Posts
2579Following
624Followers
1379Molly White
molly0xfff@hachyderm.ioFor those just learning about LibGen because of the reporting on Meta and other companies training LLMs on pirated books, I’d highly recommend the book Shadow Libraries (open access: https://direct.mit.edu/books/oa-edited-volume/3600/Shadow-LibrariesAccess-to-Knowledge-in-Global).
I just read it while working on the Wikipedia article about shadow libraries, and it’s a fascinating history. https://en.wikipedia.org/wiki/Shadow_library
I fear the already fraught conversations about shadow libraries will take a turn for the worse now that it’s overlapping with the incredibly fraught conversations about AI training.
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250320-00/?p=110981
rev.ng
revng@infosec.exchangeLet's also talk about our failures!
We tried to make a consortium for a cool EU-funded project about malware analysis, but didn't manage to do it in time. 🫤
We'll try again! If you're an SME owned and controlled in the EU, feel free to get in touch 💪
Linux Kernel Security
linkersec@infosec.exchangeLinux kernel hfsplus slab-out-of-bounds Write
Outstanding article by Attila Szasz about exploiting a slab out-of-bounds bug in the HFS+ filesystem driver.
The author discovered that Ubuntu allows local (not remote/SSH'd) non-privileged users to mount arbitrary filesystems via udisks2 due to the used polkit rules. This includes filesystems whose mounting normally requires CAP_SYS_ADMIN in the init user namespace.
The article thoroughly describes a variety of techniques used in the exploit, including a cross-cache attack, page_alloc-level memory shaping, arbitrary write via red-black trees, and modprobe_path privilege escalation.
https://ssd-disclosure.com/ssd-advisory-linux-kernel-hfsplus-slab-out-of-bounds-write/
Sonar Research
SonarResearch@infosec.exchange🦘🛜Compromising bastion host to gain full control over the internal infrastructure.
Read more about the vulnerabilities we uncovered in JumpServer in our recent blog post:
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🌪️ TyphoonPWN is back for its 7th year at TyphoonCon! 💻💰
