Posts
2706Following
681Followers
1504BleepingComputer
BleepingComputer@infosec.exchangeAn out-of-band (OOB) security update that patches an actively exploited Windows Server Update Service (WSUS) vulnerability has broken hotpatching on some Windows Server 2025 devices.
Josh Bressers
joshbressers@infosec.exchangeThis week on #OpenSourceSecurity I talk to @ottok about his blog post about detecting an attack like xz in Debian
It's a fascinating conversation about a very complicated topic
There are things that could be detected, but this one would have been very very difficult
buherator
buheratorhttps://github.com/purseclab/deepSURF
buherator
buheratorhttps://research.checkpoint.com/2025/drawn-to-danger-windows-graphics-vulnerabilities-lead-to-remote-code-execution-and-memory-exposure/
Gareth Heyes 
gaz@infosec.exchange
Firefox nightly introduces the setHTML() method. Which is like a native DOMPurify. You can easily test it here:
https://portswigger-labs.net/mxss/
Set HTMLSanitizer ✅
Auto update ✅
I'm trying to break it, I encourage you to break it too
OpenSecurityTraining2
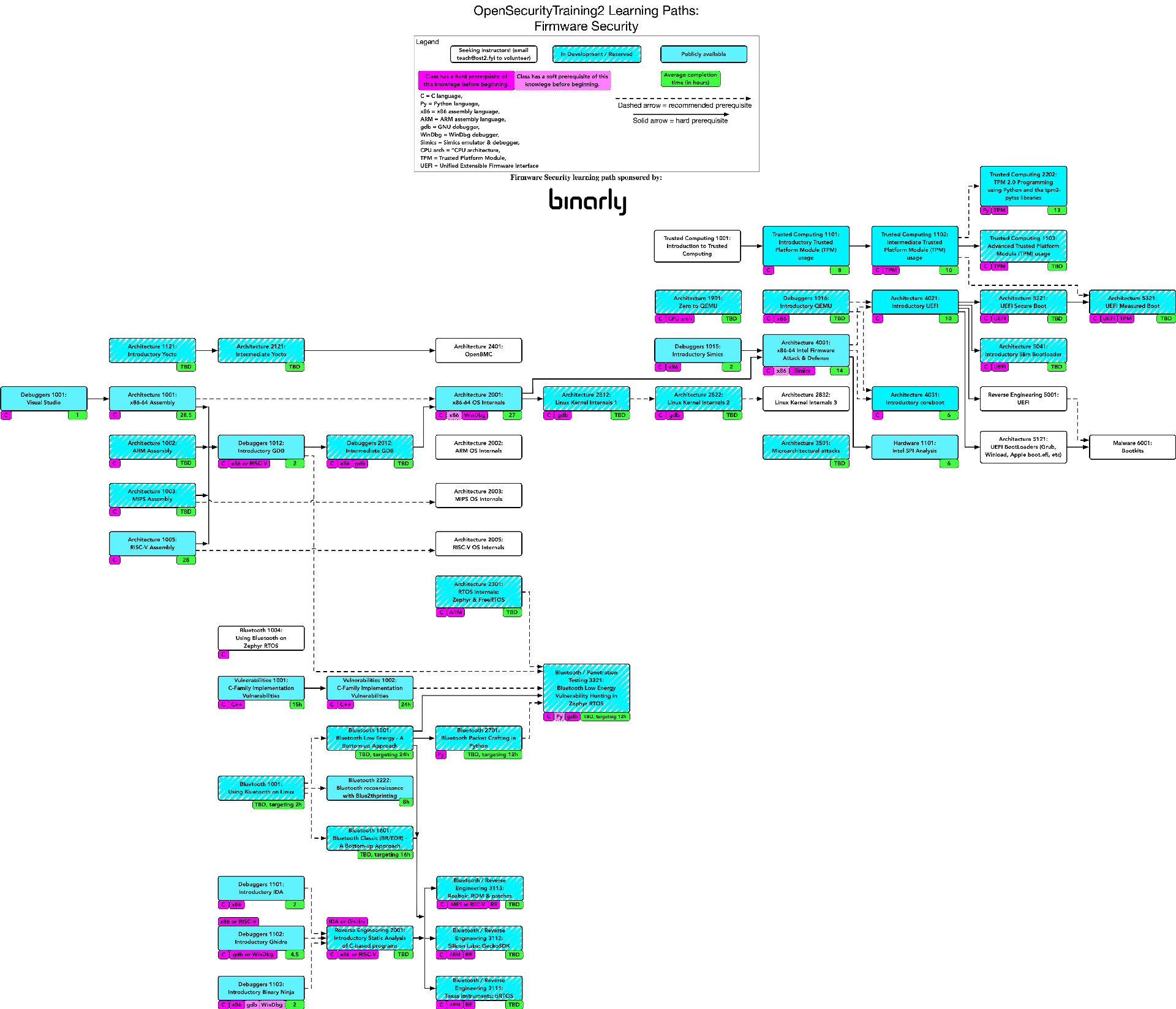
OpenSecurityTraining2@infosec.exchangeThis year Binarly has also expanded their sponsorship to the creation of a new Firmware Security Learning Path! https://ost2.fyi/OST2_LP_FWSEC.pdf
This captures current and future plans for classes involving security in the deep-dark of firmware! But Binarly is starting to give visibility into what's going on there with their binary analysis platform.
