Posts
3402Following
713Followers
1581Google is trying to jam "AI" into all of their products but an interesting element of the way they integrated it into Android Messages is "Gemini" shows up as a conversation, which means it is actually possible to block and report it to Google as spam
Simon Tatham
simontatham@hachyderm.ioThe key words "MUST", "MUST NOT", "SHOULD", "SHOULD NOT", "RECOMMENDED BUT REPULSIVE", "WRONG BUT WROMANTIC", "FREQUENTLY MISUNDERSTOOD", "NOBODY BOTHERS WITH THIS BIT", "SHOULDN'T REALLY BUT WE WON'T JUDGE", "REQUIRED IN ORDER TO WORK AROUND EVERYONE ELSE'S BUGS", "YOU DO YOU", and "OBVIOUSLY ABSURD BUT VERY COMMON FOR SOME REASON" in this document are to be interpreted as described in RFC 2119.
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: Amnesty International has documented two cases where Serbian authorities used Cellebrite to unlock the phones of a journalist and an activist.
And then they installed spyware on the devices.
In a way, this is a return to the old days of government spyware, where remote attacks were rare and impractical, and cops needed to get their hands on target's computers.
/r/netsec
_r_netsec@infosec.exchangePlatform.sh team finds auth bypass in Go SSH package https://platform.sh/blog/uncovered-and-patched-golang-vunerability/
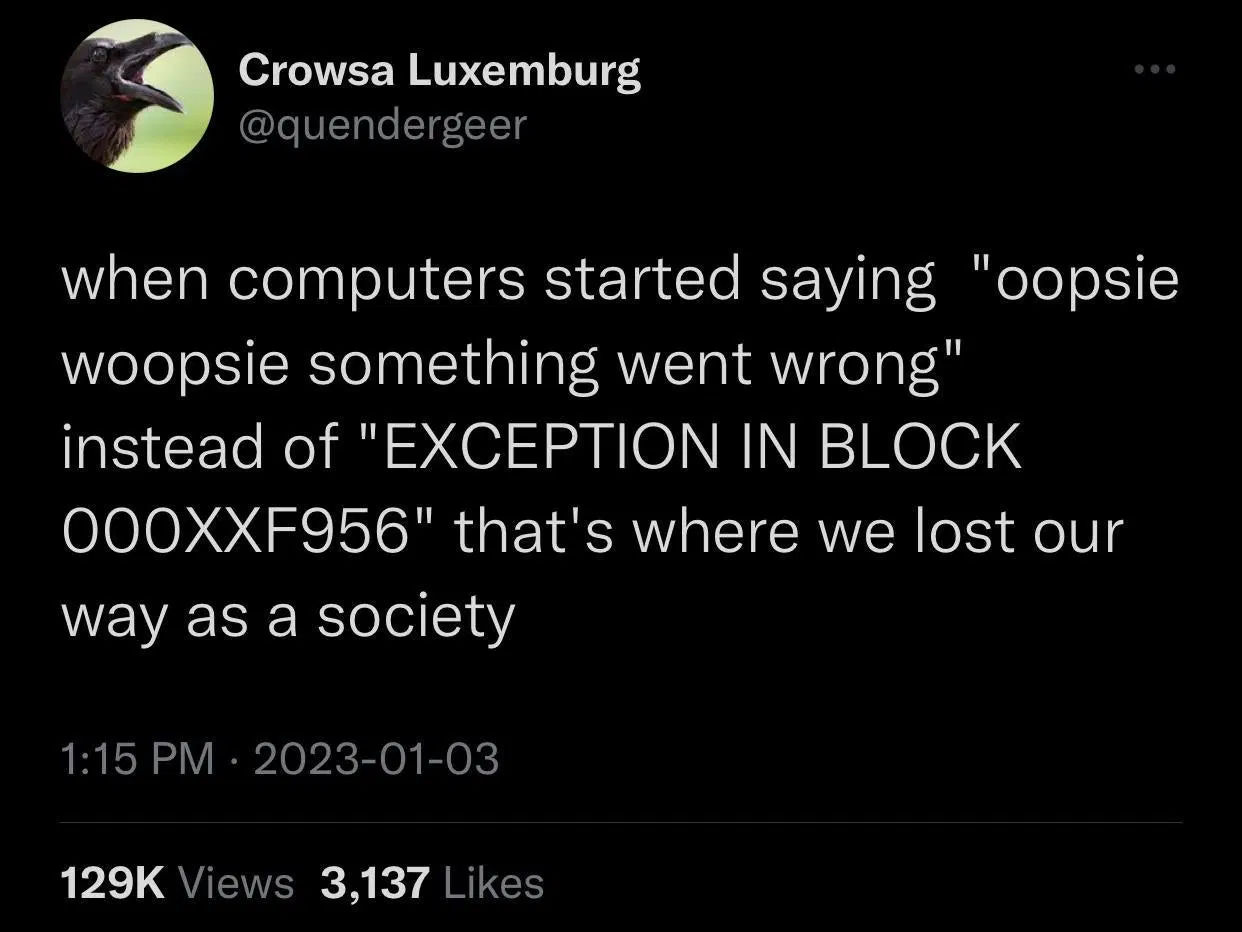
as a sysadmin this so much. It’s one thing to say “oopsie something went wrong” and provide a button for the professionals to see where it went wrong and it’s another to just not provide any diagnostic information so I get to debug a black box.
