Posts
2964Following
697Followers
1542buherator
buheratorhttps://labs.watchtowr.com/sysowned-your-friendly-rce-support-ticket/
buherator
buheratorhttps://medium.com/@cy1337/tracing-data-flow-with-pcode-f879278d9fc1
/r/netsec
_r_netsec@infosec.exchangeKnown Exploited Vulnerabilities Intel https://kevintel.com
abadidea
0xabad1dea@infosec.exchangeIt turns out that MrDeepFakes' sudden voluntary shutdown a few days ago was because Bellingcat was on their tail. https://www.bellingcat.com/news/2025/05/07/canadian-pharmacist-linked-to-worlds-most-notorious-deepfake-porn-site/
CONTENT WARNING: this article is a dox on someone credibly accused of running a nonconsensual porn site
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgEveryone agrees something needs to be done about our total dependence on US clouds. But what? And who should do it? Ample words have been written on the 'why', and we also have a lot of text on our values and that *someone* should do *something*. Here I elaborate on an earlier suggestion with a coherent strategy that is concrete enough to disagree with. This reads well with the latest Euro-Stack letter also: https://berthub.eu/articles/posts/a-coherent-non-us-cloud-strategy/
hanno
hanno@mastodon.socialThis is a gruelling summary of all the things wrong with OpenSSL https://www.haproxy.com/blog/state-of-ssl-stacks I've mostly watched this whole thing from the sidelines, but was also affected noting that private key parsing suddenly became 70 times slower. I think they've now improved it to "only" be 10-20 times slower, and there does not seem any effort to work on it any more.
Marco Ivaldi
raptor@infosec.exchange
Fabrice Roux 

fabrice@infosec.exchange
@wdormann Schrödinger patching is when you can’t rely on the software or its dlls version numbers to know if the cat is alive.
In order to know if the cat is alive you JUST need to check the hex values of 67 binaries.
Are some versions of their software certified ? I’ve seen this lousy behavior in some certified apps. They paid to get 3.14.116 certified and they don’t plan on paying again so when they move their code base from C to Rust you stay on the « same version » you have 3.14.116-c and 3.14.116-rust. (Extreme made up example). 😬
Mr. Bitterness
wdormann@infosec.exchangeOh, wow.
Only after pestering the Commvault PSIRT did they update the language of their advisory.
While it still incorrectly says that 11.38.0 - 11.38.19 are affected and that 11.38.20 is resolved (it is not), the've added a section below this misinformation to convey the actual state of the world:
11.38.20 is only patched if it has the SP38-CU20-433 and SP38-CU20-436 additional updates installed.
And 11.38.25 is only patched if it has the SP38-CU25-434 and SP38-CU25-438 additional updates installed.
I cannot think of a behavior that is more vindictive to their customers to botch language in an advisory so bad, and also to not bother bumping release versions for the fixes for a CVSS 10 EITW vulnerability. 🤦♂️
Mr. Bitterness
wdormann@infosec.exchangeI'll admit that even with the updated explicit instructions on how to get Commvault updates, I fail to see how one can get these mythical SP38-CU25-434 and SP38-CU25-438 optional updates.
When I first go to "Download or copy software", Commvault tells me that I'm Up-to-date
If I manually force a download of Latest Fixes for Current Release: 11.38.25, I get an installer that specifies:
[Image Information]
Version=11.80.380.0
ServicePack=38
SPTranID=6988515
UnixTime=1732240991
RevisionNumber=1352
Tip=1
ReducedMedia=1
And if I run this installer and even reboot for good measure, the system is still vulnerable. And the jar that contains the vulnerable code, cv-ac-common.jar has not changed from my original 11.38.25 vulnerable system.