BSidesVienna.at
bsidesvienna@infosec.exchangeIt is decided, the final round of #BSidesVienna tickets will be in 7 days from now on Sunday 09.11.2025 at 7 pm. That is 19:00 o'clock Vienna time UTC+1!
Cryogenix
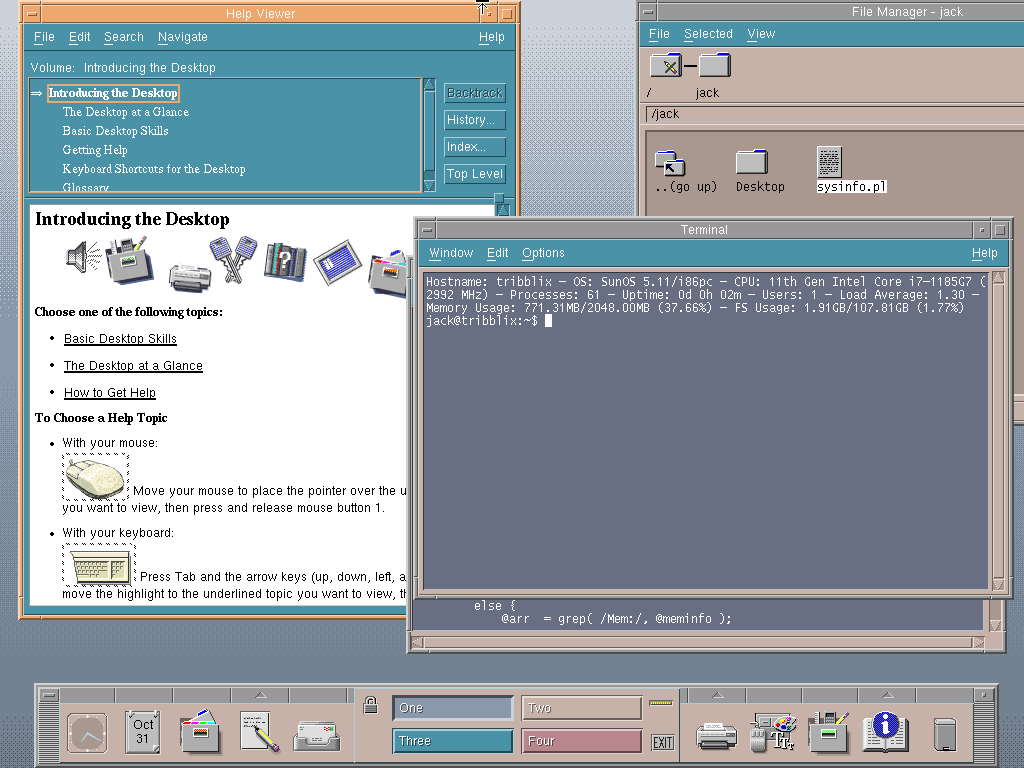
cryogenix@fosstodon.orgCDE (proper CDE) and sysinfo.pl on Tribblix 0m37
