Posts
3368Following
712Followers
1580buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/07/11/2
CVE-2025-7424 CVE-2025-7425
#OSS #FOSS
buherator
buherator- CVE-2025-1735 SQLi via pgsql (related to CVE-2025-1094)
https://github.com/php/php-src/security/advisories/GHSA-hrwm-9436-5mv3
- CVE-2025-1220 SSRF via fsockopen()
https://github.com/php/php-src/security/advisories/GHSA-3cr5-j632-f35r
- CVE-2025-6491 NULL deref in SOAP handling
https://github.com/php/php-src/security/advisories/GHSA-453j-q27h-5p8x
Valerie Aurora 🇺🇦
vaurora@mstdn.socialWant to influence the rules for vulnerability handling for every internet-connected product sold in the EU? Of course you do!
You are invited to the vulnerability handling deep dive session for the Cyber Resilience Act. July 22, online, free registration:
https://www.stan4cra.eu/event-details/deep-dive-session-vulnerability-handling
More info: https://www.stan4cra.eu/resources
/r/netsec
_r_netsec@infosec.exchangeRevisiting automating MS-RPC vulnerability research and making the tool open source https://www.incendium.rocks/posts/Revisiting-MS-RPC-Vulnerability-Research-automation/
buherator
buherator/index.xml
/feed.xml
#syndication
No-AI and solid end-to-end encryption is the new tech hype.
If you don't invest heavily in solid end-to-end encryption, privacy-protective and No-AI features, you will be left behind. People might even laugh at you.
Tell everyone.
buherator
buheratorhttps://swarm.ptsecurity.com/buried-in-the-log-exploiting-a-20-years-old-ntfs-vulnerability/
I think I missed this one about CVE-2025-49689
raptor 
raptor@infosec.exchange
[CVE-2025-38001] #Exploiting All Google #kernelCTF Instances And Debian 12 With A #0Day For $82k: A RBTree Family Drama (Part One: LTS & COS)
