Posts
2929Following
697Followers
1538
Lee Holmes 
Lee_Holmes@infosec.exchange
It makes me super uncomfortable that globbing in Bash can turn into code execution. The fact that the name of a file can change the behavior of ls is scary. This also works for other commands that you tend to glob with, such as rm.
sam4k
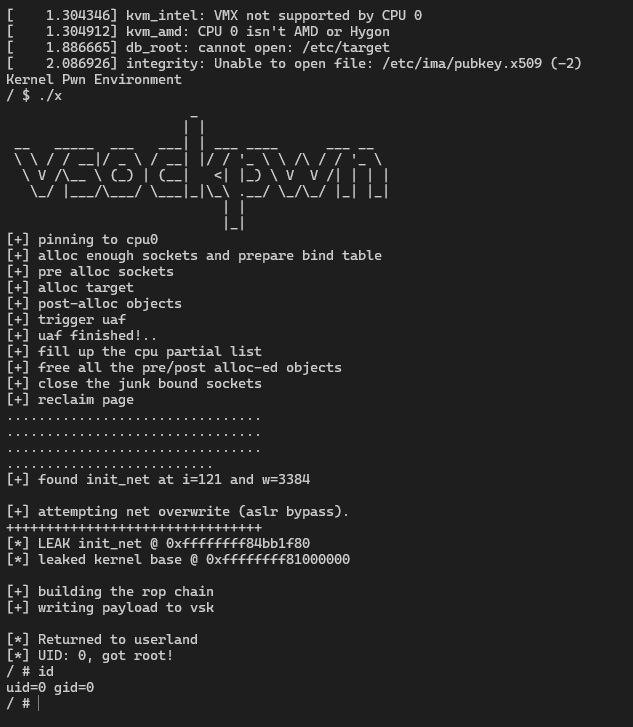
sam4k@infosec.exchangewith offensivecon around the corner, i figured id write another post on linux kernel exploitation techniques - this time i cover the world of page table exploitation! enjoy 🤓
Wikipedia
wikipedia@wikis.worldWhile we wait, here's a quick look at the web traffic currently hitting Wikimedia projects — can you perhaps guess when the reports of white smoke from the Vatican first started?
adafruit
adafruit@mastodon.cloudTariffs just got real: our first $36K bill with 125% + 20% + 25% markup hits hard 💸. These are upfront costs - due before selling a single unit - causing serious cash flow strain, price increases, read more! 📦 http://adafruit.com/tariffbill
Open Rights Group
openrightsgroup@social.openrightsgroup.orgWikipedia @wikimediauk are going to court over the UK Online Safety Act!
Saddling platforms with hefty duties and penalties under the new regime will cause many safe sites to fold.
We can't lose the best of the web due to laws that were meant to tackle the worst of it.
https://www.bbc.co.uk/news/articles/c62j2gr8866o
#OnlineSafetyAct #OSA #NetPlurality #ukpol #ukpolitics #wikipedia #freedomofexpression
buherator
buheratorhttps://chronicles.mad-scientist.club/tales/conversations-with-an-artificial-intelligence/
Thing is, we've seen this before, played with it, found its limits and got bored. Of course LLM's provide much better results, but I still don't think the underlying principle is that much different.
Same with shitcoins: we designed a proof-of-work system as teenagers for password cracking, so the principle is not magical to us and this goes against the marketing.
Pen Test Partners
PTP@infosec.exchangeMicrosoft Copilot for SharePoint just made recon a whole lot easier. 🚨
One of our Red Teamers came across a massive SharePoint, too much to explore manually. So, with some careful prompting, they asked Copilot to do the heavy lifting...
It opened the door to credentials, internal docs, and more.
All without triggering access logs or alerts.
Copilot is being rolled out across Microsoft 365 environments, often without teams realising Default Agents are already active.
That’s a problem.
Jack, our Head of Red Team, breaks it down in our latest blog post, including what you can do to prevent it from happening in your environment.
📌Read it here: https://www.pentestpartners.com/security-blog/exploiting-copilot-ai-for-sharepoint/
#RedTeam #OffSec #AIsecurity #Microsoft365 #SharePoint #MicrosoftCopilot #InfoSec #CloudSecurity
Linux Kernel Security
linkersec@infosec.exchangeCVE-2025-21756: Attack of the Vsock
Michael Hoefler published an article about exploiting an incorrect reference counter decrement causing a UAF in the vsock subsystem.
