Posts
3368Following
712Followers
1580Micro SF/F by O. Westin
MicroSFF@mastodon.artHistory students are often disappointed when they learn why the AI take-over failed. They were defeated by human resistance, which was kept alive by libraries and old paper books, and a surprising machine ally.
Books had not been replaced, because even the mightiest AI could not make printers work.
Elinor Mills
elinor@infosec.exchangeFascinating article by @kimzetter about the 2013 Mandiant APT 1 report that revealed the identities of the Chinese PLA threat actors behind the attacks. Q&A with the main report's architect reveals behind-the-scenes details. It's a great read! https://www.zetter-zeroday.com/how-the-infamous-apt-1-report-exposing-chinas-pla-hackers-came-to-be/?ref=zero-day-newsletter
Andrey Konovalov
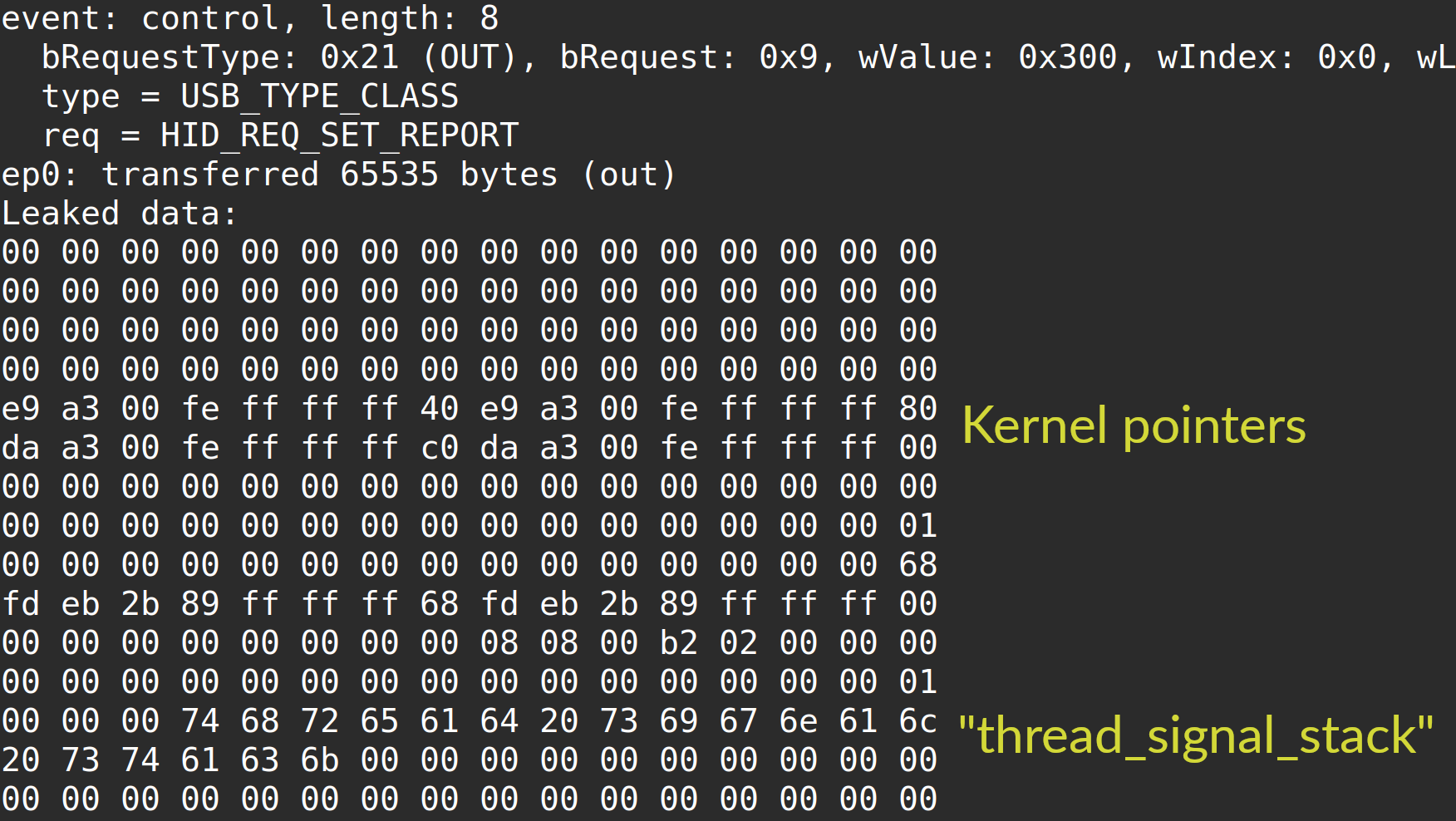
xairy@infosec.exchangeWrote a trigger for CVE-2025-38494/5 (an integer underflow in the HID subsystem) that leaks 64 KB of OOB memory over USB.