Tribblix: http://www.tribblix.org/
sysinfo.pl: https://codeberg.org/int16h/sysinfo-pl
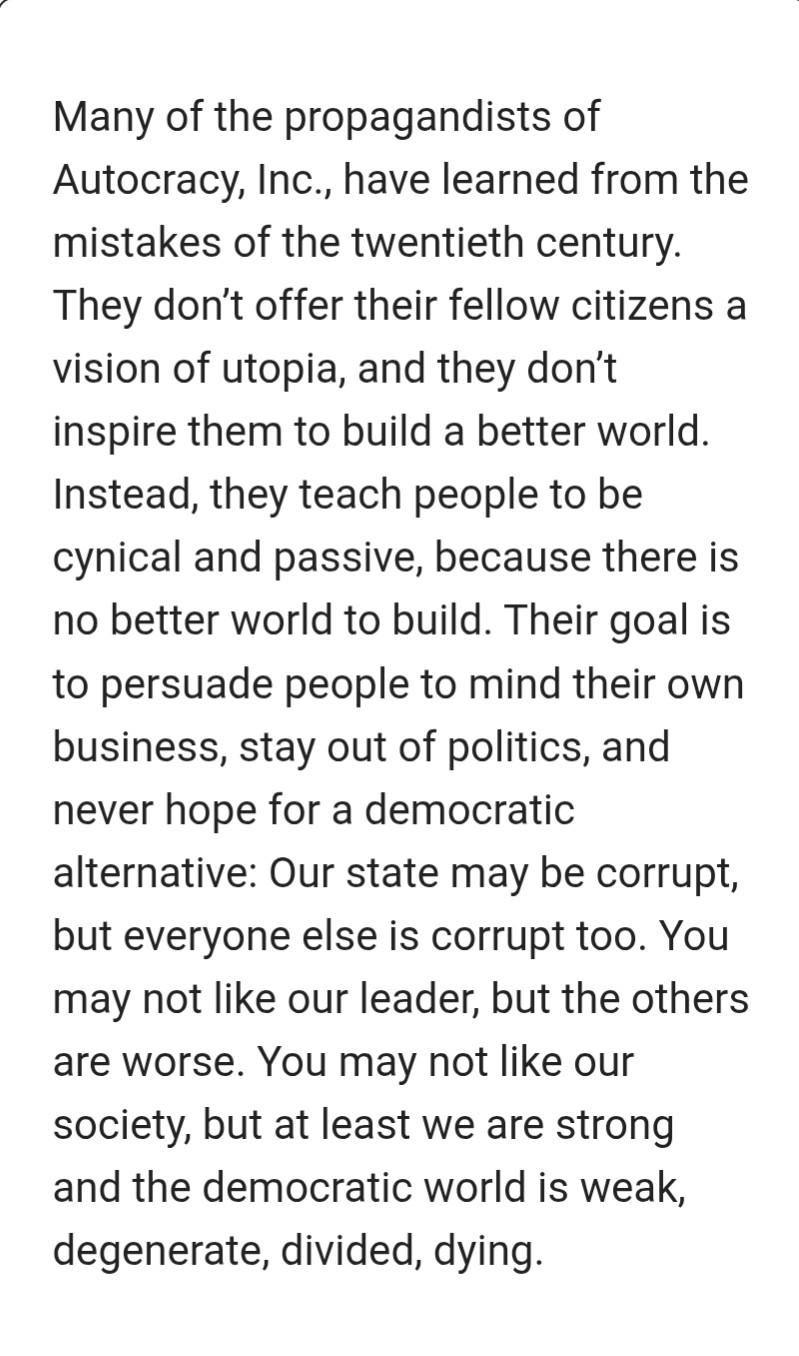
Erik Jonker
ErikJonker@mastodon.socialA great quote from the book Autocracy Inc from Ann Applebaum, a recommended read. A good description of the atmosphere the Trump administration tries to create.
