Posts
2584Following
627Followers
1397buherator
buheratorAccidental CISO
accidentalciso@infosec.exchangeAs you are preparing for your annual password change, I would like to remind you that our password policy clearly states that all characters are special.
Yellow Flag
WPalant@infosec.exchangeJohn @tuckner sent me on an interesting wild goose chase. He is investigating the Cyberhaven extension compromise, trying to find out more. And he found something that he considered another campaign compromising browser extensions, related to the sclpfybn[.]com domain: https://secureannex.com/blog/cyberhaven-extension-compromise/#a-new-thread-to-pull-on
One of the extensions that used to contain the code in question was Visual Effects for Google Meet – which brought him to me because I recently covered that extension in my Karma Connection article: https://palant.info/2024/10/30/the-karma-connection-in-chrome-web-store/
I checked my data but couldn’t find sclpfybn[.]com domain mentioned in any extensions other than the ones @tuckner found already. I then looked for similar code and immediately found it in Urban VPN Proxy.
First thought: Urban VPN Proxy has the legitimate version of a library that was trojanized elsewhere. Taking a look at the communication of Urban VPN Proxy disproved that theory almost immediately – not only was it communicating in exactly the same way, but also to an unknown domain, namely ducunt[.]com. Yet the same endpoint existed on the official urban-vpn[.]com domain as well.
So not only did Urban VPN Proxy contain essentially the same code, it was likely added there by the developers themselves. Further investigation increased the suspicion that all these extensions haven’t been compromised, that this was rather some monetization SDK.
At which point @tuckner found the sales pitch for that SDK, detailing how it would add ad blocking functionality to the extension at the cost of exfiltrating very detailed browsing data (of course anonymized and aggregated before being sold to everyone asking for it, we know the drill). And explanations on how to make sure Google won’t object.
And that explains it all: before the Visual Effects for Google Meet developer sold their extension to Karma, they tried to monetize it with this “ad blocking library.” The sales pitch doesn’t mention who develops the library but everything points to Urban VPN.
According to Urban VPN privacy policy, they are selling the data they collect from their users via BIScience Ltd. Who are most likely the hidden owners of Urban Cyber Security Inc., a company registered to a virtual address in the USA.
Alan Sguigna
alansguigna@bird.makeupPart 2 of my series on Hypervisor-Managed Linear Address Translation (HLAT) is here: https://www.asset-intertech.com/resources/blog/2024/12/vt-rp-hlat-and-my-aaeon-alder-lake-core-i7-1270pe-board-part-2/. I used SourcePoint to pinpoint where HLAT is enabled on the p-cores of my AAEON Alder Lake board. Many thanks to @yarden_shafir, @aall86 and @standa_t for inspiration.