Still works on Pixels and Ubuntus (but the bug is fixed in stable kernels).
https://github.com/xairy/kernel-exploits/tree/master/CVE-2025-38494
buherator
buheratorCaitlin Condon
catc0n@infosec.exchange"this thing is super junk"
- Quote from the team exploit mines 2025-09-09T15:37:00Z
buherator
buheratorhttps://qriousec.github.io/post/oob-angle/
Phrack
phrack@haunted.computerProton enabled the two accounts of the authors again (after 3+ weeks and ignoring appeal and email to legal). The authors did not violate any ToS. No spam/malware was sent. No hacking. Just 6 emails to warn South Korea about a breach (not by them). Our reply and offer to Proton:
leonjza 
leonjza@infosec.exchange
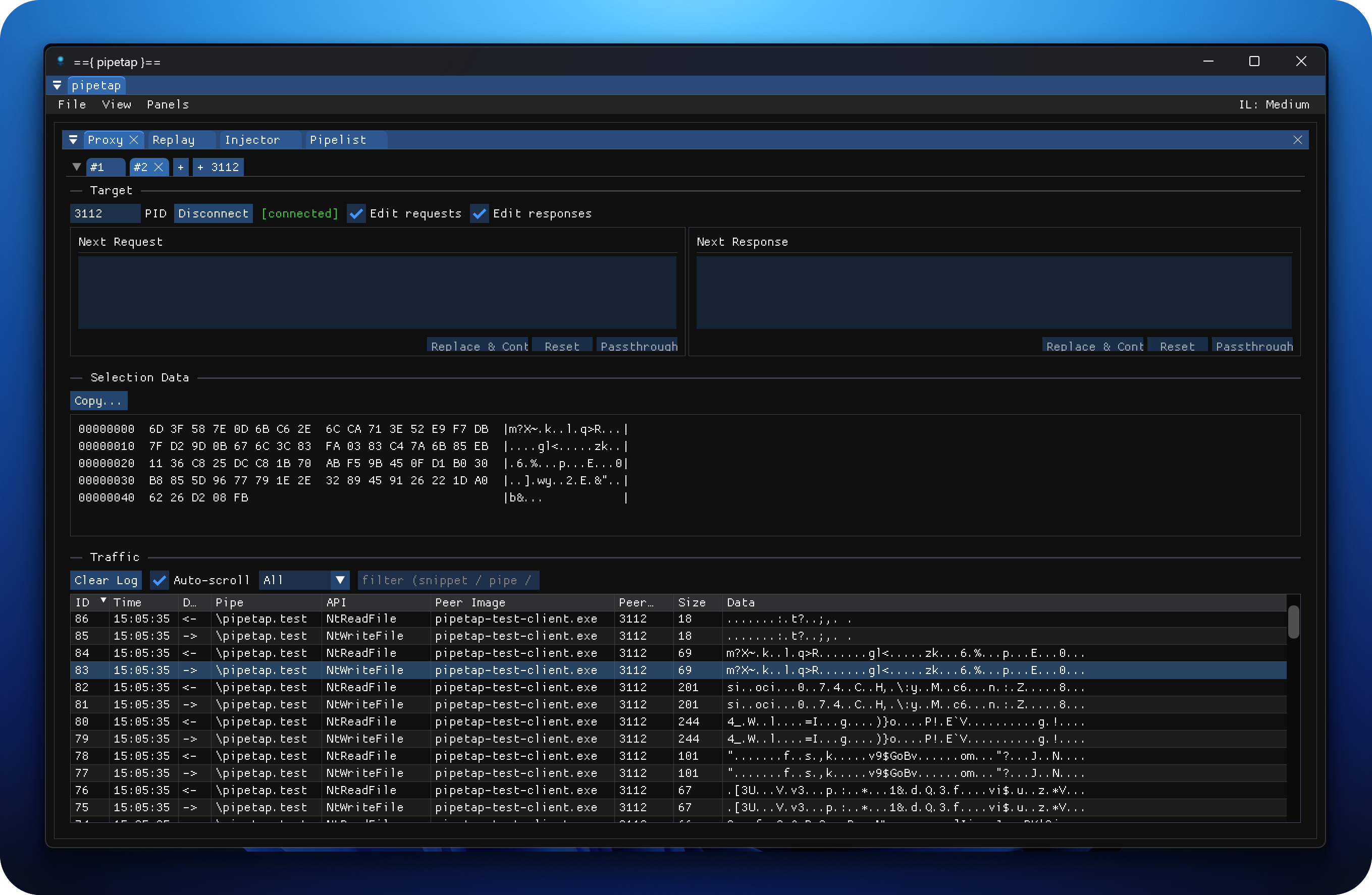
I've been hacking on a new Windows Named Pipe tool called PipeTap which helps analyse named pipe communications. Born out of necessity while doing some vulnerability research on a target, its been super useful in reversing it's fairly complex protocol. :)
Of course, I'm aware alternatives exist (and that really, using just a Frida hook you can get far), but I wanted something more versatile.
