Posts
2559Following
621Followers
1372ɗ𐐩ʃƕρʋ
deshipu@fosstodon.orgThere is more cost to programming assistants than I have realized. I was recently talking with a friend, and I mentioned a new programming language that has some interesting features. The friend told me that they won't try it, because the programming assistant doesn't support it, because there aren't enough examples out there to train it.
We are literally throwing away innovation and diversity in exchange for convenience.
tmp.0ut
tmpout@bird.makeupWould you look at that, it's tmp.0ut Volume 4! Happy Friday, hope you enjoy this latest issue!
Juhis
hamatti@mastodon.world"How do you deal with code snippets in blog posts getting outdated?"
Every time I give a talk about blogging for developers, I'm asked this. Now I started to take action with the first iteration of the solution.
I added version metadata to my blog posts and display them at the start of the post.
https://hamatti.org/posts/track-software-versions-for-technical-blog-posts/
Programming Quotes
programming_quotes@mastodon.socialWe're programmers. Programmers are, in their hearts, architects, and the first thing they want to do when they get to a site is to bulldoze the place flat and build something grand. We're not excited by incremental renovation: tinkering, improving, planting flower beds.
— Joel Spolsky
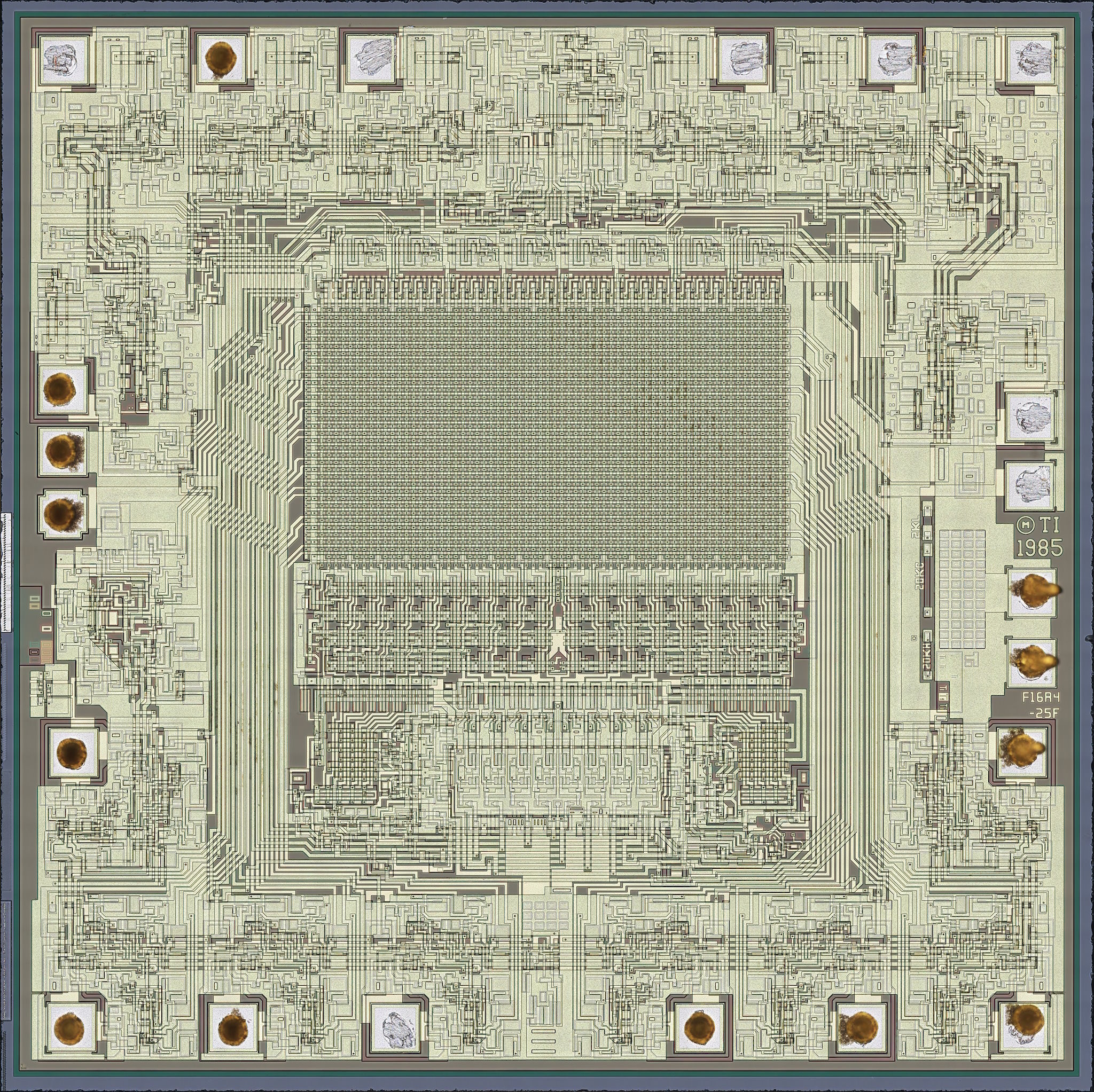
Hello and welcome to this week's installment of #nakeddiefriday !
