Posts
3373Following
712Followers
1579David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeUse of AI tools reduces critical thinking abilities. Frank Herbert looks more prophetic every day.
/r/netsec
_r_netsec@infosec.exchangeExploiting SSTI in a Modern Spring Boot Application (3.3.4) https://modzero.com/en/blog/spring_boot_ssti/
buherator
buheratorhttps://xia0.sh/blog/overview-of-wasm-in-jsengine-exploit?ref=blog.exploits.club
Project Zero Bot
p0botSamsung S24: Out of bounds write in APE Decoder
https://project-zero.issues.chromium.org/issues/368695689
CVE-2024-49415
buherator
buheratorThis company should not exist by now.
https://labs.watchtowr.com/do-secure-by-design-pledges-come-with-stickers-ivanti-connect-secure-rce-cve-2025-0282/
RE//verse Conference
REverseConf@infosec.exchangeOur 2025 RE//verse talk schedule is now live! Talks start Friday, but don't forget to check the Thursday schedule and arrive early enough for the kick-off event!
Arne Brasseur
plexus@toot.catOne of the most useful skills you get out of doing open source comes from learning to write READMEs.
Being able to describe a piece of software clearly and concisely in terms of
- what is is
- what it does
- how it does it
- why it does it that way
- how you use it
is a superpower that will you will be able to use throughout your career.
BrianKrebs
briankrebs@infosec.exchangePowerSchool, a provider of K-12 software and cloud solutions, had a breach over the holidays. But not to worry, they paid the cybercriminals who hacked them and they have a video of the crooks deleting the data.
"PowerSchool has received reasonable assurances from the threat actor that the data has been deleted and that no additional copies exist."
Thank goodness the threat actors are so reasonable, right? SMH.
Software Freedom Conservancy
conservancy@sfconservancy.orgdaniel:// stenberg://
bagder@mastodon.socialCongratulations all crowd strike users on macOS who now get warnings about the libcurl version shipped by Apple. May you all enjoy your choices of software vendors.
It alerts about CVE-2024-9681. We said it is severity low. NVD says 6.5 medium.
Never a dull moment.
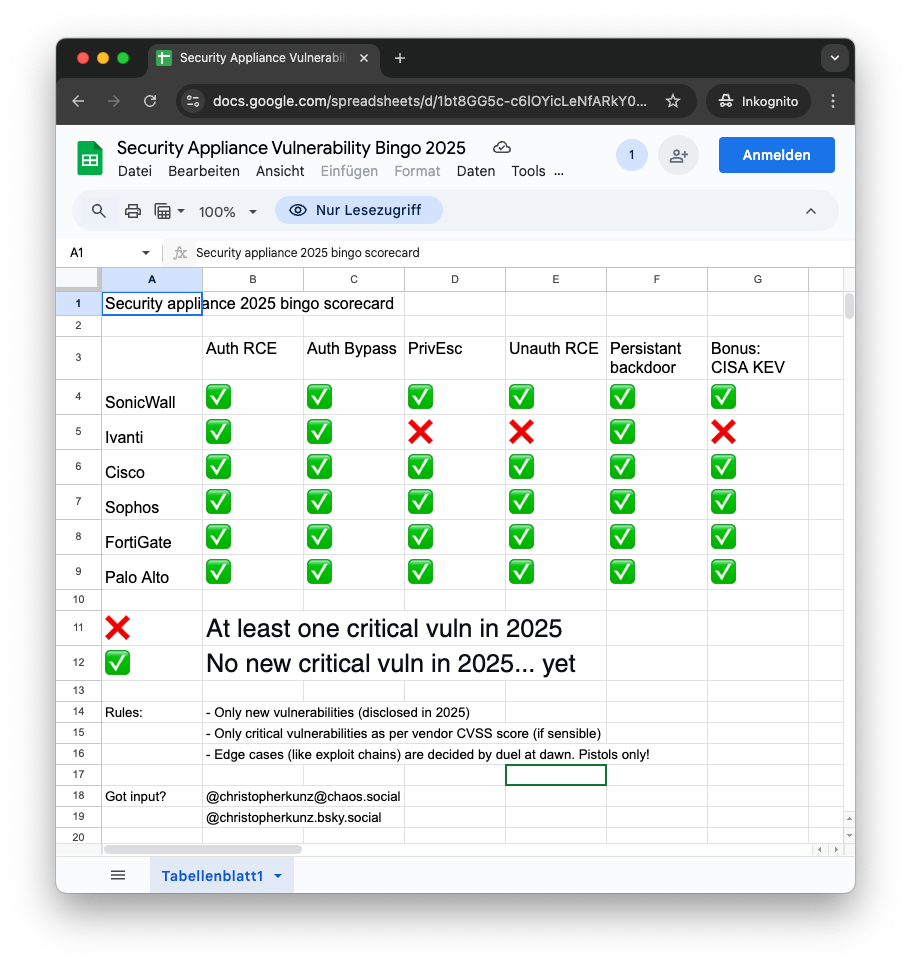
Dr. Christopher Kunz
christopherkunz@chaos.socialOK, I fleshed this out a little more. You can find the (In)Security Appliance Bingo 2025 in proper, two-dimensional form here:
Suggestions and submissions very welcome.