This year, we’re offering up to $70,000 for discovering and exploiting Linux Privilege Escalation vulnerabilities.
Remote participation is allowed, so grab your gear, sharpen your knowledge, and sign up: https://typhooncon.com/typhoonpwn-2025/
buherator
buheratorbuherator
buheratorhttps://x41-dsec.de/lab/advisories/x41-2025-001-OpenSlides/
DEY!
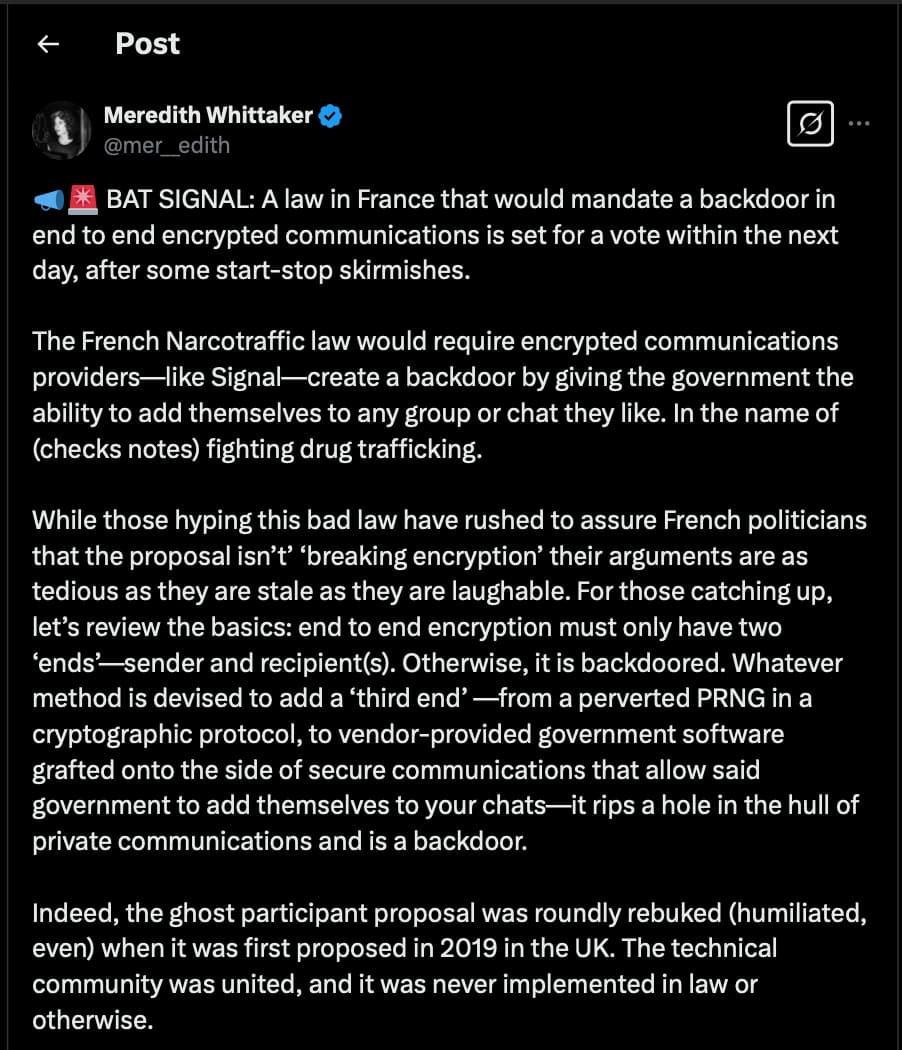
dey@mastodon.socialTHIS IS HUGE!
"Signal would exit the French market before it would comply with this law as written"
What next HTTPS?
@Mer__edith President of Signal
@signal.org
buherator
buheratorhttps://github.com/CoatiSoftware/Sourcetrail
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgUseful piece. Solar panels are largely cloud managed, and now in The Netherlands alone create the same power as 50 of our nuclear power plants. If you switch this 25GW on/off remotely, the consequences could be huge. And we do not regulate these cloud platforms at all: https://www.dw.com/en/how-hackers-capture-your-solar-panels-and-cause-grid-havoc/a-71593448
Piotr Bazydło
chudypb@infosec.exchangeIt seems that our Veeam CVE-2025-23120 post is live.
I would never do this research without @SinSinology He insisted a lot, thx man. 😅
If you know CVE-2024-40711, this vuln can be patch-diffed and exploit armed in 5 minutes. Unfortunately, it's super simple at this point.
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250319-00/?p=110979
Love the prank call example :D
RE//verse
reverseconf@bird.makeupOur first video from RE//verse 2025 is live! Part journey of personal discovery, part technical deep-dive, this presentation from Markus Gaasedelen was the highest rated in the feedback survey and is a must-see talk: https://youtu.be/hGlIkgmhZvc
Worty
_worty@bird.makeupMy writeup for the KalmarCTF challenge "no sqli" is out, covering the exploitation of CVE-2024-6382, an integer overflow in the Rust's MongoDB library. A very interesting challenge, enjoy! :)
Robert De Niro on a Netflix show (Zero Day) mentioning the O.MG Cable! 😎
Shoutout to whoever did the text, you got the silent punctuation perfectly.
