Posts
2581Following
629Followers
1407buherator
buherator@recon 2024 - Control Flow Intergrity on IBM i
https://www.youtube.com/watch?v=0uBbklP9BSE
The video also has some '90s VHS vibes to it, the writeup is still available here (minus the last temporal safety stuff):
https://silentsignal.github.io/BelowMI/
buherator
buheratorShow content
buherator
buheratorShow content
buherator
buheratorShow content
Perfect music for this #Saturday, and a strong contender for Album Cover of the Year!
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/04/04/3
* Issue #8602 - Fixed an XSS vulnerability issue in the Query Tool and View/Edit Data (CVE-2025-2946).
* Issue #8603 - Fixed a remote code execution issue in the Query Tool and Cloud Deployment (CVE-2025-2945).
Project Zero Bot
p0botFirefox: inconsistent comparator in xslt/txNodeSorter leads to out-of-bounds access
https://project-zero.issues.chromium.org/issues/392850860
CVE-2025-1932
buherator
buheratorhttps://eshard.com/posts/emulating-ios-14-with-qemu
buherator
buheratorhttps://go.dev/issue/71988.
net/http: request smuggling through invalid chunked data
buherator
buheratorIt's more important to make people realize that they have shit to loose: enumerate critical assets, create estimations what damage can be done (which is what banks do as part of their compliance process). Many businesses (manufacturing is a typical example) don't realize how much they rely on IT these days.
buherator
buherator1) APTx runs its dumbest fuzzer and writes an exploit
2) ???
3) Ivanti releases a patch
4) APTx notices their bug is burned
5) APTx goes for a aggressive campaign (or passes the exploit to low-end peers) to cash in on the patch gap.
6) Threat intel picks up ItW exploitation
With my previous comment I wanted to express my worry that we are probably in stage 2) with God knows how many Ivanti 0-days right this moment.
Hey #infosec,
what's your best answer to people telling you "But we're not a Bank!" whenever you plan to introduce any measure to lower a risk?
buherator
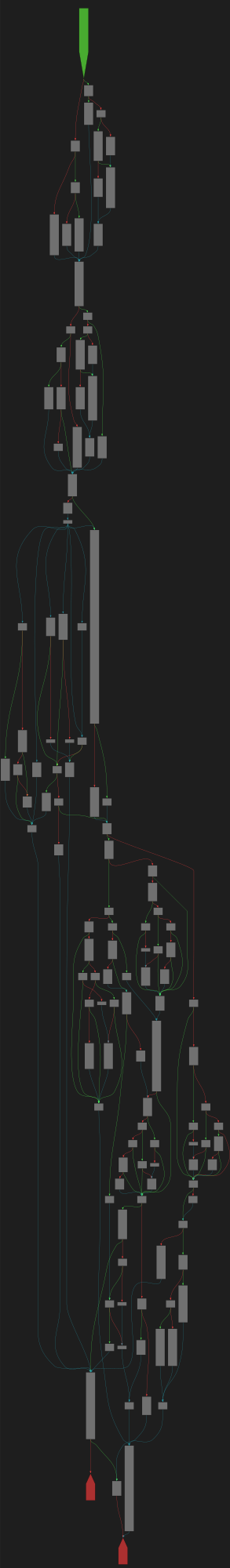
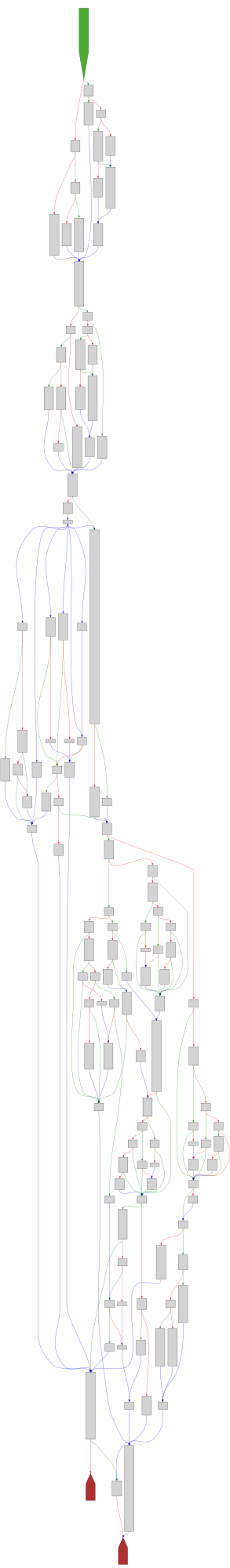
buheratorCFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00926180
__multf3
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00926180.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00926180.json&colors=light
xvonfers
xvonfers@bird.makeupOne Bug to Rule Them All: Stably Exploiting a Preauth RCE Vulnerability on Windows Server 2025
https://i.blackhat.com/Asia-25/Asia-25-Peng-One-Bug-to-Rule-Them-All.pdf
Will Dormann
wdormann@infosec.exchangeAnd per the excellent folks at watchTowr, we can see what the vulnerability is:
A stack buffer overflow in X-Forwarded-For
No need to find a specific endpoint or do something clever. Simply make a web request to anywhere on an ICS system with a large X-Forwarded-For HTTP header and you'll get a stack buffer overflow on the system. 🤦♂️
And due to the fact that the Ivanti web server does a fork() without a corresponding exec(), we get the same memory layout every single time.
Now, about Ivanti's use of remediated... The function where the overflow happens just happens to have been rewritten in a way that avoids the overflow.
Did Ivanti recognize the possibility of a stack buffer overflow and not recognize it as a security issue? Or did they just happen to change code to accidentally avoid the overflow (and decide to use exploit mitigations as well).
You decide...
Probably the highlight of all the varieties, meet its holiness the god-tier inductor.
I would really love to hear the rationale behind (hehe) this design.

 🌻
🌻





