Posts
2688Following
681Followers
1504Sebastian
moehrenfeld@social.karotte.org#TIL that the #IAEA uses something called a „COBRA seal“ to seal relevant objects against manipulation. One type of these seals works by using a multi-core optical cable. When the seal is locked a random number of cores are cut. This creates a unique optical pattern that can be verified simply by shining a light into the cable and can’t be recreated.
The Verge
verge@mastodon.socialThe moral bankruptcy of Marc Andreessen and Ben Horowitz https://www.theverge.com/2024/7/24/24204706/marc-andreessen-ben-horowitz-a16z-trump-donations
hanno
hanno@mastodon.socialDo I know anyone with a mail address on a mail server managed by barracuda networks who would help me with something? I'd like to test a few things (just sending you a few test mails and see if they arrive).
BrianKrebs
briankrebs@infosec.exchangeWild, true story from the security awareness and training company KnowBe4 that details how they inadvertently hired a North Korean hacker who was posing as a Western tech worker.
Kudos to them for publishing this. If it can happen to a security awareness company, it can happen to anyone (full disclosure: they've been an advertiser on my site for ages).
https://blog.knowbe4.com/how-a-north-korean-fake-it-worker-tried-to-infiltrate-us
DoI
DoI@mastodon.nzI've published a little blog on binary patching Golang produced assembly to alter the stdlib net/http functionality. #golang and #infosec frens maybe interested! https://pulsesecurity.co.nz/articles/golang-patching
Doyensec
doyensec@infosec.exchangeWe're proud our testing helps ensure the security of Thinkst's OSS Canary Tokens! As part of their transparency efforts, you can read the results of our latest round of testing here:
https://www.doyensec.com/resources/Doyensec_ThinkstCanaryTokensOSS_Report_Q22024_WithRetesting.pdf
screaminggoat
screaminggoat@infosec.exchangeCISA: CISA Adds Two Known Exploited Vulnerabilities to Catalog
Hot off the press! CISA adds two vulnerabilities to the KEV Catalog:
- CVE-2012-4792 (CVSSv2: 9.3 "high") Microsoft Internet Explorer Use-after-free vulnerability
- CVE-2024-39891 (5.3 medium) Twilio Authy Information Disclosure Vulnerability
#CISA #KEV #knownexploitedvulnerabilitiescatalog #CVE_2012_4792 #CVE_2024_39891 #eitw #activeexploitation #CVE #vulnerability
/r/netsec
_r_netsec@infosec.exchangeCVE-2019-8805: Apple EndpointSecurity framework Privilege Escalation https://blog.securelayer7.net/applied-endpointsecurity-framework-previlege-escalation/
Sabrina has moved!
sabi@infosec.spaceBlog posts should always include a first published date and a last edited date.
Royce Williams
tychotithonus@infosec.exchangeWas ILOVEYOU worse than CrowdStrike?
https://en.m.wikipedia.org/wiki/ILOVEYOU
Looks like more hosts were affected by ILOVEYOU (45 million in the first 24 hours) ... but the damage was somewhat more random because files were overwritten.
And now that there is a well-known CrowdStrike recovery procedure, as long as you follow it, you're okay -- but if you didn't have good backups, files overwritten by ILOVEYOU were unrecoverable.
Taggart 
mttaggart@infosec.town
Any event that makes the front page of a news outlet will be used as a phishing lure.
Any “threat intelligence” that alerts you to this is next to useless.
Stefano Marinelli
stefano@bsd.cafeEmail received a few days ago: "We need to know which version of SSH is installed on the server, as we want to ensure it is not vulnerable to external attacks." My response: "Don’t worry, SSH is accessible ONLY via VPN, and I am the only one with access to that VPN—activated only when needed—so there is no way for there to be any issues, regardless of the version used."
Email received this morning: "We’re not interested; you must provide the SSH version installed and, if it's not the latest, ensure us of the update date."
My response: "Sorry, could you explain the rationale? SSH is not exposed, it’s not listening on any public IP."
Their reply: "Provide the version."
My response: "OpenSSH_9.7, LibreSSL 3.9.0, on OpenBSD."
Their reply: "This is not considered secure. It must be OpenSSH_9.2p1 Debian-2+deb12u3."
My response: "It’s not Debian; it’s OpenBSD."
Their reply: "So the systems are insecure."
And they claim to be a cybersecurity company...
#CyberSecurity #SSH #VPN #ITSecurity #SysAdmin #TechSupport #OpenBSD #Debian
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🌪️ Our CEO @nrathaus had an engaging chat with our keynote speaker @yarden_shafir. They covered starting out in cybersecurity, tips for beginners, and future trends in the industry.