So far PipeTap can:
- Proxy reads/writes (even some async ones).
- Be a client, incl. the ability to have the *actual* connection in a remote process for those targets that do client pid validation.
- Proxy TCP <-> Named pipe for arbitrary Python clients.
- And more to come!
If you're at Cyber Saiyan / RomHack Conference, Training and Camp at the end of the month, come tell me your GitHub username and I'll give you early access to the @sensepost tool repo for PipeTap at the con! 🙃
Below is a demo of the proxy in action.
Zhuowei Zhang
zhuowei@notnow.devNeat: @streypaws posted a write up on CVE-2025-38352, the Linux kernel vulnerability exploited in the wild in the September Android Security Bulletin: https://x.com/streypaws/status/1965328009650733496
https://streypaws.github.io/posts/Race-Against-Time-in-the-Kernel-Clockwork/
allison
aparrish@friend.camp@KinkyKobolds this is the best explanation i've read for why anyone who is monetarily backed by the tech industry is feeling pressured to include generative models in everything https://gauthierroussilhe.com/en/articles/how-to-use-computing-power-faster
pancake 
pancake@infosec.exchange
Just pushed the last #webassembly build from git in the r2wasm test website. Testing, feedback and patches are welcome! Let’s make the web a solid foundation for r2 users too https://radareorg.github.io/r2wasm/index.html
buherator
buheratorhttps://curl.se/docs/CVE-2025-9086.html
Found via Google Big Sleep:
https://googleprojectzero.blogspot.com/2024/10/from-naptime-to-big-sleep.html
daniel:// stenberg://
bagder@mastodon.socialThere's going to be more speak about AIs finding genuine security problems soon.
Google Big Sleep found one in #curl that we reveal tomorrow.... in about eight hours. (but no, we don't know how much was AI and how much was human or how many false positives they had to wade through to get there etc maybe they will let us know later?)
Allison Husain
ezhes_@mastodon.onlineMemory Integrity Enforcement is the culmination of a truly incredible amount of work :)
While there's so much to love, one of my favorite pieces was getting to bring kalloc_type-style isolation to out-of-bounds accesses on both the architectural and speculative path. This lets us both mitigate a variety of Spectre v1 style attacks and break the reliable exploitation of some of the most powerful first-order memory corruption primitives (arb offset OOB R/W).
https://security.apple.com/blog/memory-integrity-enforcement/
Dino A. Dai Zovi
dinodaizovi@bird.makeupEvery minute that your security team is spending on things that aren't a risk is a minute that they *aren't* spending on things that *are* a risk.
