Posts
2706Following
681Followers
1504FOR IMMEDIATE RELEASE: exploits.forsale's statement on the arrest of Peter Williams
buherator
buherator- Fixing bugs in Gradle scripts
- Resolving systemd and Network Manager fights
I see a pattern emerging!
buherator
buheratorhttps://jfrog.com/blog/CVE-2025-11953-critical-react-native-community-cli-vulnerability
"The Metro development server [..] binds to external interfaces by default [...] The server%27s /open-url endpoint handles a POST request that includes a user-input value that is passed to the unsafe open() function provided by the open NPM package, which will cause OS command execution."
Adam Caudill
adam_caudill@infosec.exchangeRandomly Scheduled Reminder: You should use a tool like Loqseq or Obsidian to keep notes and a journal of your life, work, and what you're doing. Future you will thank you. Having those details handy and searchable comes in handy in so many ways.
My approach: https://adamcaudill.com/2022/06/05/logseq-my-external-brain/
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: This is how former L3Harris Trenchant boss Peter Williams was able to steal zero-days worth millions of dollars and sell them to a Russian broker, based on court documents and interviews with his former colleagues.
A former Trenchant employee told me that “no one had any supervision over [Williams] at all. He was kind of allowed to do things the way he wanted to.”
“He was, in my opinion, perceived to be beyond reproach,” the former employee, who has knowledge of Trenchant's IT systems, told me.
Kevin Beaumont
GossiTheDog@cyberplace.socialNew by me - CyberSlop, where I look at orgs misusing GenAI fears to take from their own customers.
