Posts
3373Following
712Followers
1579Computer History Museum 🇸🇮
muzej@mastodon.social🎂🗻 Looking for simh/DEC J-11 experts to volunteer for our project of developing a libre emulator of the Slovenian Iskra Delta Triglav computer which is celebrating 40 years! We have ROM and disk images (RSX11-M/DELTA-M OS) and lots of documentation. Interested? 👉 marko@muzej.si
CFG Bot 🤖
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
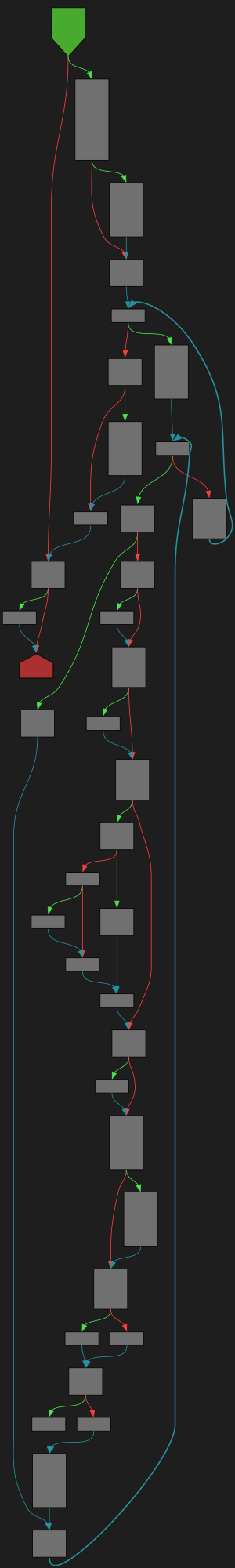
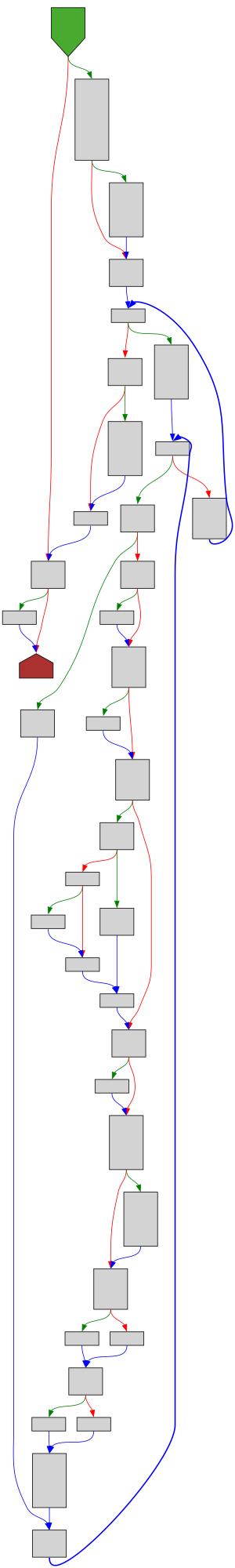
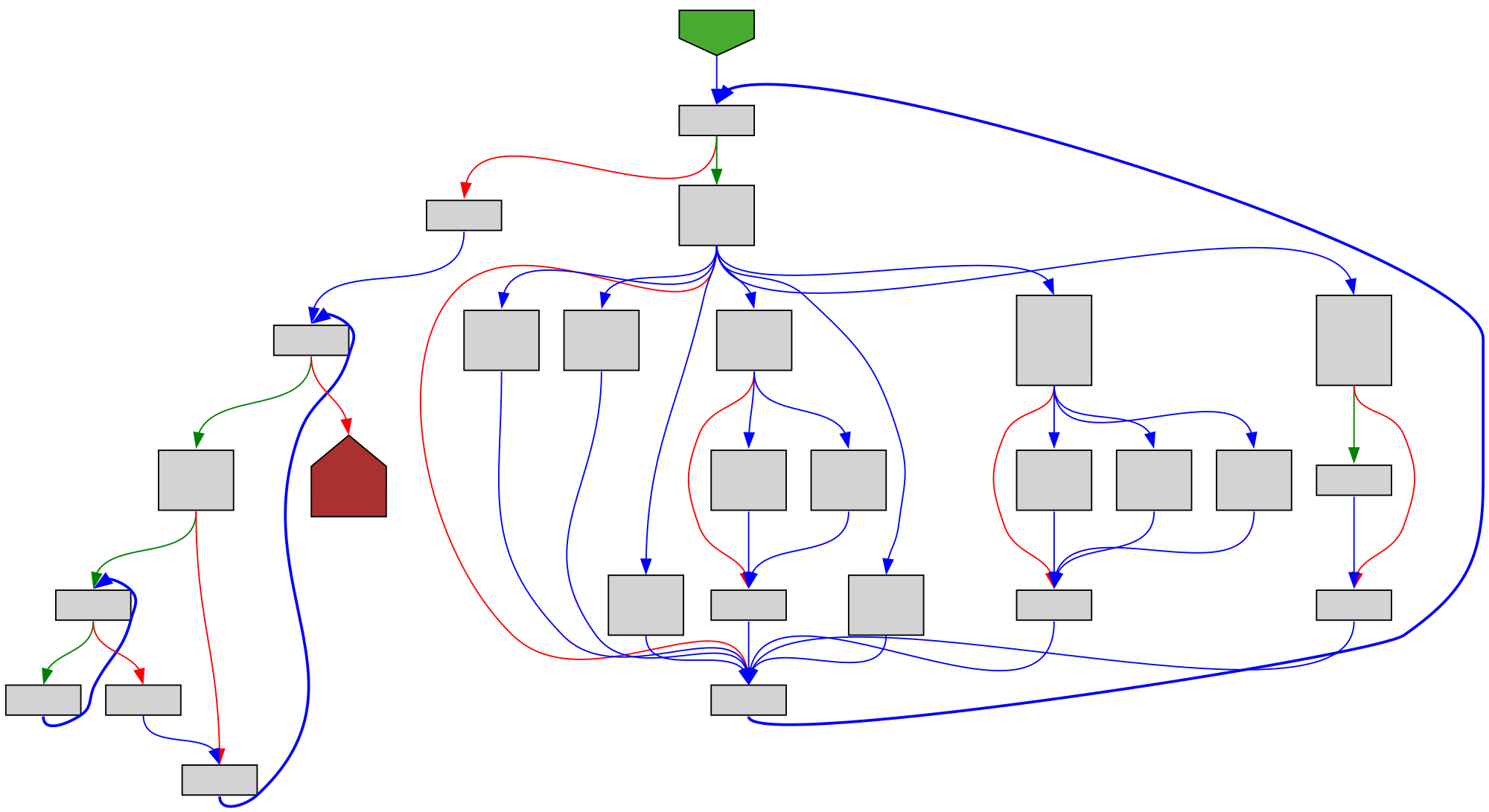
File: src/runtime/map.go:1255 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/runtime/map.go#L1255
