Posts
3381Following
713Followers
1580DEF CON
defcon@defcon.socialSpring has sprung. Birds are singing, flower buds are budding and the #DEFCON33 website is open for business. Bookmark https://defcon.org/html/defcon-33/dc-33-index.html for all the latest info on everything #DC33. August will be here before you know it and you’ll want to be in the loop as things develop.
Stay in touch, and we’ll see you at #defcon.
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a1a737c
match
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1a737c.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1a737c.json&colors=light
buherator
buheratorApparently Bugcrowd was not pwned, they just try to roll out mandatory MFA:
https://www.bugcrowd.com/blog/bugcrowd-security-update-password-reset-and-mfa-requirement/
Scientists still struggle to come up with a way how this information could be included in the password reset mails they sent out, we’ll keep you updated about any breakthroughs!
h/t @raptor
buherator
buheratorhttps://cyberinsider.com/toddycat-hackers-exploit-eset-antivirus-flaw-to-bypass-windows-security/
Spoiler: version.dll strikes again...
Robin Green
fatlimey@mastodon.gamedev.placeInteresting talk on designing low-bit floating point number systems. Imagine you have 6-bits, using IEEE754 would you want to waste 6 of your codes for different NaNs? Do you really need two zeros? How about adding ±∞ or does saturating to ±FLT_MAX work for you use case? You can upconvert to Binary32 or Binary64 to do math operations, but which one gives you the better conversion when re-packing back down to 6-bits?
IEEE working group P3109 has the goods.
mei
mei@donotsta.recpresser
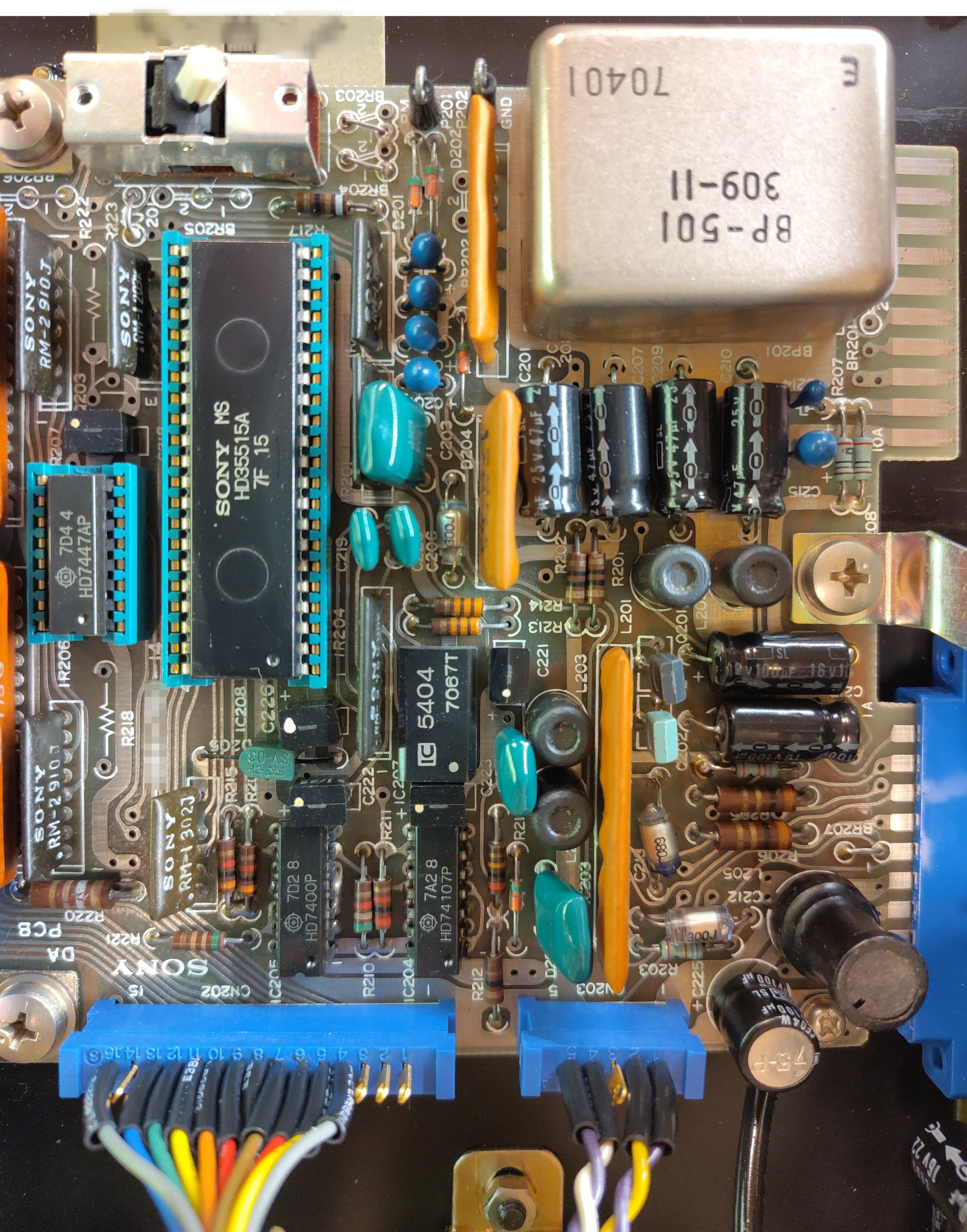
cccpresser@chaos.socialHere is another #NameThatWare challenge. While I know what the device does, I was not able to identify much of the components on the circuit board. Quite sure I could not solve this challenge myself.
So far I have not been able to identify
* the microcontroller
* the silver can on the top right
* any datecode
As always, please write down your deductions and guesses behind a CW to not spoil it for others.
Tim Blazytko
