Posts
3014Following
699Followers
1547Mr. Bitterness
wdormann@infosec.exchangeSo apparently starting with Linux 5.18, ASLR is weakened for 64-bit executables, and absolutely BROKEN (i.e. not present) for 32-bit executables when the library is 2MB or larger.
Oops? 🤦♂️
https://zolutal.github.io/aslrnt/
The Verge
verge@mastodon.socialFTC bans major data broker from selling invasive location tracking details https://www.theverge.com/2024/1/10/24032966/ftc-bans-outlogic-location-data-sales-tracking-settlement?utm_content=buffer92d43&utm_medium=social&utm_source=bufferapp.com&utm_campaign=buffer
@yabellini@fosstodon has moved
yabellini@fosstodon.orgDid you realize that we live in a reality where SciHub is illegal, and OpenAI is not?
Jayne
dotjayne@tech.lgbt80 character column limits in code are a legacy from 80 column text displays which are a legacy of IBM's 80 column punch cards which are a legacy of Roman chariots which had two side-by-side 40 column horses
❄️☃️Merry Jerry🎄🌲
jerry@infosec.exchangeIt's probably obvious to most of you, but a big difference between the commercial social media platforms and the fediverse is that as those commercial platform grow, they get additional revenue from ads, from selling personal information, and otherwise monetizing their users. While that is turning out to not actually pay the bills for them, in the fediverse, just about every instance is run by volunteers and funded by donations or out of the volunteers' pockets. It's a labor of love and a hope for a better future. When traffic grows, we need to expand our capacity.
That is why I am asking, if you are able, please consider donating to the instance you on to help keep the fediverse ecosystem going. Typically the /about web page will have details on how to donate.
Note: I am well aware that many of you are not in a financial position to donate - and that is OK. We are here to serve you as well. Donations are completely optional.
Timo Lo(n)gin
login@infosec.exchangeThe first version of an SMTP smuggling scanner is now available at https://github.com/The-Login/SMTP-Smuggling-Tools.
More tools to come! Feedback is much appreciated!
Foone🏳️⚧️
foone@digipres.clubThe 37C3 talk on TEA1 encryption (used by police and military units in europe) is hilarious.
The hackers announced they found a vulnerability in the encryption, and one of the ways the organization that standardized the TEA1 encryption downplayed the breach was by saying that it wasn't viable, because it required "high powered GPUs".
So they ported their algorithm to a Toshiba Satellite P1 running Windows 95, and re-cracked the encryption there.
Neil Craig
tdp_org@mastodon.socialI've only just noticed that GitHub has a "Download SBOM" button on repos, e.g. https://github.com/bbc/simorgh/network/dependencies
It's in SPDX format (https://spdx.github.io/spdx-spec/v2.3/introduction/) which seems pretty reasonable to me from a machine-reading PoV.
Hopefully being a standardised format means it can be ingested into standardised tooling.
gábor ugray
twilliability@genart.socialUnder-the-radar late night launch: RSS Parrot is live! It talks like Mastodon, but it doesn't walk like Mastodon. BUT! It will relay any RSS feed straight into your timeline.
Turn Mastodon into your very own feed reader. Follow anything that has an RSS feed and get a toot about new posts.
How? Mention @birb with the address you want to follow.
More details at https://rss-parrot.net. Boost for visibility :)
abadidea
0xabad1dea@infosec.exchangePSA to all junior hackers: pasting some random code into GPT, asking it to “identify” a security vulnerability, and submitting it as a bug bounty will never, ever work. You will succeed only in getting yourself banlisted as a crank.
You can spend five years becoming an actual expert or you can find a career that’s easier for you; if it were so easy that ChatGPT could do it, there wouldn’t be any bug bounties
Paolo Melchiorre
paulox@fosstodon.orgI highly recommend supporting the Standard Ebooks project. 📚
«Standard Ebooks is a volunteer-driven project that produces new editions of public domain e-books that are lovingly formatted, open source, free of copyright restrictions, and free of cost.»
