Posts
2356Following
513Followers
1231Heretek of Silent Signal
Cindʎ Xiao 🍉
cxiao@infosec.exchangeHello @recon attendees! My workshop, Reversing Rust Binaries: One Step Beyond Strings will be delayed by one hour, and will run from 4:30 pm to 6:30 pm today in Soprano B.
It's finally happened! NEWAG IP Management just sued us for copyright infringement and unfair competition. This is a civil lawsuit in Warsaw, parallel to a criminal investigation that's happening in Cracow.
Of course, they got our postal addresses wrong (they could've just asked!) so we only just got a copy from the court, but hey, we now have 164 pages of content to dive into.
Jeffrey
jtig@infosec.exchange"The NCC Group Global Threat Intelligence team has been made aware of significant compromise of
the TeamViewer remote access and support platform by an APT group. Due to the widespread usage
of this software the following alert is being circulated securely to our customers."
NCC Group can't disclose the source at the time and keep investigating this. Big source, but no substance. Curious to see how this will work out. ping @campuscodi @screaminggoat
Trammell Hudson
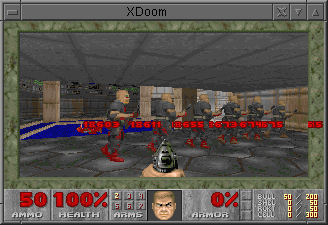
th@v.stdevops fun tip: use psdoom to manage your processes. https://www.cs.unm.edu/~dlchao/flake/doom/
scriptjunkie
sj@social.scriptjunkie.usnetstat when there's no netstat or ss
S=(- ESTABLISHED SYN_SENT SYN_RECV FIN_WAIT1 FIN_WAIT2 TIME_WAIT CLOSE CLOSE_WAIT LAST_ACK LISTEN CLOSING);hex2ipport(){ printf '%d.%d.%d.%d:%d\n' $(echo $1|awk -F: '{print $1}'|sed 's/../0x& /g'|awk '{print $4" "$3" "$2" "$1}') 0x$(echo $1|awk -F: '{print $2}');};cat /proc/net/tcp|tail -n +2|while read L;do echo $(hex2ipport $(echo $L|awk '{print $2}')) $(hex2ipport $(echo $L|awk '{print $3}')) ${S[$(( 0x$(echo $L|awk '{print $4}') ))]};done
Jon Greig
jgreig@ioc.exchangeProgress declined to answer any questions about the third-party issue that forced them to increase the CVSS score of CVE-2024-5806 to 9.1
https://therecord.media/progress-software-elevates-severity-bug
Not Simon 🐐
screaminggoat@infosec.exchangeTenable: Fortra FileCatalyst Workflow Unauthenticated SQLi
Tenable decided to drop a same-day proof of concept for Fortra FileCatalyst Workflow SQL injection vulnerability CVE-2024-5276 (9.8 critical, disclosed 25 June 2024, see Fortra security advisory).
See Bleeping Computer reporting: Exploit for critical Fortra FileCatalyst Workflow SQLi flaw released
#CVE_2024_5276 #Fortra #vulnerability #CVE #ProofofConcept #POC
Cisco Talos
TalosSecurity@mstdn.socialVulnerability Deep Dive: Multiple vulnerabilities in TP-Link Omada system could lead to root access https://blog.talosintelligence.com/multiple-vulnerabilities-in-tp-link-omada-system/
Silent Signal
silentsignal@infosec.exchangeIt was an honor to present our #IBMi exploits at #TROOPERS24 today! You'll have to wait until @WEareTROOPERS releases the recordings for the full show (incl. live demos), until then you can find our slides here:
https://silentsignal.hu/docs/S2-TROOPERS24-IBM_i_for_Wintel_Hackers.pdf
Will Dormann
wdormann@infosec.exchangeA few notes on this GrimResource .MSC thing from Elastic.
For starters, there are not one but THREE security warnings from Windows before opening a .MSC file from the internet.
Just kidding. Nobody still has Smart App Control enabled after using Windows for a day and realizing what doesn't work. 😂 So two security warnings that clearly state that you're about to do something bad. Or maybe just one if you've received the file in a ZIP or ISO or the like. But in the end, this is convincing the user to do something dangerous, and there are PLENTY of ways to accomplish this on a fully-patched system.
But perhaps more interestingly, the issue being leveraged was discovered by GPZ over 6 years ago by GPZ. Microsoft fixed it in Edge as one of CVE-2018-8463 CVE-2018-8468 and CVE-2018-8469. (Nobody can tell exactly what is what from MSRC publications). But Microsoft apparently neglected to recognize that it affects things other than Edge (e.g. MMC.EXE)
https://bugs.chromium.org/p/project-zero/issues/detail?id=1598
buherator
buheratorDan Lockton
danlockton@mastodon.socialThe fact that Microsoft Teams 🤮 contains a feature called "Teams" where actual teams can create a Team, and at Microsoft the teams working on that feature probably have a Team to discuss the Teams feature, suggests that there exists a Microsoft Microsoft Teams Teams Teams' Microsoft Teams Team.
Ange
Ange@mastodon.socialI gave an "unusual” keynote at Troopers today:
https://speakerdeck.com/ange/a-question-of-time
Cindʎ Xiao 🍉
cxiao@infosec.exchange🦀 Hello Rust reversers! If you're at @recon in Montreal this year, come check out my workshop, Reversing Rust Binaries: One Step Beyond Strings! It will be Friday June 28th, at 2:30 pm, in Soprano B.
https://cfp.recon.cx/recon2024/talk/QCA37X/
For pre-workshop setup instructions, including a prebuilt VM, prebuilt binaries, and sample code, see https://github.com/cxiao/rust-reversing-workshop-recon-2024
Hope to see many of you there!
#REcon2024 #reconmtl #rustlang #reverseengineering #reversing #malwareanalysis
Kevin Beaumont
GossiTheDog@cyberplace.socialGood find by Elastic - possibly North Korean based threat actors using an unfixed bug in Windows to execute code, undetected across all vendors until that point (and as of writing only Elastic detect still)
They’ve named it GrimResource https://www.elastic.co/security-labs/grimresource
/r/netsec
_r_netsec@infosec.exchangeWhy nested deserialization is harmful: Magento XXE (CVE-2024-34102) https://www.assetnote.io/resources/research/why-nested-deserialization-is-harmful-magento-xxe-cve-2024-34102
Dumb Password Rules
dumbpasswordrules@botsin.spaceThis dumb password rule is from E-Trade.
Causes:
* Your two-factor authentication code must be appended to the end of the password
* Passwords have a limit of 32 characters
Effect:
If your account has a 32-character password and has two-factor authentication,
their system appears to cut off the token, making it impossible to login.
Yo...
https://dumbpasswordrules.com/sites/e-trade/
#password #passwords #infosec #cybersecurity #dumbpasswordrules