Posts
2931Following
697Followers
1538real tournament when unreal tournament walks in 💽 --> 39c3
domi@donotsta.re
Slashdot 
slashdot@mastodon.cloud
VMware Perpetual License Holders Receive Cease-And-Desist Letters From Broadcom https://yro.slashdot.org/story/25/05/07/1856255/vmware-perpetual-license-holders-receive-cease-and-desist-letters-from-broadcom?utm_source=rss1.0mainlinkanon
buherator
buheratoralexandra
xandra@tilde.zoneonly FOUR DAYS left in our spring tea party coding event!
help create a template, theme, or layout for new and seasoned website owners to create their own websites easily!
submissions close may 11!~
#webdev #smallweb #indieweb #codejam #web #webdesign #handmadeweb #coding #codingisart #html #css #internet #neocities #nekoweb #website #personalwebsite #openinternet #foss #opensource
Dmytro Oleksiuk
d_olex@mastodon.socialI’m sorry, but Facebook did more harm to humankind than all NSO-alike spyware vendors of the world altogether. You are fighting into the wrong direction
Cindʎ Xiao 🍉
cxiao@infosec.exchangeNext Thursday, May 15 at @NorthSec in Montreal, I will be hosting the workshop "Reconstructing Rust Types: A Practical Guide for Reverse Engineers"! This will be a 3-hour workshop how to approach Rust types and data structures when reversing Rust binaries. See https://nsec.io/session/2025-reconstructing-rust-types-a-practical-guide-for-reverse-engineers.html for more details!
Workshops at NorthSec will be streamed on YouTube Live. My workshop is scheduled for 1300-1600 EDT (UTC-4) on Thursday, May 15 in the Workshop 2 track, in Salle de la Commune. The stream link for all the Thursday Salle de la Commune workshops is here: https://www.youtube.com/watch?v=UwJgS32Q6As&list=PLuUtcRxSUZUrW9scJZqhbiuTBwZBJ-Qic&index=7
Looking forward to seeing folks there! 🦀
(Edited since I can't count days of the week apparently: May 15, which is when my workshop is occurring, is a Thursday, not a Wednesday.)
#rustlang #ReverseEngineering #MalwareAnalysis #NorthSec #infosec #reversing
buherator
buheratorhttps://therecord.media/jury-orders-nso-to-pay-meta-168-million-over-whatsapp-hack
buherator
buheratorhttps://lore.kernel.org/all/bb0a1948-d418-4720-97bf-4aceb30ea787@intel.com/t/#u
Guess I'll just run the fuzzer on the host then?
buherator
buheratorhttps://www.ibm.com/support/pages/node/7232750?myns=swgother&mynp=OCSWG60&mynp=OCSSC5L9&mynp=OCSSKWKM&mynp=OCSSTS2D&mynp=OCSSB23CE&mynp=OCSS9QQS&mync=A&cm_sp=swgother-_-OCSWG60-OCSSC5L9-OCSSKWKM-OCSSTS2D-OCSSB23CE-OCSS9QQS-_-A
The Zen and Art of Obfuscating Vulnerability Information (CWE-295?!)
buherator
buheratorhttps://labs.watchtowr.com/sysowned-your-friendly-rce-support-ticket/
buherator
buheratorhttps://medium.com/@cy1337/tracing-data-flow-with-pcode-f879278d9fc1
/r/netsec
_r_netsec@infosec.exchangeKnown Exploited Vulnerabilities Intel https://kevintel.com
abadidea
0xabad1dea@infosec.exchangeIt turns out that MrDeepFakes' sudden voluntary shutdown a few days ago was because Bellingcat was on their tail. https://www.bellingcat.com/news/2025/05/07/canadian-pharmacist-linked-to-worlds-most-notorious-deepfake-porn-site/
CONTENT WARNING: this article is a dox on someone credibly accused of running a nonconsensual porn site
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgEveryone agrees something needs to be done about our total dependence on US clouds. But what? And who should do it? Ample words have been written on the 'why', and we also have a lot of text on our values and that *someone* should do *something*. Here I elaborate on an earlier suggestion with a coherent strategy that is concrete enough to disagree with. This reads well with the latest Euro-Stack letter also: https://berthub.eu/articles/posts/a-coherent-non-us-cloud-strategy/
hanno
hanno@mastodon.socialThis is a gruelling summary of all the things wrong with OpenSSL https://www.haproxy.com/blog/state-of-ssl-stacks I've mostly watched this whole thing from the sidelines, but was also affected noting that private key parsing suddenly became 70 times slower. I think they've now improved it to "only" be 10-20 times slower, and there does not seem any effort to work on it any more.
