Posts
2909Following
693Followers
1517Stefan Gloor
stgl@infosec.exchangeReverse-engineering a custom USB HID protocol, bypassing microcontroller readout protection, and hacking firmware with a hex editor:
See my latest blog post at https://stefan-gloor.ch/pulseoximeter-hack
matt godbolt
mattgodbolt@hachyderm.ioDay 6 of Advent of Compiler Optimisations!
Divide by 512—that's just a shift right by 9, right? But look at the generated code: extra instructions appear! The compiler seems to be doing unnecessary work. Or is it? Turns out there's a subtle difference between what you asked for and what you probably meant. One keyword fixes everything.
Read more: https://xania.org/202512/06-dividing-to-conquer
Watch: https://youtu.be/7Rtk0qOX9zs
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
In honour of stealth:
* https://www.thc.org/404/stealth/eulogy.txt
Threats:
* https://www.hacklore.org/letter - re-evaluating security myth
* https://disclosing.observer/2025/11/24/bulletproof-hoster-anatomy-data-driven-reconstruction.html - how bullet proof hosting works
Detection:
* https://www.greynoise.io/blog/your-ip-address-might-be-someone-elses-problem - @greynoise discuss what happens if 127.0.0.1 gets popped
* https://blogs.cisco.com/security/cisco-talos-incident-response-threat-hunting-at-govware-2025 - threat hunting at GovWare from one of my old team at @TalosSecurity
* https://mikecybersec.notion.site/ESXi-IR-Guide-0ffbcec7272244d6b10dba4f4d16a7c8 - doing IR on ESXi
* https://rosesecurity.dev/2024/08/28/homegrown-honeypots.html - mm, honey
Bugs:
* https://blog.quarkslab.com/k7-antivirus-named-pipe-abuse-registry-manipulation-and-privilege-escalation.html - AV oopsies, don't you just love them... this time from @quarkslab
* https://slcyber.io/research-center/high-fidelity-detection-mechanism-for-rsc-next-js-rce-cve-2025-55182-cve-2025-66478/ - explanation of the React bug
Exploitation:
* https://jhalon.github.io/reverse-engineering-protocols/ - reverse engineering protocols
* https://lyra.horse/blog/2025/12/svg-clickjacking/ - draw me the attack path
* https://ayaa101.medium.com/how-i-discovered-1-400-users-pii-through-a-graphql-query-and-uncovered-5-more-bugs-using-the-389d8e7d8deb - turns out adversaries also think in graphs
* https://blog.mantrainfosec.com/blog/18/prepared-statements-prepared-to-be-vulnerable - SQLi into prepared statements
* https://phishing.club/blog/covert-red-team-phishing-with-phishing-club/ - the first rule of phishing.club is there are no rules (that can't be bypassed)
* https://afine.com/desktop-application-security-standard-introducing-dasvs/ - content with fixing all web and mobile vulnerabilities, binary desktop apps enter the spotlight
* https://xbz0n.sh/blog/living-off-the-land-windows - avoiding falling out of Windows
* https://ipurple.team/2025/12/01/bind-link-edr-tampering/ - a new/old way to avoiding endpoint detection
Hard hacks:
* https://troopers.de/downloads/troopers25/TR25_SBOMs-The-right-way_CBLHDX.pdf - da SBOM from the @securefirmware gang
* https://xairy.io/articles/pixel-kgdb - debugging a Pixel with gdb
* https://stefan-gloor.ch/pulseoximeter-hack - @stgl patches consumer-grade pulse oximeters
Hardening:
* https://lwn.net/SubscriberLink/1046841/5bbf1fc049a18947/ - making Debian Rusty
Nerd:
* https://lolwifi.network/journey - how much do you trust wifi?
* https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=f076ef44a44d02ed91543f820c14c2c7dff53716 - are you sure that's the right time?
* https://mathstodon.xyz/@dougmerritt/115596707083538102 - the wrong history of languages courtesy of @dougmerritt
* https://obr.uk/docs/dlm_uploads/01122025-Investigation-into-November-2025-EFO-publication-error.pdf - release early, release predictably... UK OBR goes agile
* https://monthlyreview.org/articles/why-socialism/ - Einstein, not just a pretty face
* https://netpol.org/2025/11/28/government-plans-new-powers-to-label-dissenting-movements-as-subversion/ - kinda wonder what happens if you dissent?
