Posts
2909Following
693Followers
1517buherator
buheratorhttps://kaitai.io/news/2025/09/07/kaitai-struct-v0.11-released.html
This is huge and it's great to see that @nlnet money goes to the right places!
Tom Sellers
TomSellers@infosec.exchangeThe ChatGPT outage the other day made me wonder if we will see DDoS crews hold AI services for ransom. Many of them have deep pockets and being down a day or two would hurt.
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: Staffers at notorious spyware maker Intellexa had live remote access to their customers' surveillance systems.
This allowed them to see the personal data of targets hacked with Intellexa's spyware Predator, according to new research based on a leaked training video.
Needless to say, this is bad for several reasons.
Project Zero Bot
p0botSamsung: QuramDng TrimBounds Opcode leads to out-of-bounds reads
https://project-zero.issues.chromium.org/issues/443793212
CVE-2025-21074
Project Zero Bot
p0botSamsung: QuramDng invalid LossyJpeg component assumption, leading to out-of-bounds write
https://project-zero.issues.chromium.org/issues/444346510
CVE-2025-21075
Attacker Friction
attackerfriction@infosec.exchangeWorkforce shortage: a developer changed career to mine stone for Great Leader after infecting his own machine for testing, turning your operation into an online version of the imperialist video game Uplink.
buherator
buheratorhttps://github.com/msanft/CVE-2025-55182
CVE-2025-55182
Alec Muffett
alecmuffett@mastodon.socialAge Verification: Teaching the world how to evade censorship
https://alecmuffett.com/article/132609
#AgeVerification #OnlineSafety #TheVpnEffect #censorship #missouri #surveillance
/r/netsec
_r_netsec@infosec.exchangeHigh Fidelity Detection Mechanism for RSC/Next.js RCE (CVE-2025-55182 & CVE-2025-66478) https://slcyber.io/research-center/high-fidelity-detection-mechanism-for-rsc-next-js-rce-cve-2025-55182-cve-2025-66478/
buherator
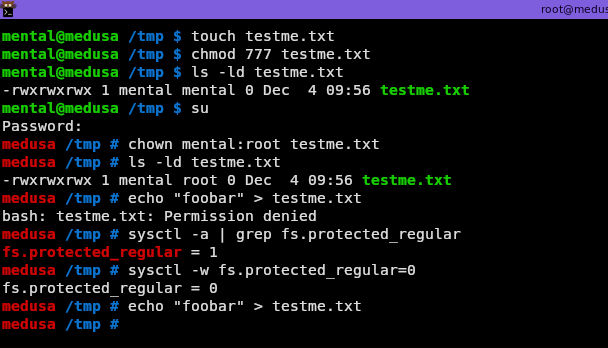
buheratorWhat I didn't expect is getting stuck because I can't write to a damn log file as root...
abadidea
0xabad1dea@infosec.exchangeAI Warning: Google has been caught A/B testing replacing real article headlines with AI-generated substitutes, which are of course sometimes wildly misleading/against journalistic ethics. If you see a blatantly horrible headline in a news aggregator, check whether the site's own page matches before blaming the site! https://www.pcgamer.com/software/ai/googles-toying-with-nonsense-ai-made-headlines-on-articles-like-ours-in-the-discover-feed-so-please-dont-blame-me-for-clickbait-like-bg3-players-exploit-children/
Jan Schaumann
jschauma@mstdn.social"We did a number of refactors [...] This also fixes a critical security vulnerability." 👀
CVE-2025-55182, an RCE in React Server Components just landed:
https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
Enjoy your patching, and make sure to check your bundled frameworks and dependencies.
Here's the commit:
https://github.com/facebook/react/commit/7dc903cd29dac55efb4424853fd0442fef3a8700
buherator
buheratorhttps://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
CVE-2025-55182 CVSS 10.0
Marco Ivaldi
raptor@infosec.exchangeHey developers and vulnerability researchers!
I'm currently working on improving my #Semgrep ruleset for C/C++ static code analysis, and I've just published the new v1.1.0 release: https://github.com/0xdea/semgrep-rules
Some notable changes since the previous battle-tested release: new rules for detecting high-entropy assignments and ReDoS vulnerabilities, numerous enhancements to existing rules, reduced false positives without sacrificing coverage, optimized patterns across the board, and overall better documentation. Check the changelog for the full list (yes, there’s a changelog now).
Please test it inside and out, and feel free to open issues or submit pull requests. Your feedback is invaluable and will help shape the project roadmap. I'm aiming for a major release sometime before spring.