Posts
2711Following
681Followers
1505Alex Stamos
alex@cybervillains.comAnyDesk was popped, with 170,000 advertised users.
They claim their install base is secure, but that the code signing cert was stolen. From the changelog, its clear that they knew this on January 29th but didn't announce until the end of the day on a Friday. Not cool.
Based upon their actions so far, I would recommend all enterprises kill AnyDesk across their fleet using EDR or other means for now until we know more.
https://anydesk.com/en/public-statement
https://anydesk.com/en/changelog/windows
Dan Hulton
danhulton@hachyderm.ioI wanna surface this to my main timeline because it's kinda important to say out loud from time to time:
Businesses do NOT "have to" focus exclusively on their return to shareholders. Not legally, not morally.
That is the misguided OPINION of a 1970 essay by Milton Friedman, and the fact that everyone seemed to just hop on board that opinion is a significant reason why we switched gears into hyper-hell-capitaliam since then.
Push back on this every time you see it.
Aaron Toponce ⚛️
atoponce@fosstodon.org
Given Okta's recent troubles with keeping their network secure, I guess I shouldn't be surprised by this blog post.
Still, a company that supposedly markets and sells security services, you would think they would have a better handle on something as rudimentary as password hashing.
TL;DR- Use SHA-2 or SHA-3 to hash passwords.
🤦🏻
https://auth0.com/blog/hashing-passwords-one-way-road-to-security/
Kevin Beaumont
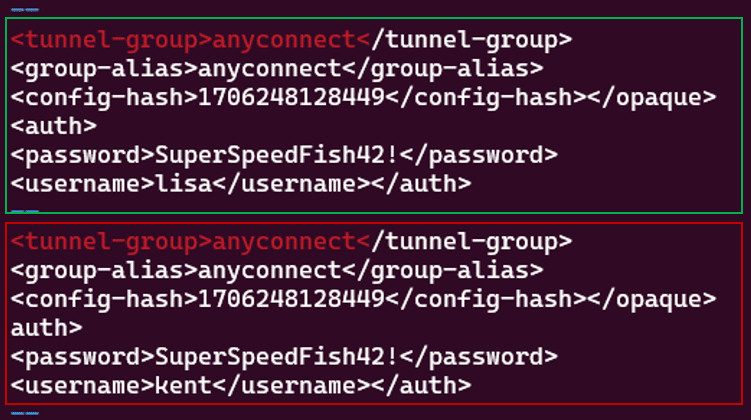
GossiTheDog@cyberplace.social🚨 patch your Cisco AnyConnect boxes 🚨
For a 2020 vulnerability. Really.
Lots of ransomware cases coming in for Cisco AnyConnect/ASA recently and finally we know how - CVE-2020-3259
It was a vuln which allowed a CitrixBleed style memory dump, found by a Russian research org now under US sanctions. Ransomware operators have an exploit.
Sadly it looks like many orgs never patched.
Mastodon Engineering
MastodonEngineering@mastodon.socialWe are planning to release critical security patches for versions 3.5, 4.1, 4.2 and nightly this Thursday, Feb 01, at 15:00 UTC. We encourage server administrators to plan for a timely upgrade to ensure their Mastodon server is protected.
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgMicrosoft is trying to get all email users, including governments, to migrate to their cloud-based solutions. This makes their email cloud _THE_ prime target for nation-state/state sponsored hackers. Yet Microsoft appears to be leaving gaping security holes in the setup of their email services: https://arstechnica.com/security/2024/01/in-major-gaffe-hacked-microsoft-test-account-was-assigned-admin-privileges/
nano's old account's rotting corpse
nano@fedi.nano.lgbt
John Mark  ☑️
☑️
johnmark@freeradical.zone
Just read @pluralistic 's blog post about the difficulty that @2600 is having, both with its publication and producing the #HOPE con. This is tragic - I've never attended HOPE, but I've seen many videos and read so many recaps and articles inspired by it. Support 2600 today!
https://pluralistic.net/2024/01/19/hope-less/#hack-the-planet
https://www.hope.net/
https://store.2600.com/products/tickets-to-hope-xv
Doctor Memory
memory@blank.orgRIP the man who was the absolute incarnation of XKCD's "one random dude holding up the entire internet". You may never have heard of David Mills, but your entire goddamn world depends on what he did.
christine
christine@ruby.socialFor my hackathon project I did try to make CFA (Cat Factor Authentication, using your cat's microchip as a second factor) a thing 😆 The project did win a prize, but more for the experimentation then the actual result https://wpengine.com/blog/hackathon-december-2023/
quarkslab
quarkslab@infosec.exchangeIs remote code execution in UEFI firmware possible? Well, yes it is.
Meet #PixieFAIL: 9 vulnerabilities in the IPv6 stack of EDK II, the open source UEFI implementation used by billions of computers.
Full details by @fdfalcon and @4Dgifts in our new blog post:
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgThis blog post comes from deep inside the world of advertising, from people trying to move away from cookies. And along the way offer a VERY rare insight into the dark technology behind advertising and tracking ("hashed offline passbacks", "first and multi-touch attribution"), stuff you almost never read about. https://blog.sentry.io/we-removed-advertising-cookies-heres-what-happened/
Günter Born
gborn@social.tchncs.deAfter the takeover by Broadcom, VMware is in total chaos when it comes to orders and license renewals. Here is a status overview.
mistymntncop
blackeggs@infosec.exchange@pervognsen Did u see that the RAD Debugger has been released :O ? https://github.com/EpicGames/raddebugger
martenson
martenson@mastodon.world"OpenAI says it’s “impossible” to create useful AI models without copyrighted material"
10 years ago three dudes from Sweden were hunted by FBI, Interpol and their own government for challenging copyright laws and seeking a fresh approach without ever profiting from it. 🏴☠️
Now venture capitalist-backed corporations will sell us our own copyrighted material at a premium. Working tirelessly to embed it in every product designed from now on so you will not be able to avoid it. 💰


 🌻
🌻 