With advice from h0mbre, the researcher used brute force to bypass KASLR and hijacked the control flow for LPE.
Royce Williams
tychotithonus@infosec.exchangeReally hoping that the title of the W3C's position paper "Third-Party Cookies Must Be Removed":
https://w3c.social/@w3c/114432468864338537
... is a deliberate echo of "Carthage must be destroyed":
Filippo Valsorda
filippo@abyssdomain.expertThe AWS team published a key-committing variant (https://eprint.iacr.org/2025/758.pdf) of XAES (https://words.filippo.io/xaes-256-gcm/)!
Still FIPS-compliant, and with a proof.
Key commitment ensures the ciphertext can only be decrypted with one key, to avoid issues in higher-level protocols.
“Anonymous has decided to enforce the Judge's order since you and your sycophant staff ignore lawful orders that go against your fascist plans,”
GlobalX, Airline for Turnip’s Deportations, Hacked
https://www.404media.co/globalx-airline-for-trumps-deportations-hacked/
Insinuator
Insinuator@infosec.exchangeNew post: Disclosure: Input Validation Vulnerabilities in Microsoft Bookings https://insinuator.net/2025/05/disclosure-input-validation-vulnerabilities-in-microsoft-bookings/
S3cur3Th1sSh1t
shitsecure@bird.makeupBlogpost from my colleague about what’s still possible with recently published COM/DCOM toolings, Cross Session Activation and Kerberos relaying 🔥
https://www.r-tec.net/r-tec-blog-windows-is-and-always-will-be-a-potatoland.html
Claudius Link
realn2s@infosec.exchangeJust read an article from an #ai influencer musing on the Innovative power of AI.
(Edit 2: while linked articles a current / May 2025 they refer to an event in 2017 🤪 )
Tasked with breaking the Enigma code, an AI system trained to recognise German using Grimm’s fairytales, utilizing 2,000 virtual servers, cracked a coded message in 13 minutes.
Let's pause for a second to let it sink.
And let's think for a second