buherator
buheratorhttps://seclists.org/fulldisclosure/2024/Dec/21
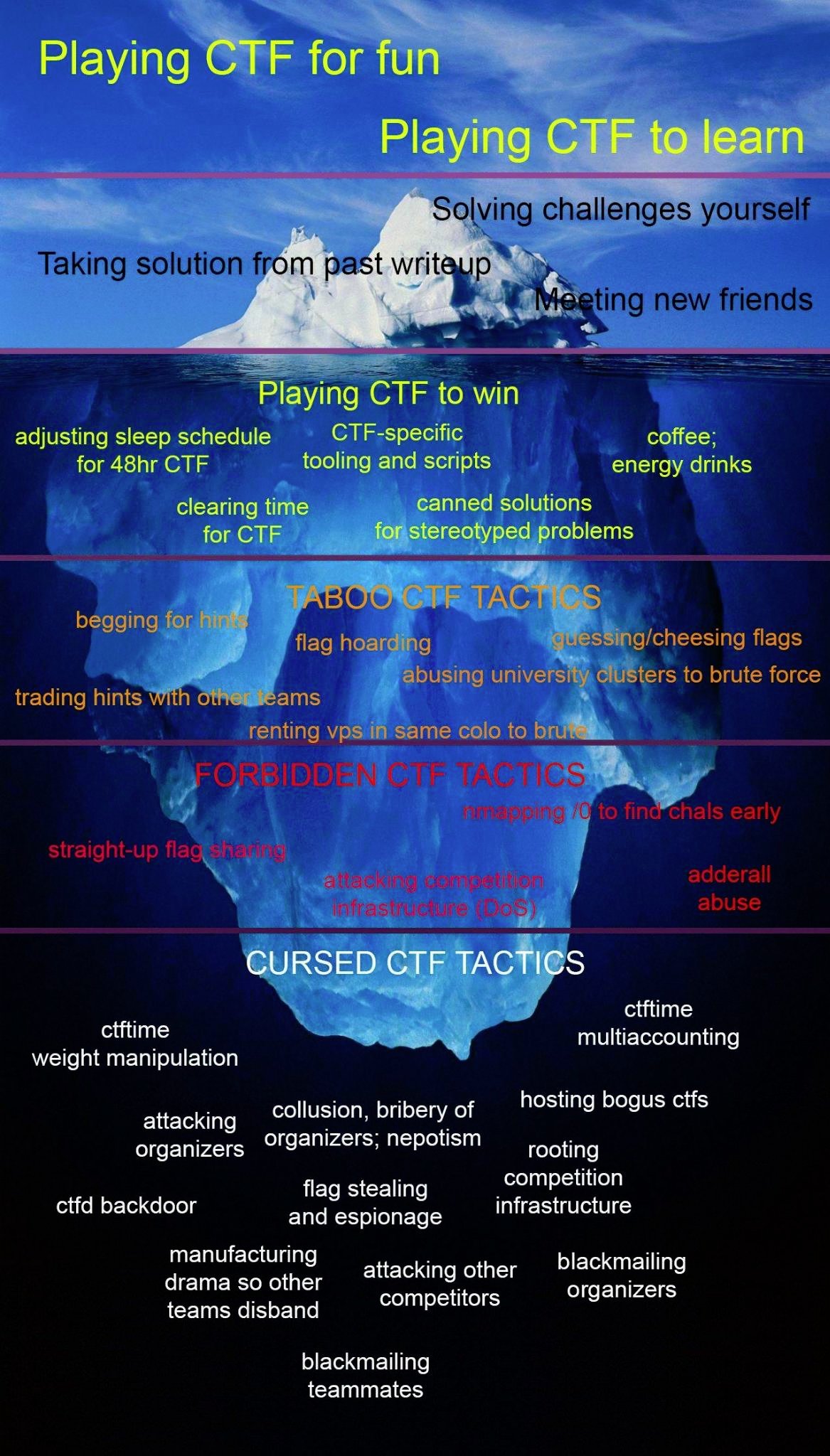
Do these count as Cursed CTF tactics?
buherator
buheratorhttps://hyp3rlinx.altervista.org/advisories/IBMi_Navigator_Server_Side_Request_Forgery_CVE-2024-51463.txt
https://hyp3rlinx.altervista.org/advisories/IBMi_Navigator_HTTP_Security_Token_Bypass-CVE-2024-51464.txt
(CVE-2024-51463, CVE-2024-51464)
buherator
buheratorhttps://www.ibm.com/support/pages/node/7180036?myns=swgother&mynp=OCSSPHQG&mynp=OCSWG60&mync=A&cm_sp=swgother-_-OCSSPHQG-OCSWG60-_-A
buherator
buheratorhttps://u1f383.github.io/linux/2024/12/28/remote-memory-access-in-linux.html
buherator
buheratorhttps://u1f383.github.io/linux/2024/12/29/the-feasibility-of-using-hardware-breakpoints-to-extend-the-race-window.html
buherator
buheratorhttps://blog.convisoappsec.com/en/from-arbitrary-file-write-to-rce-in-restricted-rails-apps/
buherator
buheratorhttps://old.reddit.com/r/ghidra/comments/1hpom0c/what_does_mean_to_commit_paramsreturn/
Benjamin Ross
BenRossTransit@mastodon.socialWaymo (aka Google) admits that it trains its robotaxis to break the law. When WaPo reporter finds robotaxis fail to stop for pedestrians in marked crosswalk 70% of the time, Waymo says it follows "social norms" rather than laws.
Expert explains: When robotaxis obey law, they don't go fast enough to compete successfully with Uber, so Google execs ordered engineers to ignore laws.
https://wapo.st/3ZZDifm
Kevin Beaumont
GossiTheDog@cyberplace.socialBeyondTrust SaaS hack announced just before Xmas was used to access US Treasury Department.
I understand it impacts other customers, too - the threat actor stole keys used to access customer workstations (even where they deployed the on prem server - the product is a reverse proxy effectively), which BeyondTrust has opted not to disclose to customers.
Justin du Coeur
jducoeur@social.coopThis is, BTW, why I'm such a passionate #Kagi enthusiast. Their technology is good, but their business plan -- subscriptions instead of advertisements, bootstrapped instead of VC-based -- matters way more. It means that they *have* to focus on what's good for their users, not what pleases the current whim of the stock market and the billionaires.
I dearly wish more companies would catch that clue…
Eniko Fox
eniko@peoplemaking.gamesto elaborate: i went without heating for the last 2 years of kitsune tails production. we have enough to run the heating now, but if you want to play gay fox girl SMB3 and help ensure the heating stays on, you can get it on sale now: https://store.steampowered.com/app/1325260/
or on itch: https://eniko.itch.io/kitsunetails
#GameDev #PixelArt #QueerGames #IndieGame #IndieDev #RetroGaming