Watch now at: https://youtu.be/b51Ptn5K79U
HyperDbg
hyperdbg@infosec.exchangeHappy to announce @hyperdbg v0.10! 🎉🎊✨
This version comes with numerous bug fixes and stability improvements, plus new features like running assembly code directly in the events (VMX root-mode) and two new commands.
Check out the latest version: https://github.com/HyperDbg/HyperDbg/releases
For more information,
Assembly codes in conditions:
- https://docs.hyperdbg.org/using-hyperdbg/prerequisites/how-to-create-a-condition
Assembly codes in code sections:
- https://docs.hyperdbg.org/using-hyperdbg/prerequisites/how-to-create-an-action
Assemble virtual address:
- https://docs.hyperdbg.org/commands/debugging-commands/a
Assemble physical address:
- https://docs.hyperdbg.org/commands/extension-commands/a
cynicalsecurity 
cynicalsecurity@bsd.network
On the  there is a narrative whereby a Cobalt Strike¹ update "forced" #CrowdStrike to push out an update which caused the Falcon crash² .
there is a narrative whereby a Cobalt Strike¹ update "forced" #CrowdStrike to push out an update which caused the Falcon crash² .
Inevitably the usual crowd came out and we have statements such as:
> So, it’s Cobalt Strike’s success and popularity with threat actors that prompted CrowdStrike to rush out a signature for their agents, resulting in crashes on thousands of systems.
>
> Can someone add this to the balance sheet of damage caused by popular C2 frameworks?³
We therefore justify the complete lack of QA by blaming a C2 framework from a commercial company which, as many others, is used by baddies too.
The best bit is that Florian had to tell people it was said in jest (follow-up xeet) but… too late. He was quoting a xeet by Constantin Raiu but it was taken seriously.
We have just given #CrowdStrike something to blame in their narrative: "we were doing it to save the world from Cobalt Strike, they should not be allowed to exist!"

__
¹ https://www.cobaltstrike.com
² https://x.com/craiu/status/1814566308056318381
³ https://x.com/cyb3rops/status/1814944503498678678
cynicalsecurity 
cynicalsecurity@bsd.network
A #CrowdSstrike offensive summary (update):
* we know Flacon updates are not verified prior to being enabled
* we know that they don't do staged updates
* we know a lot of large customer names
* we know the DR plans (or lack thereof) of said large customers
* we know the systemic reactivity
Learned opinion: it does not look good.
For those involved with the darker side of cybersecurity this is a monstrously useful set of data points.
