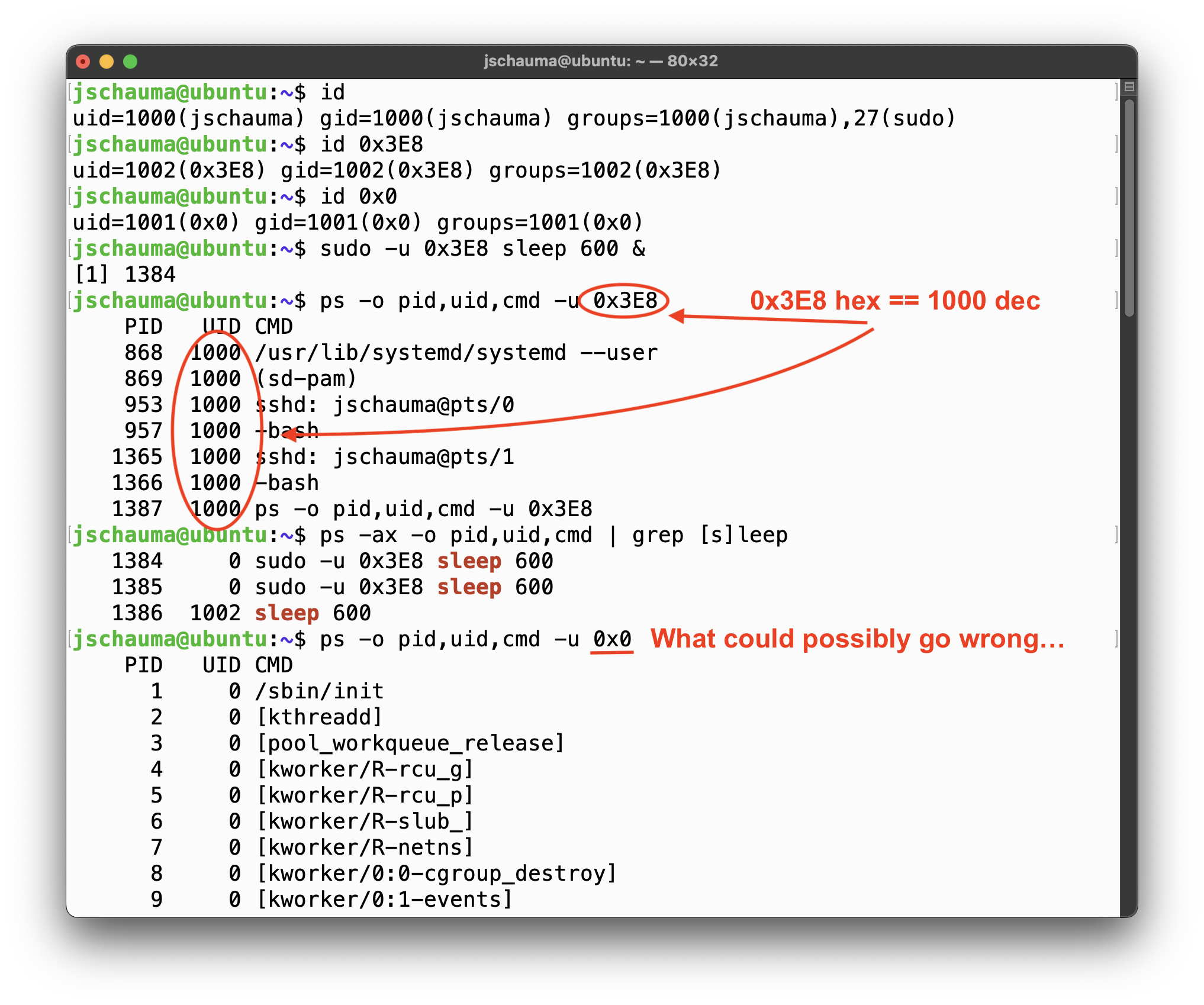
jschauma@mstdn.socialPffft *spits coffee all over keyboard*
So apparently on #Linux, usernames starting with "0x" are interpreted as hex numbers under certain circumstances. 🤪 That seems like asking for trouble...
buherator
buheratorhttps://seclists.org/oss-sec/2025/q2/126
"malformed ORC files can cause the decompressor to allocate a 250-byte buffer but then attempts to copy 295 bytes into it"
nixCraft 🐧
nixCraft@mastodon.socialThe European Vulnerability Database (EUVD) is now fully operational, offering a streamlined platform to monitor critical and actively exploited security flaws amid the US struggles with budget cuts, delayed disclosures, and confusion around the future of its own tracking systems https://euvd.enisa.europa.eu/