Alan Turing “Bombes” could decipher two messages every minute.
😱 Suddenly the AI result isn't all that impressive any more.
AI cuts out all the research, knowledge gain, and insight. With all the resources available today, it still performs worse than a solution from 70 years ago (to be precise 26 times).
And this is seen as an impressive innovation 🤡🤯
"Sources":
Influencer post https://mastodon.social/@Caramba1/114470245795906227
Guardian article
https://www.theguardian.com/science/2025/may/07/todays-ai-can-crack-second-world-war-enigma-code-in-short-order-experts-say
Alex Plaskett
alexjplaskett@bird.makeupBiting the CHERI bullet: Blockers, Enablers and Security Implications of CHERI in Defence
Trend Zero Day Initiative
thezdi@bird.makeupAn analysis of CVE-2024-44236 - an RCE in macOS due to the lack of proper validation of “lutAToBType” and “lutBToAType” tag types. Read the details, see the source code review, and get detection guidance at https://www.zerodayinitiative.com/blog/2025/5/7/cve-2024-44236-remote-code-execution-vulnerability-in-apple-macos
blacktop
blacktop@mastodon.socialGet your macOS 15.4 xnu CodeQL database here! 👩🔬
Also NOW includin the compile_commands.json 🎉
(I also wrote a util for converting the paths github.com/blacktop/ccpaths)
`ccpaths JSON /Users/runner/work/darwin-xnu-build/darwin-xnu-build /path/to/your/xnu`
https://github.com/blacktop/darwin-xnu-build/releases/tag/v15.4
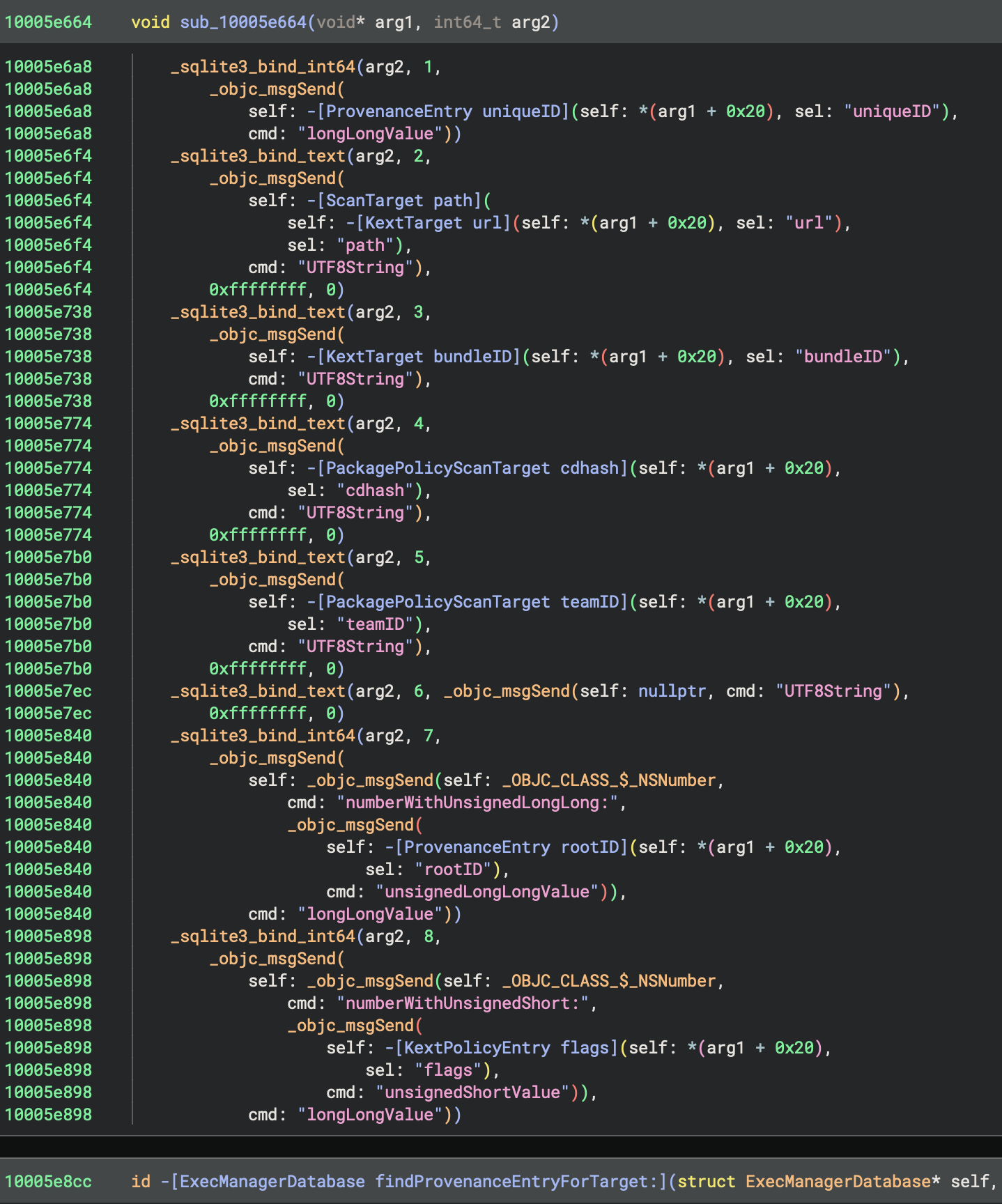
bdash
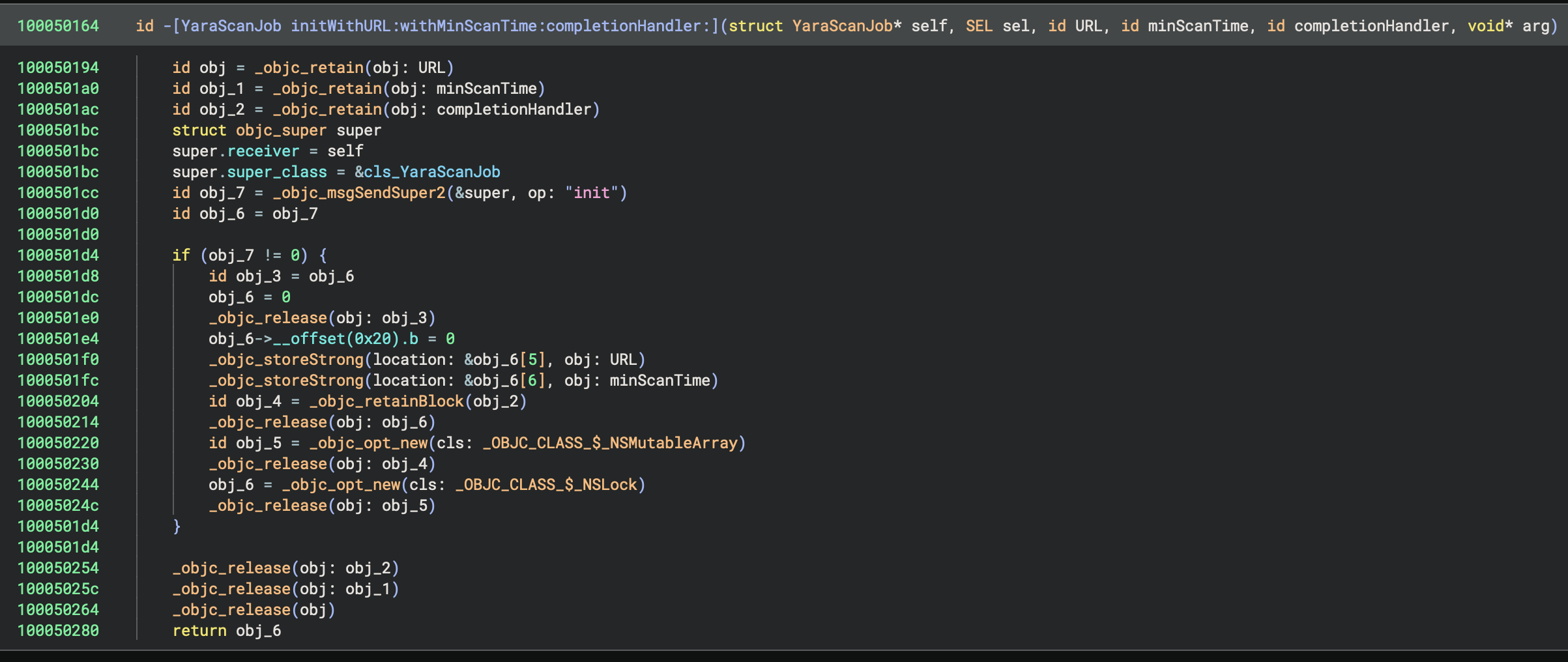
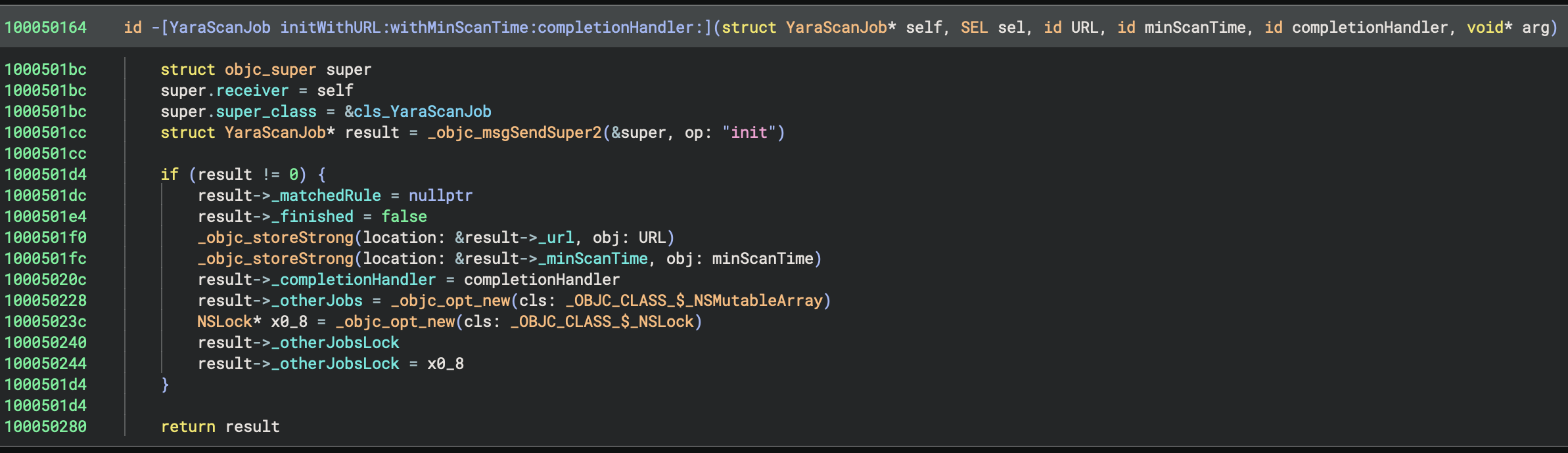
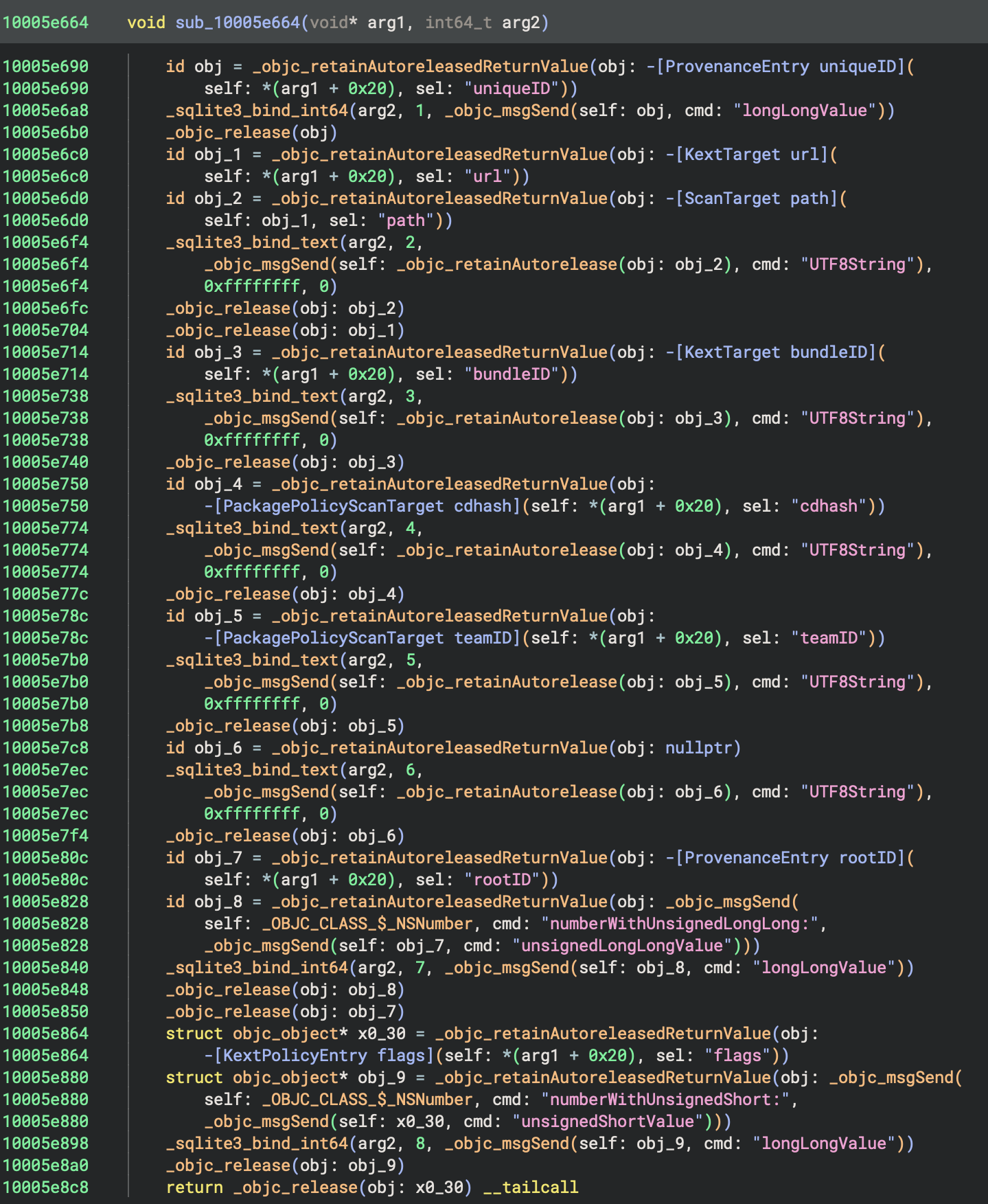
mrowe@bdash.net.nzI've been experimenting with improving Binary Ninja's analysis of Objective-C code recently. Having the ability to hide Obj-C runtime reference counting calls, and apply type information based on [super init] and objc_alloc_init calls can dramatically improve the readability (and in some cases even accuracy!) of the decompiled code.