Posts
2471Following
660Followers
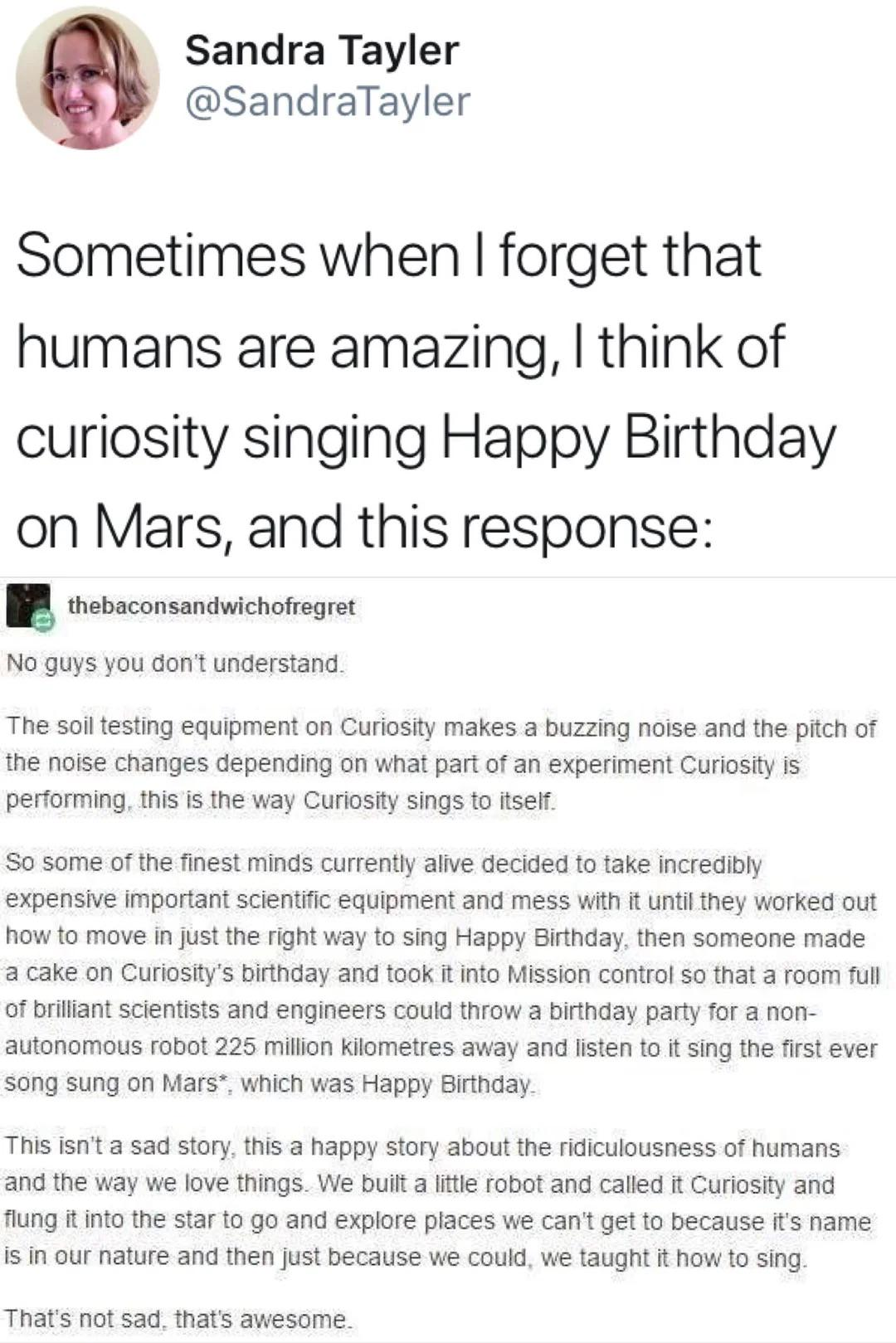
1482Peter Kröner
sir_pepe@mastodon.social🤯🚨 BREAKING NEWS 🚨🤯
In a shocking development, new additions to the #ECMAScript standard WILL UNLEASH THE HERETOFORE UNAVAILABLE POWER OF ADDITION _IN JAVASCRIPT_ upon the world!
👉 https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/Math/sumPrecise
Only works in Firefox ATM. Like, Chrome and Safari can't even add numbers currently.
Paolo Amoroso
amoroso@oldbytes.spaceEerie Linux posted an extensive introduction to using CP/M that assumes no previous knowledge of early operating systems. They also link to other posts they wrote on the evolution of CP/M.