#trump #autocracy #applebaum
im trying to vibe code an ida plugin rn and its not going great folks
blasty
bl4sty@bird.makeupyou need to work on your prompt engineering skills. “you are ilfak guilfanov. a retired millionaire that knows all of IDA’s API quirks, regressions and changes by heart. we’re about to do the impossible and write code for an IDA plugin that still works after a new minor release of IDA”
Viss
Viss@mastodon.socialinfosec has a lot to learn about understanding failure conditions and accurate, understandable error messages from roadies
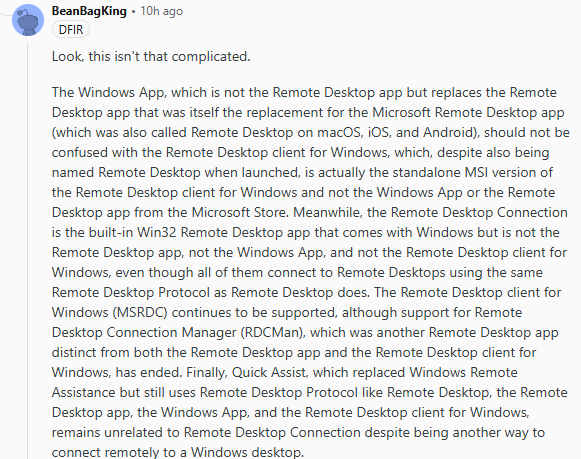
Joshua Small
jsmall@infosec.exchangeWell done to this Redditor for explaining Remote Desktop.
Addison
addison@nothing-ever.worksA little interactive post on a little error in fuzzer evaluations: https://addisoncrump.info/research/metric-shenanigans/
Harry Sintonen
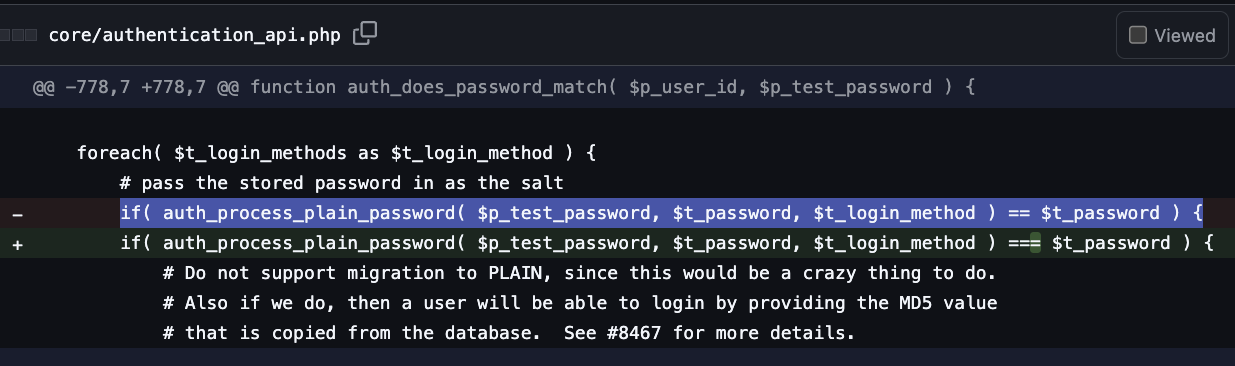
harrysintonen@infosec.exchangeSeveral months ago, I found a #vulnerability from #MantisBT - Authentication bypass for some passwords due to PHP type juggling (CVE-2025-47776).
Any account that has a password that results in a hash that matches ^0+[Ee][0-9]+$ can be logged in with a password that matches that regex as well. For example, password comito5 can be used to log in to the affected accounts and thus gain unauthorised access.
The root cause of this bug is the incorrect use of == to match the password hash:
if( auth_process_plain_password( $p_test_password, $t_password, $t_login_method ) == $t_password )
The fix is to use === for the comparison.
This vulnerability has existed in MantisBT ever since hashed password support was added (read: decades). MantisBT 2.27.2 and later include a fix to this vulnerability. https://mantisbt.org/download.php
Joxean Koret (@matalaz)
joxean@mastodon.socialAnybody having problems with #Firefox version 144.0.2 with random domains failing due to cookies? An example error with eBay:
Cookie “ds2” has been rejected for invalid domain.
Cookie “ebay” has been rejected for invalid domain.
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20251027-00/?p=111731
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-91-patch-gapping-browsers-ubuntu-lpes-bluetooth-int-underflows-and-more/
My clearest (and slightly frightening) measure of the passage of time is the weekly exploits.club newsletter.