Posts
2506Following
574Followers
1284Heretek of Silent Signal
Foone🏳️⚧️
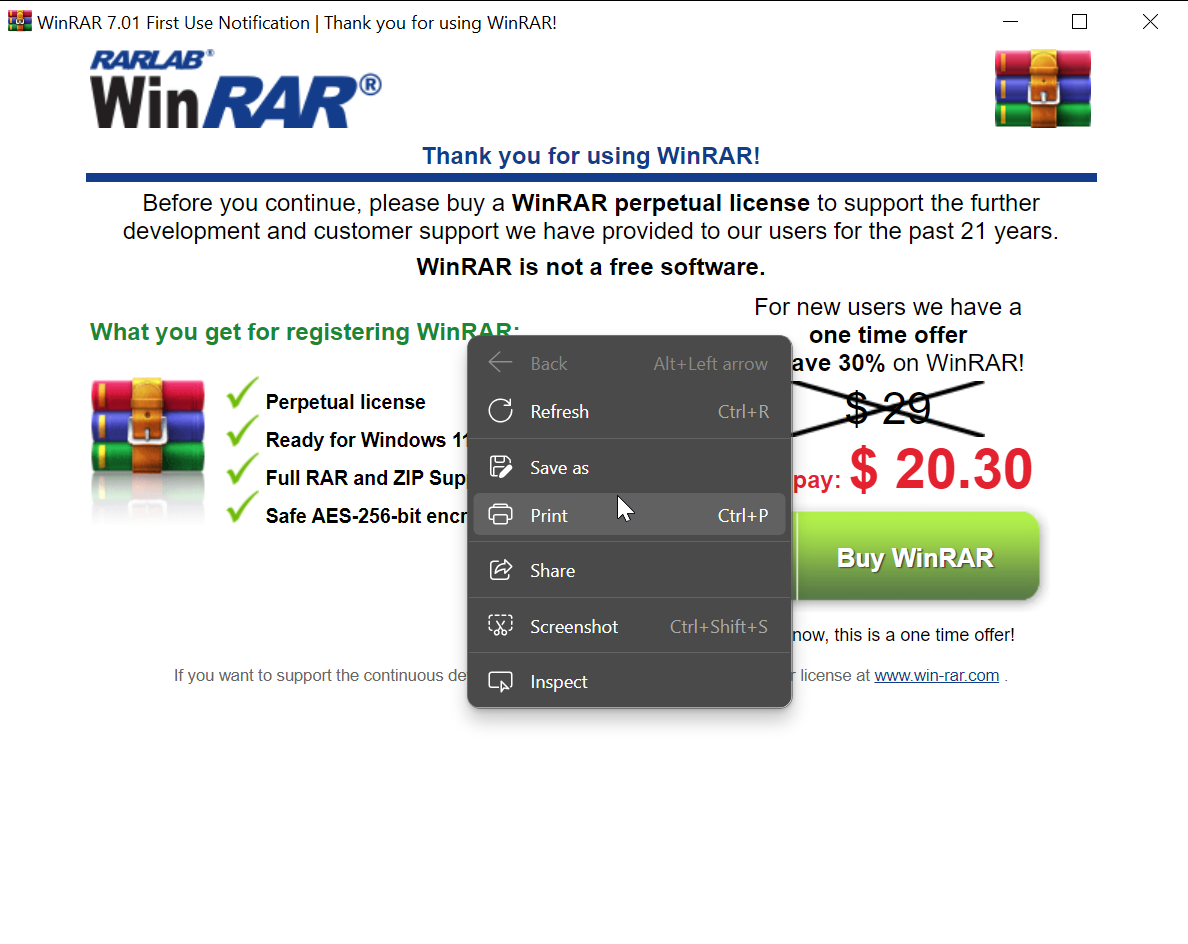
foone@digipres.clubFeel old yet? The winrar registration nag screen is Electron these days.
EDIT: Whoops, it seems I'm wrong: This is just an embedded webview, which on Win10 is apparently chromium-backed (probably because it's Edge)
Virtual Colossus
virtualcolossus@infosec.exchange#Polish researchers have discovered components of a German #Enigma cipher machine, crucial to the Nazi wartime communications system, on Sobieszewska island near the city of Gdańsk. All in all, 8 rotors and various other parts were recovered. https://tvpworld.com/84053156/fragments-of-rare-german-enigma-machine-unearthed-in-poland
buherator
buherator"[Person] will be the wall
that guides us through the night!"
buherator
buheratorhttps://www.ibm.com/support/pages/node/7179158
Emphasis mine:
"A user with authority to a *view* can alter the based-on *physical file* security attributes without having object management rights to the physical file."
I wonder what other discrepancies there may be between Db2 and other interfaces.
Stephen Rees-Carter 
valorin@phpc.social
One of the fun parts of doing my security audits is coming across unexpected code that looks exploitable, and trying it out myself to see what possibilities exist.