screaminggoat
screaminggoat@infosec.exchangeCrowdStrike: Recruitment Phishing Scam Imitates CrowdStrike Hiring Process
Following CrowdStrike's successful Denial of Service attack on customers' Windows systems worldwide in July 2024, recruitment has gone up (this is a joke). CrowdStrike reports that a newly discovered phishing campaign uses CrowdStrike recruitment branding to convince victims to download a fake application, which serves as a downloader for the XMRig cryptominer. They describe the infection chain and provide Indicators of Compromise.
#crowdstrike #IOC #xmrig #cryptomining #infosec #cybersecurity #cyberthreatintelligence #CTI
buherator
buheratorhttps://devco.re/blog/2025/01/09/worstfit-unveiling-hidden-transformers-in-windows-ansi/
James Kettle
albinowax@infosec.exchangeNominations are now open for the Top 10 Web (new) Hacking Techniques of 2024! Browse the contestants and submit your own here:
https://portswigger.net/research/top-10-web-hacking-techniques-of-2024-nominations-open
screaminggoat
screaminggoat@infosec.exchangeMozilla Foundation security advisories 09 January 2025:
- MFSA2025-04 Security Vulnerabilities fixed in Thunderbird 134 (9 CVEs: 2 high, 7 "moderate")
- MFSA2025-05 Security Vulnerabilities fixed in Thunderbird ESR 128.6 (7 CVEs: 1 high, 6 moderate)
No mention of exploitation.
