Posts
2700Following
681Followers
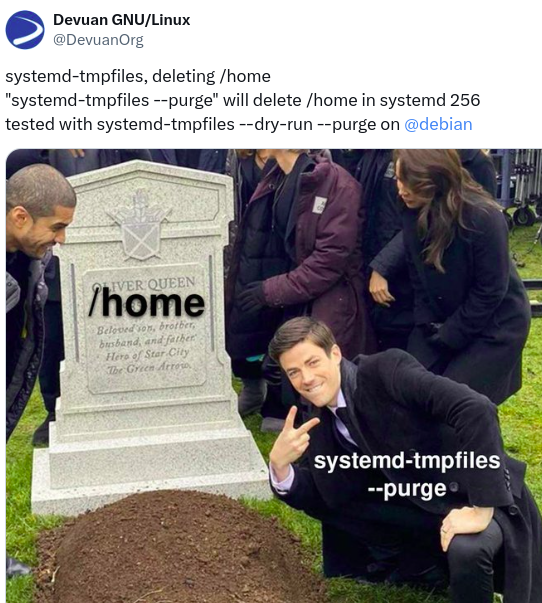
1504☢️ Systemd 256.1 Fixes "systemd-tmpfiles" Unexpectedly Deleting Your /home Directory - Phoronix
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.socialI heard someone complaining "Why did they have to put pixel art on the Museum of Ethnography?!"
Reader, they are traditional cross stitch patterns.
drhoopoe
drhoopoe@mastodon.sdf.orgMan, I just spent two hours ricing tmux instead of writing my article that's due next week. #Linux really is the ultimate procrastination tool.
daniel:// stenberg://
bagder@mastodon.socialMy talk for https://nsss.se/
Title: CVEMITRECVSSNVDCNAOSS WTF
Abstract:
Bogus CVEs, know-better organizations, conflicting databases, AI hallucinations, inflated severity scoring, security scanners, Jia Tan. As the lead developer in the curl project, Daniel describes some of the challenges involved and what you need to do to stay on top of security when working in a high profile Open Source project running in some twenty billion instances. Involving many examples from real life.
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgLast year European Parliament and national parliaments rejected the “EU child porn scanner” that was set to be installed on every phone. Apparently this week we’re going to ignore all that parliamentary action and mandate such a scanner once more. Here’s what I wrote earlier on how this super scary thing would work in practice: https://berthub.eu/articles/posts/client-side-scanning-dutch-parliament/
/r/netsec
_r_netsec@infosec.exchangeAnalysis of CVE-2024-2738 Apache HugeGraph https://blog.securelayer7.net/remote-code-execution-in-apache-hugegraph/
Sonar Research
SonarResearch@infosec.exchange🐮Re-moo-te Code Execution in mailcow!
Dive into our analysis of two vulnerabilities we found in the mail suite mailcow. Learn how attackers can go from XSS to RCE, and why it's important to sanitize your error messages:
Graham Sutherland / Polynomial
gsuberland@chaos.socialI watched the new Practical Engineering video on the bridge collapse, and Grady said words to the effect of "all the work was partitioned out. nobody had a complete view of the situation. the people who really saw the problems had no autonomy to do anything about them, and the people with the authority to do something never saw the full picture - all they got was a piece of paper with action items", and I've never nodded along to something so hard. This happens aaaaalllllll the time in security.
TROOPERS Conference
WEareTROOPERS@infosec.exchangeHey you fine people: Our agenda for the birthday party is public now: https://troopers.de/troopers24/agenda/ #TROOPERS24 See you next week! 🥳
James Kettle
albinowax@infosec.exchangeLast year in "How I choose a security research topic", I used two unnamed attack concepts as case-studies for fast failure. I can now reveal both unnamed techniques were timing attacks. I'm happy to say my third attempt went better!
https://portswigger.net/research/how-i-choose-a-security-research-topic
Taggart 
mttaggart@infosec.town
Enjoy this month’s nasty VMWare vulns, including a CVSS 9.8 potential RCE: https://www.theregister.com/2024/06/18/vmware_criticial_vcenter_flaws/
Direct advisory link: https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24453
#ThreatIntel #CVE_2024_37079 #CVE_2024_37080 #CVE_2024_37081
Ian Coldwater 👻🌿
ian@hachyderm.iosomebody asked how people who have historically been anti-copyright could be against AI content theft, so let me give this a shot:
Information wants to be free to enrich human knowledge. It does not want to be free to make human knowledge worse to enrich the pockets of assholes
Trail of Bits
trailofbits@infosec.exchangeOur tl;dr from @RealWorldCrypto
https://buff.ly/4c3J70h
nixCraft 🐧
nixCraft@mastodon.socialFYI, there is a bug in systemd. So, running: "systemd-tmpfiles --purge" will delete your /home/ in systemd version 256. #linux
Source: https://mathstodon.xyz/@bremner/112615591101488528 and https://x.com/DevuanOrg/status/1802997574695080067
the grugq
thegrugq@infosec.exchangeThis is a keynote that I quite enjoy and highly recommend. https://mastodon.social/@joxean/112631528543638454
daniel:// stenberg://
bagder@mastodon.socialNewly disclosed (and dismissed) #curl vulnerability reports
"HTTP headers eat all memory:"
https://hackerone.com/reports/2552192
"Incorrect conversion in hostname"
https://hackerone.com/reports/2552179
"Unicode-to-ASCII conversion in cmdlines on Windows lead to argument injection"
https://hackerone.com/reports/2550951
Transparency baby.
cynicalsecurity 
cynicalsecurity@bsd.network
The new Intel Skymont architecture details, as presented brilliantly by Chips & Cheese¹ (strongly recommended) have a very "inspiring" paragraph:
"Skymont duplicates microcode for the most common complex instructions across all three clusters, letting them handle those instructions without blocking each other. Intel gave gather instructions as an example, which can load from multiple non-contiguous memory locations."
Intel is calling this nanocode, I am calling this a new playground...
__
¹ https://chipsandcheese.com/2024/06/15/intel-details-skymont/
Veronica Explains
vkc@linuxmom.netYou open up a Commodore 64, and the box says "welcome to the world of friendly computing."
You turn on a modern PC, and it immediately threatens your data unless you agree to save your data to *their* cloud service.
That right there is why we talk about vintage computers. Folks need to be reminded of what's possible.
Lorin Hochstein 
norootcause@hachyderm.io
Cook’s “How complex systems fail” is the most personally impactful paper I have ever read, and yet I’m convinced that it would never have been accepted for publication in a peer-reviewed journal.
https://www.adaptivecapacitylabs.com/HowComplexSystemsFail.pdf