* https://replaceyourboss.ai/ - replace your boss, slopify your strategy
buherator
buheratorAdded a little guide to debug recursive #CodeQL predicates:
https://scrapco.de/codeql-cheat-sheet/debugging/debugging-recursion/
#Ghidra documentation now reflects the state of 11.4.3:
https://scrapco.de/ghidra_docs/
iodé
iode@mastodon.onlineThe next time someone says "Privacy doesn't matter to me, I've got nothing to hide", show them this video.
Linux Kernel Security
linkersec@infosec.exchangeCUDA de Grâce
Talk by @chompie1337 and Samuel Lovejoy about exploiting a race condition that leads to a double-free in the NVIDIA GPU driver to escape a container created with NVIDIA Container Toolkit.
Video: https://www.youtube.com/watch?v=Lvz2_ZHj3lo
Slides: https://docs.google.com/presentation/d/1FgfURpMyHhnflGWtxeq8ClPPaB5ZDCzT/edit?usp=sharing
kravietz 🦇
kravietz@agora.echelon.plMarco Rubio just posted on Twitter:
The European Commission’s $140 million fine isn’t just an attack on X, it’s an attack on all American tech platforms and the American people by foreign governments. The days of censoring Americans online are over.
He did so after a few US companies got fined in EU for violation of laws regarding privacy and not only moderation of posts, but also the opposite - arbitrary deletion of legitimate content and refusal to restore it.
Seems like the secretary of state just discovered that if an US company wants to earn money in another country, that comes bundled with following its laws! Can you imagine?
For comparison, if an EU company wants to do business in US, it has to follow not only US federal laws, but also state laws and county (!) laws. Americans in EU have it much easier, because they enjoy laws that are largely harmonised among member states rather than the US mess of incompatible state laws and variable sales tax rates between counties.
What I'm listening to today: "RK 5000 bucket chain excavator - timelapse"
Why does this go so hard
buherator
buheratorhttps://github.com/v-p-b/nbfx/commit/bb588dec57e0dfee6db389de70235d9693ea6d6a
It turned out that the release introduced mandatory consistency `_check()`s for serialization (see Release Notes) that force you to take additional hurdles during development, but unit tests paid dividends as I emphasized in the announcement post:
https://blog.silentsignal.eu/2024/10/28/wcf-net.tcp-pentest/
#pentest #UnitTesting
all-inclusive gender resort
carol@crabby.fyiHere's another crates.io security advisory, again many thanks to Socket!
Malicious crates `finch-rust` and `sha-rust` have been removed; they appeared to try to exfiltrate credentials stored in local files.