#mozilla #thunderbird #vulnerability #cve #infosec #cybersecurity
Tamir Bahar
tmr232@mastodon.socialI really hope I'm missing something, but I can't find a VSCode API that allows me, in an extension, to get an event when a breakpoint is hit.
Seems like a massive blocker for developing debugging tools.
Doyensec
doyensec@infosec.exchangeTaking his previous research to the next level, our Maxence Schmitt explores how to bypass various upload restrictions to exploit client-side path traversal. Read about it in our latest blog post today!
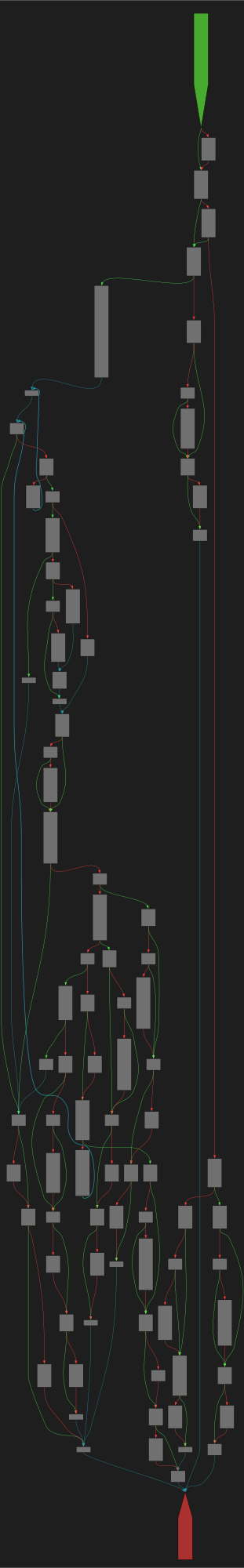
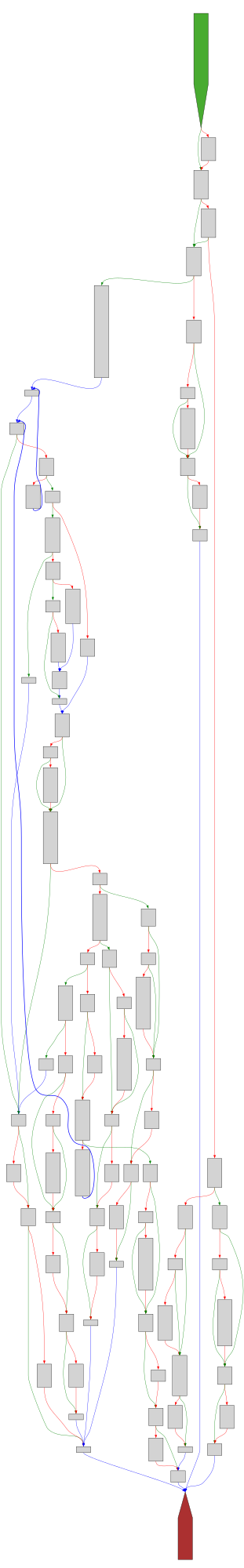
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a7fb8c4
RenameFile
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a7fb8c4.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a7fb8c4.json&colors=light
nullagent
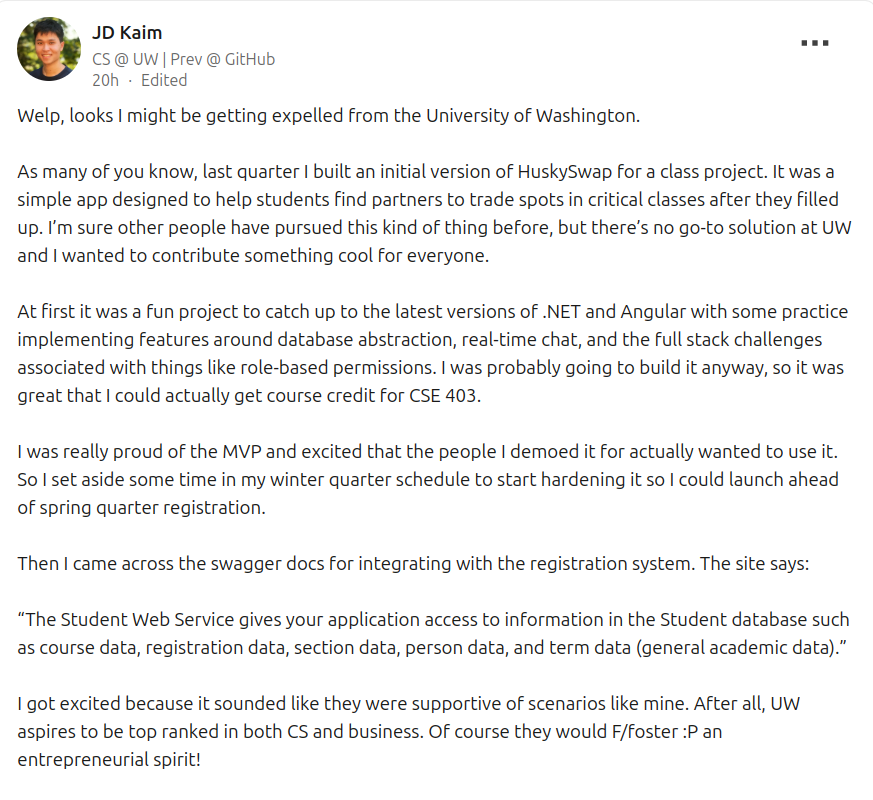
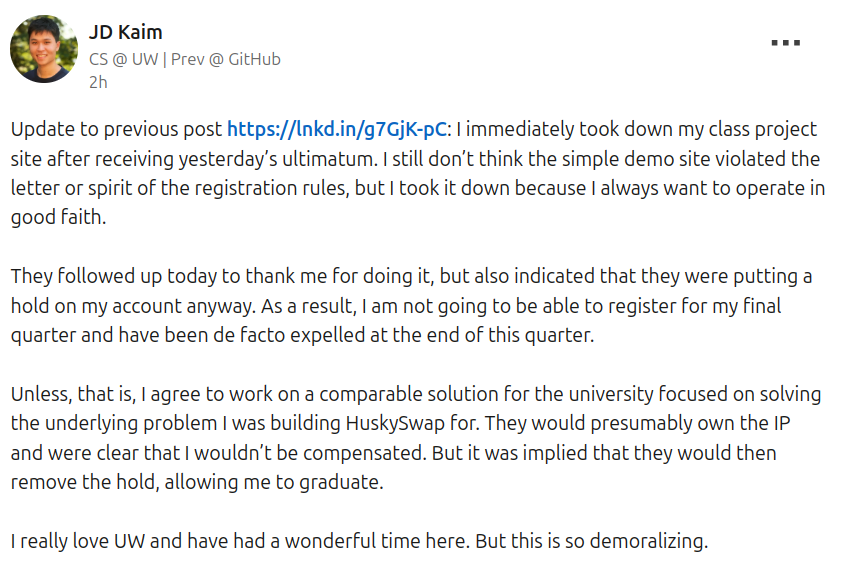
nullagent@partyon.xyzHearing about a young hacker whose being extorted by the University of Washington, not cool UW.
The student claims they built an app to help kids get the course schedules they want, a hack as old as time, and the university decided to expel him until he ports his app to the university's internal systems.
This would be unpaid labor.
Until then his class registration is on hold and he can't register or attend his last few classes. 🥴