Posts
2962Following
697Followers
1542Claudius Link
realn2s@infosec.exchangeJust read an article from an #ai influencer musing on the Innovative power of AI.
(Edit 2: while linked articles a current / May 2025 they refer to an event in 2017 🤪 )
Tasked with breaking the Enigma code, an AI system trained to recognise German using Grimm’s fairytales, utilizing 2,000 virtual servers, cracked a coded message in 13 minutes.
Let's pause for a second to let it sink.
And let's think for a second
Alan Turing “Bombes” could decipher two messages every minute.
😱 Suddenly the AI result isn't all that impressive any more.
AI cuts out all the research, knowledge gain, and insight. With all the resources available today, it still performs worse than a solution from 70 years ago (to be precise 26 times).
And this is seen as an impressive innovation 🤡🤯
"Sources":
Influencer post https://mastodon.social/@Caramba1/114470245795906227
Guardian article
https://www.theguardian.com/science/2025/may/07/todays-ai-can-crack-second-world-war-enigma-code-in-short-order-experts-say
Alex Plaskett
alexjplaskett@bird.makeupBiting the CHERI bullet: Blockers, Enablers and Security Implications of CHERI in Defence
Trend Zero Day Initiative
thezdi@bird.makeupAn analysis of CVE-2024-44236 - an RCE in macOS due to the lack of proper validation of “lutAToBType” and “lutBToAType” tag types. Read the details, see the source code review, and get detection guidance at https://www.zerodayinitiative.com/blog/2025/5/7/cve-2024-44236-remote-code-execution-vulnerability-in-apple-macos
blacktop
blacktop@mastodon.socialGet your macOS 15.4 xnu CodeQL database here! 👩🔬
Also NOW includin the compile_commands.json 🎉
(I also wrote a util for converting the paths github.com/blacktop/ccpaths)
`ccpaths JSON /Users/runner/work/darwin-xnu-build/darwin-xnu-build /path/to/your/xnu`