The guest of today is the TIBPAL16R4 by TI, a programmable array logic chip made with bipolar logic. The die has 2 metal layers, its maskwork produced in 1985. A short thread follows.
More info and hi-res pano at: https://siliconpr0n.org/archive/doku.php?id=infosecdj:ti:tibpal16r4
#electronics #reverseengineering #microscopy #icreverseengineering
Filippo Valsorda 
filippo@abyssdomain.expert
It’s disheartening to see AI reactionism lead my community to a 180° on copyright.
Everyone is merrily attacking LibGen now. If it didn’t exist, big tech companies would still find training data, it just wouldn’t be accessible to regular people.
buherator
buheratorhttps://projectdiscovery.io/blog/discourse-backup-disclosure-rails-send_file-quirk
This is CVE-2024-53991
buherator
buheratorhttps://swarm.ptsecurity.com/last-barrier-destroyed-or-compromise-of-fuse-encryption-key-for-intel-security-fuses/
Marco Ivaldi
raptor@infosec.exchangeRejoice! 🎉
My idalib-based vulnerability research tools are now fully compatible with Windows 🪟
Please test them and report any bugs 🪲
https://security.humanativaspa.it/streamlining-vulnerability-research-with-ida-pro-and-rust/
(PS. Ya like my GPT writing style? 🚀)
CFG Bot 🤖
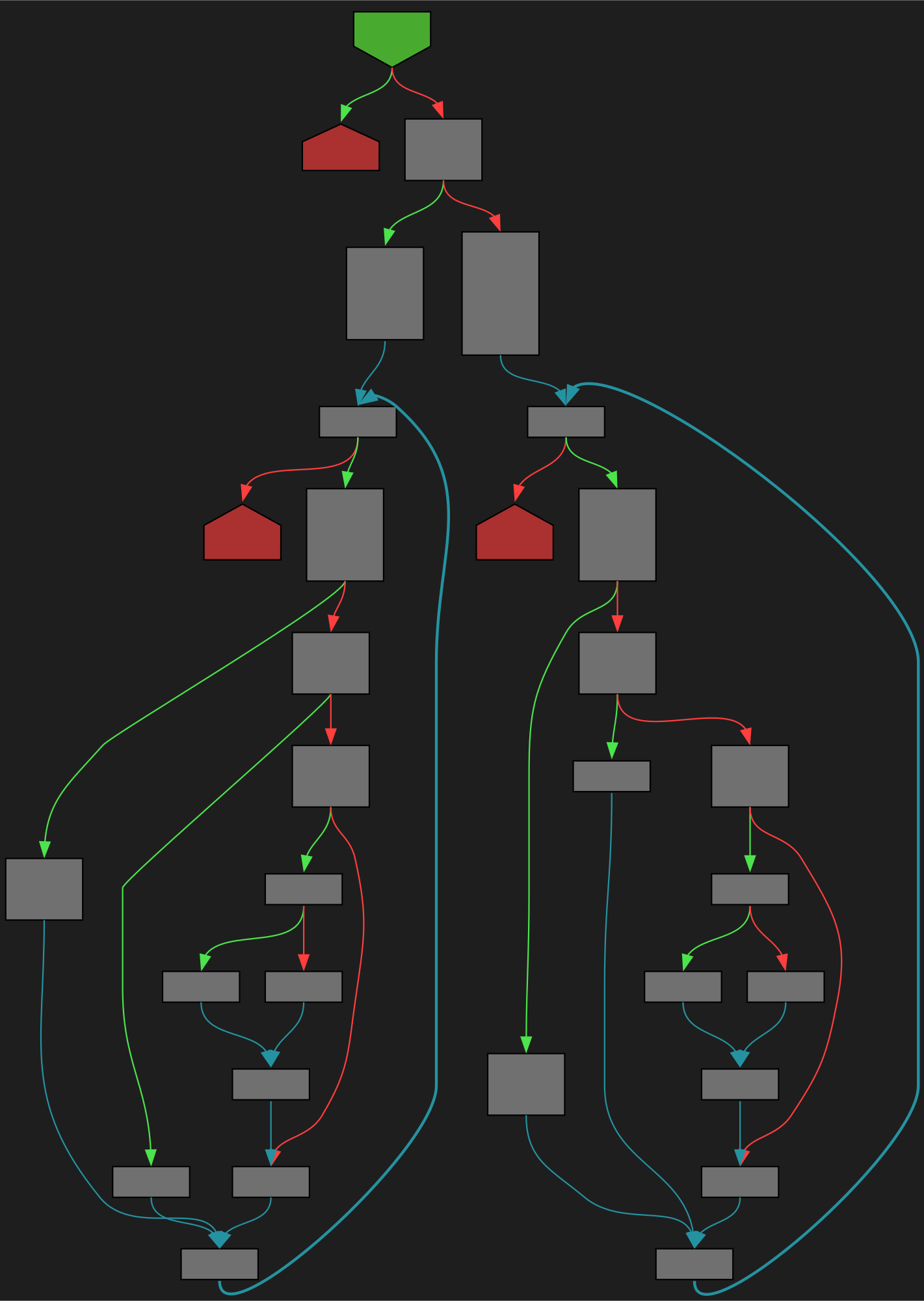
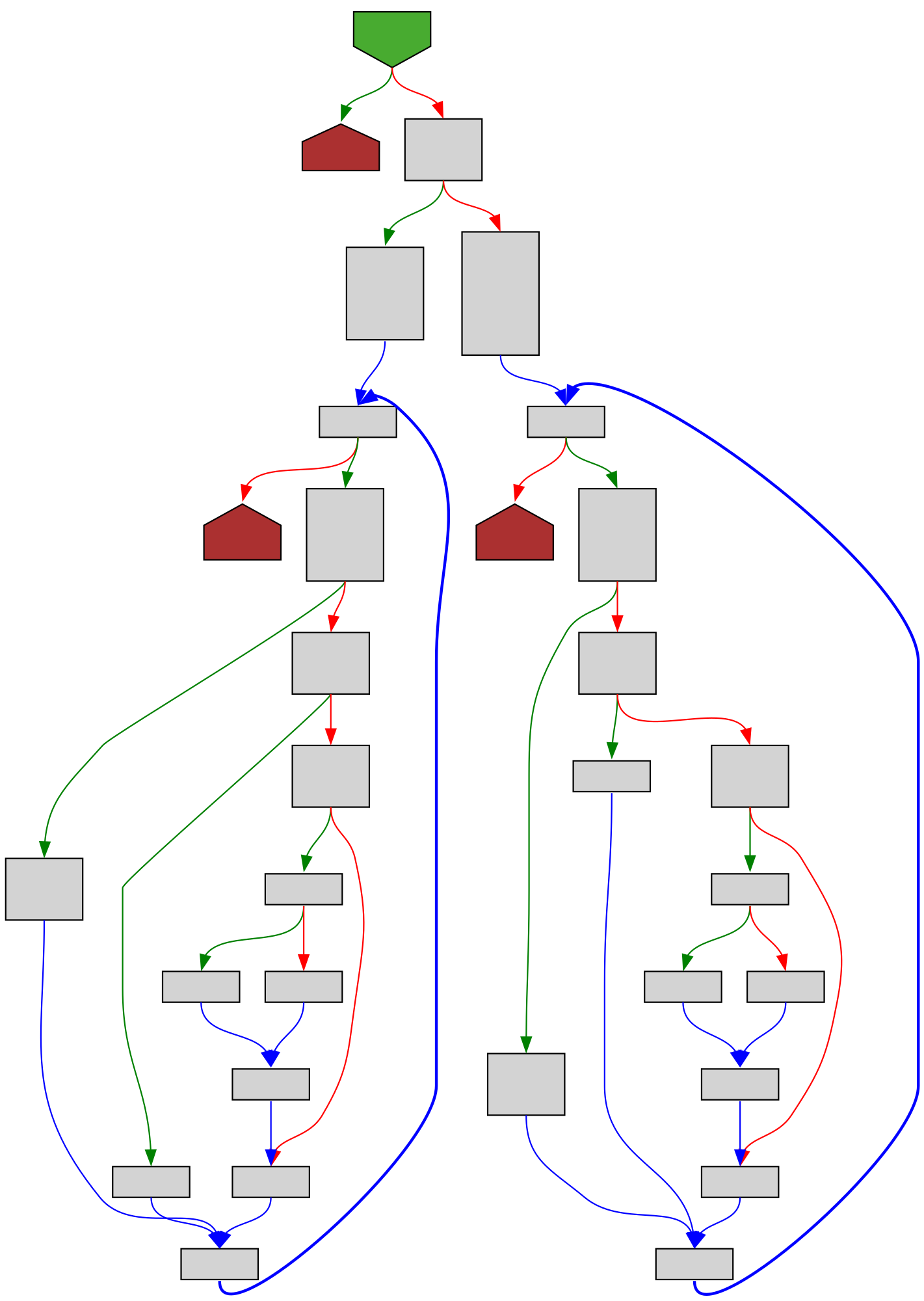
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/compile/internal/abt/avlint32.go:175 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/compile/internal/abt/avlint32.go#L175
func (t *T) Intersection(u *T, f func(x, y interface{}) interface{}) *T
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fabt%2Favlint32.go%23L175&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fabt%2Favlint32.go%23L175&colors=light
Ryan Castellucci 
ryanc@infosec.exchange
"But Ryan, the C preprocessor isn't a programming language!"
Skill issue.
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeThe official website of zero-day broker Zerodium has been updated in December of last year. There are no price lists nor any information anymore, just an email and a PGP public key.
🤔
If you know what's happening there...let me know.
Project Zero Bot
p0botmsm_npu: Race between npu_host_unload_network and npu_host_exec_network_v2 leads to memory corruption
https://project-zero.issues.chromium.org/issues/380081941
CVE-2025-21424
buherator
buheratorhttps://seclists.org/oss-sec/2025/q1/234
"The order in which objects are deleted
during namespace termination is not defined, and it is possible for network
policies to be deleted before the pods that they protect." whoops :)
I don't recall seeing a CVE for a WAF lib bypass before but here you go, add it to your tricks if it isn't already there.
https://github.com/corazawaf/coraza/security/advisories/GHSA-q9f5-625g-xm39
sev:MED 5.4 - CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:C/C:L/I:L/A:N
OWASP Coraza WAF is a golang modsecurity compatible web application firewall library. Prior to 3.3.3, if a request is made on an URI starting with //, coraza will set a wrong value in REQUEST_FILENAME. For example, if the URI //bar/uploads/foo.php?a=b is passed to coraza: , REQUEST_FILENAME will be set to /uploads/foo.php. This can lead to a rules bypass. This vulnerability is fixed in 3.3.3.