Posts
3325Following
710Followers
1575nixCraft 🐧
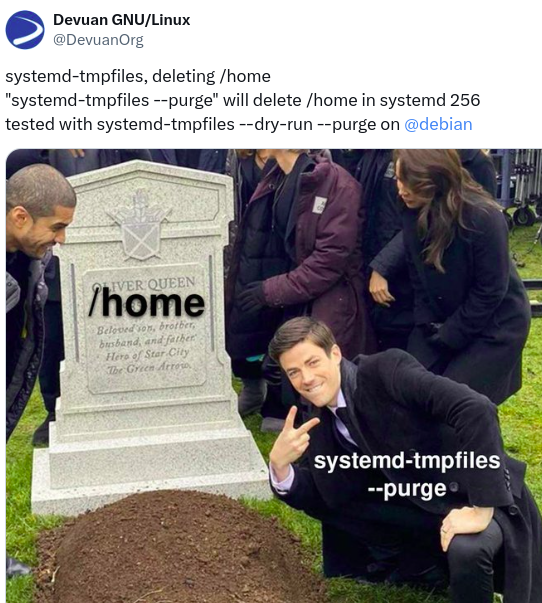
nixCraft@mastodon.socialFYI, there is a bug in systemd. So, running: "systemd-tmpfiles --purge" will delete your /home/ in systemd version 256. #linux
Source: https://mathstodon.xyz/@bremner/112615591101488528 and https://x.com/DevuanOrg/status/1802997574695080067
the grugq
thegrugq@infosec.exchangeThis is a keynote that I quite enjoy and highly recommend. https://mastodon.social/@joxean/112631528543638454
daniel:// stenberg://
bagder@mastodon.socialNewly disclosed (and dismissed) #curl vulnerability reports
"HTTP headers eat all memory:"
https://hackerone.com/reports/2552192
"Incorrect conversion in hostname"
https://hackerone.com/reports/2552179
"Unicode-to-ASCII conversion in cmdlines on Windows lead to argument injection"
https://hackerone.com/reports/2550951
Transparency baby.
cynicalsecurity 
cynicalsecurity@bsd.network
The new Intel Skymont architecture details, as presented brilliantly by Chips & Cheese¹ (strongly recommended) have a very "inspiring" paragraph:
"Skymont duplicates microcode for the most common complex instructions across all three clusters, letting them handle those instructions without blocking each other. Intel gave gather instructions as an example, which can load from multiple non-contiguous memory locations."
Intel is calling this nanocode, I am calling this a new playground...
__
¹ https://chipsandcheese.com/2024/06/15/intel-details-skymont/
Lorin Hochstein 
norootcause@hachyderm.io
Cook’s “How complex systems fail” is the most personally impactful paper I have ever read, and yet I’m convinced that it would never have been accepted for publication in a peer-reviewed journal.
https://www.adaptivecapacitylabs.com/HowComplexSystemsFail.pdf
TROOPERS Conference
WEareTROOPERS@infosec.exchange📢 Next week is #TROOPERS24 week! We will celebrate 15 years of making the world a safer place and are looking forward to all of you. See you in #Heidelberg. 🥳
Jason Scott
textfiles@mastodon.archive.orgA few years ago, a kid mourning his dad handed me over 300 DVDs his dad had made of local bands in his London Suburb in the 2010s before passing on. He didn't know what do with them. I did. All of them are up at Internet Archive, hundreds of hours of cover bands playing in a bar, and now, thanks to a volunteer, Ducky, we have them all with dates and descriptions, where known. Enjoy.
Binary Ninja
binaryninja@infosec.exchangeOur Program Analysis for Vulnerability Research class is filling up, if you were planning on attending Recon in a few weeks and were hoping to grab one of the last seats, you move quickly!
https://recon.cx/2024/trainingprogramanalysisforvulnerabilityresearch.html
Trail of Bits
trailofbits@infosec.exchangeFuzzing can do more than find memory corruption vulnerabilities. With the right invariants, it can catch runtime errors and logical issues, as demonstrated by our custom testing harness for Fuel Labs. https://blog.trailofbits.com/2024/06/17/finding-mispriced-opcodes-with-fuzzing/
Slashdot 
slashdot@mastodon.cloud
ASUS Releases Firmware Update for Critical Remote Authentication Bypass Affecting Seven Routers https://mobile.slashdot.org/story/24/06/17/0237229/asus-releases-firmware-update-for-critical-remote-authentication-bypass-affecting-seven-routers?utm_source=rss1.0mainlinkanon
pancake 
pancake@infosec.exchange
IBM vs LzLabs. On reverse engineering zOS / mainframe software and big corpo lawsuits https://mainframeupdate.blogspot.com/2024/06/ibm-versus-lzlabs.html
/r/netsec
_r_netsec@infosec.exchangeAbusing title reporting and tmux integration in iTerm2 for code execution (CVE-2024-38396) https://vin01.github.io/piptagole/escape-sequences/iterm2/rce/2024/06/16/iterm2-rce-window-title-tmux-integration.html
Chris Gioran 💔
chrisg@fosstodon.orgThe year is 2030.
Computers boot directly into the browser. IDEs are just a web app now, running in the GPU. No one knows why. Or how.
All programs run in 4 nested containers on top of a hypervisor abstracting over the 5 major computational clouds. The last time a branch was predicted correctly, in any CPU anywhere, was 4 years ago.
Cloud costs are withdrawn directly from your retirement fund.
Ext7 just came out, it's written in Javascript and uses AI to guess what the file may contain.
Frederik
fre@infosec.exchangeI've done it! After literal months of work, I've finally finished my (rather long) blog post about how AES-GCM works and how it's security guarantees can be completely broken when a nonce is reused:
It includes more than 10 interactive widgets for you to try out AES-GCM, GHASH and the nonce reuse attack right in your browser! (Powered by #RustLang and #WASM )
If you're interested in #cryptography , #math (or #maths ) or #infosec you might find it interesting.
If you do read it, I'm all ears for feedback and criticism!
Filippo Valsorda
filippo@abyssdomain.expertJust published age v1.2.0 ✨
Minor release:
• binaries built with Go 1.22.4
• plugin client API
• CLI edge case fixes
• RecipientWithLabels to make auth'd or post-quantum recipients
Very happy about the last point, it was the last hardcoded thing about scrypt recipients.
screaminggoat
screaminggoat@infosec.exchangeProof of concept for CVE-2024-26229 (7.8 high, disclosed 09 April 2024 by Microsoft) Windows CSC Service Elevation of Privilege Vulnerability is allegedly available: https://github.com/varwara/CVE-2024-26229
@hexnomad can you confirm that the CWE is actually CWE-781: Improper Address Validation in IOCTL with METHOD_NEITHER I/O Control Code?
#CVE_2024_26229 #proofofconcept #CVE #vulnerability #Microsoft #MSRC
0xor0ne
0xor0ne@infosec.exchangeExcellent guide to page cache, memory management, mmap and cgroups in Linux kernel
https://biriukov.dev/docs/page-cache/0-linux-page-cache-for-sre/
Credits @brk0v
Hacker News 100
hn100@social.lansky.nameGoogle, Cloudflare and Cisco will poison DNS to stop piracy block circumvention
Link: https://torrentfreak.com/google-cloudflare-cisco-will-poison-dns-to-stop-piracy-block-circumvention-240613/
Discussion: https://news.ycombinator.com/item?id=40693451
raptor 
raptor@infosec.exchange
#ManageEngine #ADAudit - Reverse engineering #Windows #RPC to find CVEs