Posts
3007Following
698Followers
1546Stephen Brennan
brenns10@snake.club@kernellogger
@kernelconfig only partially related, but if you're ever in need of looking up the values of configurations for common Linux distro kernels, you can check:
https://oracle.github.io/kconfigs/
A bit of shameless self promotion but I do find it genuinely useful.
buherator
buheratorShow content
https://theblackdahliamurder.bandcamp.com/album/servitude
R.I.P. Trevor :(
Peter van Dijk
habbie@fosstodon.orgOpenPrinting/CUPS project decided to publish my related-but-different finding (in code that is about to all go away) https://github.com/OpenPrinting/cups-filters/security/advisories/GHSA-rq86-c7g6-r2h8
Aris Adamantiadis  💲Paid
💲Paid
aris@infosec.exchange
So in an insight it's obvious why the details leaked. Someone wanted to cut this drama short.
Aris Adamantiadis  💲Paid
💲Paid
aris@infosec.exchange
Some soft skills insight I gathered over my long career as a security researcher and shitposter:
- When you insult the devs on your security bug reports when they dare not understanding the impact of your awesome bug on the first try, they turn non cooperative. Their main focus shifts from fixing the bug to avoid interacting with you.
- When the disclosure process isn't going well, going to your community to stir the pot isn't going to make things go easier, especially when you're overevaluating the impact of your bug.
Thanks for following my Ted speech
buherator
buherator#Ghidra 11.2 released
Documentation links with HTML preview (generated links point to raw repo contents):
https://github.com/NationalSecurityAgency/ghidra/releases/tag/Ghidra_11.2_build
buherator
buheratorhttps://www.assetnote.io/resources/research/insecurity-through-censorship-vulnerabilities-caused-by-the-great-firewall
buherator
buheratorhttps://www.thezdi.com/blog/2024/9/25/exploiting-exchange-powershell-after-proxynotshell-part-4-no-argument-constructor
Thunderbird: Free Your Inbox
thunderbird@mastodon.onlineThunderbird for Android is coming soon! Find out how to get involved, from beta testing to localization to support and more, in our shiny new contributor guide!
(Seriously, by soon, we mean soon!)
#Thunderbird #Android #OpenSource
https://blog.thunderbird.net/2024/09/contribute-to-thunderbird-for-android/
nixCraft 🐧
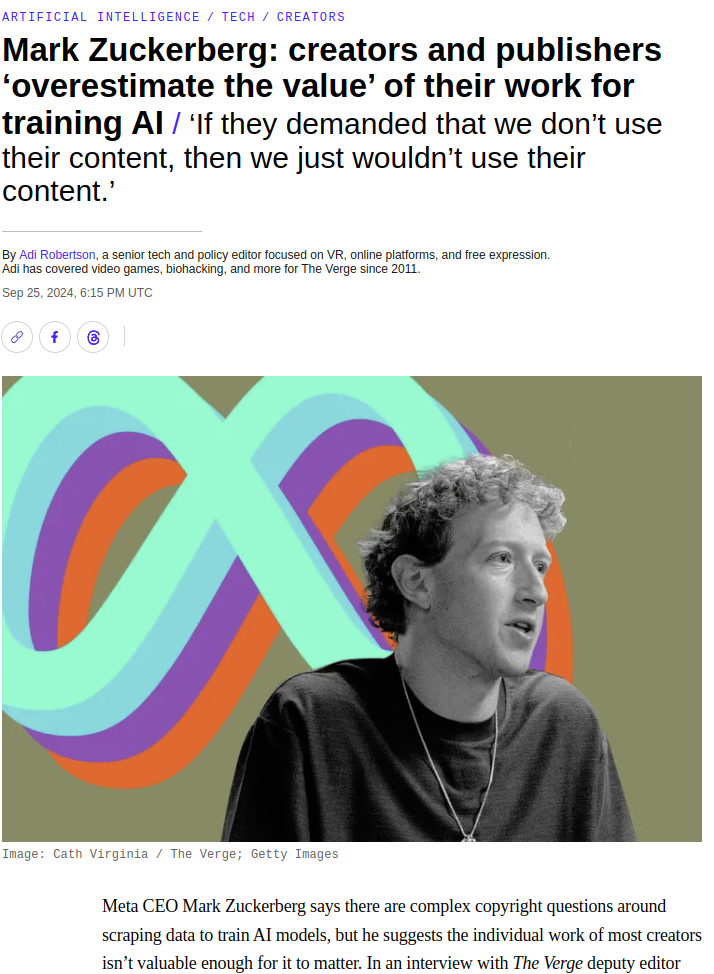
nixCraft@mastodon.socialMark Zuckerberg says the individual work of most creators isn’t valuable enough for it to matter. First of all, FUCK you, Mark. Another billionaire thinks an artist's work, such as images/art, books, music, text, and other things, has no value. People can't even browse IG or FB without downloading your shity app. Why don't you allow everyone to scrap those IG/FB posts? This guy is a menace to society and doesn't care if someone will lose their livelihood so that he can have another 100 billion.
/r/netsec
_r_netsec@infosec.exchangeUnath RCE in CUPS which triggers after a print job - affects most desktop linux flavors https://www.evilsocket.net/2024/09/26/Attacking-UNIX-systems-via-CUPS-Part-I/
Andy Greenberg
agreenberg@infosec.exchangeHackers showed me (there's video) how a website vulnerability let them locate, unlock, honk the horn, start ignition of any of millions Kias in seconds, just by reading a car's license plate.
They found similar bugs for a dozen carmakers over the last two years.
https://www.wired.com/story/kia-web-vulnerability-vehicle-hack-track/
buherator
buheratorhttps://gabrieldurdiak.github.io/clfd/
Anderson Nascimento
andersonc0d3@infosec.exchangeI am teaching a course on Linux kernel exploitation, and I mentioned the indeterminism of the objects in the physmap to the class. An example I showed is the struct task_struct of the first process, systemd. Even with KASLR disabled, that address will always differ on every boot. I said the CPU is fundamentally indeterministic, but my answer is too vague. I will read the Linux kernel initialization code to see if I discover anything interesting. Still, I would appreciate it if someone could give me a more detailed answer or point me in the right direction.
(gdb) p/x init_task->tasks->next
$76 = 0xffff888005028890
(gdb)
(gdb) p/x init_task->tasks->next
$77 = 0xffff88800502bb90
(gdb)
(gdb) p/x init_task->tasks->next
$79 = 0xffff88800502d510
(gdb)
404 Media
404mediaco@mastodon.socialA jockey who is paralyzed from the waist down lost his ability to walk after a small battery for his $100,000 exoskeleton broke and the manufacturer refused to fix it because it was more than 5 years old
Jason Scott
textfiles@mastodon.archive.orgGreetings, cool people. The Internet Archive is having our yearly celebration event in October. The announcement and the link to getting tickets to attend are here:
https://blog.archive.org/2024/08/19/celebrate-with-the-internet-archive-on-october-22nd-23rd/
#science #BlackHole #simulation #JeanPierreLuminet #c1960 #c1978
The first simulated image of a black hole was calculated with an IBM 7040 computer using 1960 punch cards and hand-plotted by French astrophysicist Jean-Pierre Luminet in 1978.