Donate 👇
https://standardebooks.org/donate
Please boost 🙏
#standardebook #standardebooks #ebook #ebooks #publicdomain #book #books #reading #epub #standard
Taggart 
mttaggart@infosec.town
Okay, listen up:
Mozilla is two different entities. The Mozilla Corporation and the Mozilla Foundation. The second one? That’s the social good one you really want focused on important things.
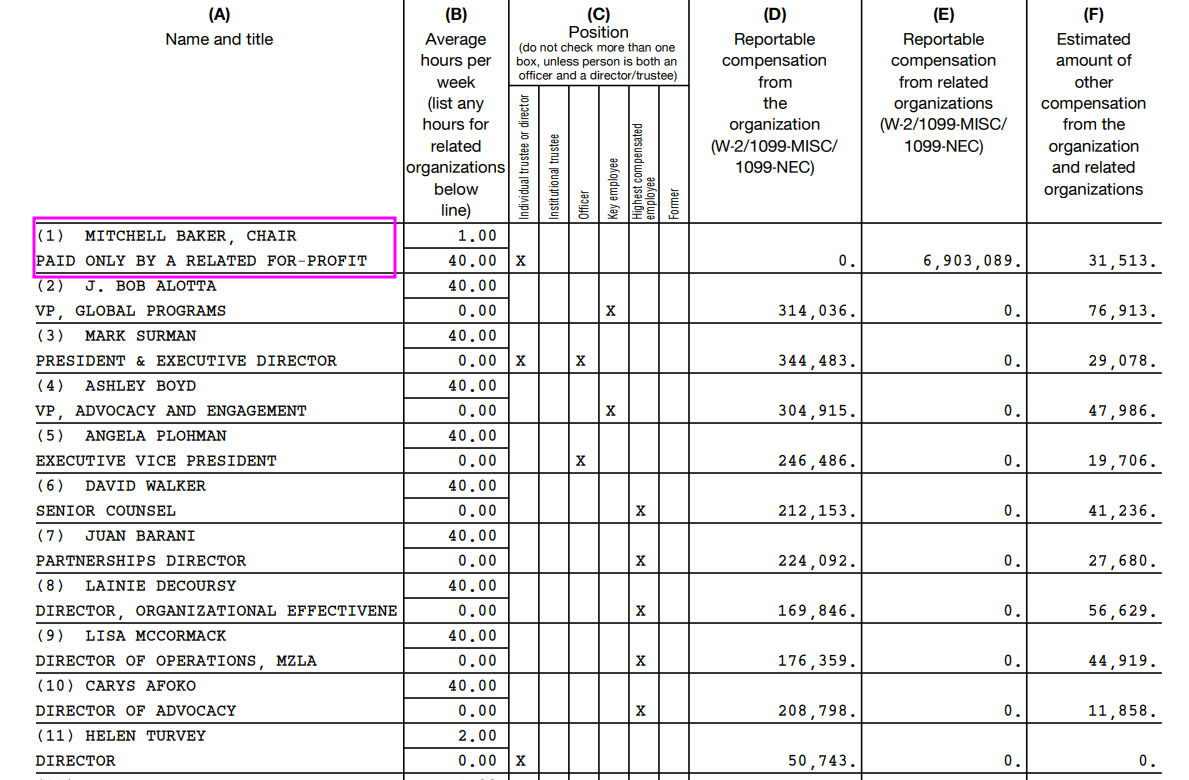
The Mozilla Foundation, like all non-profits, publishes their Form 990 annually to disclose compensation. Here it is.
You’ll see that the top earner there, Mitchell Baker, who is very handsomely rewarded, is actually paid by the Mozilla Corporation, not the Foundation. Put another way, the non-profit is not blowing its funding on a CEO.
And the corp, by the way, is what generates revenue that largely funds Firefox.
The annual report of the Foundation shows a pretty healthy financial situation, and increased investment in public good projects year-over-year.