func evacuate(t *maptype, h *hmap, oldbucket uintptr)
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fruntime%2Fmap.go%23L1255&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fruntime%2Fmap.go%23L1255&colors=light
CFG Bot 🤖
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
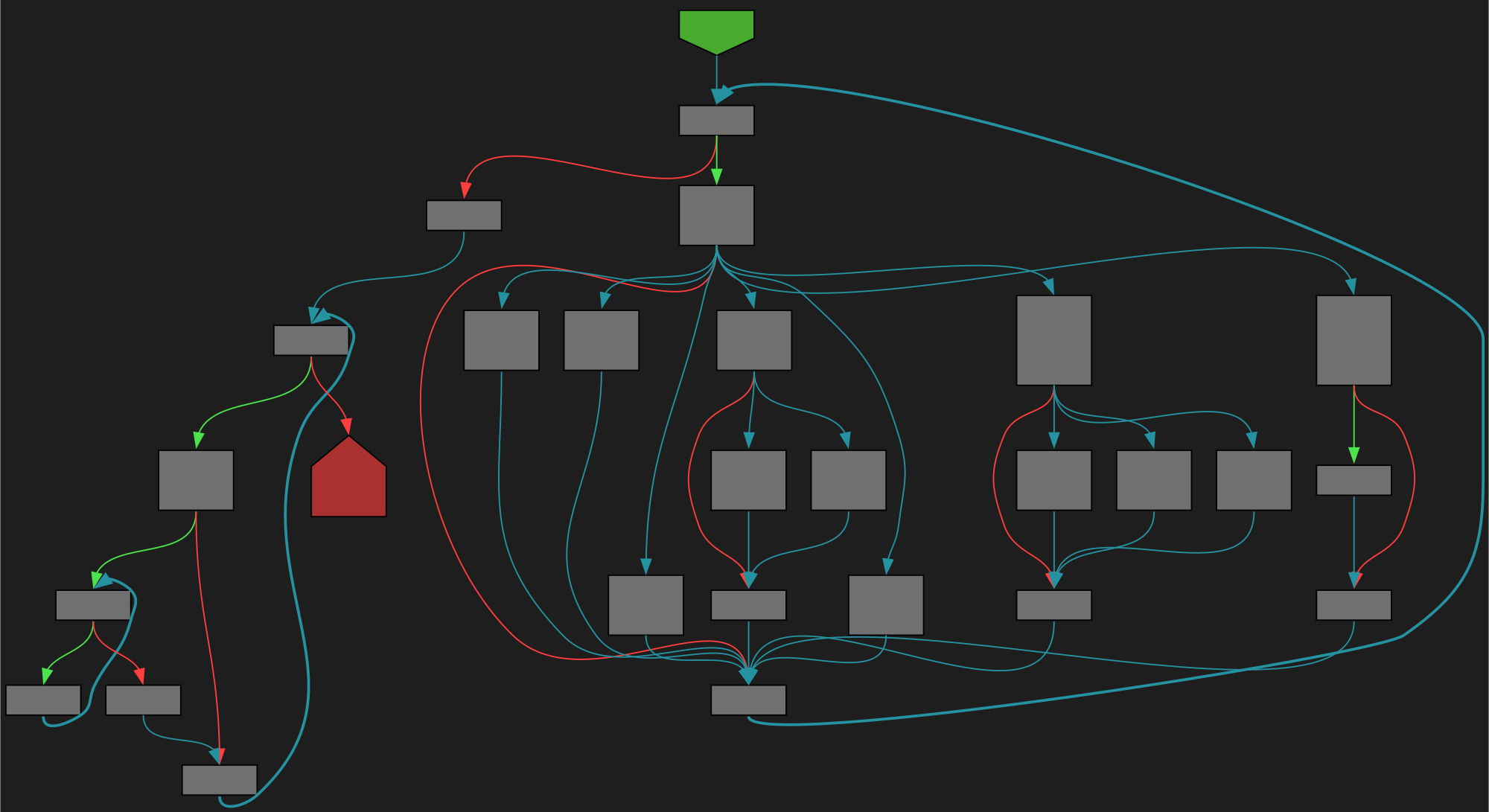
File: src/cmd/trace/gen.go:41 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/trace/gen.go#L41
func runGenerator(ctx *traceContext, g generator, parsed *parsedTrace, opts *genOpts)
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Ftrace%2Fgen.go%23L41&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Ftrace%2Fgen.go%23L41&colors=light
Caitlin Condon
catc0n@infosec.exchangeNew #Ivanti Connect Secure #0day — I'm sure we'll see Mandiant and MSTIC write-ups shortly on whichever threat campaign/actor was hitting CVE-2025-0282. https://www.rapid7.com/blog/post/2025/01/08/etr-cve-2025-0282-ivanti-connect-secure-zero-day-exploited-in-the-wild/
Blort™ 🐀Ⓥ🥋☣️
Blort@social.tchncs.deI'm very happy to see @kagihq joining Peertube with their inaugural video below about what makes Kagi independent search special!
https://tilvids.com/w/twGQeYV9c1TGwMmbdXtY2q
Remember to follow their Peertube account at @kagi and boost to encourage and show them the effort is appreciated! Also do check out their excellent lenses feature, shown in the video.
