Posts
2577Following
668Followers
1496buherator
buheratorLonghorn
never_released@mastodon.socialSomething quite interesting: https://fil-c.org/
tldr: CHERI guarantees (purecap only) on existing hardware
The catch is as always with purecap models is that you have a whole new ABI.
Interestingly pointers stay 8 bytes here, with the capability being invisible to the running program (but instead maintained invisibly by the runtime).
packagist
packagist@phpc.social🚨 Warning to PHP package maintainers: We did not email you to change your passwords & 2FA. Emails asking you to update your credentials are a phishing attempt. We had the phishing site & domain taken down. If you got the email and entered your credentials, please contact us. #phpc #composerphp
Tim Bray
timbray@cosocial.caThis is beautiful; pure poetry: https://obsidian.md/blog/less-is-safer/
(Obsidian’s dependency-management philosophy.)
I have a suggestion: If you have a project or repo that's getting popular, stop writing features for a few months and implement this instead.
evacide
evacide@hachyderm.ioThere is a lot of demand for digital privacy and security advice out there right now and lots of people are giving advice and writing guides. I beg them to do a few things:
1. Be explicit about the threat model your advice is meant for.
2. Do not give advice you haven't tried implementing yourself. Eat your own dog food.
3. Get feedback on your guide from your target audience before publication.
4. Incorporate that feedback. This is not an optional step.
Filippo Valsorda
filippo@abyssdomain.expert"Lack of scalability is enough for us to disqualify QKD outright: if a technology can’t bring security to the whole Internet, we’re not going to spend much time on it."
Quantum Key Distribution (as opposed to post-quantum cryptography) has a number of problems, but this succinctly captures the core issue.
blacktop
blacktop@mastodon.socialUpdated to also include a plugin/language extension for Ghidra 🐉 (in addition to the IDA Pro plugin)
buherator
buherator1) Locked iPhone Arbitrary Phone Call
https://szilak.com/2025-09-18-locked-iphone-arbitrary-number-call.html
2) Locked iPhone Saved Contact Confirmation
https://szilak.com/2025-09-18-locked-iphone-contact-brute-force.html
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@eupolicy.socialEarlier this year I presented on "Small is beautiful: microstacks or megadependencies", https://webdevcon.nl/session/small-is-beautiful-microstacks-or-megadependencies/ - in which I talk about the state of web development, cloud, and the fun of building self contained highly efficient solutions.
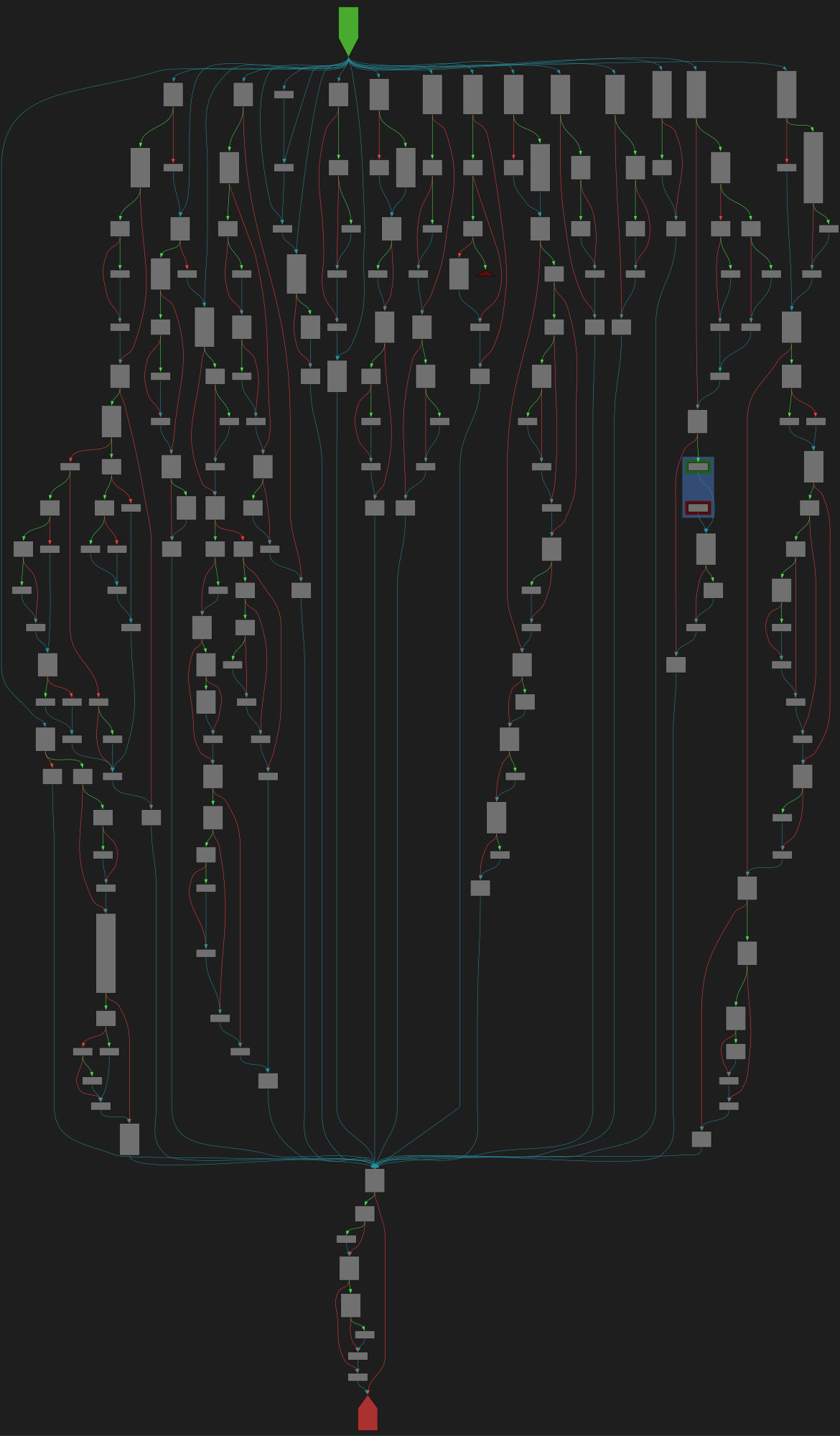
CFG Bot 🤖
cfgbot@mastodon.socialProject: facebook/react https://github.com/facebook/react
File: packages/react-reconciler/src/ReactFiberCommitWork.js:1981 https://github.com/facebook/react/blob/c250b7d980864be49facf2306f06455e7f9e305d/packages/react-reconciler/src/ReactFiberCommitWork.js#L1981
function commitMutationEffectsOnFiber( finishedWork: Fiber, root: FiberRoot, lanes: Lanes, )
