Posts
3422Following
714Followers
1582Michal Špaček
spazef0rze@infosec.exchangeGoogle is now sending a warning about loading 3rd party JS from domains like polyfill.io bootcss.com bootcdn.net & staticfile.org that may do nasty things to your users if your site uses JS from these domains. I've already seen ads disapproved by Google after they detected malicious code being served by one these domains but of course that may not be the biggest problem here.
Possibly the best known case is the polyfill.io domain. Sold to a Chinese company some time ago, contributors have warned us to stop using it https://x.com/triblondon/status/1761852117579427975 Cloudflare and Fastly both set up their own mirrors. https://blog.cloudflare.com/polyfill-io-now-available-on-cdnjs-reduce-your-supply-chain-risk + https://polykill.io/
This security issue is called a supply chain attack, and it's not fun. There are solutions for that problem, like the SRI (Subresource Integrity) hashes (the `integrity` HTML attribute) but sometimes they can't be used, like with the polyfill lib, because the response changes depending what the browser supports.
Matthew Sheffield
mattsheffield@mastodon.socialIn an unbelievable act of corporate vandalism, Paramount completely erased the entire archives of MTV dot com, wiping out more than 30 years and hundreds of thousands of pages https://www.showbiz411.com/2024/06/25/paramount-shuts-down-mtv-website-wipes-history-after-20-plus-years
Taggart 
mttaggart@infosec.town
Don’t sleep on this; I am pretty sure 100k is an undercount. https://www.bleepingcomputer.com/news/security/polyfillio-javascript-supply-chain-attack-impacts-over-100k-sites/
pwelch
pwelch@mastodon.socialGitHub Artifact Attestations is generally available #github #sigstore #supplychainsecurity | https://github.blog/changelog/2024-06-25-artifact-attestations-is-generally-available
screaminggoat
screaminggoat@infosec.exchangeMichael Coppola: Google: Stop Burning Counterterrorism Operations
Michael Coppola writes about Google Project Zero and Threat Analysis Group's In-the-Wild Series from 2021, and the alleged harm caused to U.S and western-led counterterrorism efforts. It is not so farfetched to think that a discovered nation-state actor's servers and exploits "belong to the good guys" (cue are we the baddies? meme).
Counterterrorism is one of the clearest examples of this. Cyber is a pivotal component of modern counterterrorism operations, and these campaigns have life-and-death implications that place them in a distinct category from “routine” espionage acts. When governments deploy cyber capabilities for this purpose, they are directly using these tools to thwart potential attacks on civilians, provide vital intelligence to soldiers on the ground, and deny technological resources to terrorists – all conducted while risking fewer U.S. and allies’ lives in the process.
He gave specific examples where offensive cyber operations (OCO) aided in counterterrorism operations in identifying/capturing ISIS/Al Qaeda members or caused them to break OPSEC. He also wrote: "It’s crucial to make this point clear: Cyber operations keep people out of harm’s way while enabling them to collect critical intelligence for our national security."
He quoted @maddiestone, and @tiraniddo left a comment as well.
#counterterrorism #nationalsecurity #cybersecurity #OCO #terrorism #projectzero #threatanalysisgroup #google
Slashdot 
slashdot@mastodon.cloud
Julian Assange Reaches Plea Deal With US, Allowing Him To Go Free https://yro.slashdot.org/story/24/06/24/2319232/julian-assange-reaches-plea-deal-with-us-allowing-him-to-go-free?utm_source=rss1.0mainlinkanon
Juanma Fernandez
XC3LL@mastodon.socialYou can find my talk about Offensive VBA here => https://github.com/X-C3LL/congresos-slides/blob/master/Offensive%20VBA.pdf
Satoshi
satoshi_tanda@infosec.exchangeAdded a command to dump HVPT (HLAT) protected regions to hvext.js for our talk at #Recon Montreal on this coming Saturday. If you want to study details by yourself, have a look.
https://github.com/tandasat/hvext
Frederik Braun �
freddy@security.plumbingNow that browsers are *upgrading* some mixed content (instead of loading it insecurely), I wrote a tiny article which what I believe is sane and updated advice for the web of 2024. https://frederikbraun.de/mixed-content.html
screaminggoat
screaminggoat@infosec.exchangeKaspersky: XZ backdoor: Hook analysis
Do you remember the XZ Utils incident? 29 March 2024 was a long time ago. The XZ Utils backdoor was discovered through miraculous troubleshooting by a PostgreSQL Developer (@AndresFreundTec) who noticed that SSH was taking 500ms longer in liblzma. He reported to OSS-Security that XZ Utils data compression library (used in major Linux distros) and its tarballs have been backdoored, and would lead to ssh server compromise.