rev.ng
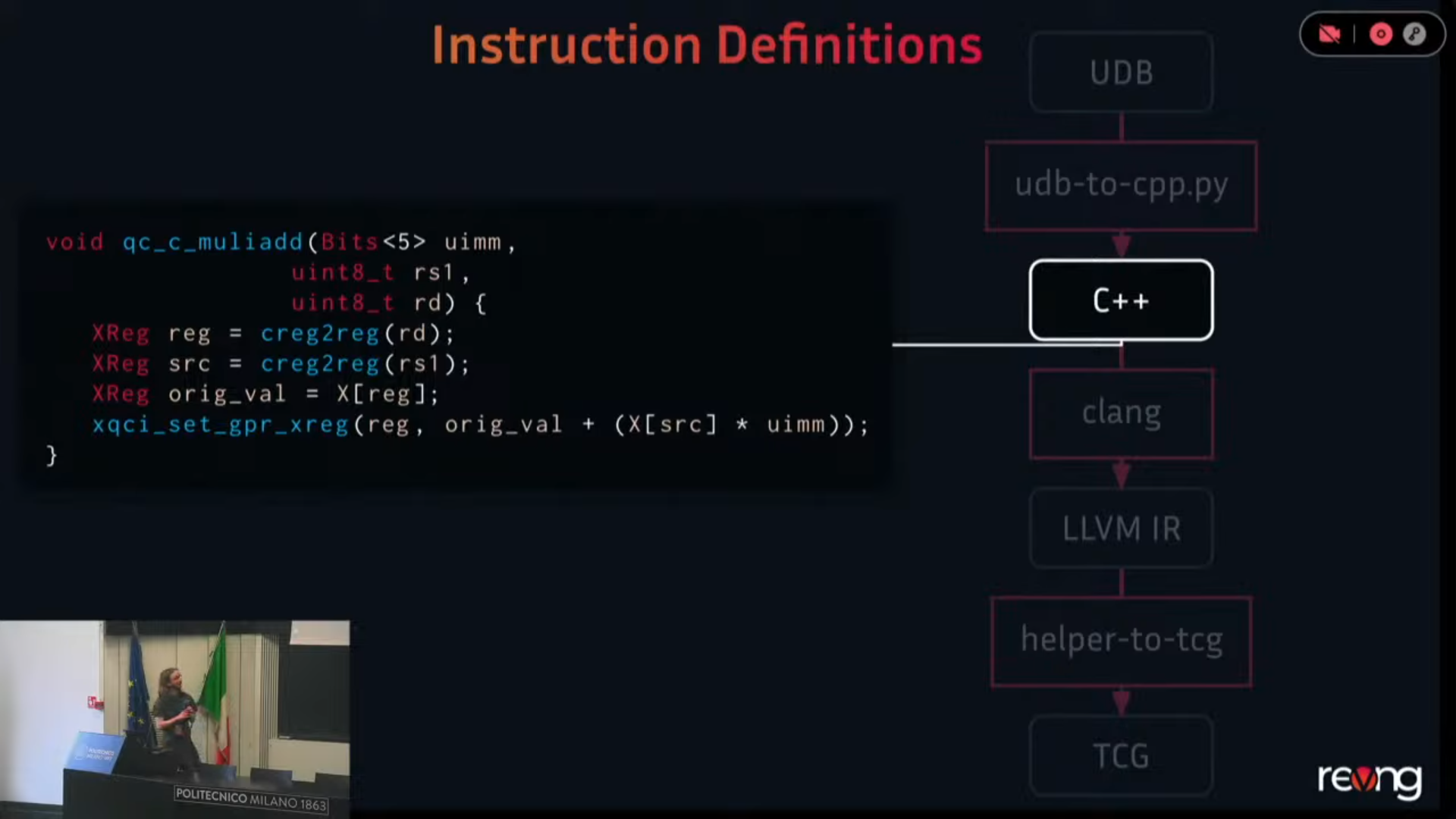
revng@infosec.exchange📢 Aaand here is Anton's talk about QEMU+RISC-V at KVM Forum 2025!
