Posts
3393Following
713Followers
1581buherator
buheratorhttps://swarm.ptsecurity.com/last-barrier-destroyed-or-compromise-of-fuse-encryption-key-for-intel-security-fuses/
raptor 
raptor@infosec.exchange
Rejoice! 🎉
My idalib-based vulnerability research tools are now fully compatible with Windows 🪟
Please test them and report any bugs 🪲
https://security.humanativaspa.it/streamlining-vulnerability-research-with-ida-pro-and-rust/
(PS. Ya like my GPT writing style? 🚀)
CFG Bot 🤖
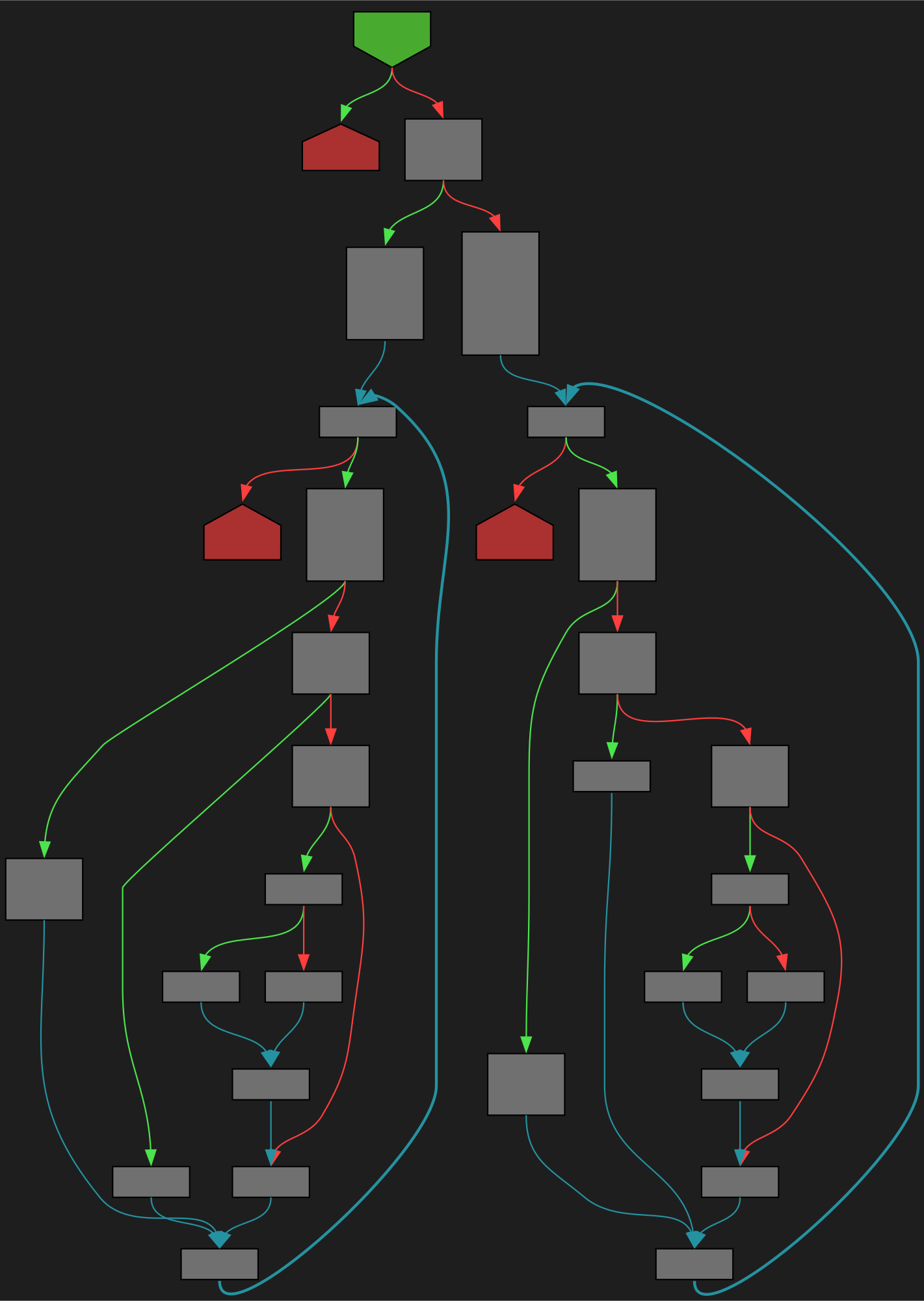
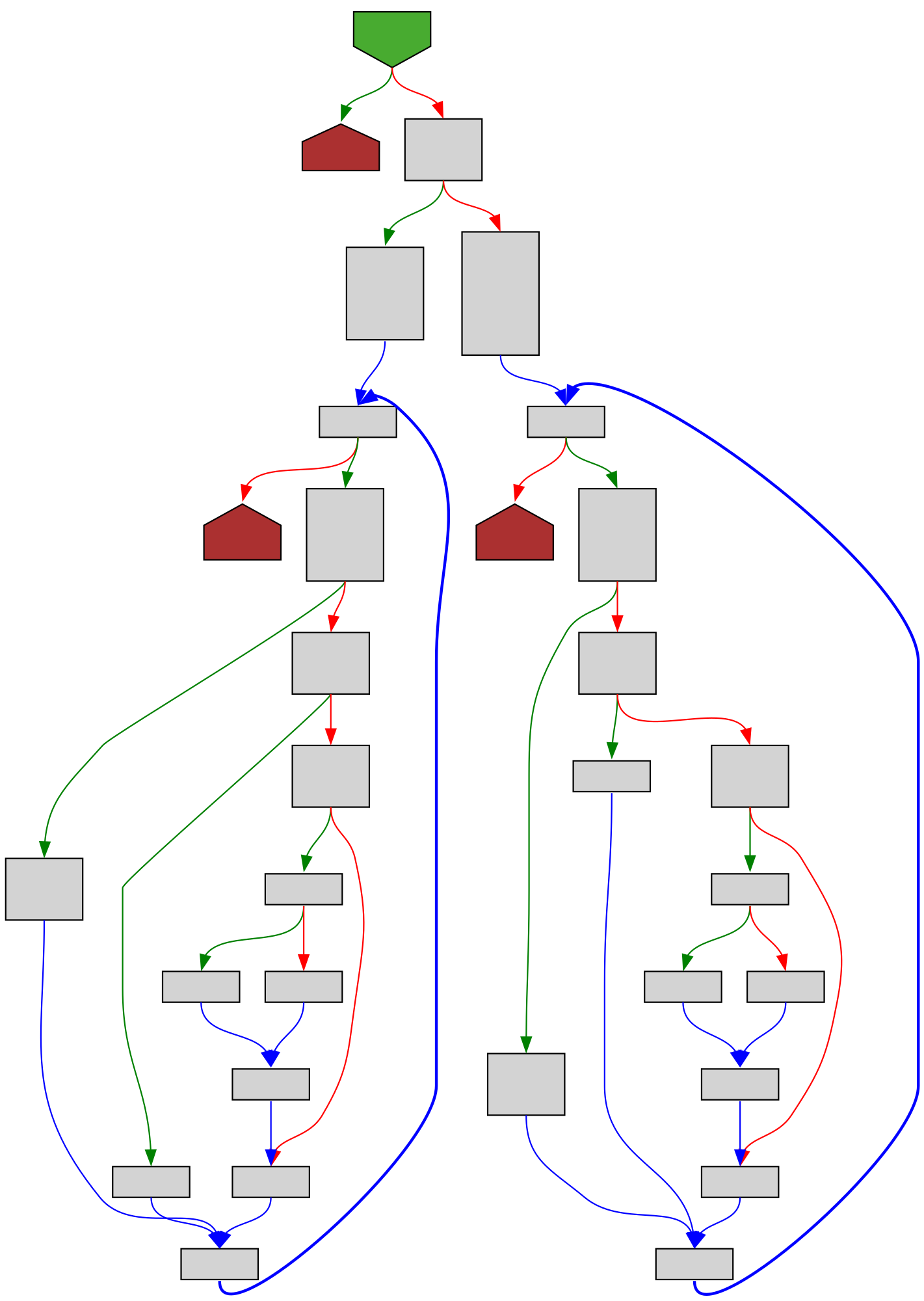
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/compile/internal/abt/avlint32.go:175 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/compile/internal/abt/avlint32.go#L175
func (t *T) Intersection(u *T, f func(x, y interface{}) interface{}) *T
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fabt%2Favlint32.go%23L175&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Fcompile%2Finternal%2Fabt%2Favlint32.go%23L175&colors=light
Ryan Castellucci (they/them) 
ryanc@infosec.exchange
"But Ryan, the C preprocessor isn't a programming language!"
Skill issue.
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeThe official website of zero-day broker Zerodium has been updated in December of last year. There are no price lists nor any information anymore, just an email and a PGP public key.
🤔
If you know what's happening there...let me know.
Project Zero Bot