DocAtCDI
DocAtCDI@mastodon.socialMy office computer just crashed and now all the other computers have slowed down so they can see whats happening.
daniel:// stenberg://
bagder@mastodon.socialSource of some unbearably loud snoring
algernon@come-from.mad-scientist.clubI just released #iocaine version 2.5.0, probably the last 2.x version, as I'm starting to lay out the roadmap for 3.0.
Apart from a couple of handy new features to aid in bot detection and data collection, there's an important fix in it too: previously, the built-in templates did not escape the generated text properly, which could lead to all kinds of weirdness. Now they do.
The templates also have access to a new filter - urlencode -, which helps escaping random text generated to be used as URLs.
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@eupolicy.socialEurope appears to just have given up on doing anything technical. Perhaps we should hurry up & stop pretending we want to do anything ourselves, so we can speed up getting to our eventual destiny of a full time holiday destination for American, Chinese and Russian tourists. And mind you, that is the _best_ outcome I can see right now. https://therecord.media/spain-awards-contracts-huawei-intelligence-agency-wiretaps
eprint
eprint@ioc.exchange#eprint Replication of Quantum Factorisation Records with an 8-bit Home Computer, an Abacus, and a Dog by Peter Gutmann, Stephan Neuhaus (https://ia.cr/2025/1237)
chiefpie
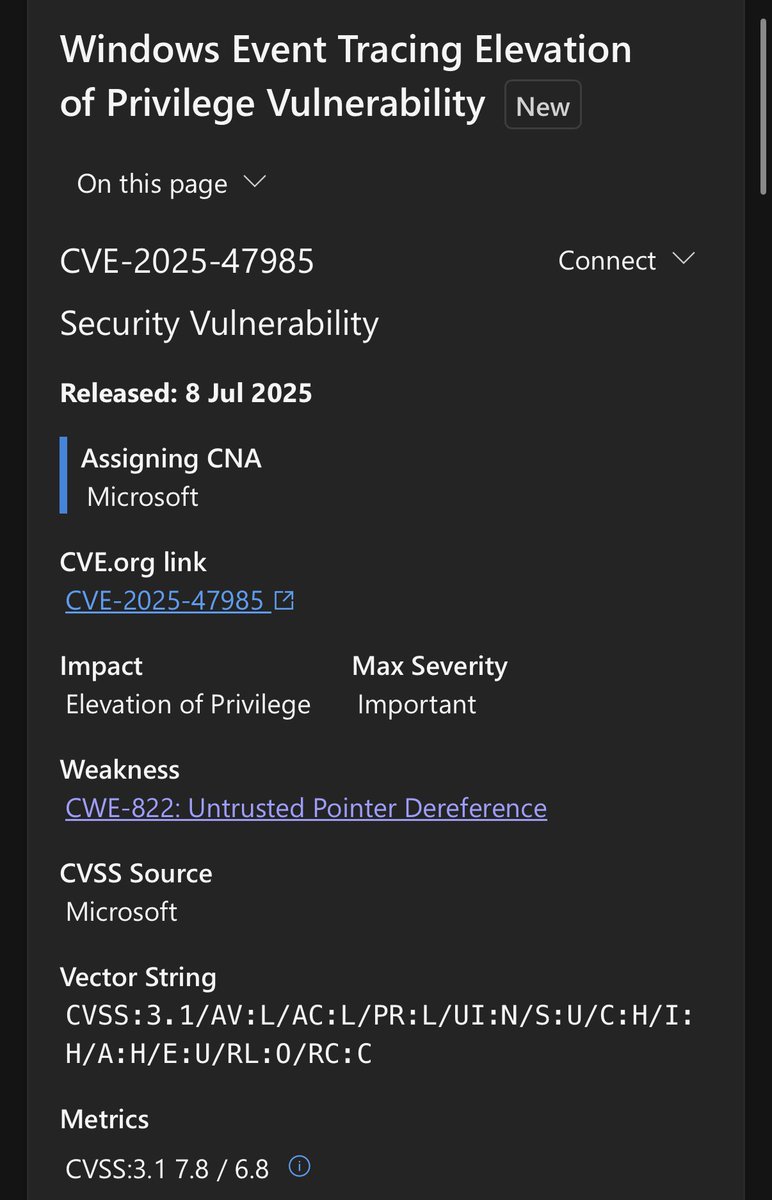
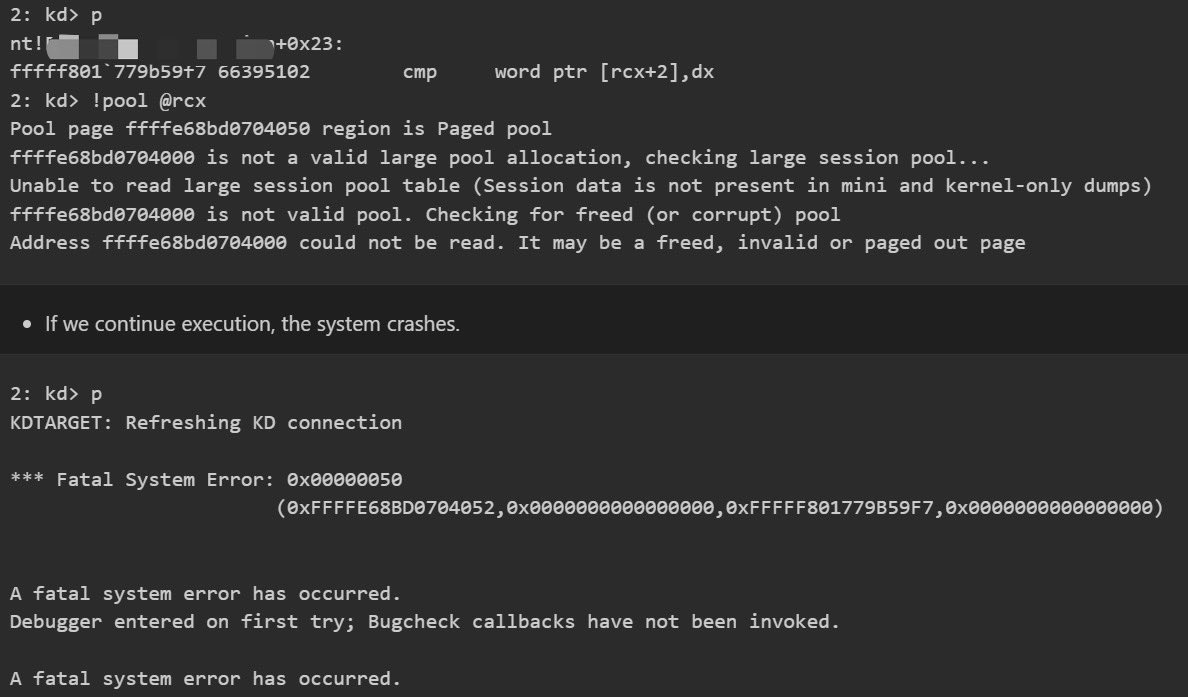
cplearns2h4ck@bird.makeupSome of my bugs in Windows Kernel ETW have been fixed by MSRC this month.