mr_phrazer@infosec.exchangeAt @recon , @nicolodev and I discuss the current state of MBA (de)obfuscation and their applications. We’ll also introduce a new #BinaryNinja plugin for simplifying MBAs in the decompiler.
Details: https://cfp.recon.cx/recon-2025/featured/
I'll also give a training: https://recon.cx/2025/trainingSoftwareDeobfuscationTechniques.html
buherator
buherator- Welcome to the #Bureaucracy! You owe us some money, but fear not, you can easily pay it with our very modern VPOS!
- Really? There’s no new items in my online mailbox you usually use.
- Oh we sent this request in a (non-certified) paper letter to the other side of the city.
- commuting Got the letter, what’s the URL for the VPOS?
- Oh we won’t tell you that…
- Nvm, I just googled it, what’s next?
- You have to choose the code that corresponds to your debt!
- Is the code in the letter you sent me?
- No, but we gave each code a title, multiple of which are very similar to what you want to pay for.
- googling OK, I found a page that matches the codes with account numbers and you did sent me the an account number so I think I found the right code!
- (mumbbling Damn it we have to get that page down!)
- So you actually sent me two letters with different sums, which one is correct?
- crickets
- I’ll just pay the bigger amount, just in case click pay Transaction rejected!
- Banks these days, huh?
- Let’s retry…
- You can’t just retry, the form you filled out is invalid now! But we can automatically create you a copy.
- This “copy” has a NULL where the original had some unique ID, are you sure this is right?
- We’re sure it’s fine…
- Alright, click pay
- UNRECOVERABLE ERROR
clownpertino - A simple macOS debugger detection trick.
Pretty sure someone using this one since it's so easy but I haven't seen it in the wild. Just some Monday lulz while the stock markets burn :P
Zack Whittaker
zackwhittaker@mastodon.socialNew, by me: Someone hacked into the Everest ransomware gang's dark web leak site and defaced it.
"Don't do crime CRIME IS BAD," Everest's site now reads.
https://techcrunch.com/2025/04/07/someone-hacked-everest-ransomware-gang-dark-web-leak-site
buherator
buheratorbuherator
buheratorhttps://hackaday.com/2025/04/06/command-and-conquer-ported-to-the-pi-pico-2/