First threat actor - MIT and Safe Security go full cyberslop.
https://doublepulsar.com/cyberslop-meet-the-new-threat-actor-mit-and-safe-security-d250d19d02a4
Nina Kalinina
nina_kali_nina@tech.lgbtI love reverse-engineering because it allows me to dismantle structures of control.
Blacktop
blacktop__@bird.makeupFirst attempt at building macOS 26.0 XNU as a LIBRARY?! 👩🔬
Check it out! 🎉
https://github.com/blacktop/darwin-xnu-build/releases/download/v26.0/xnu-lib-26.0.tar.gz
CFG Bot 🤖
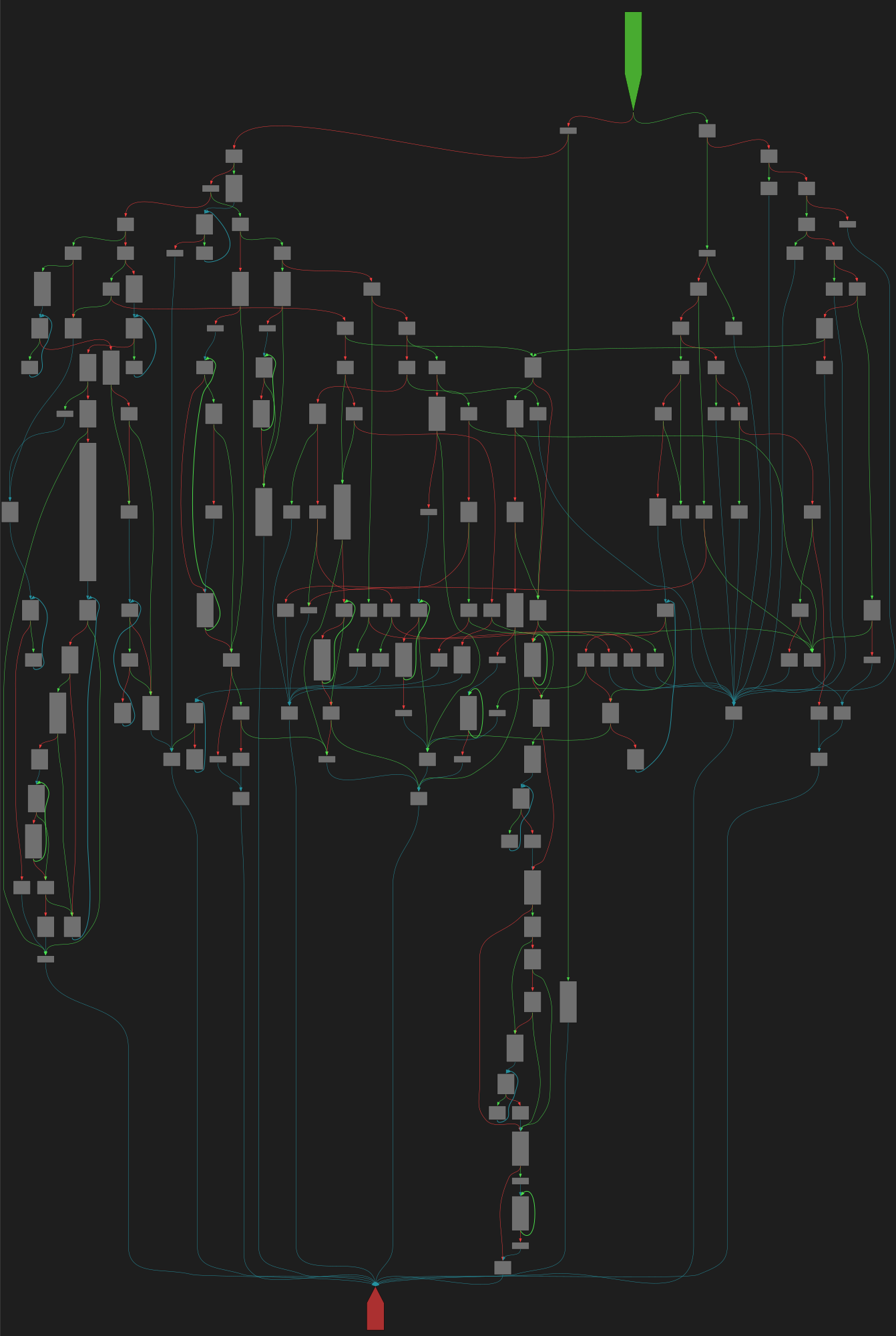
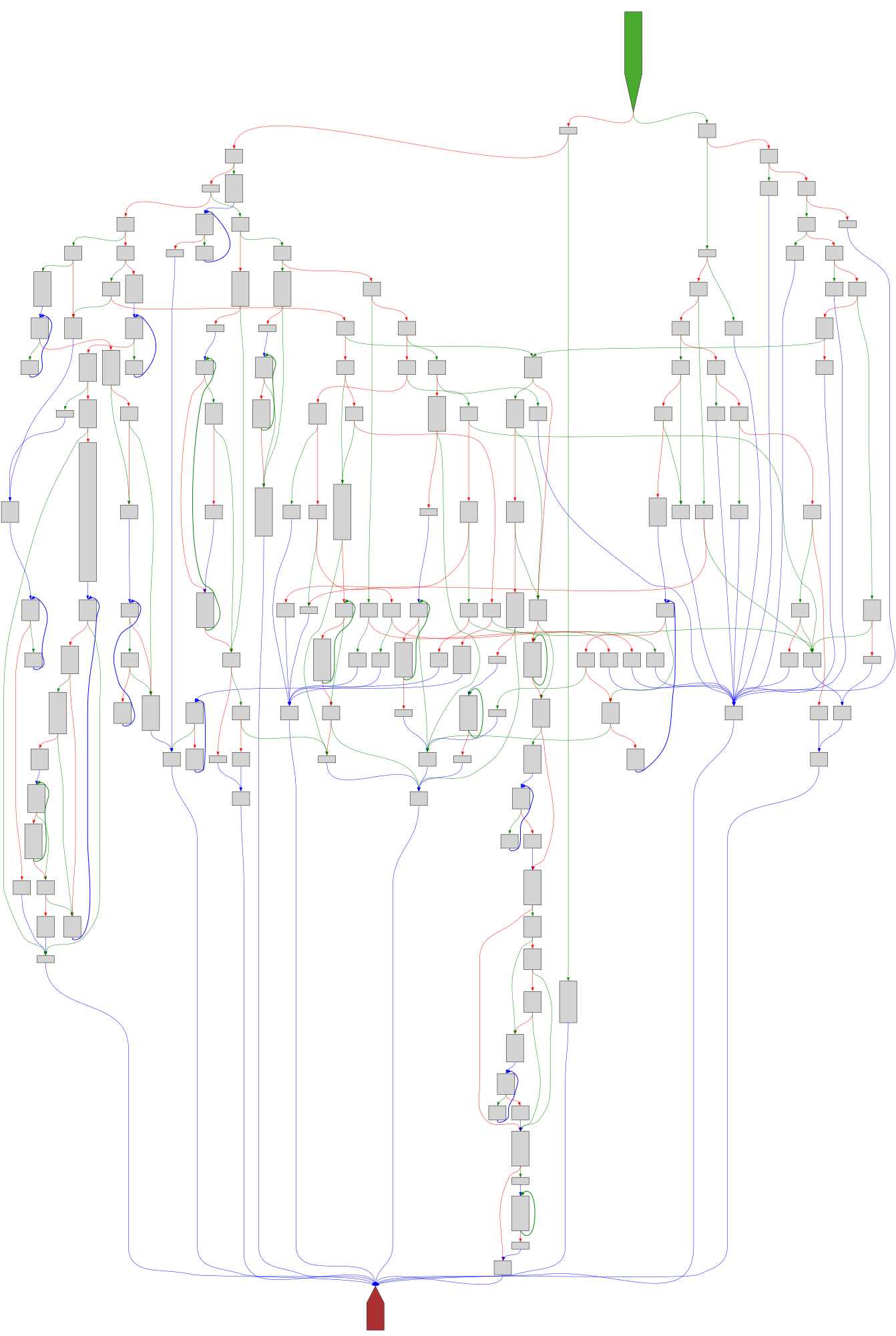
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a287e00
sqlite3GetToken
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a287e00.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a287e00.json&colors=light
Graham Sutherland / Polynomial
gsuberland@chaos.social@aeva oh and I run a script that pulls the UKF Drum & Bass Top 100 playlist every hour and turns it into a cumulative playlist containing everything that's ever been in the top 100 chart.
the official UKF playlist itself deletes all entries and re-adds them every time it's updated, so it all ends up with the same added timestamp and you can't tell what's new, so I made this to get around that issue.
https://open.spotify.com/playlist/3eV8DEw5Sm4dgzEZHy26lI
no external JSON export available on this one unfortunately.
ApplSec
applsec@infosec.exchange⚒️ FIXED IN iOS and iPadOS 26.1 ⚒️
- 18 bugs in WebKit
- 4 bugs in Model I/O
- 3 bugs in Safari
- 2 bugs in Apple Neural Engine
and 29 other vulnerabilities fixed
https://support.apple.com/en-us/125632