In a recent audit, I found myself asking... What if you hashed null?
https://securinglaravel.com/security-tip-what-if-you-hashed-null/
cR0w h0 h0
cR0w@infosec.exchangeThat's not how you're supposed to put the ../ in the pentest report!
https://github.com/pwndoc/pwndoc/security/advisories/GHSA-2mqc-gg7h-76p6
Prof. Emily M. Bender(she/her)
emilymbender@dair-community.socialCalling all Mystery AI Hype Theater 3000 fans! Have you found a piece of Fresh AI Hell but not known where to send it? Here's the spot:
https://thecon.ai/submit-fresh-ai-hell/
Help @alexhanna.bsky.social and me clean out the Fresh Hell by submitting it there!
cR0w h0 h0
cR0w@infosec.exchangeCritical command injection in BeyondTrust Remote Support and Privileged Remote Access. Yikes.
Cloud customers patched as of yesterday but on-prem needs to patch.
https://www.beyondtrust.com/trust-center/security-advisories/bt24-10
💻📡🛰️ IooNag
IooNag@infosec.exchangeDevOps practices are all well and good, but beware of the configuration of the tools that access your production.
I've written a blog post sharing some dangerous ways Argo CD can be configured, detailing the security impact: https://ledger.com/argo-cd-security-misconfiguration-adventures
buherator
buheratorAnd this comes from someone who's been writing #documentation professionally at #Microsoft! I'm at loss for words...
https://github.com/MicrosoftDocs/WSL/pull/2021#issuecomment-2548390973
buherator
buheratorSerious question.
Project Zero Bot
p0botLinux: Panthor: racy panthor_vm_pool_get_vm() leads to UAF
https://project-zero.issues.chromium.org/issues/377500597
CVE-2024-53080
Project Zero Bot
p0botLinux >=5.10: wrong order of operations on close_and_free_vma error path causes temporary dangling PTE
https://project-zero.issues.chromium.org/issues/374117290
CVE-2024-53096
David Gerard
davidgerard@circumstances.runMicrosoft refuses pull request to put documentation in readable table form because LLMs are bad at parsing tables https://github.com/MicrosoftDocs/WSL/pull/2021
tmpout
tmpout@haunted.computerWe are extending our call for papers to January 1, 2025!
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
Phrack
phrack@haunted.computerWe updated our CFP for Phrack 72! The deadline is now April 1st 2025. Check the site for specifics on how to contribute, as well as some inspiration! We also posted a link to purchase physical copies of Phrack 71, and a donation link too. Enjoy!
Yellow Flag
WPalant@infosec.exchangeI just replied to a blog comment, and I thought that I post my reply here as well:
I think that I have good reasons to be “against Avast,” having published seven articles on them so far. The security issues alone are bad enough. But Avast abused their position to collect and sell users’ browsing profiles. After they were caught they claimed the data to be anonymized, they claimed to only sell aggregated data – and they continue lying to this day, despite there being conclusive evidence to the contrary. While the company has been bought, it’s still the same people in charge. This sort of undermines any trust in them for anything related to security.
As the security of antivirus software goes, I’m not very fond of any as the articles in the “antivirus” category of my blog show. With Kaspersky it wasn’t only the security issues but also how they handled them, pushing out half-hearted fixes only for these to be circumvented shortly afterwards. McAfee and BullGuard had massive security issues stemming from being careless about security and not following best practices.
I’ve found a critical security issue in Bitdefender’s solution as well, but with them I at least had the impression that they were trying. Unfortunately, that’s currently the bar in the antivirus industry – at least trying to make their product secure.
Security-wise, one good thing about Windows Defender is that it only needs to do one job. It doesn’t need all the extra functionality as a selling argument. It doesn’t need to be a banking browser, it doesn’t need to be a phishing protection, it only needs to be an antivirus solution. It can keep a very small attack surface compared to all those antivirus suites, and so it does (yes, I checked).
#antivirus #security #avast #McAfee #BullGuard #Bitdefender #WindowsDefender
yossarian (1.3.6.1.4.1.55738)
yossarian@infosec.exchangejust had an interesting realization: one of the reasons people struggle to understand template injection in GHA is probably because lines like this:
```
echo "hello: ${{ expr }}"
```
...get lexed mentally as "variable expansion, followed by Jinja template."
in other words, people think the `$` comes from the shell and the `{{ }}` is the template syntax, and therefore the entire thing is quoted correctly.
in reality of course the entire `${{ .. }}` is template syntax, and has nothing to do with shell quoting/expansion rules. but `$` is mentally overloaded!
i wonder how much easier this would be to teach people if GitHub had chosen `@{{ ... }}` or even just `{{ }}` as their template syntax instead.
Doyensec
doyensec@infosec.exchange🎉Announcing the latest research from our intern Michael Pastor! In it, you'll learn all about Decompression Attacks, get to practice in custom-built labs and get some free Semgrep rules for detecting flaws. Check it out today!
b33f | 🇺🇦✊
fuzzysec@bird.makeupI have posted the slides for the talk @chompie1337 and I gave this past weekend at @h2hconference -> The Kernel Hacker’s Guide to the Galaxy: Automating Exploit Engineering Workflows #H2HC