David K.
leeN@chaos.socialJust returned from #BHEU. I presented my research on how server-side HTML sanitization is a security nightmare due to the mess that is HTML parsing.
If you are interested in learning more on that topic, please check out the following resources:
Github: https://github.com/ias-tubs/HTML_parsing_differentials
Our S&P '24 Paper: https://www.ias.cs.tu-bs.de/publications/parsing_differentials.pdf
Slides will be available shortly.
Or get in touch :)
Huge thanks to @BlackHatEvents, @InfosecVandana, and all the other great folks who made this such an amazing experience.
Alexandre Borges
ale_sp_brazil@bird.makeupGood and interesting presentation by Joe Bialek:
Pointer Problems – Why We’re Refactoring the Windows Kernel:
Yarden Shafir
yarden_shafir@bird.makeupImportant news: Microsoft is working to bring SMAP into Windows
buherator
buheratorhttps://www.bbc.com/news/articles/cd0elzk24dno
Natalie Silvanovich
natashenka@infosec.exchangeCan you find an ITW 0-day from crash logs? Project Zero finds out
Patrick C Miller 
patrickcmiller@infosec.exchange
Yearlong supply-chain attack targeting security pros steals 390K credentials https://arstechnica.com/security/2024/12/yearlong-supply-chain-attack-targeting-security-pros-steals-390k-credentials/
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Looking at legacy NeXT source:
Quoting from the OS X man page for execvp():
"Historically, the default path for the execlp() and execvp() functions was ``:/bin:/usr/bin''. This was changed to place the current directory last to enhance system security."
buherator
buherator- You already mentioned them.
- I know I did. They are twice as bad as anything else.
https://m.imdb.com/title/tt0107362/?ref_=ttqu_ov
Andrea Junker 
Strandjunker@mstdn.social
JOURNALISM 101 RULE: If someone says it’s raining, and another person says it’s dry, it’s not your job to quote them both. Your job is to look out of the fucking window and find out which is true. — Now more than ever.
Jerry on Mastodon
Jerry@hear-me.socialImportant reminder, if you own a domain name and don't use it for sending email.
There is nothing to stop scammers from sending email claiming to be coming from your domain. And the older it gets, the more valuable it is for spoofing. It could eventually damage your domain's reputation and maybe get it blacklisted, unless you take the steps to notify email servers that any email received claiming to come from your domain should be trashed.
Just add these two TXT records to the DNS for your domain:
TXT v=spf1 -all
TXT v=DMARC1; p=reject;
The first says there is not a single SMTP server on earth authorized to send email on behalf of your domain. The second says that any email that says otherwise should be trashed.
If you do use your domain for sending email, be sure to add 3 records:
SPF record to indicate which SMTP server(s) are allowed to send your email.
DKIM record so the receiving email server can confirm the FROM addresses are valid.
DMARC record that tells the receiving email server how to handle email that fails either check.
You cannot stop scammers from sending email claiming to be from your domain, any more than you can prevent people from using your home address as a return address on a mailed letter. But, you can protect both your domain and intended scam victims by adding appropriate DNS records.
#cybersecurity #email #DomainSpoofing #EmailSecurity #phishing
Signal
signalapp@mastodon.worldIt costs around $50 million every year to ensure Signal is robust and available all over the world for anyone whenever they need it.
And as a nonprofit, that money comes from all of you; the people who believe that we all deserve a place to speak freely.
buherator
buheratorhttps://wetw0rk.github.io/posts/0x01-killing-windows-kernel-mitigations/