https://github.com/blacktop/darwin-xnu-build/releases/tag/v15.4
bdash
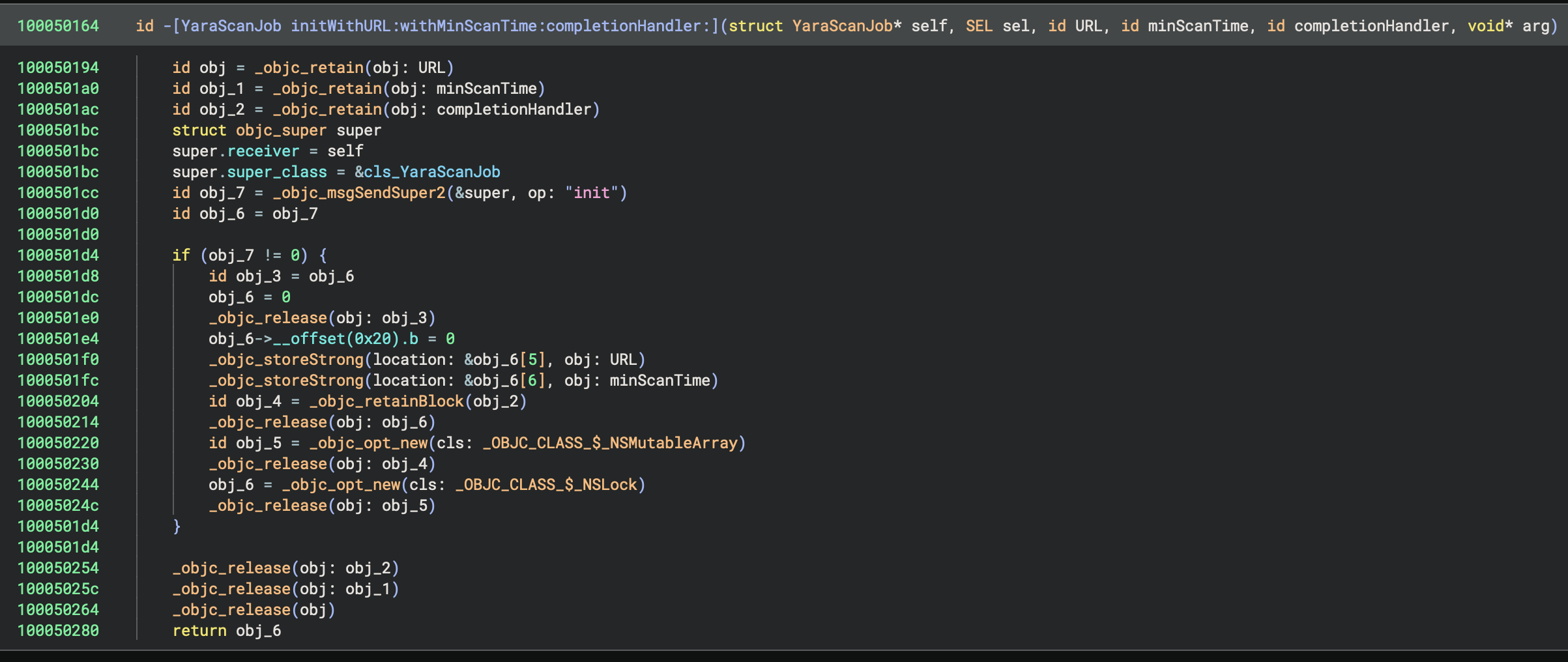
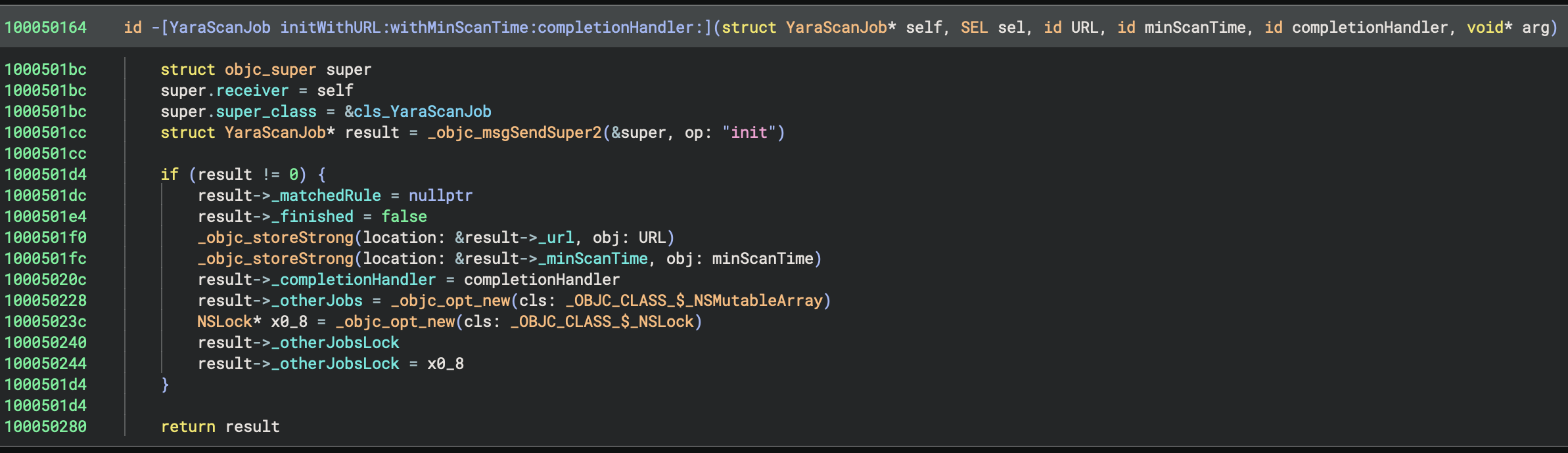
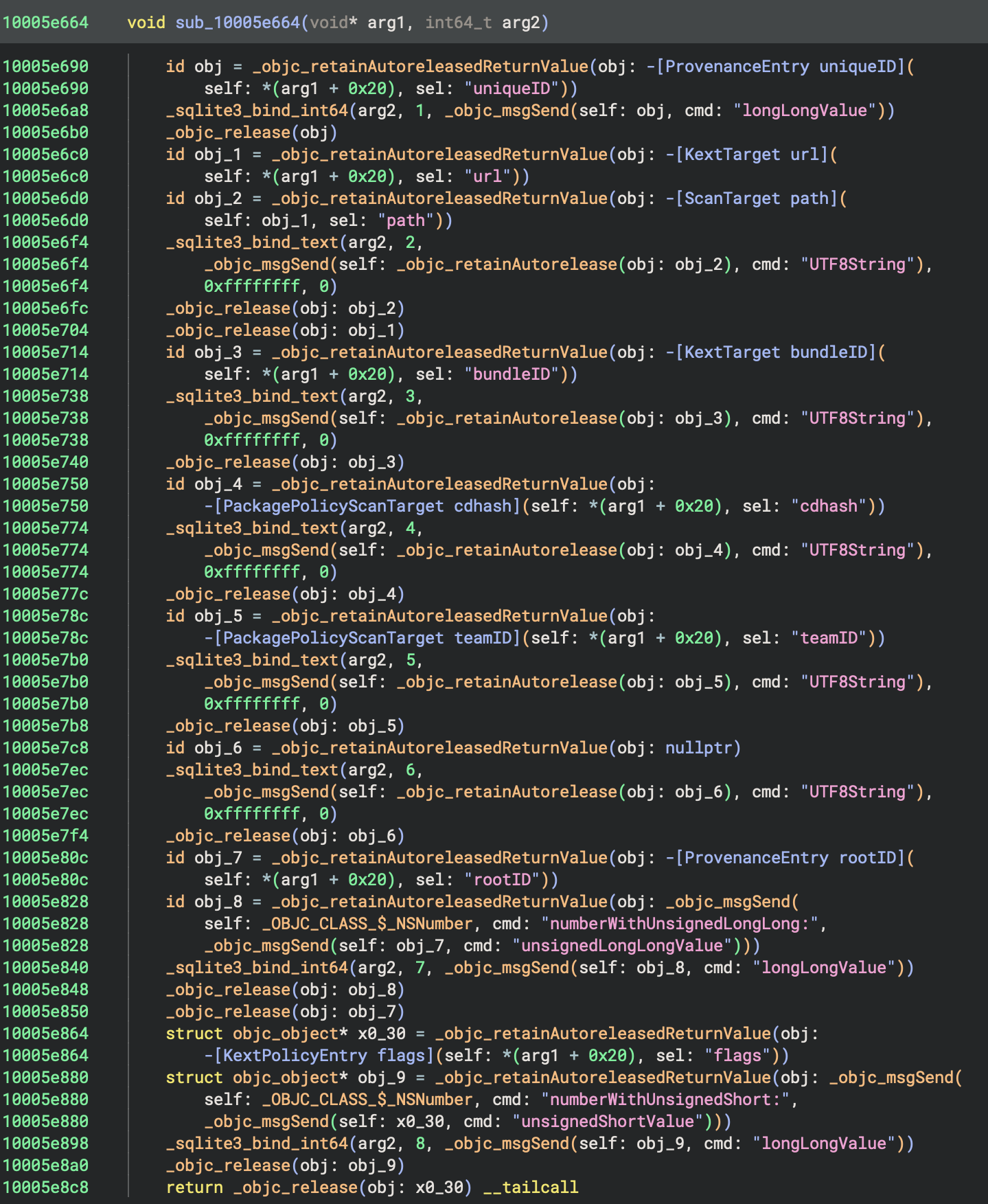
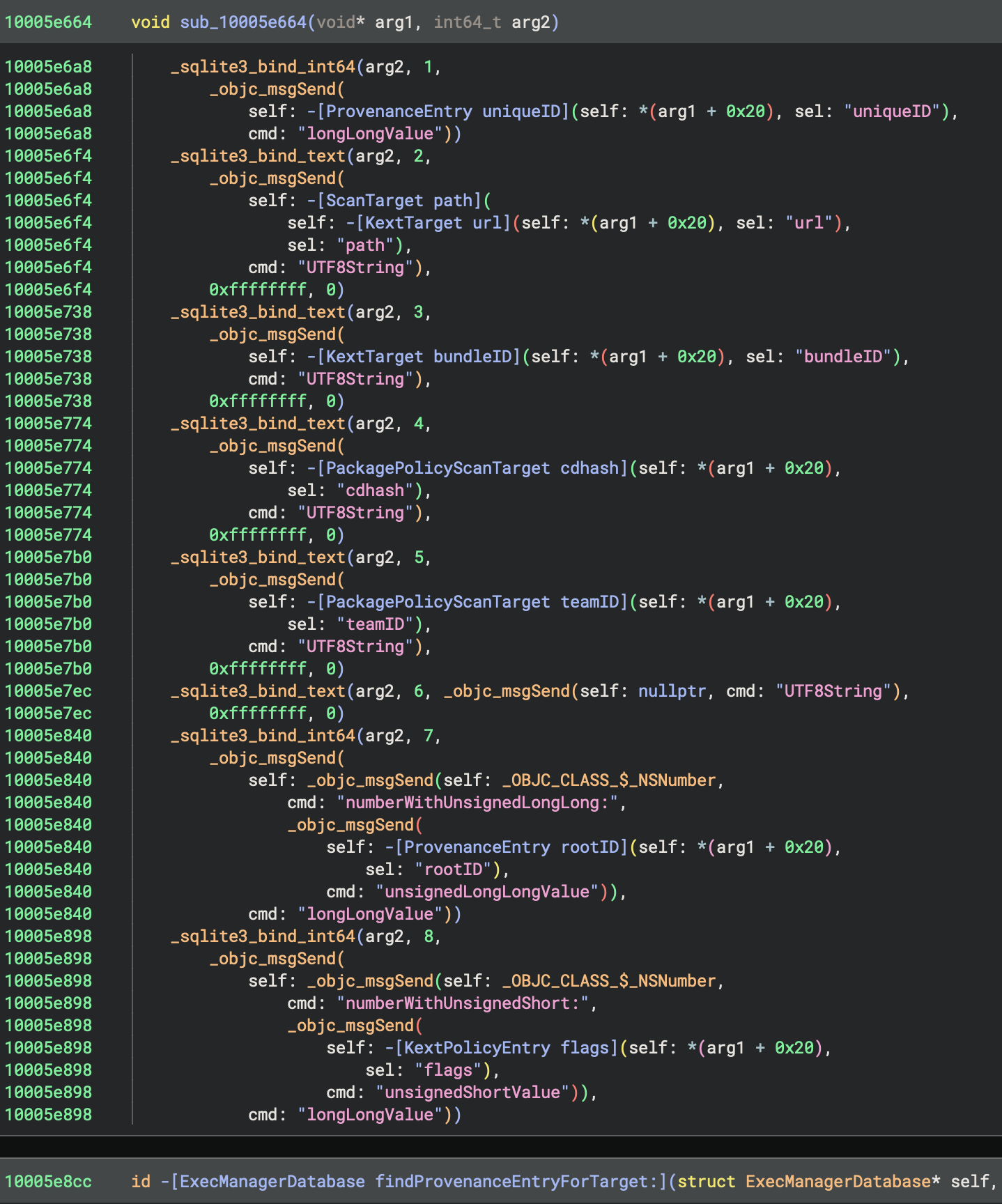
mrowe@bdash.net.nzI've been experimenting with improving Binary Ninja's analysis of Objective-C code recently. Having the ability to hide Obj-C runtime reference counting calls, and apply type information based on [super init] and objc_alloc_init calls can dramatically improve the readability (and in some cases even accuracy!) of the decompiled code.
