Posts
3381Following
713Followers
1580internetarchive
internetarchive@mastodon.archive.orgIn a new Q&A, Philip Bump, columnist for The Washington Post, reflects on why archiving the news goes beyond saving stories. From holding leaders accountable to capturing moments in culture, Bump shares insights on the need to preserve digital media. #VanishingCulture
🔗 https://blog.archive.org/2024/11/04/vanishing-culture-qa-with-philip-bump-the-washington-post/
AttackerKB
attackerkbTopic description: "Improper Input Validation in the admin portal of Ivanti Connect Secure before 22.7R2.1 and 9.1R18.9, or Ivanti Policy Secure before 22.7R1.1 allows a remote authenticated attacker to achieve remote code execution. ..."
"Ivanti Connect Secure versions prior to 22.7R2.1 and 22.7R2.2, and Ivanti Policy Secure versions prior to 22.7R1 are vulnerable to [CRLF injection](https://owasp.org/www-community/vulnerabilities/CRLF_Injection), which leads to remote code execution with the privileges of the user `root` ..."
Link: https://attackerkb.com/assessments/34ea5769-e0d6-4c65-bfc3-510c679ef515
RE//verse Conference
REverseConf@infosec.exchangeDon’t miss out—RE//verse tickets are on sale now! https://shop.binary.ninja/products/re-verse
ph0wn
ph0wn@infosec.exchangeAnnouncement: ph0wn registration is opening today at 2pm!
The Ph0wn/Pico fan shop is already open. You'll find there hoodies, t-shirts, bags and many other items with or without @picolecroco . All items are sold at cost price and there's a 25% discount for 10 days.
Wear your item on the day of ph0wn!
Joxean Koret (@matalaz)
joxean@mastodon.socialI have written a copyleft #chiptune and #lofi album for the upcoming Radare2 conference: https://rada.re/con/2024/
Enjoy!
jiska 🦄
jiska@chaos.social
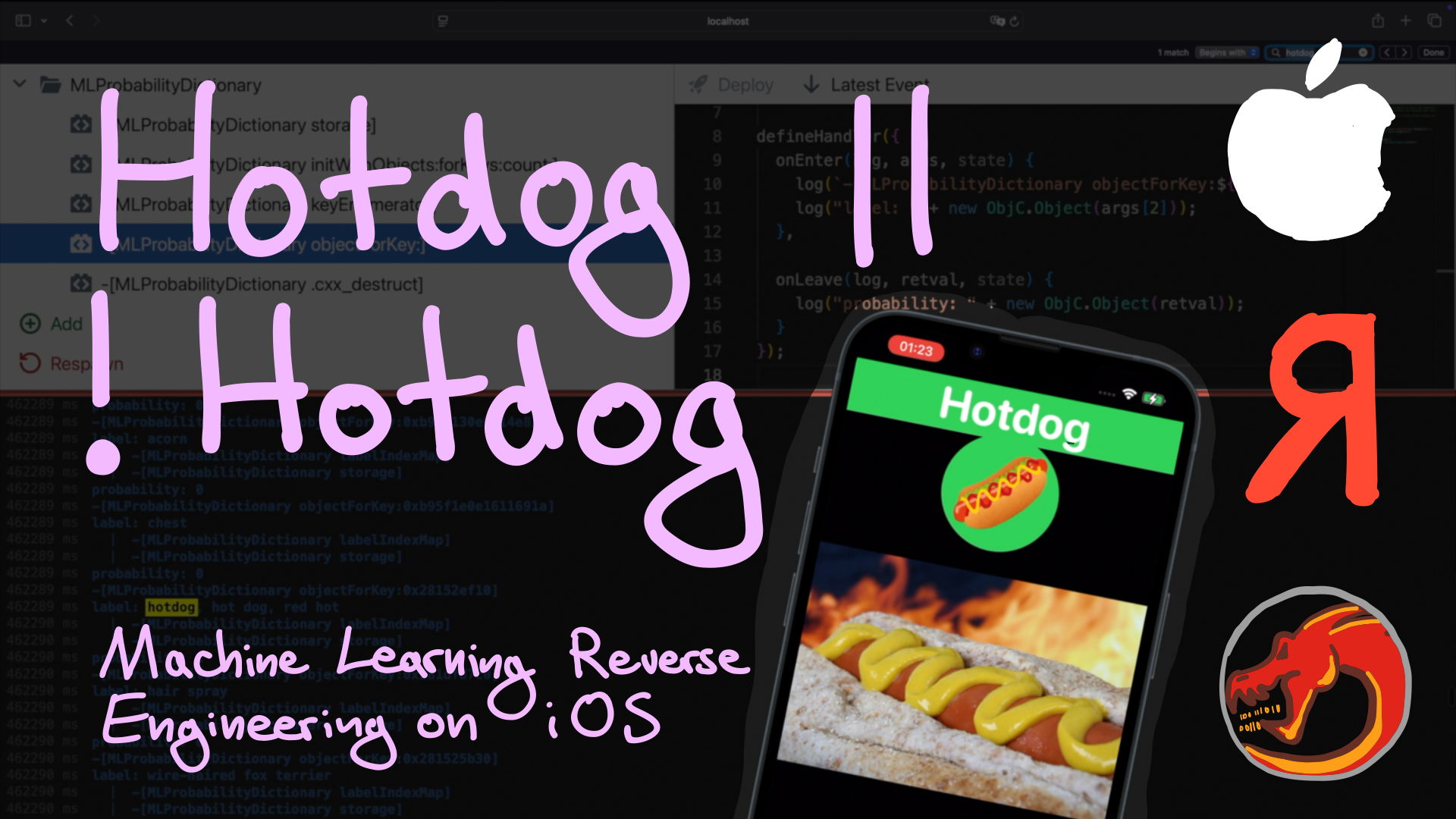
Hotdog or not hotdog?? 🌭
Let's take a look into a machine learning app that can detect hotdogs. How does it work? Can we change it into a pizza detector 🍕 app?
https://youtu.be/e2kosWm2vag
#reverseengineering #reversingshorts
SinSinology
sinsinology@bird.makeup🔥💀After 40 hours of constant reversing of weird looking c++ and no sleep, I Finally cooked the
CVE-2024-47575 fortimanager unauthenticated RCE 🩸
buherator
buheratorhttps://www.netmeister.org/blog/tls-hybrid-kex.html
#cryptoraphy #tls #pqcrypto
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20241029-00/?p=110436
#PowerPC #PPC #Itanium
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20241030-00/?p=110440
sha1lan
sha1lan@infosec.exchangeCode auditing is not the same as vulnerability research
