Posts
3368Following
712Followers
1580buherator
buheratorhttps://www.reuters.com/sustainability/boards-policy-regulation/meta-wont-tweak-pay-or-consent-model-further-despite-risk-eu-fines-sources-say-2025-07-11/
IMO pay-or-consent is a reasonable model for #adtech, but if Meta implements that *and* pays fines, that's good enough for me!
Attack and Defense
attackanddefense@infosec.exchangeWe just updated our bug bounty hall of fame to include the great security researchers from the last two quarters. Thank you for securing the best #Firefox yet :)
https://www.mozilla.org/en-US/security/bug-bounty/hall-of-fame/
alexandra
xandra@tilde.zonein the interest of helping other small publications, i want to pass along a request for elpis zine, an online zine about the small web, retro tech, and alternate protocols that recently celebrated its 10th issue!
for their next issue, they want to focus on #women of the #internet: "who, one way or another, influenced the creation of the modern Internet, which is why the modern World Wide Web looks exactly like this."
from elpis:
These are women who are at the forefront of the attack and work on the technologies that surround us. These are women who have influenced design, content, and politics. But we're not just talking about the modern Internet, we're also talking about the small web.
There are legendary women here, too. We want to write about you, about your sites, if you have ideas about whom we can also write about, or links to pages (feel free to give your sites), that's cool! We'll publish them.
the editors are looking specifically for "ideas about who can be written about from the great women who influenced the modern Internet (designers, programmers, and so on)." there's so many women in internet #history that we must keep their stories going! <3
the editor of the zine, turboblack, is a 32-bit cafe member and a passionate member of the independent web. :) i hope you appreciate this departure to spread some internet-focused publication love!
Sam Thomas
xorpse.ghost.sh@bsky.brid.gyI'm pleased to announce a new version of the Rust bindings for IDA Pro! With:
- Improved strings, metadata, and core APIs.
- Support for the names API.
Thank you to @raptor.infosec.exchange.ap.brid.gy & Willi Ballenthin for contributing!
Docs: idalib.rs
Code: git.idalib.rs
idalib documentation
CFG Bot 🤖
cfgbot@mastodon.socialProject: kubernetes/kubernetes https://github.com/kubernetes/kubernetes
File: staging/src/k8s.io/api/certificates/v1/generated.pb.go:1378 https://github.com/kubernetes/kubernetes/blob/a62752db5110225a89a83ec844a5884413e550ff/staging/src/k8s.io/api/certificates/v1/generated.pb.go#L1378
func (m *CertificateSigningRequestSpec) Unmarshal(dAtA []byte) error
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fkubernetes%2Fkubernetes%2Fblob%2Fa62752db5110225a89a83ec844a5884413e550ff%2Fstaging%2Fsrc%2Fk8s.io%2Fapi%2Fcertificates%2Fv1%2Fgenerated.pb.go%23L1378&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fkubernetes%2Fkubernetes%2Fblob%2Fa62752db5110225a89a83ec844a5884413e550ff%2Fstaging%2Fsrc%2Fk8s.io%2Fapi%2Fcertificates%2Fv1%2Fgenerated.pb.go%23L1378&colors=light
buherator
buheratorscott f
scott@carfree.citylocal restaurants I love you but please have a website that isn't your instagram profile and has your hours of business on it. kthx
buherator
buheratorbuherator
buheratorhttps://www.lrqa.com/en/cyber-labs/remote-code-execution-in-broadcom-altiris-irm/
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.6 beta2 vs. iOS 18.6 beta3 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_6_22G5064d__vs_18_6_22G5073b/README.md
Sass, David
sassdawe@infosec.exchangeWHAT IS THIS SOURCERY?!
#Winget has #DSC support now?!
I can start #WindowsSandbox and have the required security tools installed #automagically!
https://github.com/microsoft/winget-dsc/tree/main/samples/DscResources/Microsoft.WindowsSandbox.DSC
There’s an entire rant buried in here but, in short, I absolutely agree.