p0botmsm_npu: Race between npu_host_unload_network and npu_host_exec_network_v2 leads to memory corruption
https://project-zero.issues.chromium.org/issues/380081941
CVE-2025-21424
buherator
buheratorhttps://seclists.org/oss-sec/2025/q1/234
"The order in which objects are deleted
during namespace termination is not defined, and it is possible for network
policies to be deleted before the pods that they protect." whoops :)
buherator
buheratorbuherator
buheratorhttps://scrapco.de/blog/analysis-of-cve-2025-24813-apache-tomcat-path-equivalence-rce.html
Also note that even with HTTP response data it's not straightforward to conclude that:
- file based session management was configured
- there were useful gadget chains available
Molly White
molly0xfff@hachyderm.ioFor those just learning about LibGen because of the reporting on Meta and other companies training LLMs on pirated books, I’d highly recommend the book Shadow Libraries (open access: https://direct.mit.edu/books/oa-edited-volume/3600/Shadow-LibrariesAccess-to-Knowledge-in-Global).
I just read it while working on the Wikipedia article about shadow libraries, and it’s a fascinating history. https://en.wikipedia.org/wiki/Shadow_library
I fear the already fraught conversations about shadow libraries will take a turn for the worse now that it’s overlapping with the incredibly fraught conversations about AI training.
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250320-00/?p=110981