https://pacibsp.github.io/2024/code-auditing-is-not-the-same-as-vulnerability-research.html
buherator
buheratorhttps://nickg.ca/posts/economics-of-proving-exploitability/
x43r0
x43r0@infosec.exchange@sha1lan I see the two as very similar activities, but as you say with different goals and outputs.
I think what I would call code auditing is closer to what you would call vulnerability research. One example you gave was of a highly vulnerable library used to process static content. If I am reviewing a product or feature I will do my best to avoid ever reporting something like that, because it’s not actually vulnerable to anything. That’s not to say I am perfect as sometimes time constraints and complexity can lead to a useless report, but I do what I can under the circumstances. I might just be nitpicking that specific example. :)
I wrote about a slightly different framing of this a few months back: https://nickg.ca/posts/economics-of-proving-exploitability/
I see the difference as depth vs breadth. Depth provides stronger evidence of exploitability at the expense of breadth. Breadth provides a higher quantity of dangerous looking code or at the expense of possibly useless findings.
Anyway any differences I have with it are quite minor. I think I like it so much because it’s very focused on the customer goals instead of my focus on the activities I would take to meet those goals.
buherator
buheratorMarcin Wichary
mwichary@mastodon.onlineI love how this looks like they’re having a conversation.
Ethan J. A. Schoonover
ethanschoonover@mastodon.socialStop thinking of Twitter, TikTok, IG, (et al) as social media sites.
They are **Content Refineries.**
Like processed food manufacturers they take user content & extract the most addicting/engaging content. Brains eat it up but in an unhealthy “devour the whole bag of chips” way.
They make hyper-processed social media junk food.
Mastodon is more like a potluck. We're all bringing dishes. It's a mess. Kids are running all over. But we are, at least, real people sharing real things.
Cassandrich
dalias@hachyderm.ioFinally achieved empty tcpdump starting Firefox. Had to find and clear location.services.mozilla.com and push.services.mozilla.com from show-all in about:config. Then there were the following that are hard-coded, not appearing in about:config, for which /etc/hosts needed to be invoked:
firefox.settings.services.mozilla.com content-signature-2.cdn.mozilla.net prod.remote-settings.prod.webservices.mozgcp.net content-signature-chains.prod.autograph.services.mozaws.net
FFS do better.