buherator
buheratorhttps://karmainsecurity.com/KIS-2025-04
buherator
buheratorBtw. this is the talk&slides by @ifsecure :
https://www.youtube.com/watch?v=U1kc7fcF5Ao
https://docs.google.com/presentation/d/1pAosPlKUw4uI5lfg7FVheTZAtI5mUy8iDeE4znprV34/edit
OpenSecurityTraining2
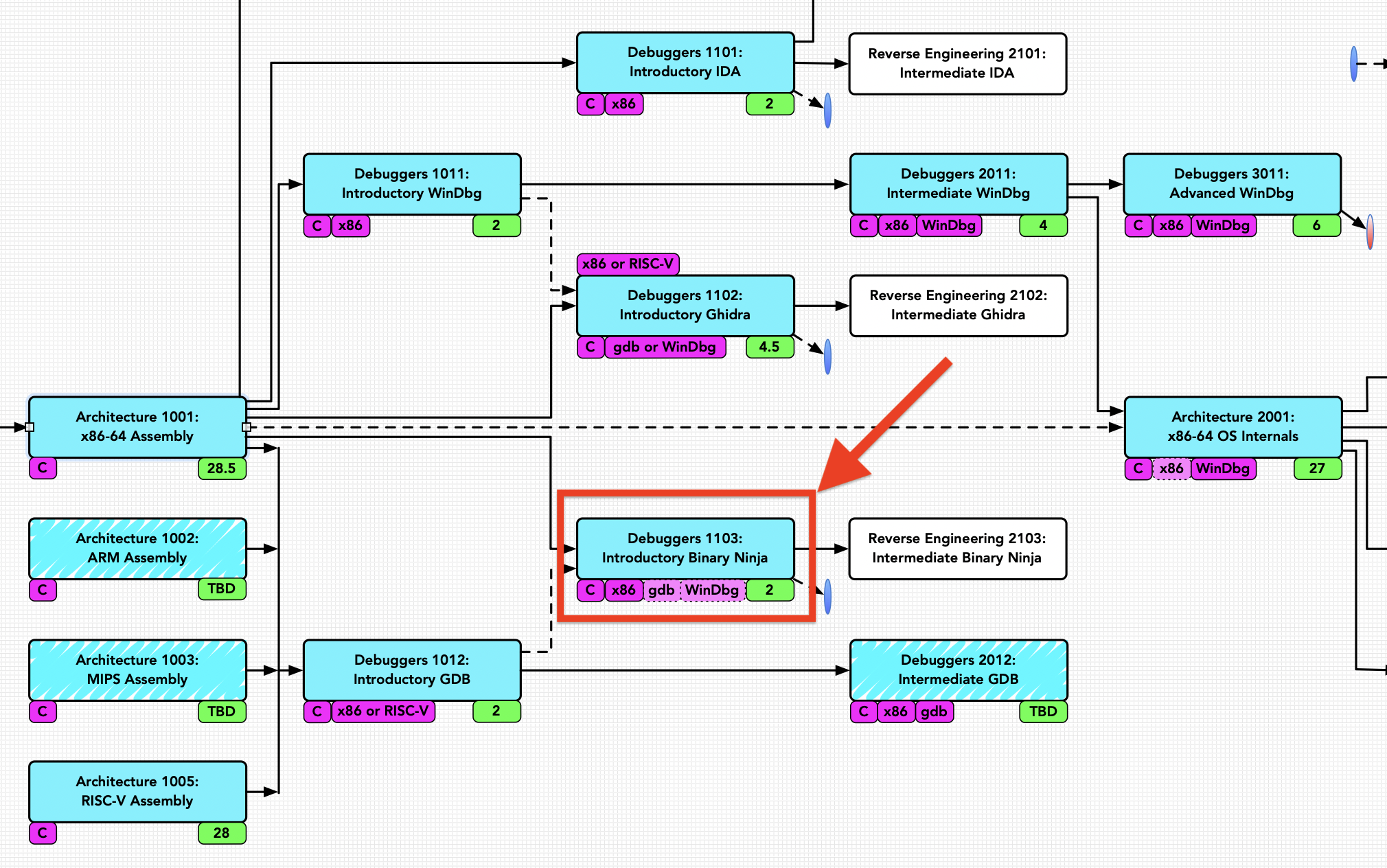
OpenSecurityTraining2@infosec.exchange📣"Debuggers 1103: Introductory Binary Ninja" is released!📣
https://ost2.fyi/Dbg1103
This class by Xusheng Li of Vector 35 @binaryninja provides students with a hands-on introduction to the free version of Binja as a debugger, thus providing decompilation support!
Like all current #OST2 classes, the core content is made fully public, and you only need to register if you want to post to the discussion board or track your class progress. This mini-class takes approximately 2 hours to complete, and can be used as standalone cross-training for people who know other reverse engineering tools, or by students learning assembly for the first time in the https://ost2.fyi/Arch1001 x86-64 Assembly class.
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/07/11/2
CVE-2025-7424 CVE-2025-7425
#OSS #FOSS