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-47985
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49660
These bugs are triggered from NTOS syscall.
Source of some unbearably loud snoring
algernon@come-from.mad-scientist.clubGetting started with iocaine is now online.
From nothing to running iocaine + Caddy with ai.robots.txt's robots.json and a few metrics as a starting point.
Contains #Roto, #Lua, and #Fennel - and a few tests too, for each.
Greg Linares (Laughing Mantis)
laughing_mantis@bird.makeupTruly humbled to share I had the honor of being a guest on the legendary @darknetdiaries. We talked about some wild stories, the epic screw ups, and others adventures. Really grateful for the chance to tell a few tales and hope it resonates with some
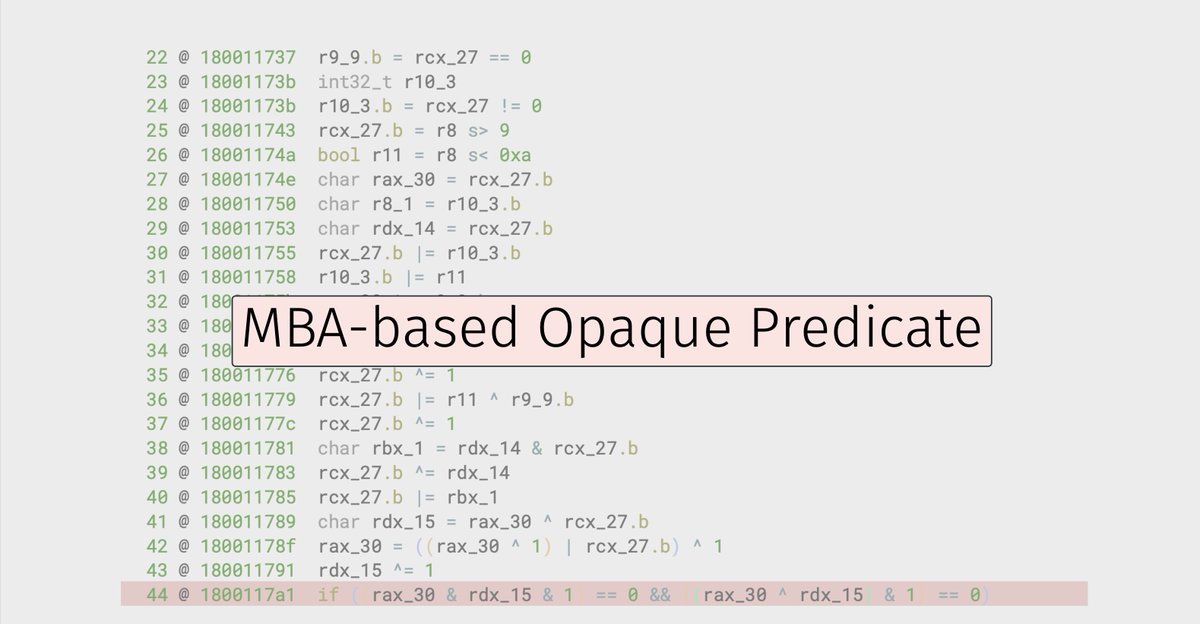
Tim Blazytko
mr_phrazer@bird.makeupThe slides from our @reconmtl talk, "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" (CC @nicolodev), are now online!
Slides: https://synthesis.to/presentations/recon25_mba_obfuscation.pdf
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting Git repos of the week:
Detection:
* https://github.com/telekom-security/tpotce - have some honey
Exploitation:
* https://github.com/tlsfuzzer/tlsfuzzer - fuzz TLS
* https://github.com/ShawnDEvans/smbmap - map SMB shares
* https://github.com/nccgroup/fuzzowski - another nice fuzzer
Data:
* https://github.com/sneakers-the-rat/gpu-free-ai - the AI implementation you don't want to use!
Again with the showing Bill how wrong he was when he said memory interference flaws were just theoretical.
https://www.securityweek.com/rowhammer-attack-demonstrated-against-nvidia-gpu/