Posts
3059Following
703Followers
1553Dan Goodin
dangoodin@infosec.exchangeBy me:
Chief among them: mandatory resets, required or restricted use of certain characters, and the use of security questions
Wladimir Palant
WPalant@infosec.exchangeOk, I found the hotel on booking.com but I restarted my browser and now it shows up with a much higher price… I see, coming from the search as opposed to opening the hotel page directly gives you a discount… And pretending to be a mobile browser (via Firefox’ Responsive Mode) gives you another discount… Ah, screw booking.com and their attempts to overcharge me, I can just book directly on the hotel website which is still cheaper.
I want this LEGO Turing machine! https://ideas.lego.com/projects/10a3239f-4562-4d23-ba8e-f4fc94eef5c7
buherator
buheratorhttps://www.synacktiv.com/en/publications/fuzzing-confused-dependencies-with-depfuzzer
buherator
buheratorhttps://ssd-disclosure.com/ssd-advisory-nortek-linear-emerge-e3-pre-auth-rce/
No CVE for this one?
Project Gutenberg
gutenberg_org@mastodon.social#OTD in 1905.
Albert Einstein publishes the third of his Annus Mirabilis papers, introducing the special theory of relativity, which used the universal constant speed of light c to derive the Lorentz transformations.
There are some controversies on the question of the extent to which Mileva Marić contributed to the insights of Einstein's annus mirabilis publications
https://en.wikipedia.org/wiki/Annus_mirabilis_papers#
On the Electrodynamics of Moving Bodies at PG:
https://www.gutenberg.org/ebooks/66944
buherator
buheratorI have some doubts about this "half-life" metric, but maybe I don't get the full picture:
https://infosec.place/notice/AmO2BAowHxngnThcjg
buherator
buheratorI still have to dig into the works referenced by the recent Google post, but the data is obviously based on known vulns.
https://security.googleblog.com/2024/09/eliminating-memory-safety-vulnerabilities-Android.html
Because of this I think the conclusion shouldn't be that bugs naturally die out ("half-life"). Rather, if we have a fixed set of methods to discover vulns, we will eventually find everything _we currently can_ in a fixed code base, and we will again find some in new code.
I think Orange Tsai's latest work on Apache modules is a great demonstration of how a new approach can result in a bunch of CVE's. But the "realization" about format strings also comes to mind. How much "old" code had to be fixed because of that?
What I'd like to see is some data on memory-safe languages blocking otherwise vulnerable code paths, or vulns getting discovered during integration with safe languages.
Mr. Q The Pizza Demon
radicalrobit@laserdisc.partysilicon valley is fucking cooked man. they have absolutely nothing left. they don't even have straws to grasp at anymore.
Talos Vulnerability Reports
talosvulnsMicrosoft Pragmatic General Multicast Server PgmCloseConnection stale memory dereference
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2062
CVE-2024-38140
jeffvanderstoep
jeffvanderstoep@infosec.exchangeI’m super excited about this blogpost. The approach is so counterintuitive, and yet the results are so much better than anything else that we’ve tried for memory safety. We finally understand why.
https://security.googleblog.com/2024/09/eliminating-memory-safety-vulnerabilities-Android.html
Jonathan Yu
jawnsy@mastodon.social"By turning off your lights all day every day for a month, you conserved about 1 percent of the energy needed for AI to generate a picture of a duck wearing sunglasses. Isn’t he cute? Aside from the fact that he has the feet of a human man, of course."
"By dropping $7K on better, energy-efficient insulation for your home, Google AI was able to tell someone how to prepare chicken incorrectly, and they got, like, super sick—thanks to you!"
Ange
Ange@mastodon.socialOur paper "Magika: AI-powered content-type detection" is up on Arxiv:
https://arxiv.org/abs/2409.13768
c3voc releases
c3voc_releases@chaos.socialEnhancing Security with Systemd: Secure Web Tokens and TPM 2.0 has been released on media.ccc.de and YouTube #asg2024 #MainHall https://media.ccc.de/v/all-systems-go-2024-265-enhancing-security-with-systemd-secure-web-tokens-and-tpm-2-0 https://www.youtube.com/watch?v=NrO-Q_x36U8
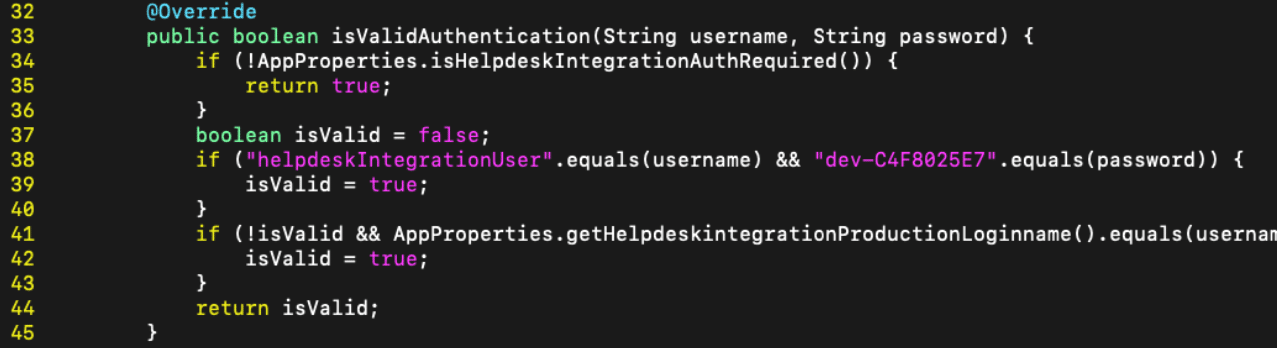
buherator
buheratorhttps://www.horizon3.ai/attack-research/cve-2024-28987-solarwinds-web-help-desk-hardcoded-credential-vulnerability-deep-dive/
/r/netsec
_r_netsec@infosec.exchangeCritical Vulnerabilities in WatchGuard SSO Agent https://www.redteam-pentesting.de/advisories/rt-sa-2024-006/