Dave Anderson
danderson@hachyderm.ioIt's quite funny that in the midst of the crowdstrike thing yesterday, someone tweeted - afaict as a shitpost - that Southwest Airlines were unaffected due to running windows 3.1. Then digitaltrends published that claim using the tweet as a source, and are now being quoted themselves as a source.
AFAICT, it's entirely bollocks. Same with the claim they still run Windows 95, that's from the same lazy digitaltrends article, misquoting another misquote from 2 years ago.
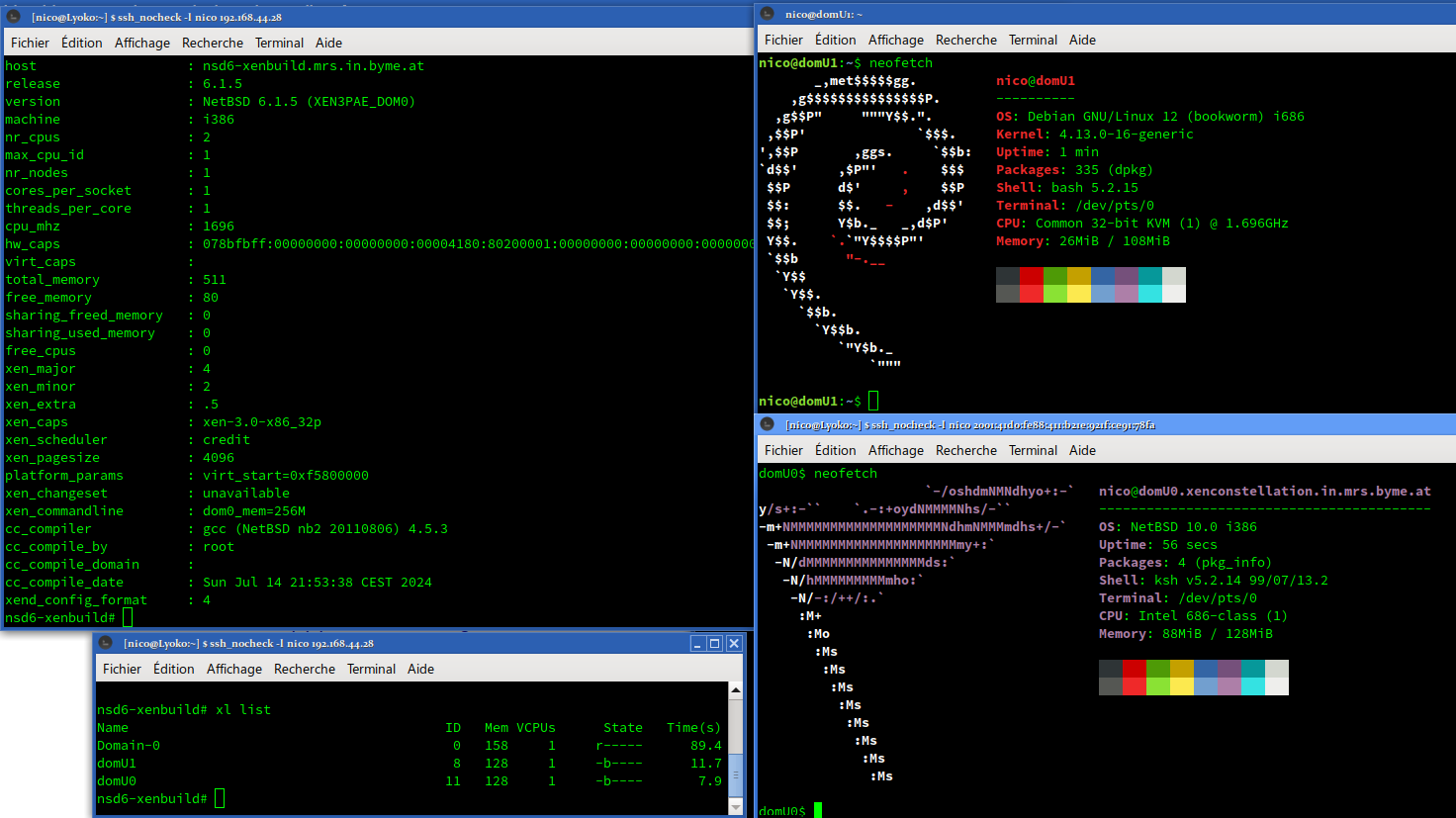
Nicolas SAPA 
nico@ublog.byme.at
I am able to confirm that #NetBSD 10 and #Linux 4.13 are able to run as domU PV.
The journey was very long:
#pkgsrc 2018Q3 provided a lot of help and sometime tiny annoyances.
I had to build 3 compilers: gcc 4.4, gcc 4.8 and gcc 6.4.
I had to downgrade #ocaml to version 4.00.1, rewriting xentools42 Makefile to use my downgrade and kill xen' ocaml binding (because file not found in pkg install).
I had to force some version of GCC to build some packages - pkgsrc helped there.
Recent version of Linux doesn't seem to boot, the ramdisk/initrd for old Linux is broken, the xm stack seem more broken than the xl stack.
But I was able to run 2 domU PV on i386!
cynicalsecurity 
cynicalsecurity@bsd.network
#crowdstrike T&Cs¹, paragraph 8.6 (HT: @JdeBP ), as usual the bit in caps is the best one:
TO THE MAXIMUM EXTENT PERMITTED UNDER APPLICABLE LAW, CROWDSTRIKE AND ITS AFFILIATES AND SUPPLIERS SPECIFICALLY DISCLAIM ALL IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, TITLE, AND NON-INFRINGEMENT WITH RESPECT TO THE OFFERINGS AND CROWDSTRIKE TOOLS. THERE IS NO WARRANTY THAT THE OFFERINGS OR CROWDSTRIKE TOOLS WILL BE ERROR FREE, OR THAT THEY WILL OPERATE WITHOUT INTERRUPTION OR WILL FULFILL ANY OF CUSTOMER’S PARTICULAR PURPOSES OR NEEDS. THE OFFERINGS AND CROWDSTRIKE TOOLS ARE NOT FAULT-TOLERANT AND ARE NOT DESIGNED OR INTENDED FOR USE IN ANY HAZARDOUS ENVIRONMENT REQUIRING FAIL-SAFE PERFORMANCE OR OPERATION. NEITHER THE OFFERINGS NOR CROWDSTRIKE TOOLS ARE FOR USE IN THE OPERATION OF AIRCRAFT NAVIGATION, NUCLEAR FACILITIES, COMMUNICATION SYSTEMS, WEAPONS SYSTEMS, DIRECT OR INDIRECT LIFE-SUPPORT SYSTEMS, AIR TRAFFIC CONTROL, OR ANY APPLICATION OR INSTALLATION WHERE FAILURE COULD RESULT IN DEATH, SEVERE PHYSICAL INJURY, OR PROPERTY DAMAGE.
So very sorry for airports, airlines, hospitals and many other victims covered by the above… it says you shouldn't have used it even if we sold it to you.