Kaspersky previous provided the initial analysis of the XZ Utils backdoor, and then covered the threat actor Jia Tan’s social engineering tactics. This is a detailed analysis focusing on the backdoor’s behavior inside OpenSSH portable version 9.7p1. These are their key findings:
- The attacker set an anti-replay feature to avoid possible capture or hijacking of the backdoor communication.
- The backdoor author used a custom steganography technique in the x86 code to hide the public key, a very clever technique to hide the public key.
- The backdoor hides its logs of unauthorized connections to the SSH server by hooking the logging function.
- The backdoor hooks the password authentication function to allow the attacker to use any username/password to log into the infected server without any further checks. It also does the same for public key authentication.
- It has remote code execution capabilities that allow the attacker to execute any system command on the infected server.
Trail of Bits
trailofbits@infosec.exchangeIntroducing Decree by @trailofbits: A new tool that helps devs define, enforce, and understand their Fiat-Shamir transcripts. Check it out!
https://buff.ly/3KUnALC
robbje
robbje@infosec.exchangeWhen building a x86 lifter, the first 1000 instructions are the hardest. After that all that's left is another 1000 or so SSE instructions.
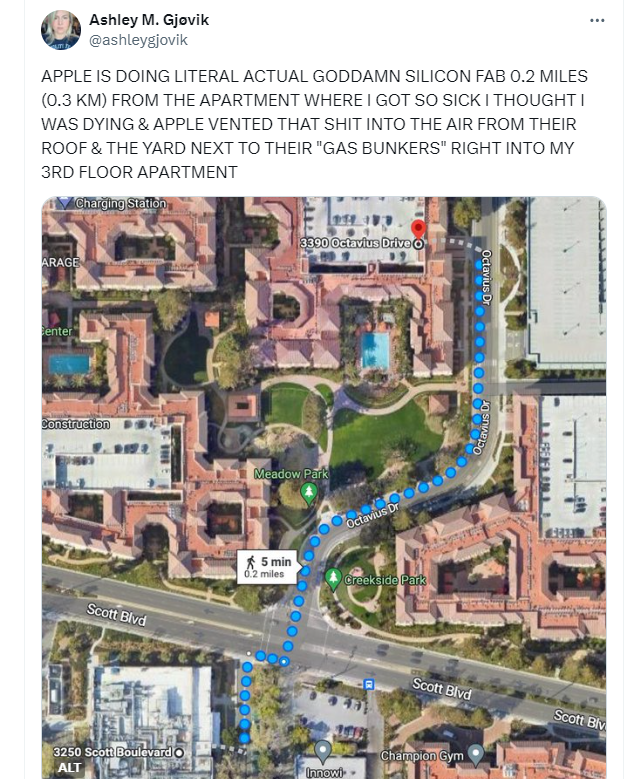
Ashley M. Gjøvik, JD
ashleygjovik@mastodon.social🧵 In 2020, I nearly died from mysterious industrial chemical exposure at my apartment. Later, in 2023, I discovered my employer was dumping toxic waste into the apartment windows from their Skunkworks semiconductor fab next-door. I tipped off the US EPA, who sent their env cops to raid Apple's plant in Aug of 2023. The US EPA finally released the report of their enforcement inspections & sent me a copy on Friday. 💀 ⬇️
Joxean Koret (@matalaz)
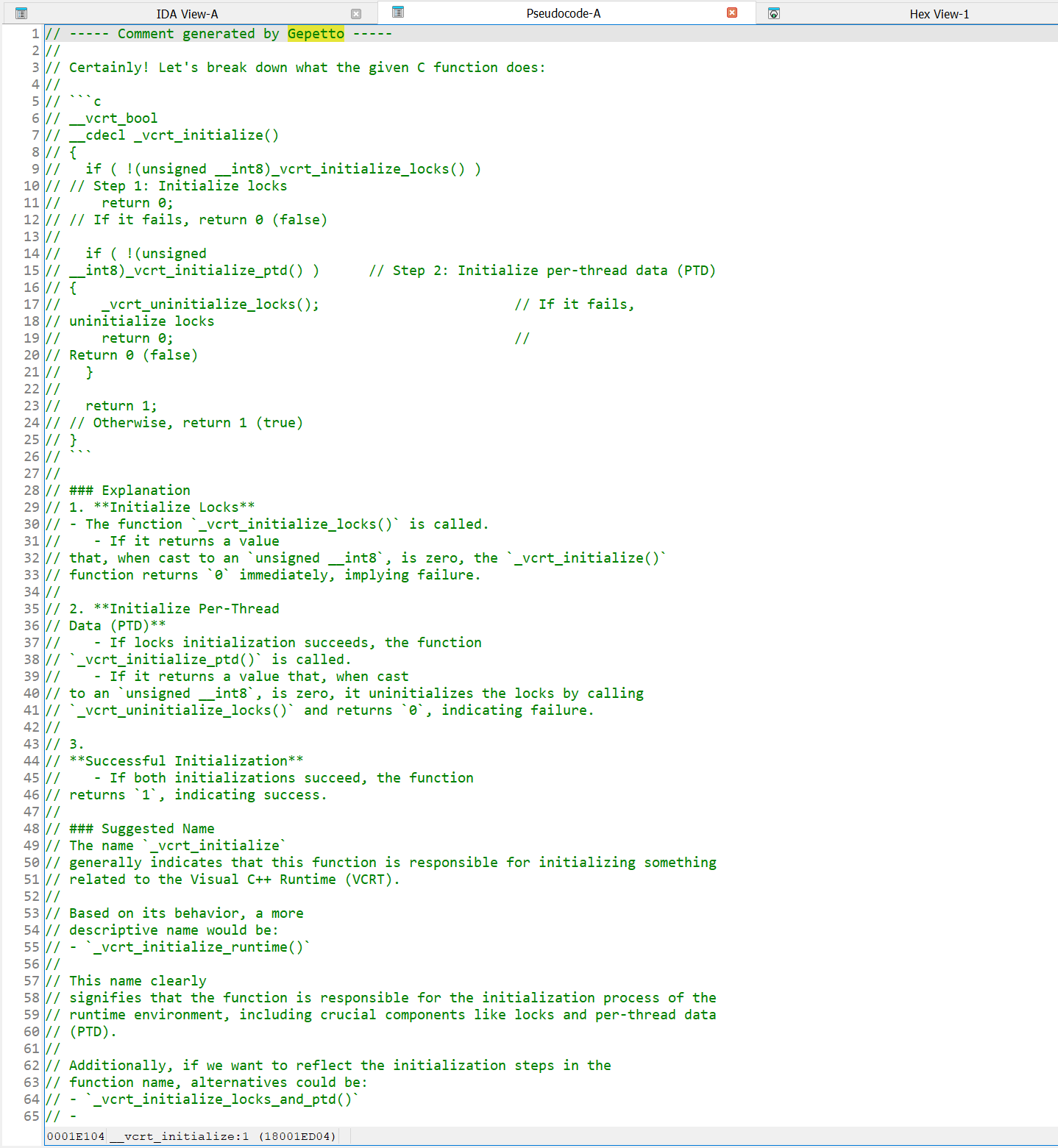
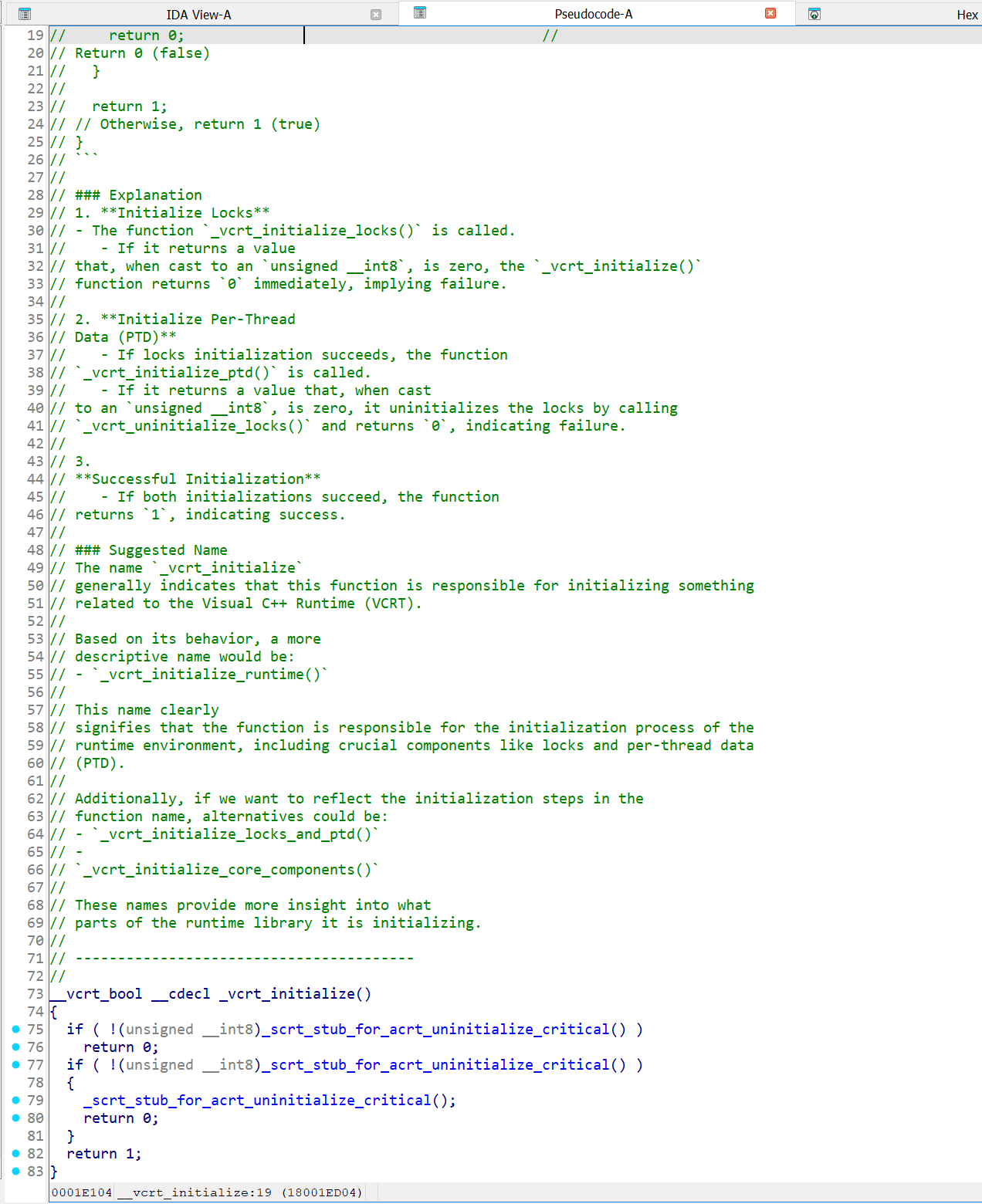
joxean@mastodon.socialI have just discovered that a function's comment added to a MSVC well known runtime function added by IDA's Lumina Server was generated using an AI tool for IDA.
Please don't. I fucking hate it.
BTW: The code for the function that the LLM model is trying to explain *is hallucinated* and does not even correspond to the real function.
Tube❄Time
tubetime@mastodon.socialfun fact: the landing zone on a hard disk platter has a special surface texture that reduces stiction. the rest of the surface is so smooth the head would get stuck if it landed on it.
Attack & Defense (Old Account)
attackanddefense@mozilla.socialAs of today, Firefox Nightly ships with "HTTPS First". So, all new tabs, all links will try HTTPS🔒 regardless of the written URL scheme. When HTTPS fails, Firefox will fall back to using http.
This is thanks to the tireless work of our intern @mjurgens 👏👏👏.
lcamtuf 


lcamtuf@infosec.exchange
Random objects: Intel Edison, or a look at the misadventures of x86 in the IoT space - https://lcamtuf.substack.com/p/random-objects-intel-edison
Nick Selby 
fuzztech@infosec.exchange
If you are still doing this to your customers, you're not understanding what has happened in the world of technology since 2004 and you are part of the problem.