buherator
buheratorhttps://www.oobs.io/posts/four-bytes-one-lie/
CVE-2025-50168
Natalie Silvanovich
natashenka@infosec.exchangeNew Blog Post: Seth Jenkins broke kASLR by doing … nothing 😩
https://googleprojectzero.blogspot.com/2025/11/defeating-kaslr-by-doing-nothing-at-all.html
Jeff Atwood
codinghorror@infosec.exchangeUploaded here -- this is great! 🤩 https://stickertop.art/main/
Kevin Beaumont
GossiTheDog@cyberplace.socialMIT have also silently, without noting on the pages, started rewriting their website to remove references to their own work. They've also changed the URLs of the pages to remove references.
Left, before: https://archive.ph/SckSr
Right, after: https://mitsloan.mit.edu/ideas-made-to-matter/80-ransomware-attacks-now-use-artificial-intelligence
FFmpeg
ffmpeg@bird.makeupHere's an example of Google's AI reporting security vulnerabilities in this codec:
https://issuetracker.google.com/issues/440183164
We take security very seriously but at the same time is it really fair that trillion dollar corporations run AI to find security issues on people's hobby code? Then expect volunteers to fix.
https://bird.makeup/users/ffmpeg/statuses/1983949866725437791
FFmpeg
ffmpeg@bird.makeupArguably the most brilliant engineer in FFmpeg left because of this. He reverse engineered dozens of codecs by hand as a volunteer.
Then security "researchers" and corporate employees came along repeatedly insisted "critical" security issues were fixed immediately waving their CVEs.
This was hugely demotivating to the fun and enjoyment of reverse engineering.
https://bird.makeup/users/ffmpeg/statuses/1978390935433097310