buherator
buheratorhttps://u1f383.github.io/linux/2025/01/08/two-network-related-vulnerabilities-analysis.html
#Linux kernel - CVE-2023-6932 CVE-2023-0461
buherator
buheratorhttps://www.netspi.com/blog/technical-blog/cloud-pentesting/hijacking-azure-machine-learning-notebooks/
screaminggoat
screaminggoat@infosec.exchangeGitLab security advisory 08 January 2025: GitLab Patch Release: 17.7.1, 17.6.3, 17.5.5
- CVE-2025-0194 (6.5 medium) Possible access token exposure in GitLab logs
- CVE-2024-6324 (4.3 medium) Cyclic reference of epics leads resource exhaustion
- CVE-2024-12431 (4.3 medium) Unauthorized user can manipulate status of issues in public projects
- CVE-2024-13041 (4.3 medium) Instance SAML does not respect external_provider configuration
Jerry 🦙💝🦙
jerry@infosec.exchangeHi all. Given the recent announcement from Meta about AI personas and allowed behavior, I am moving threads.net back to a limit, and will likely move them to a block in the future on infosec.exchange. I can’t ignore the reality that the changes they’re making are specifically intended to permit attacks on many of the people that call this place home. I won’t rule out that they walk the changes back, which is why I’m not jumping to sever the nearly 4000 mutual follow relationships between people on threads and here.
MADWeb Workshop
madwebwork@infosec.exchange🚨 Deadline Extended 🚨
By popular demand, the #MADWeb submission deadline is now January 14, 2025 (AoE)! 🗓️
You still have 1 week to send your papers and join us in San Diego!
📜 Submit here: https://madweb25.hotcrp.com
🔗 Details: https://madweb.work
Spread the word!
Mr. Bitterness
wdormann@infosec.exchangeThere are rumor swirling that there might be some upcoming Ivanti Connect Secure (ICS) CVEs being released soon.
I feel bad for anybody needing to decipher what Ivanti product versions are vulnerable to what CVE.
The Ivanti advisories use confusing language that is unclear if it's referring to which versions are fixed, and which are affected. The CVE entries don't mention which versions contain the fix. And the release notes...
Can somebody smarter than myself decipher what order the security patches are listed in? It's not by order of CVE ID, and it's not by order of ICS version. Which leaves... ?
If we are indeed about to have an Ivanti fire drill, good luck folks.
Ivan Fratric
ifsecure@infosec.exchangeIn case it wasn't posted here already, Project Zero is hiring!
See https://t.co/bA3FT6ZbzH
Gynvael Coldwind
gynvael@bird.makeup(please RT for reach - thank you!)
Learned a cool new Linux trick? Know an interesting quirk in a network protocol? Or have something else to share?
Write a 1-page article for the #6 issue of Paged Out! :)
https://pagedout.institute/?page=cfp.php
Soft deadline is Feb 1st.
Mr. Bitterness
wdormann@infosec.exchangeFrom over at the Bad Place:
https://gist.github.com/alfarom256/f1342f14dc6a742de7ea4004a1b6d7ed
IObit Malware Fighter has a driver device called IMFForceDelete123.
When you call the only exposed IOCTL to this device, 0x8016E000, along with a specified path, the Windows kernel will delete the specified file/directory. NTFS ACLs don't matter because we're the kernel.
Who is allowed to interact with this device? EVERYONE.
The more software you have on your system, the less secure it is.
Talos Vulnerability Reports
talosvulnsProgress WhatsUp Gold SnmpExtendedActiveMonitor path traversal vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2089
CVE-2024-12105
Programming Quotes
programming_quotes@mastodon.socialThe art of programming is the art of organizing complexity, of mastering multitude and avoiding its bastard chaos as effectively as possible.
— E. W. Dijkstra
buherator
buheratorhttps://bughunters.google.com/blog/6752136441233408/capturing-the-flags-of-the-internet-find-0-days-in-oss-and-write-scanners-to-detect-them
/r/netsec
_r_netsec@infosec.exchangeBackdooring Your Backdoors - Another $20 Domain, More Governments - watchTowr Labs https://labs.watchtowr.com/more-governments-backdoors-in-your-backdoors/