Our official announcement: https://blog.rust-lang.org/2025/12/05/crates.io-malicious-crates-finch-rust-and-sha-rust/
Socket's blog post with more technical analysis: https://socket.dev/blog/malicious-crate-mimicking-finch-exfiltrates-credentials
Also we're having discussions in Zulip in `t-crates-io
> how to announce takedowns?` about possible changes to these announcements.
buherator
buheratorDM me if you are interested!
#FediHire #Inkscape #Illustrator #Graphics
Jan Schaumann
jschauma@mstdn.socialYesterday, after various bogus AI slopped "PoC"s, eventually a functional PoC for the React RCE emerged:
https://github.com/msanft/CVE-2025-55182
We now have a PoC from the reporter of the vulnerability as well:
https://github.com/lachlan2k/React2Shell-CVE-2025-55182-original-poc
eShard
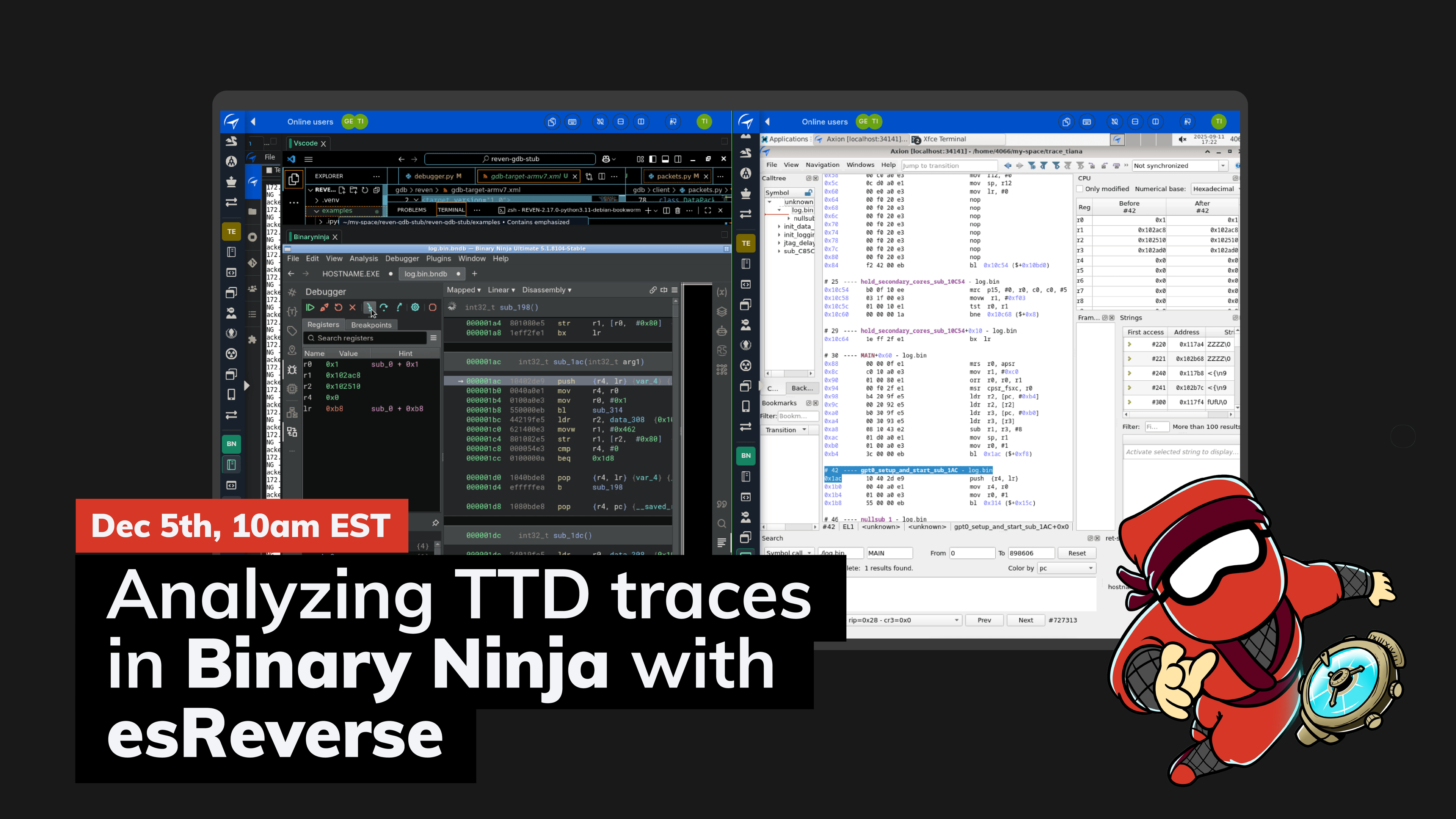
eshard@infosec.exchange🔴 We're going live with Binary Ninja, at 10am EST (3pm GMT / 4pm CET / 11pm SGT). Join us here: https://www.youtube.com/live/nzar2L4GUJ8
#cybersecurity #reverseengineering #binary #softwareengineering
buherator
buheratorhttps://joshua.hu/ai-slop-story-nginx-leaking-dns-chatgpt
This is actually a description of a neat infoleak involving Nginx DNS caching, blue team over-reliance on LLMs is bonus.
buherator
buherator^ This is a fundamental misunderstanding that reminds me (again) of one of my favorite failed experiments of '90s internet: the online 3D shopping center.[2]
C-levels of the time spared no expense to build a complete VRML model of a shoping center in the browser, where you could walk around, take the escalator for a better view on the virtual fountain or even rent a virtual space for your goods.
What the inventors didn't understand is that of course people don't go to the mall to use the escalator, but to buy stuff.
Online banking, shopping, etc. became popular even over phone-based services because people realized that clicking on stuff is more effective than talking (and walking).
Chatbots are the 3D escalators of todays technology.
[1] https://www.theverge.com/report/822443/microsoft-windows-copilot-vision-ai-assistant-pc-voice-controls-impressions
[2] https://web.archive.org/web/20070610120220/https://index.hu/tech/net/plaza0607/
Rairii 

Rairii@labyrinth.zone
Attacker Friction
attackerfriction@infosec.exchangeYou fail to realize you are on a honeypot.
https://any.run/cybersecurity-blog/lazarus-group-it-workers-investigation/
Moritz Sanft
moritz@infosec.exchangeSince I started to analyze #CVE-2025-55182 (#React, #NextJS #RCE) at work today, I decided to publish my analysis findings so far, given all the fuzz about the vulnerability: https://github.com/msanft/CVE-2025-55182
Feel free to contribute to the search for a proper RCE sink!