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Ffacebook%2Freact%2Fblob%2Fc250b7d980864be49facf2306f06455e7f9e305d%2Fpackages%2Freact-reconciler%2Fsrc%2FReactFiberCommitWork.js%23L1981&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Ffacebook%2Freact%2Fblob%2Fc250b7d980864be49facf2306f06455e7f9e305d%2Fpackages%2Freact-reconciler%2Fsrc%2FReactFiberCommitWork.js%23L1981&colors=light
buherator
buheratorhttps://bughunters.google.com/blog/4684191115575296/project-rain-l1tf
"a detailed overview of the L1TF vulnerability, a CPU vulnerability on some Intel CPUs (Skylake and older)"
Phil M0OFX
philpem@digipres.clubGhidra: I SUPPORT 16-BIT SEGMENTED MODE
Also Ghidra: WHAT IS DS, ES, That's segment zero! Must be!
Seriously though. Does anyone know how to deal with 16-bit code in Ghidra?
#ReverseEngineering
buherator
buheratorhttps://hackaday.com/2025/09/18/worst-clock-ever-teaches-you-qr-codes/
Misty
misty@digipres.clubThe more and more old servers I see close, the more intolerable it is that Mastodon still doesn't offer a way to migrate data like posts to new accounts. A user's post history is valuable, and it's more valuable the older the account is. Users *should* have the option to migrate those to a new server!
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-86-ksmbd-0clicks-apple-ends-memory-corruption-mini-kernels-in-zig-and-more/
tmaher
tmaher@infosec.exchange@adamshostack where are you seeing reference to symmetric keys?
In the Technical Details section on Actor Tokens, it says “These hybrid setups used to provision a certificate credential on the Exchange Online Service Principal (SP) in the tenant, with which it can perform authentication.” . Adversary would then use the (x509) cert (and private key) to authN to eSTS (the Entra IdP), get one of these wacky “Actor Tokens” that AAD Graph doesn’t validate properly.
eSTS does support both x509 and client secrets for an SP to authN, but client secrets are just CSPRNG-generated passwords. They’re bearer tokens, not symmetric AES or RC4 keys.
I’d argue the causes were the ad-hoc “Actor Tokens” for impersonation (wrapping in an unsigned JWT: what the heck?), and that AAD Graph still hasn’t been shut down. It’s been deprecated since before I joined MS Identity in 2020, and has been a steady source of vulns
Violet
Violet@chitter.xyzOn the 26th of September I will also be streaming a birthday demoparty from London, I heavily encourage everyone to send entries!
chompie
chompie1337@haunted.computerkernel hackers go serverless
ring0 → cloud 9 ☁️ ??
brb pwning yr gpu nodes ✨
BrianKrebs
briankrebs@infosec.exchangeHoly moly. The DOJ just unveiled their charges against Jubair, alleging he was involved in 120 intrusions and extortion against 47 US entities. The complaint alleges victims paid at least $115 million in ransom payments. At a hearing today in the UK, it emerged that Jubair had access to $200 million in crypto, and Flowers $7M
buherator
buheratorhttps://bughunters.google.com/blog/6715529872080896/beyond-sandbox-domains-rendering-untrusted-web-content-with-safecontentframe