I don’t like everything they do either (e.g. that risible website generator), but I don’t actually think they are suffering from a lack of focus. They’re suffering from a mature market.
benjojo
benjojo@benjojo.co.ukJeremiah Lee
Jeremiah@alpaca.goldI want Firefox to succeed more than ever and I support Mozilla finding better revenue sources than search engine default sales, but I do not support a $7M salary for its CEO.
I canceled my recurring donation to Mozilla because I need that money more than Mozilla’s CEO needs that money.
If there is a direct funding option of developers working on Firefox, I will happily reallocate that money. Send me links.
Source: Form 990 https://stateof.mozilla.org/
Edit: Replaced commentary with direct source
kira :3
chrisisgr8@tech.lgbtinfosec best practice in 2023: do not use or install any software
So some fun stuff was just presented at 37C3, and... I bet I have some answers.
https://securelist.com/operation-triangulation-the-last-hardware-mystery/111669/
First, yeah, the dbgwrap stuff makes perfect sense. I knew about it for the main CPUs, makes perfect sense it'd exist for the ASCs too. Someone had a lightbulb moment. We might even be able to use some of those tricks for debugging stuff ourselves :)
Second, that "hash" is almost certainly not a hash. It's an ECC code**. I bet this is a cache RAM debug register, and it's writing directly to the raw cache memory array, including the ECC bits, so it has to manually calculate them (yes, caches in Apple SoCs have ECC, I know at least AMCC does and there's no reason to think GPU/ASC caches wouldn't too). The "sbox" is just the order of the input bits to the ECC generator, and the algorithm is a textbook ECC code. I don't know why it's somewhat interestingly shuffled like that, but I bet there's a hardware reason (I think for some of these things they'll even let the hardware synthesis shuffle the bits to whatever happens to be physically optimal, and that's why you won't find the same table anywhere else).
This explains the behavior where writing to KTEXT works "sometimes" and panics AMCC others. There is a vulnerability in the SoCs that *I* discovered and reported where cache snooping bypasses CTRR at the AMCC level. You can "write" to read only memory ranges and, as long as those writes remain in snoopable cache, they are effective even though AMCC will block them and panic when they are written back. I didn't get any money for that one because the way I exploited it didn't apply to normal macOS (I used it to patch DCP code from m1n1), but now a nation state figured out how to use it for a real exploit chain. "Whoops".
So what was being observed there was that writing to kernel text "worked" *as long as that cache line remained dirty*. Then once it got written back, AMCC panic.
This whole thing hinges on the elephant in the room that, for performance reasons, **there is no IOMMU for the GPU**. PPL security relies entirely on GFX-ASC uPLL software protection and the GPU page tables being managed properly by PPL. This fun fact got Lina a $150k bounty when she found major bugs across the stack that allowed a full takeover from userspace shaders. Now someone else figured out how to puppeteer either GFX-ASC or the GPU L2 cache* from EL2/1, bypassing PPL from the kernel. I bet this isn't the last time we're going to see fun memory bypasses that hinge on the GPU. Heck, for all we know, these attackers might've even been inspired by Lina's antics :)
The patch for this vector is trivial: you don't let the kernel map that register range via PPL. Now the question is, how long until someone else finds another fun bypass using another obscure feature or bug of the GPU or its firmware?
* Probably the GPU L2, since as far as we know the GFX-ASC L1 isn't system fabric coherent, but GPU L2 is.
** Why do I know about ECC codes? Because this is the same algorithm used for ECC on the Nintendo Wii NAND lol, I've literally written this code before.
hanno
hanno@mastodon.socialSecurity vulnerabilities in Antivirus software are no big deal, right? I mean, they never get exploited for real, right? Like this one, where Barracuda just ran a random, unaudited perl library with eval in it as part of its Antivirus, and then some malware used it. That's basically a non-issue some infosec people like to overblow because they don't like AVs. https://www.barracuda.com/company/legal/esg-vulnerability
web3 is going just great
web3isgreat@indieweb.socialTether mints itself a $1 billion Christmas present
December 25, 2023
https://web3isgoinggreat.com/?id=tether-christmas-2023-mint