I'm not particularly good with computers, so hopefully Commvault sysadmins in the real world are better at this than I am. But I'll admit that even with explicit instructions, I have no idea how to get the updates that protect me against CVE-2025-34028.🤷♂️
Andrey Konovalov
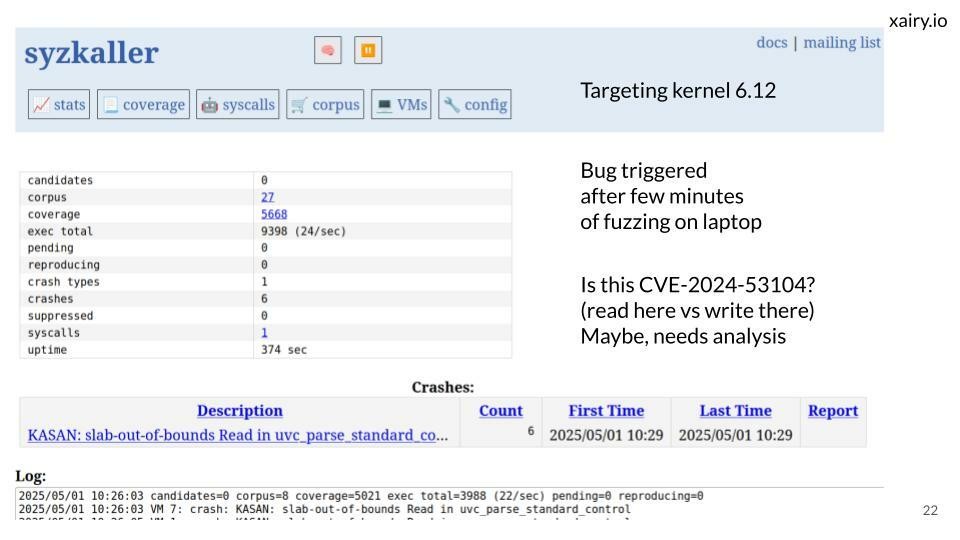
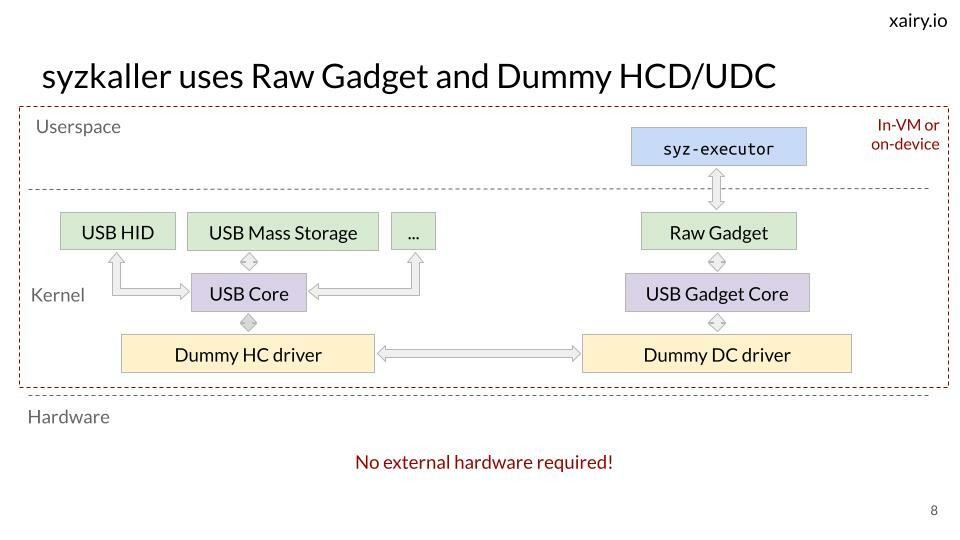
xairy@infosec.exchangeGave a talk on external fuzzing of Linux kernel USB drivers with syzkaller at SAFACon.
Includes a demonstration of how to rediscover CVE-2024-53104, an out-of-bounds bug in the USB Video Class driver.
Slides: https://docs.google.com/presentation/d/1NulLxRowsHzgcL1AFzNF_w8nh3zk2BKKPfGi_1j76A8/edit?usp=sharing
(If you use newer Ubuntu and the code formatting looks off, use File → Print preview; @ubuntu still hasn't fixed the issues with their monospace fonts.)
CISA KEV Tracker
cisakevtracker@mastodon.socialCVE ID: CVE-2025-27363
Vendor: FreeType
Product: FreeType
Date Added: 2025-05-06
Vulnerability: FreeType Out-of-Bounds Write Vulnerability
Notes: This vulnerability affects a common open-source component, third-party library, or a protocol used by different products. Please check with specific vendors for information on patching status. For more information, please see https://source.android.com/docs/security/bulletin/2025-05-01 ; https://nvd.nist.gov/vuln/detail/CVE-2025-27363
CVE URL: https://nvd.nist.gov/vuln/detail/CVE-2025-27363
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.5 beta 4 vs. iOS 18.5 RC 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_5_22F5068a__vs_18_5_22F75/README.md