Posts
2578Following
627Followers
1399Hey hey, you thought there be no #nakeddiefriday today? Here we go!
Today's entry is an Infineon/Siemens SAB-C167CR-LM, a microcontroller based on the C166 core. The die is in pleasant-looking pastel colours. :-) The die has pin 1 in top left corner. I'll do a short thread.
Many thanks to @debauer for supplying the samples!
SiPron page with more info and full-res map: https://siliconpr0n.org/archive/doku.php?id=infosecdj:infineon:sab-c167cr-lm
Binary Ninja
binaryninja@infosec.exchangeLess than 30 minutes until our 5.0 live stream! Join us to see all the latest features either on dev now or coming very soon:
https://www.youtube.com/@vector35/live
Kernel Shared Cache, Unions, Stack Array Creation, and so much more...
buherator
buheratorhttps://github.com/php/php-src/security/advisories/GHSA-wg4p-4hqh-c3g9
#PHP #NoCVE
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/03/14/6
CVE data collected by Alan Coopersmith:
"Fixed GHSA-rwp7-7vc6-8477 (Reference counting in php_request_shutdown causes
Use-After-Free). (CVE-2024-11235)
https://github.com/php/php-src/security/advisories/GHSA-rwp7-7vc6-8477
Fixed GHSA-p3x9-6h7p-cgfc (libxml streams use wrong `content-type` header when
requesting a redirected resource). (CVE-2025-1219)
https://github.com/php/php-src/security/advisories/GHSA-p3x9-6h7p-cgfc
Fixed GHSA-hgf5-96fm-v528 (Stream HTTP wrapper header check might omit basic
auth header). (CVE-2025-1736)
https://github.com/php/php-src/security/advisories/GHSA-hgf5-96fm-v528
Fixed GHSA-52jp-hrpf-2jff (Stream HTTP wrapper truncate redirect location to
1024 bytes). (CVE-2025-1861)
https://github.com/php/php-src/security/advisories/GHSA-52jp-hrpf-2jff
Fixed GHSA-pcmh-g36c-qc44 (Streams HTTP wrapper does not fail for headers
without colon). (CVE-2025-1734)
https://github.com/php/php-src/security/advisories/GHSA-pcmh-g36c-qc44
Fixed GHSA-v8xr-gpvj-cx9g (Header parser of `http` stream wrapper does not
handle folded headers). (CVE-2025-1217)
https://github.com/php/php-src/security/advisories/GHSA-v8xr-gpvj-cx9g "
#PHP
buherator
buheratorAnything I missed @shellsharks ?
rev.ng
revng@infosec.exchange🧟♂️ Finding dead bodies
A pad about find dead code using code coverage tools.
It was made by one of us for a talk at the rev.ng hour of some years ago.
More effort than required was put in the image but the results was undoubtedly great.
David Gerard
davidgerard@circumstances.runOpenAI asks US government for the moon on a stick (because CHINA)
https://pivot-to-ai.com/2025/03/14/openai-asks-the-us-government-for-the-moon-on-a-stick/ - text
https://www.youtube.com/watch?v=6VxrrCdMdL0 - video
HalvarFlake
HalvarFlake@mastodon.socialMy contempt for anyone involved with this drivel knows few limits. Conflating issues and fear mongering because a Chinese company dared to publish an actual open model:
And trying to talk about copyright after training in Libgen.
Hypocrisy, lies, grifting :-( - the level of despicable behavior is just out of this world.
wild how the media has fully given up on using the word “lie” as powerful people just bullshit constantly
it’s always “contradicted earlier statements” or “made claims that do not align with the facts” like girl just say they knowingly made shit up, we all see it
buherator
buheratorbuherator
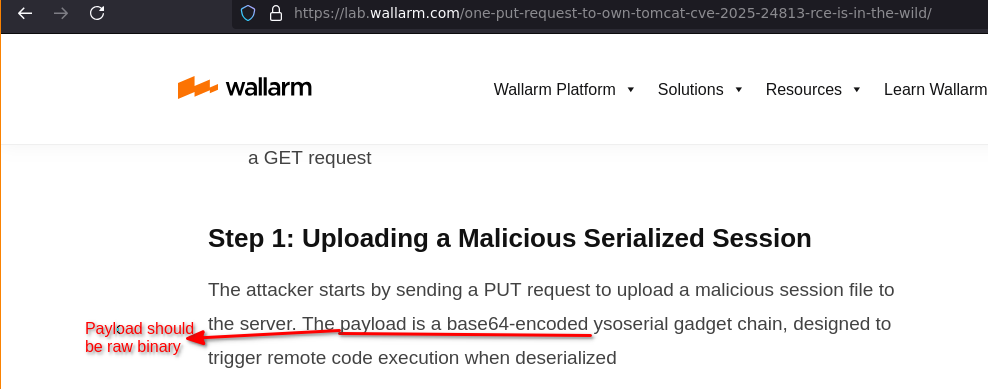
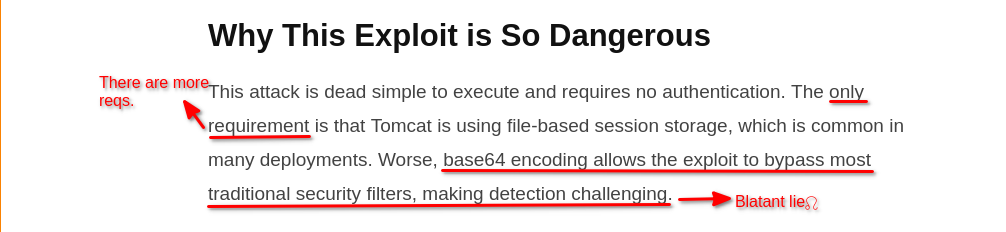
buheratorhttps://web.archive.org/web/20250314071219/https://lab.wallarm.com/one-put-request-to-own-tomcat-cve-2025-24813-rce-is-in-the-wild/
There is a PoC on GitHub too now - it improves my findings by directly invoking the session corresponding to the saved object so you don't have to wait for periodic refreshes:
https://github.com/iSee857/CVE-2025-24813-PoC/
This PoC will raise the EPSS score too.
Edit: Wallarm published an update showing that exploit traffic was detected before a PoC was public. Problem is my writeup&PoC was published well before their detection :P
Peter Stöckli
ulldma@infosec.exchangeIn this demonstration I show the impact of CVE-2025-25291/CVE-2025-25292, an authentication bypass in ruby-saml used by high profile OSS projects such as GitLab. My team coordinated with both the ruby-saml maintainer and GitLab to get this vulnerability fixed and patches are available at https://about.gitlab.com/releases/2025/03/12/patch-release-gitlab-17-9-2-released/
Jason Koebler
jasonkoebler@mastodon.socialthis is so so so wild, must read:
https://www.404media.co/super-nintendo-hardware-is-running-faster-as-it-ages/
buherator
buheratordrawio
drawio@hostux.social🚀 We’re working on a new user interface for http://draw.io! 🎨 Check out the details here 👉 https://github.com/jgraph/drawio/discussions/4953 — and let us know what you think! Your feedback will help shape the future of http://draw.io! 💡😊 #drawio #UI