real tournament when unreal tournament walks in 💽 --> 39c3
domi@donotsta.re
Slashdot 
slashdot@mastodon.cloud
VMware Perpetual License Holders Receive Cease-And-Desist Letters From Broadcom https://yro.slashdot.org/story/25/05/07/1856255/vmware-perpetual-license-holders-receive-cease-and-desist-letters-from-broadcom?utm_source=rss1.0mainlinkanon
buherator
buheratoralexandra
xandra@tilde.zoneonly FOUR DAYS left in our spring tea party coding event!
help create a template, theme, or layout for new and seasoned website owners to create their own websites easily!
submissions close may 11!~
#webdev #smallweb #indieweb #codejam #web #webdesign #handmadeweb #coding #codingisart #html #css #internet #neocities #nekoweb #website #personalwebsite #openinternet #foss #opensource
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeFor context: just three days ago CrowdStrike said it delivered "record full year operating cash flow of $1.38 billion and record full year free cash flow of $1.07 billion."
And CEO George Kurtz made $46 million last year.
https://aflcio.org/paywatch/CRWD & https://ir.crowdstrike.com/news-releases/news-release-details/crowdstrike-reports-fourth-quarter-and-fiscal-year-2025
Dmytro Oleksiuk
d_olex@mastodon.socialI’m sorry, but Facebook did more harm to humankind than all NSO-alike spyware vendors of the world altogether. You are fighting into the wrong direction
buherator
buheratorCindʎ Xiao 🍉
cxiao@infosec.exchangeNext Thursday, May 15 at @NorthSec in Montreal, I will be hosting the workshop "Reconstructing Rust Types: A Practical Guide for Reverse Engineers"! This will be a 3-hour workshop how to approach Rust types and data structures when reversing Rust binaries. See https://nsec.io/session/2025-reconstructing-rust-types-a-practical-guide-for-reverse-engineers.html for more details!
Workshops at NorthSec will be streamed on YouTube Live. My workshop is scheduled for 1300-1600 EDT (UTC-4) on Thursday, May 15 in the Workshop 2 track, in Salle de la Commune. The stream link for all the Thursday Salle de la Commune workshops is here: https://www.youtube.com/watch?v=UwJgS32Q6As&list=PLuUtcRxSUZUrW9scJZqhbiuTBwZBJ-Qic&index=7
Looking forward to seeing folks there! 🦀
(Edited since I can't count days of the week apparently: May 15, which is when my workshop is occurring, is a Thursday, not a Wednesday.)
#rustlang #ReverseEngineering #MalwareAnalysis #NorthSec #infosec #reversing
buherator
buheratorbuherator
buheratorhttps://therecord.media/jury-orders-nso-to-pay-meta-168-million-over-whatsapp-hack
buherator
buheratorhttps://lore.kernel.org/all/bb0a1948-d418-4720-97bf-4aceb30ea787@intel.com/t/#u
Guess I'll just run the fuzzer on the host then?
buherator
buheratorhttps://www.ibm.com/support/pages/node/7232750?myns=swgother&mynp=OCSWG60&mynp=OCSSC5L9&mynp=OCSSKWKM&mynp=OCSSTS2D&mynp=OCSSB23CE&mynp=OCSS9QQS&mync=A&cm_sp=swgother-_-OCSWG60-OCSSC5L9-OCSSKWKM-OCSSTS2D-OCSSB23CE-OCSS9QQS-_-A
The Zen and Art of Obfuscating Vulnerability Information (CWE-295?!)