Posts
2471Following
660Followers
1482Marco Ivaldi
raptor@infosec.exchangeEntertaining and inspiring #pwn2own #xdev writeup 👏 (also from a few months back)
#Lorex 2K Indoor Wi-Fi Security Camera: RCE #Exploit Chain
buherator
buheratorhttps://hackaday.com/2025/08/29/this-week-in-security-def-con-nonsense-vibepwned-and-0-days/
by Hackaday
Don't forget: this Friday, September 5th, is a #BandcampFriday and a #FairTradeMusicFriday!
https://IsItBandcampFriday.com
https://IsItFairTradeMusicFri.day
buherator
buheratorhttps://lukasmaar.github.io/slides/ndss25-kernelsnitch.pdf
buherator
buheratorRE: https://mstdn.io/@wolf480pl/115113655884602210
buherator
buheratorChris Herdt
cherdt@infosec.exchangeI think people often forget (or maybe never knew) that the CVSS scores provided by the NIST NVD are base scores and can be modified by organizations to better reflect their own situation.
For example, take a vulnerability that with a network attack vector and high impact to availability. Base score could be 9.3 (critical). But in your environment, let's say that system is not open to the Internet and would require access from an adjacent system. That could drop it to an 8.5 (high).
It's not a perfect system, but I think a lot of people start and end at the base scores.
Elizabeth Zagroba
ez@chaos.socialDo the “unfashionable” thing: use pen and paper. https://medium.com/@rehmanmomin/the-unfashionable-art-of-actually-learning-things-0cc7359dbb88
Clément Labro
itm4n@infosec.exchange🆕 PrivescCheck important change!
I killed PrivescCheck.ps1, well..., sort of...
Starting from now, the file is no longer available in the repository. Instead, it is now provided as a release file (more information in the README).
As you may already know, the file "PrivescCheck.ps1" is generated using a custom build script. This allows me to separate the code into multiple files and then gather and compress everything into a single one.
For a while now, I've been manually executing this script every time I wanted to push new features. This was nonsensical. So, I finally took the time to implement an automated workflow on GitHub so that release files are created automatically. Hopefully, this will save me some time in the long run. Also, it will serve as the base for an important feature I plan to implement. 😉
The Register
theregister@geeknews.chatPentagon ends Microsoft's use of China-based support staff for DoD cloud
'It blows my mind,' says SecDef The Pentagon has formally kiboshed Microsoft's use of China-based employees to support Azure cloud services deployed by US government agencies, and it's demanding Microsoft do more of its own digging to determine whether any sensitive data was compromised. …
#theregister #IT
https://go.theregister.com/feed/www.theregister.com/2025/08/29/pentagon_ends_microsofts_use_of/
buherator
buheratorhttps://www.reddit.com/r/netsec/comments/1n394gs/elastic_edr_0day_part_2_technical_details_and_the/
 radare
radare 
radareorg@infosec.exchange
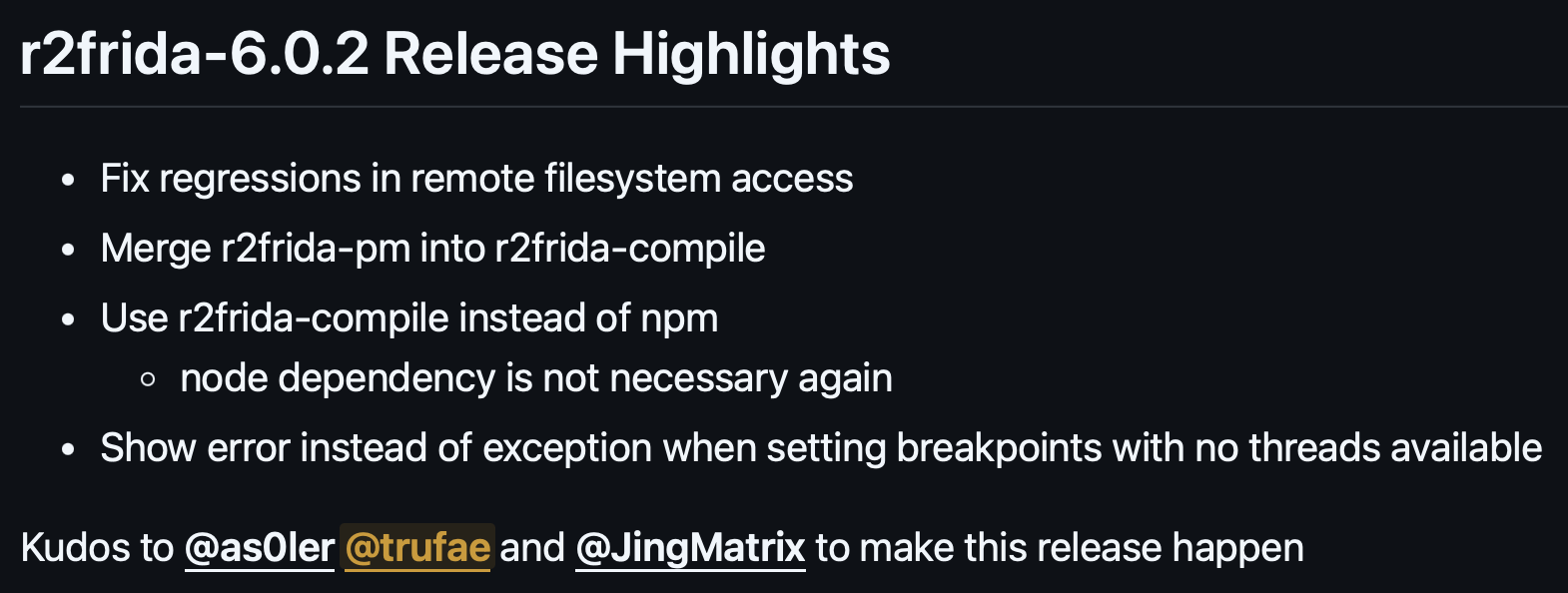
r2frida-6.0.2 is out! Shipping small fixes for breakpoints and remote filesystem access and removing the build dependency with NodeJS https://github.com/nowsecure/r2frida/releases/tag/6.0.2