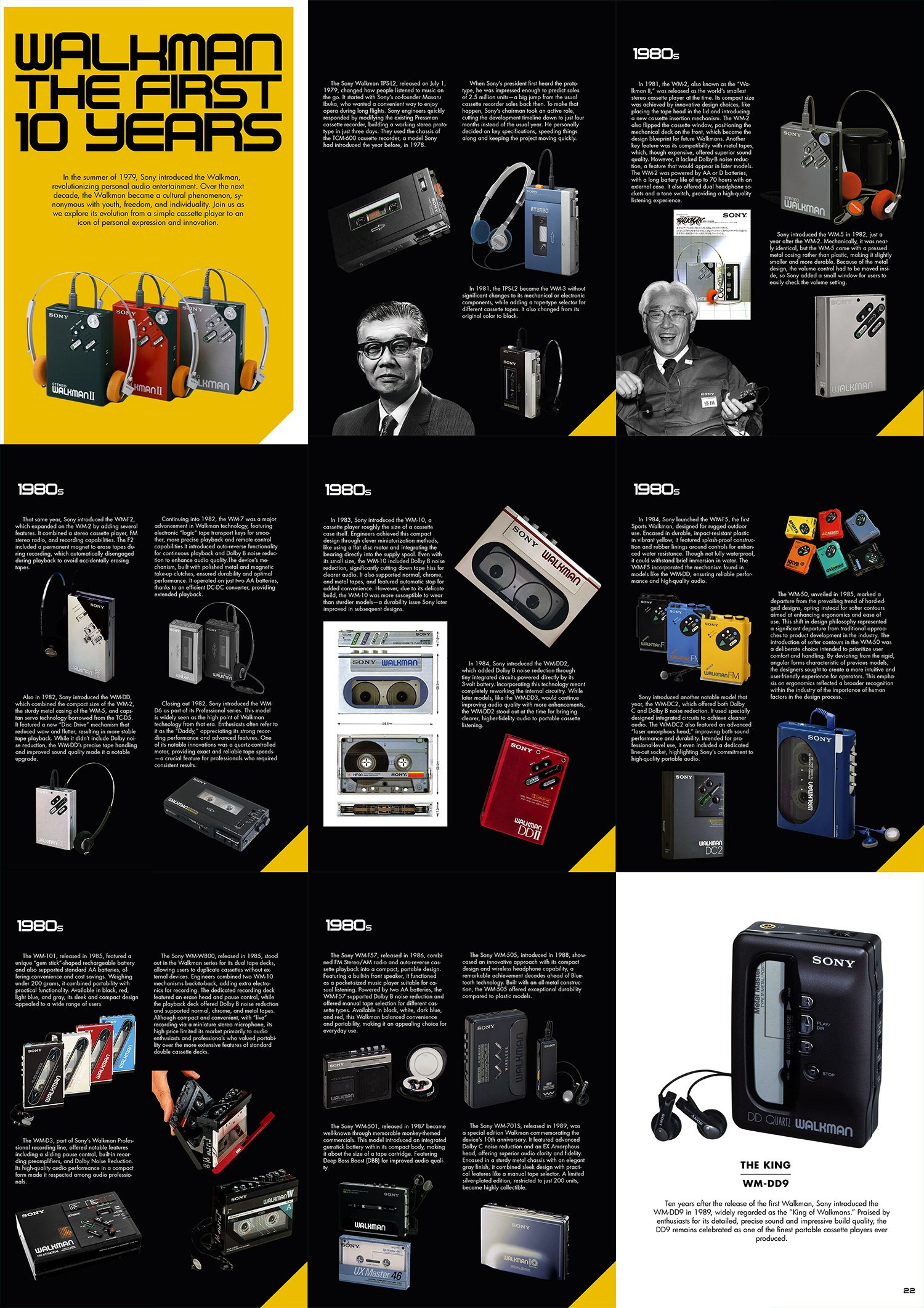
Obsolete Sony
obsoletesony@mastodon.worldThere’s been a lot written about the Walkman over the years, but no one has really focused on the first ten years to show how its early evolution took shape. Here’s a sneak peek of how the article is coming together. I can’t wait for you all to check it out in Issue 2! Download Issue 1 in PDF for FREE! https://www.patreon.com/posts/get-first-issue-123662381
Veeam isn't used to protect anything important, right? So a sev:CRIT 9.9 RCE shouldn't be a big deal.
A vulnerability allowing remote code execution (RCE) by authenticated domain users.
But it's cool because they're going to blame it on their customers:
Note: This vulnerability only impacts domain-joined backup servers, which is against the Security & Compliance Best Practices.