Marco Ivaldi
raptor@infosec.exchangeAndrey Konovalov
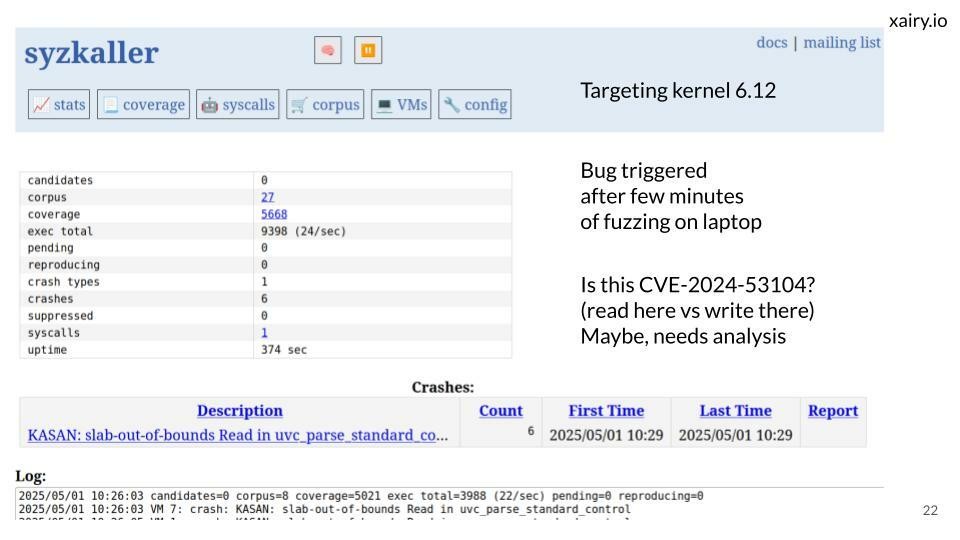
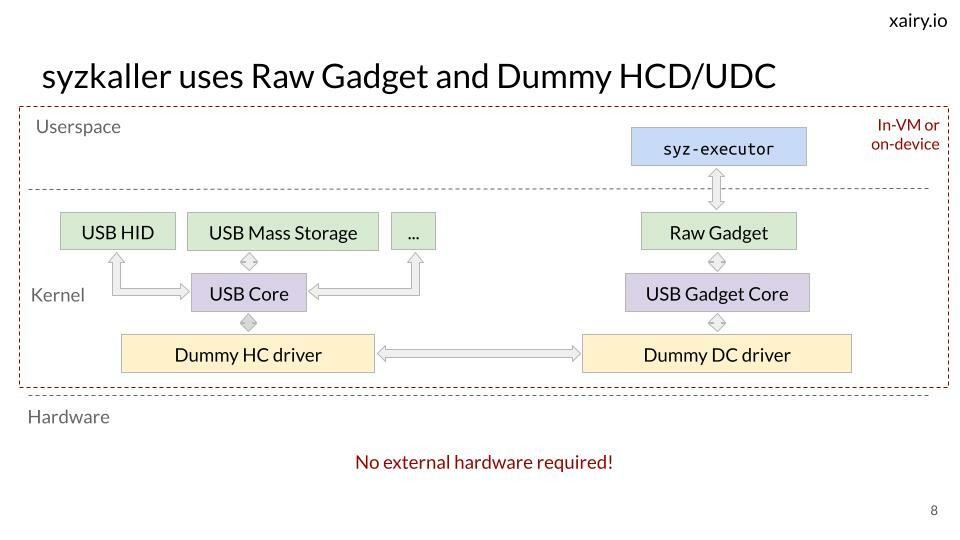
xairy@infosec.exchangeGave a talk on external fuzzing of Linux kernel USB drivers with syzkaller at SAFACon.
Includes a demonstration of how to rediscover CVE-2024-53104, an out-of-bounds bug in the USB Video Class driver.
Slides: https://docs.google.com/presentation/d/1NulLxRowsHzgcL1AFzNF_w8nh3zk2BKKPfGi_1j76A8/edit?usp=sharing
(If you use newer Ubuntu and the code formatting looks off, use File → Print preview; @ubuntu still hasn't fixed the issues with their monospace fonts.)
CISA KEV Tracker
cisakevtracker@mastodon.socialCVE ID: CVE-2025-27363
Vendor: FreeType
Product: FreeType
Date Added: 2025-05-06
Vulnerability: FreeType Out-of-Bounds Write Vulnerability
Notes: This vulnerability affects a common open-source component, third-party library, or a protocol used by different products. Please check with specific vendors for information on patching status. For more information, please see https://source.android.com/docs/security/bulletin/2025-05-01 ; https://nvd.nist.gov/vuln/detail/CVE-2025-27363
CVE URL: https://nvd.nist.gov/vuln/detail/CVE-2025-27363
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.5 beta 4 vs. iOS 18.5 RC 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_5_22F5068a__vs_18_5_22F75/README.md