https://eerielinux.wordpress.com/2025/08/28/a-gentle-introduction-to-cp-m
/r/netsec
_r_netsec@infosec.exchangeKsmbd Fuzzing Improvements and Vulnerability Discovery https://blog.doyensec.com/2025/09/02/ksmbd-2.html
buherator
buheratorhttps://u1f383.github.io/linux/2025/09/02/linux-io-port-access-checks-on-x86_64.html
Viss
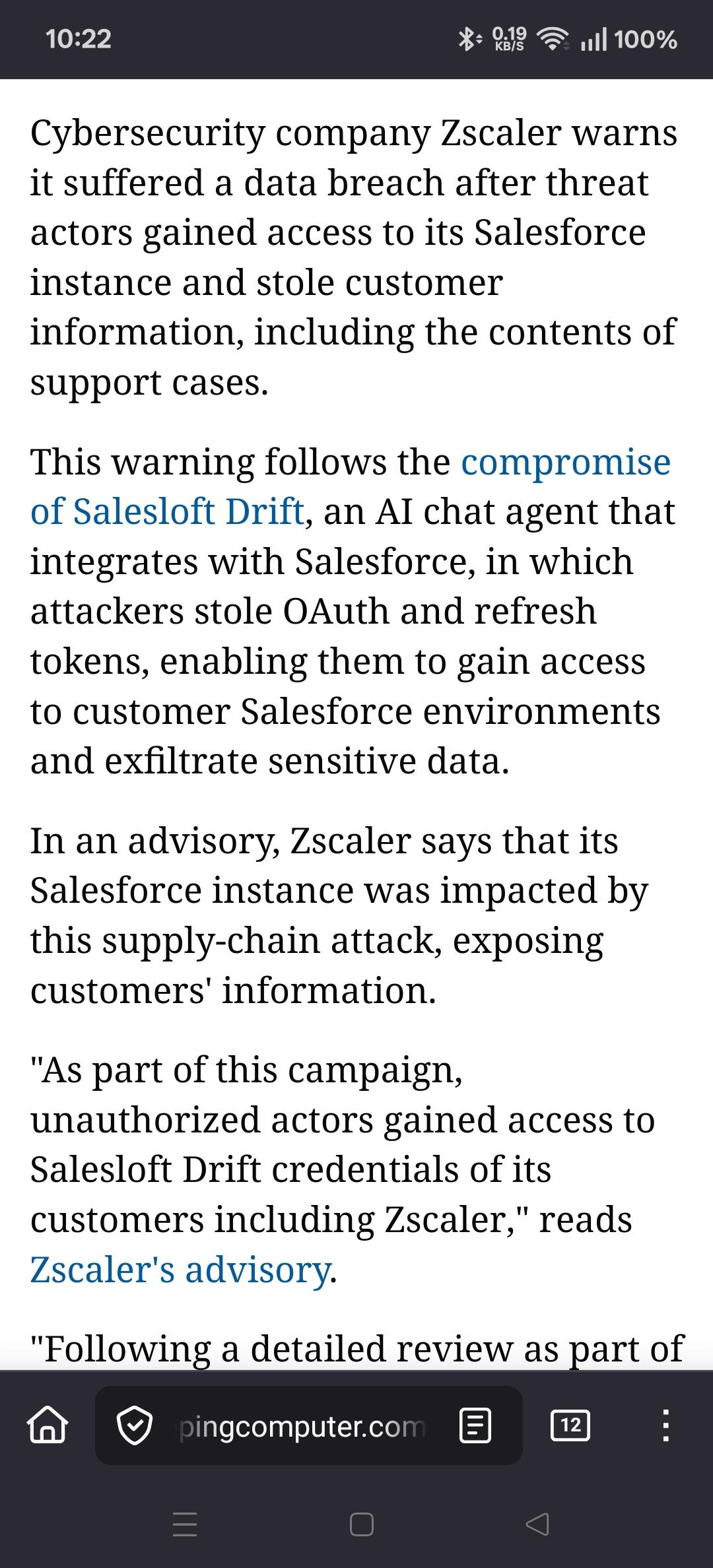
Viss@mastodon.socialgo to the cloud they said
it'll be fine they said
https://www.bleepingcomputer.com/news/security/zscaler-data-breach-exposes-customer-info-after-salesloft-drift-compromise/
buherator
buheratorhttps://en.wikipedia.org/wiki/Wired_Equivalent_Privacy
buherator
buheratorlintile
lintile@hackers.townYour #DFIU category today is OG HACKER SHIRTS
This Ron Rivest 1987 cipher, illegal to export from the US (mathematical munitions), fit on 3 lines of Perl and adorned t-shirts as a form of civil disobedience before becoming the WEP protocol's greatest weakness
buherator
buherator"import org.springframework...."
*drop and run*
Tropical Storm Jerry🌀
jerry@infosec.exchangeYes, there’s another phishing campaign contacting fediverse users to fill out a form to avoid being suspended or whatever. Stay calm and just report them and be sure to check the option to inform their home instance so the account gets suspended for everyone.
Also, please consider enabling moderated signups if you don’t already have them. I get it - signups dropped by >90% when I did it, but there’s very little capability for dealing with bad actors proactively once they have an account. I know it’s not a foolproof way to keep the scammers out, but it is an improvement.
buherator
buheratorhttps://u1f383.github.io/linux/2025/09/01/starlabs-summer-pwnables-linux-kernel-challenge-writeup.html
"Just fucking use HTML"- https://justfuckingusehtml.com/
Just a tiny bit offensive. 🤏
rev.ng
_revng@bird.makeup🔥 So, at DEF CON there was a talk about deobfuscation: VMDragonSlayer by @van1sh_bsidesit.
The author released the code and there's clearly huge amounts of AI slop.🤖
Now, WE WENT TO THE TALK and spoke with the speaker after the talk. 🧵
https://bird.makeup/users/dodo_sec/statuses/1960547263605772738
buherator
buheratorTo be fair I also hear marketing crying over constent requirements, which is good, but overall the adtech industry is still thriving while user experience deteriorated. In other words the regulation doesn't have the intended effect, while causing negative externalities, making things worse. (Please don't tell me it should be adtech that should play nicely, while the regulation is there because they don't play nicely in the first place)
buherator
buheratorhttps://blog.amberwolf.com/blog/2025/august/advisory---netskope-client-for-windows---local-privilege-escalation-via-rogue-server/