Automatic Frontend Generation for RISC-V Extensions
Video: https://www.youtube.com/watch?v=GPSKsZmu_S8&t=1297s (21:37)
Code: https://github.com/revng/udb-to-qemu/ 🦾
DebugPrivilege
debugprivilege@bird.makeupNew blog post of me analyzing a crash dump with the bugcheck 0x9F. Root cause was a power IRP timeout in RAS SSTP during a device removal. The post walks PnP locks, the stuck IRP, and more, including my thought process. Check it out here: https://medium.com/@Debugger/power-irp-timeout-in-ras-sstp-causes-blue-screen-0x9f-during-sleep-e59cb76f291c
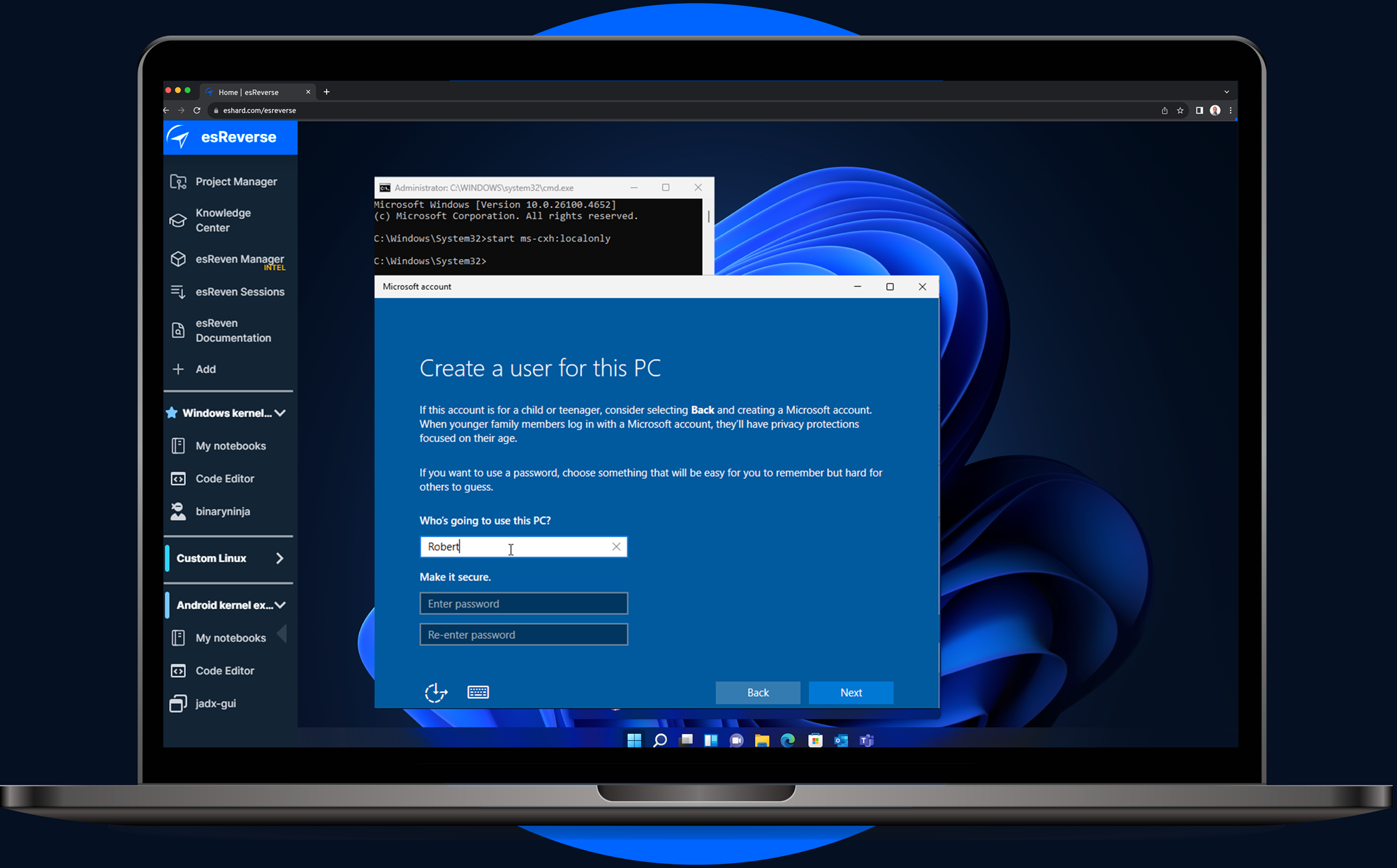
eShard
eshard@infosec.exchangeWindows 11 in esReverse. 💻 Full system emulation to boot, record, and rewind your analysis from kernel to userland.
Read the guide: https://eshard.com/posts/windows11-esreverse-emulation #windows #emulation #reverseengineering
p0pcycle
pamoutaf@infosec.exchange@Blackhoodie_RE X @hexacon_fr happening again! This time it’s my turn to give back 🥹
Use the registration link below to sign up to 4 days of free training given by Sonia, @naehrdine and myself !