Posts
3381Following
713Followers
1580It may be Monday, but today is also National No Housework Day, National Beer Day and also International Beaver Day. Do with that information what you will. 
Zhuowei Zhang
zhuowei@notnow.devI wondered how OSS-Fuzz fuzzes Woff2 fonts with Brotli compression.
The answer seems to be… brute force.
https://issues.oss-fuzz.com/issues/42478986 shows a sample WOFF2 fuzzed font, and it contains a valid Brotli stream.
So oss-fuzz must be fuzzing raw WOFF2 fonts without a special mutator.
Yet it works: OSS-Fuzz coverage shows 93% coverage on the WOFF2 decoder:
It works, but the uncovered lines are the error lines… As if there’s not enough executions to actually hit the error cases…
looking at the execution coverage:
71.2k makes it to woff2_open_font 57.3k makes it to woff2_decompress 14.7k makes it to reconstruct_font 8.68k makes it to the end of woff2_open_font
eShard
eshard@infosec.exchangeWe emulated iOS 14 in QEMU.
This is how we did it: https://eshard.com/posts/emulating-ios-14-with-qemu
#reverseengineering #cybersecurity #iosdev #ios #apple #devops
aki-nyan
lethalbit@chaos.socialI look away for 5 minutes and Annie goes and makes herself home in the vacant spot in the rack,
Little baby
Slashdot 
slashdot@mastodon.cloud
Were Still More UK Postmasters Also Wrongly Prosecuted Over Accounting Bug? https://news.slashdot.org/story/25/04/06/0221239/were-still-more-uk-postmasters-also-wrongly-prosecuted-over-accounting-bug?utm_source=rss1.0mainlinkanon
hackaday
hackaday@hackaday.socialBen Eater vs. Microsoft BASIC
https://hackaday.com/2025/04/05/ben-eater-vs-microsoft-basic/
CFG Bot 🤖
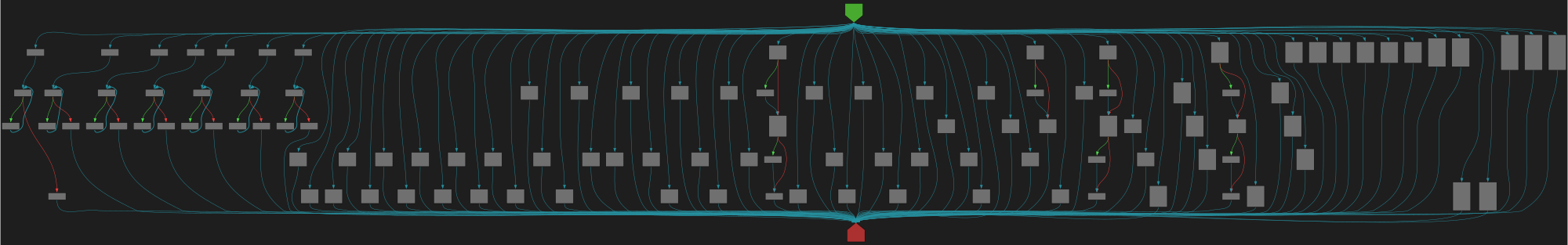
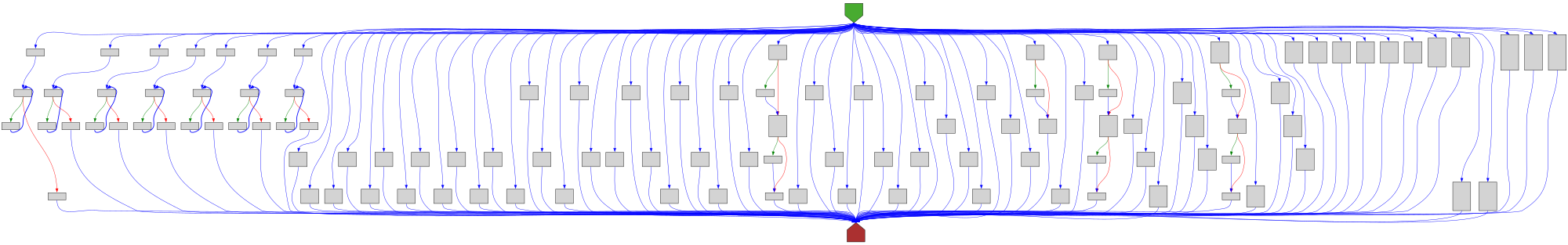
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/fix/fix.go:54 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/fix/fix.go#L54
func walkBeforeAfter(x any, before, after func(any))
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Ffix%2Ffix.go%23L54&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Ffix%2Ffix.go%23L54&colors=light
Craig Newmark
craignewmark@mastodon.socialBe like Ronin...
"Hero rat sets Guinness World Record for detecting landmines"
https://taskandpurpose.com/tech-tactics/ronin-landmines-rat-guinness-world-record/
via @TaskandPurpose
 radare
radare 
radareorg@infosec.exchange
Work in progress JNI helper plugin for #radare2 https://github.com/evilpan/jni_helper/tree/master/r2 #android #java #reverseengineering
buherator
buheratorhttps://gitlab.gnome.org/GNOME/yelp/-/issues/221
"Yelp, the GNOME user help application, allows help documents to execute
arbitrary JavaScript. A malicious help document may exfiltrate user files
to a remote server. A malicious website may download a help document
without user intervention, then trick the user into opening a ghelp URL
that references the help document. This notably requires the attacker to
guess the filesystem path of the downloaded help document."
And we just discussed old-school .HLP exploits the other day...
#EnoughEyeballs
buherator
buherator# ./mpclient_x64 ../eicar.com 2>&1 | fgrep EngineScanCallback
EngineScanCallback(): Threat Virus:DOS/EICAR_Test_File identified.
happy dance
buherator
buherator@recon 2024 - Control Flow Intergrity on IBM i
https://www.youtube.com/watch?v=0uBbklP9BSE
The video also has some '90s VHS vibes to it, the writeup is still available here (minus the last temporal safety stuff):
https://silentsignal.github.io/BelowMI/